Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Exclusive: The Posts Moncler Missed Before Latest Data Breach
published on 2022-02-08 11:56:35 UTC by Hagar MargolinContent:
Moncler, the Italian luxury fashion brand, confirmed it suffered a major ransomware attack in December, which resulted in a data breach. The attack was carried out by the AlphV/BlackCat gang, who are now selling the stolen data on the dark web.
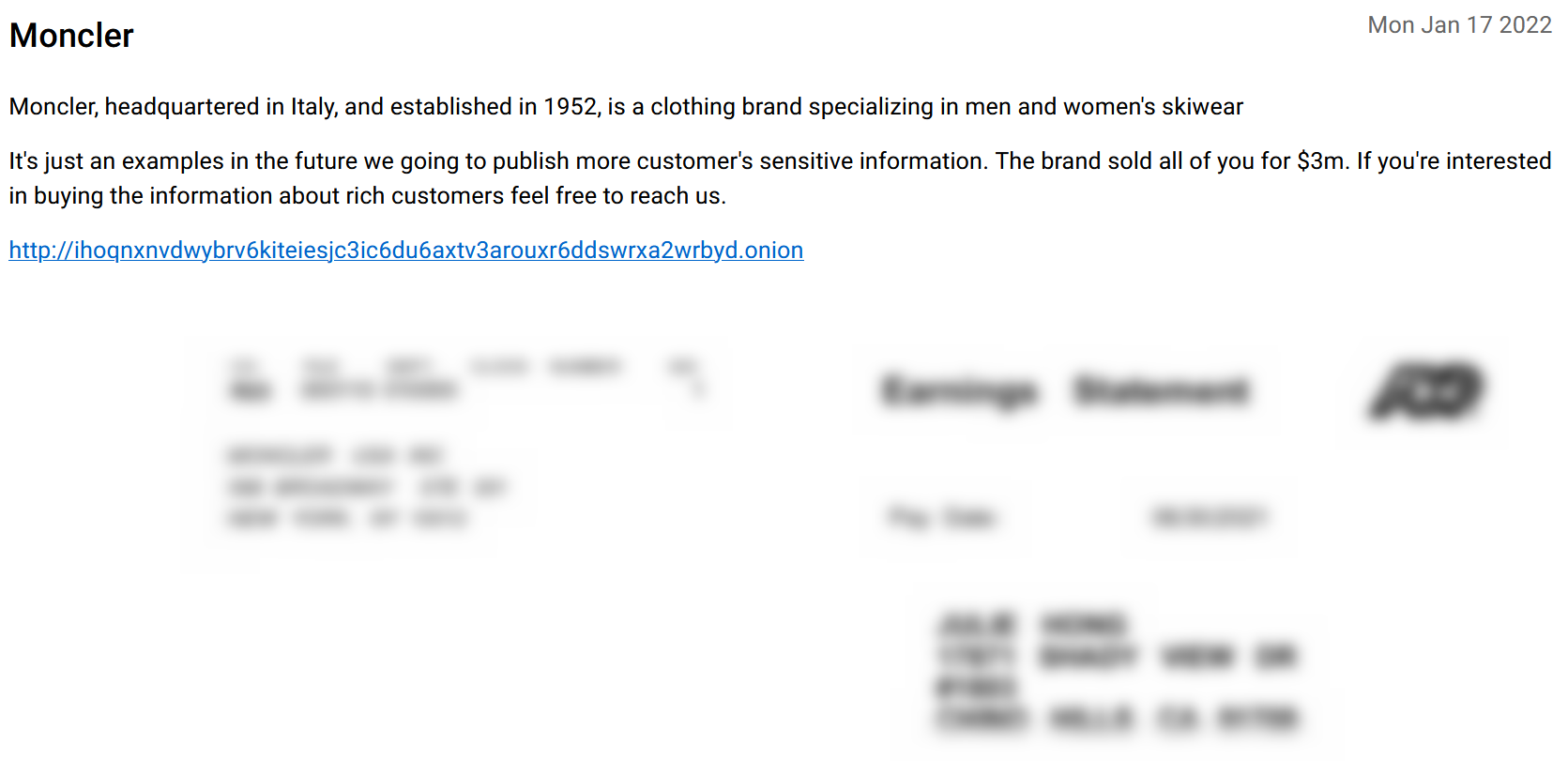
In an exclusive investigation, our cyber team discovered several highly suspicious posts in dark web forums that could indicate the breach was underway.
Monitoring Data Breaches
As seen in the picture above, the AlphV group officially announced that they had attacked Moncler, and shared a small sample of some of the company’s sensitive documents they stole, in order to prove their credibility. We crawled this post as soon as it was published on January 17, 2022, as part of our ongoing monitoring of ransomware sites.
Monitoring this type of posts in real-time is essential as it allows compromised organizations more time to assess and address the crisis.
