Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Revealed: Compromised AWS Accounts Ahead of FlexBooker Leak
published on 2022-01-25 17:51:20 UTC by yafitContent:
FlexBooker, the cloud-based booking and scheduling software, recently suffered a data breach. Using our Cyber API, we were able to find the first post relating to the leak on the popular hacking forum “Exploit”, a famous Russian forum on the TOR network.
The post was published by “Uawrong”, a new emerging hacking team responsible for several recent leaks such as Racing.com and rediCASE Case Management Software, from the Redbourne Group which supports public health networks across Australia, resulting in a leak of patient data.
Webz.io detected the leak soon after it was published, which is now available through our Data Breach Detection API.
The leak includes information belonging to 3.7 million Flexbooker customers. The compromised information includes names, phone numbers, email addresses, passwords, and in some cases, partial credit card information.
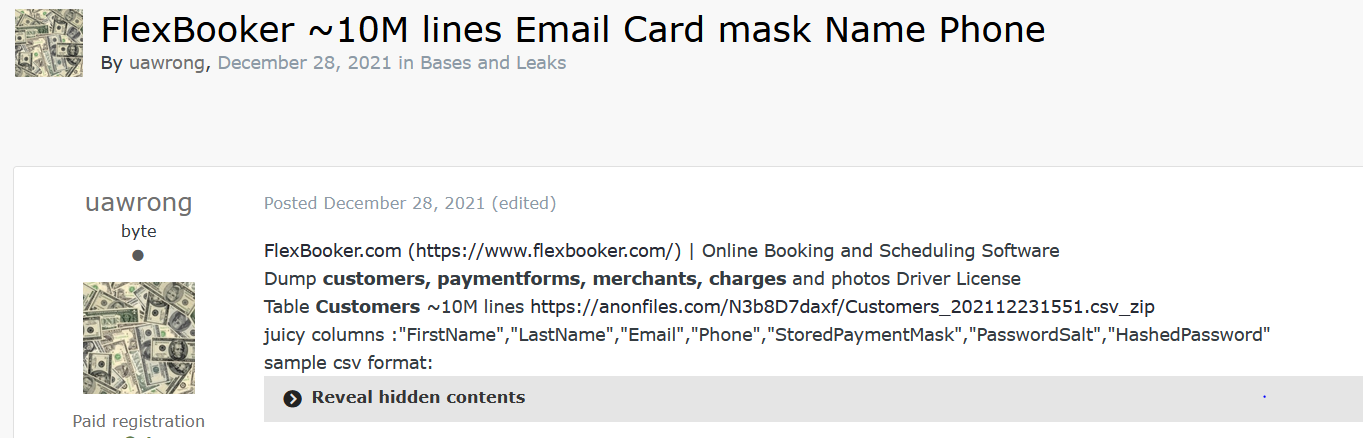
According to an official announcement Flexbooker released, the leak was caused due to a compromised account: “On December 23, 2021, starting at 4:05 PM EST our account on Amazon’s AWS servers was compromised, resulting in our temporary inability to service customer accounts, and preventing customers from accessing their data”.
This is not the first time we see how one compromised account can lead to serious breaches, including the hacking into Colonial Pipeline, the largest fuel pipeline in the U.S., and other risks to companies. Unwanted access in the form of compromised accounts is one of the most accessible options available on the dark web. Large volumes of leaked accounts can be found in “data stores”, marketplaces for stolen data such as login credentials, cookies, PIIs, and others. Data breaches are published on a daily basis in hackers forums, marketplaces and chatting applications such as Telegram.
A quick search of leaked or traded AWS accounts in our API yields over 4,000 results from the past two years. One of them could be the Flexbooker account. Tracking these compromised accounts can help prevent the next AWS leak.
https://webz.io/dwp/revealed-compromised-aws-accounts-ahead-of-flexbooker-leak/
Published: 2022 01 25 17:51:20
Received: 2022 02 09 21:50:31
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 14
