Welcome to our
Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.[SANS ISC] Custom Python RAT Builder
published on 2022-01-07 11:38:10 UTC by XavierContent:
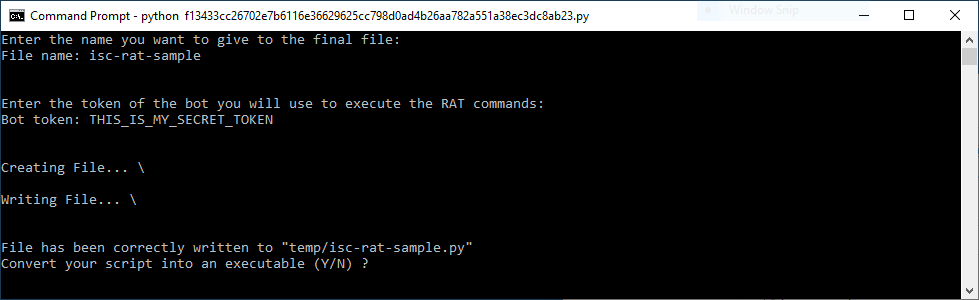
I published the following diary on isc.sans.edu: “Custom Python RAT Builder“:
This week I already wrote a diary about “code reuse” in the malware landscape but attackers also have plenty of tools to generate new samples on the fly. When you received a malicious Word documents, it has not been prepared by hand, it has been for sure automatically generated. Except if you’re a “nice” target for attackers and victim of some kind of “APT”. The keyword here is “automation”. If defenders try to automate as much as possible, attackers too… [Read more]
The post [SANS ISC] Custom Python RAT Builder appeared first on /dev/random.
https://blog.rootshell.be/2022/01/07/sans-isc-custom-python-rat-builder/
Published: 2022 01 07 11:38:10
Received: 2022 01 07 11:43:53
Feed: /dev/random
Source: /dev/random
Category: Cyber Security
Topic: Cyber Security
Views: 13