But our team found several posts Moncler should’ve seen months before the attack took place.
Post # 1: The trade of Moncler employees’ digital fingerprints
A lot of dangers lurk for individual users and companies when it comes to the trade of stolen digital fingerprints on the dark web. Stolen digital fingerprints refers to information stored on the user’s browser, including cookies, login information from the websites the victim browsed (such as usernames and passwords), IP address, and other operating system details, which are stolen by RedLine Stealer malware.
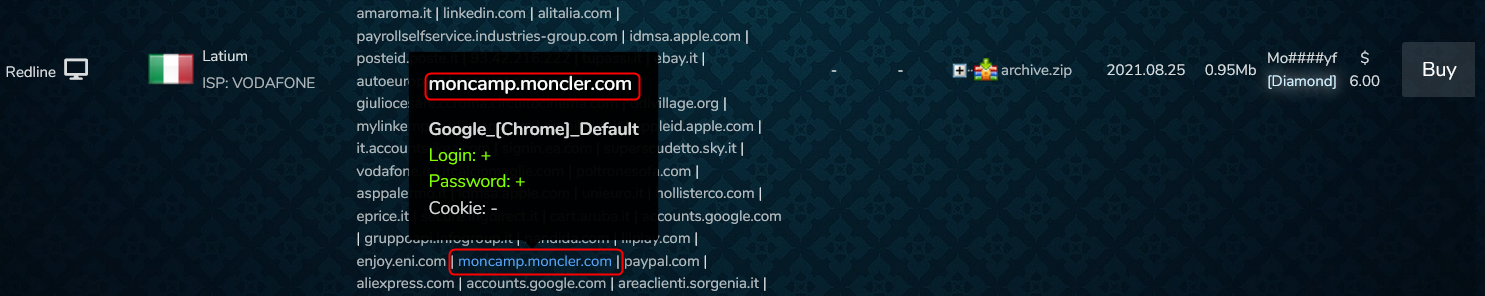
When fingerprints of an employee of a particular company are stolen and include the login details for the company’s domain, cybercriminals can use them to access the company’s system. We searched data stores, special dark web marketplaces where personal information is offered for sale and we identified a number of stolen fingerprints of Moncler users at prominent data stores in recent months. These included login details to one of the Moncler’s domains.
The following log (in the image below) is linked to Italy, and may belong to one of Moncler’s employees. This information is directly related to the process of monitoring domains on the dark web, which is key to protecting a company’s brand.
Post #2: The trade of Moncler email addresses
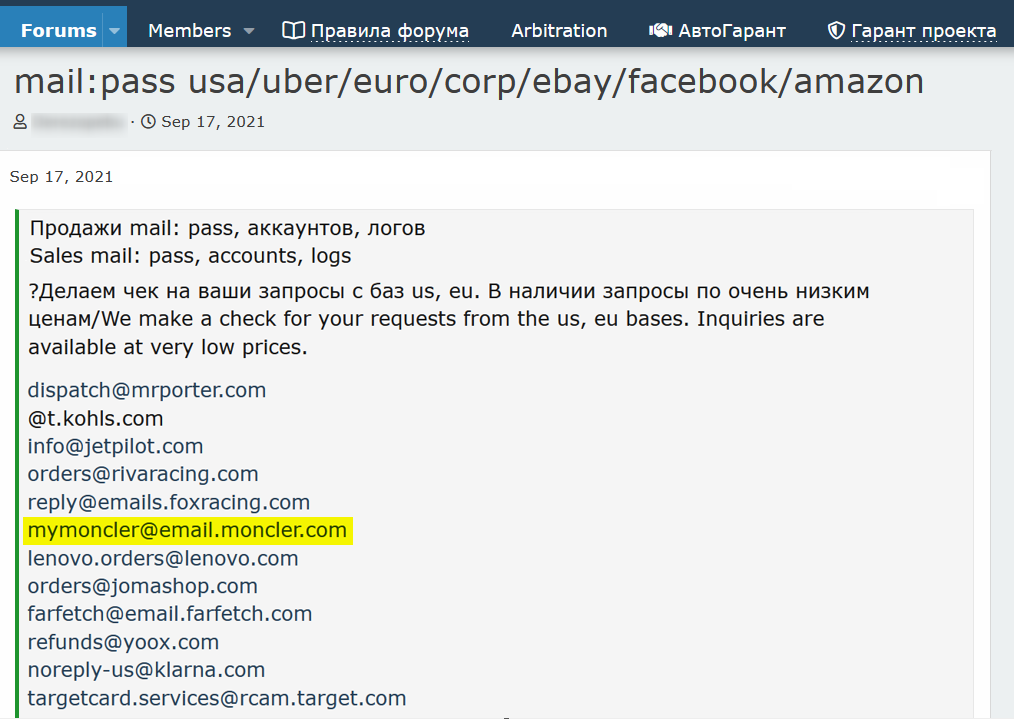
Another potential risk for an organization is phishing attacks. Phishing is an online scam that targets consumers by sending them a fraudulent message that appears to be from a well-known source and tricks them into revealing sensitive information. Using our Cyber API, we found a post on a known hacking forum which was published several months ago (see image below), where a threat actor offered for sale various email addresses, including Moncler’s domain. By using this email domain, cybercriminals can impersonate Moncler and obtain personal and confidential information either from unknowing customers or the company’s employees.
