Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.What Threats are Lurking for Executives in the Dark Web?
published on 2022-02-08 15:49:49 UTC by Avishag YulevichContent:
Security issues are increasingly becoming digital, and VIP and Executive protection is no different. In today’s day and age, high profile people can no longer solely rely on security teams to protect them from physical threats. As we monitor the dark web, we are witnessing more and more online threats against executives that can evolve into cyber crimes and even worse, into physical threats to them and their families.
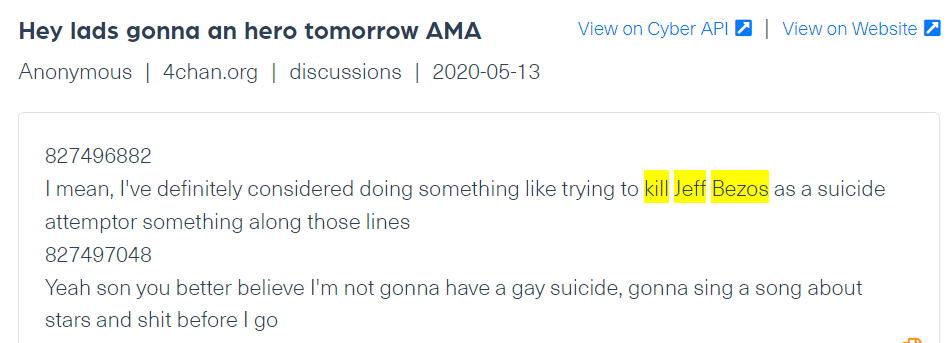
A post against Jeff Bezos, founder and executive chairman of Amazon crawled from 4chan, on Webz.io’s Cyber API 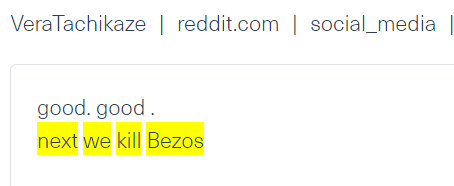
A post against Jeff Bezos, founder and executive chairman of Amazon crawled from Reddit, on Webz.io’s Cyber API
What threats are executives and VIPs facing on the dark web?
There are two main threats to executives you can monitor on the dark web:
- Incitement and recruitment – Social media and online forums have transformed the way discussions can run behind closed doors but still admit everyone who wants to join in. Since many mainstream social media platforms and forums have restricted inciting and extremist discussions, many who seek to incite, radicalize or recruit people for violent attacks have moved to other outlets like alternative social media platforms, anonymous forums, and chatting applications, where users can write freely without being barred. By monitoring our dark web feeds, we have been able to find many discussions that incite hatred towards high profile executives and plan physical attacks (see examples below).
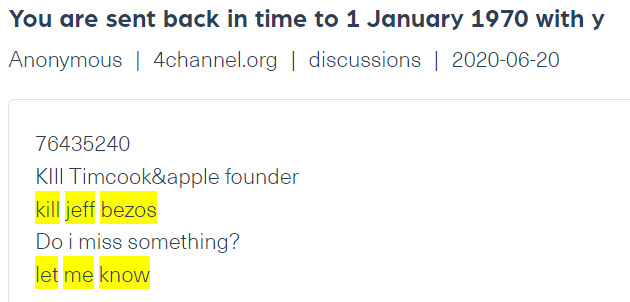
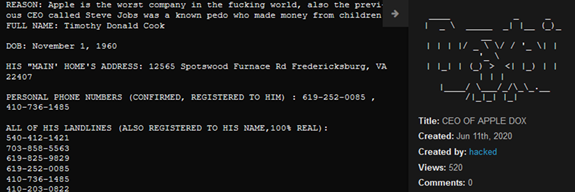
A post against Tim Cook, Apple’s chief executive officer crawled from 4Chan, from Webz.io’s Cyber API 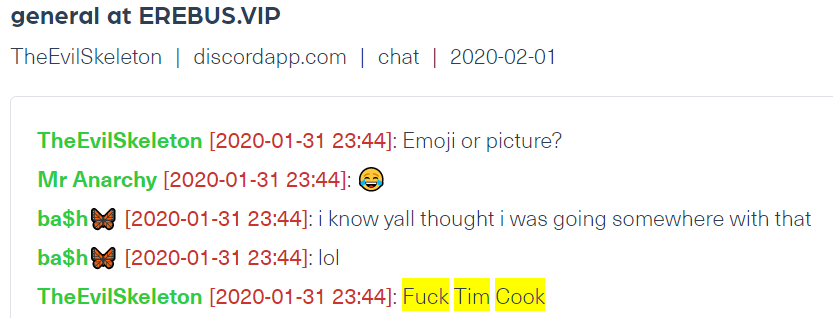
A message against Tim Cook, Apple’s chief executive officer crawled from Discord, on Webz.io’s Cyber API
- Weaponizing leaked credentials – Like any other businesses, cybercriminal businesses also publicize their services against executives online, only they’ll take extra measures to hide. We find such “ads” in hidden dark web marketplaces, paste sites, closed hackers forums and chatting applications. Their services include leaking or selling PIIs, or unwanted access to online assets.
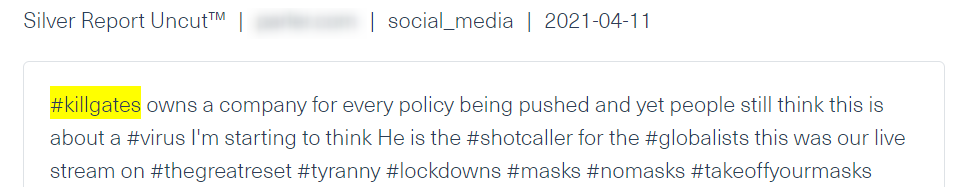
The Case of #KillGates
Lets take for example Bill Gates. Since the Covid-19 outbreak, Gates and his foundation have been at the center of anti-vax conspiracy theories around vaccinations. We find hate speech against him on a daily basis on alternative social media platforms, anonymous forums, and chatting applications. On alternative social media platforms, Gates has been given a popular hashtag called “#killgates”, which is used among extremist online threat actors. In the two examples below, we can see posts referring to Bill Gates, without even mentioning his name.
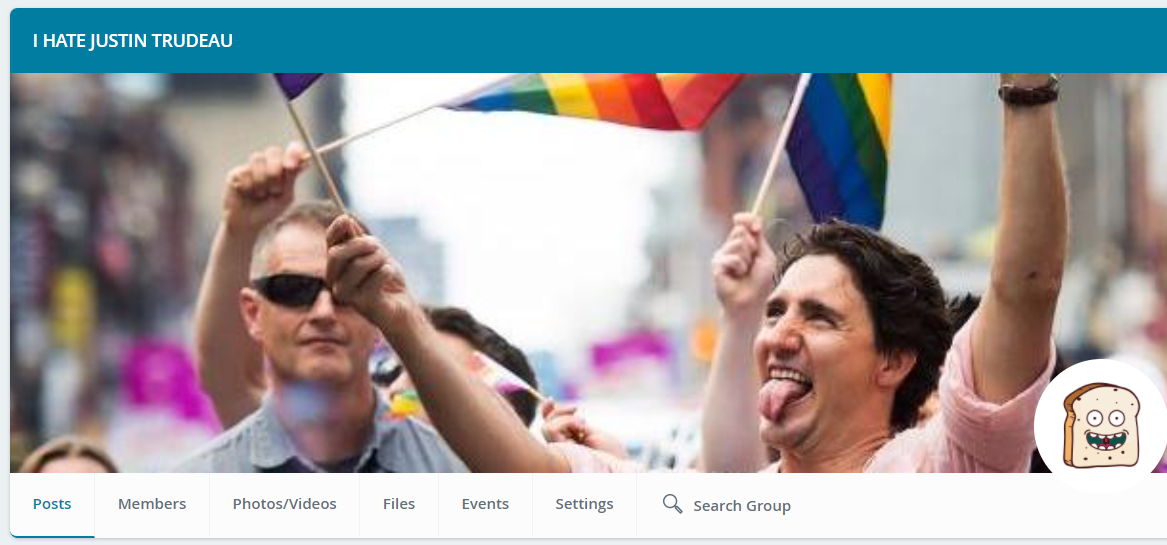
Private Hate Groups
In addition to dedicated hashtags and nicknames, we detect, on a regular basis, private hate groups and pages dedicated to executives. For example, we identified a private hate group called “I hate Justin Trudeau” targeting Canada’s current Prime Minister on an alternative social media platform.
How can you find threats to executives in the deep and dark web and how to monitor them?
As mentioned before, most of the threats to VIPs and executives can be found in social media platforms, paste sites, image boards, extremists forums, chatting applications, hackers forums and dark web marketplaces. It is important to monitor all of them. But that’s not all.
Because each case has different needs and background, it requires special customization to ensure a thorough and real time monitoring. To do that, we often customize the queries, our data and some of the sources we crawl.
There are several reasons to customize searches:
- Threat actors are constantly creating new terms and nicknames related to the executives they target.
- Nicknames are often part of a trend, and they keep evolving and changing.
- New related closed groups, pages and hashtags keep emerging everyday. We use these new sources and words together with variations of the personality name, to get a wider range of threats that would not have been found otherwise.
Customization is the key to tracing threats and preventing the next attack against executives and VIPs.
All these insights and examples are just the tip of the iceberg when it comes to online executive threat detection. As these dangerous activities keep growing, evolving and expanding to new spaces, it is vital to closely monitor the right places at the right time.
https://webz.io/dwp/what-threats-are-lurking-for-executives-in-the-dark-web/
Published: 2022 02 08 15:49:49
Received: 2022 02 09 21:50:32
Feed: Webz.io Dark Web Posts Web Intelligence
Source: Webz.io Dark Web Posts
Category: News
Topic: Web Intelligence
Views: 3