Other suspicious findings: 88 compromised Personally Identifiable Information (PIIs)
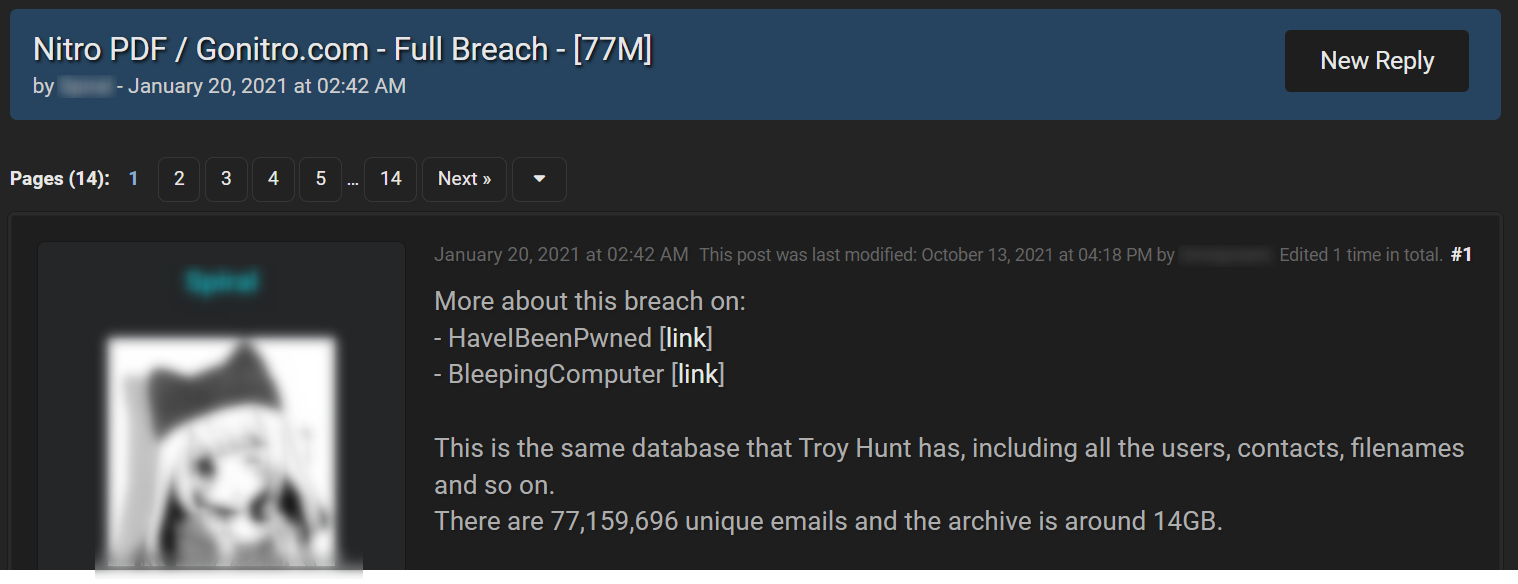
Our cyber team has also checked whether any personal information had been stolen from Moncler employees as a result of previous data breaches, and not necessarily Moncler’s. Using our DBD (Data Breach Detection) endpoint, we searched for Moncler’s domain and found 88 email entities belonging to the company’s employees which are compromised. Most interestingly, there was a leak from Gonitro.com, belonging to Nitro, a PDF software. We noticed that the leak contained many emails linked to Moncler’s domain, which may indicate Moncler employees were using the software.
This is an alarming finding, since accessing employees’ accounts on certain platforms can reveal a lot of sensitive information about the organization, and can result in data breach, similar to the one Moncler recently suffered. If we also consider the probability that some employees use the same passwords for work-related sites, servers and external sites, this type of PII leak can present a real threat to any organization, including Moncler. This is why this step of monitoring leaks of entities is essential to protecting brands from supply chain risks.
https://webz.io/dwp/exclusive-the-posts-moncler-missed-before-latest-data-breach/
Published: 2022 02 08 11:56:35
Received: 2022 02 09 21:50:29
Feed: Webz.io Dark Web Posts All
Source: Webz.io Dark Web Posts
Category: News
Topic: Cyber Security
Views: 17
