Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Revealed: The Warning Signs Ahead of Mass Breach of E-Commerce Sites
published on 2022-02-22 18:00:25 UTC by Yuval ShibiContent:
On Feb 8, Dutch security company Sansec announced it detected a mass breach of over 500 e-commerce stores running Adobe’s 12-year-old Magento 1 e-commerce platform.
Even though Adobe stopped supporting the Magento platform in June 2020, and strongly urged users to update their version, according to reports 95,000 e-commerce sites continue to use the older version. Over 500 of them have been recently hacked.
The breach is believed to have been caused by a payment skimmer, which mimics the website’s design by using a transparent input field over the real one checkout page, loaded from the domain naturalfreshmall.com. This means the criminals obtained users’ PIN numbers from debit or credit cards when they paid for services on this domain.
What did the hackers use to breach Magneto’s platform?
It has been reported that the threat actor used injections, a malicious code which is injected into a system and changes its operation, to attack Magento’s platform and gain control of the different e-commerce stores.
The two types of injections that were used are:
- SQL injection – Also referred to as SQLI. A common attack vector that uses malicious SQL code for backend database manipulation to access information that was not intended to be displayed. This information may include sensitive company data, user lists or private customer details.
- Backdoor – A malware that bypasses normal authentication procedures in order to gain access to a system. This enables remote access to the application’s resources, such as databases and file servers, allowing perpetrators to execute system commands and update malware remotely. Several Backdoor tutorials and related discussions are found on the dark web and covered by our systems every day.
Following the reports, we have searched the deep and dark web to see whether we could find any suspicious activity around the Magento 1 platform. We were surprised to find various posts and mentions that should have raised a red flag months before the attack.
Early indications ahead of recent Magento breach
An alarming mention of an SQL injection
The post below, published over six months ago on the TOR network, discusses an SQL injection that can be used to inject malicious code into Magento 1. The CVE (Common Vulnerabilities and Exposures) in this case is CVE-2021-21024, which was also found in previous versions of Magento in 2019 and 2020. Although it is hard to determine whether this vulnerability is the exact one that was used in this recent attack, the fact that we could find this type of vulnerability traded in the dark web is an alarming sign that should have been monitored in real time.
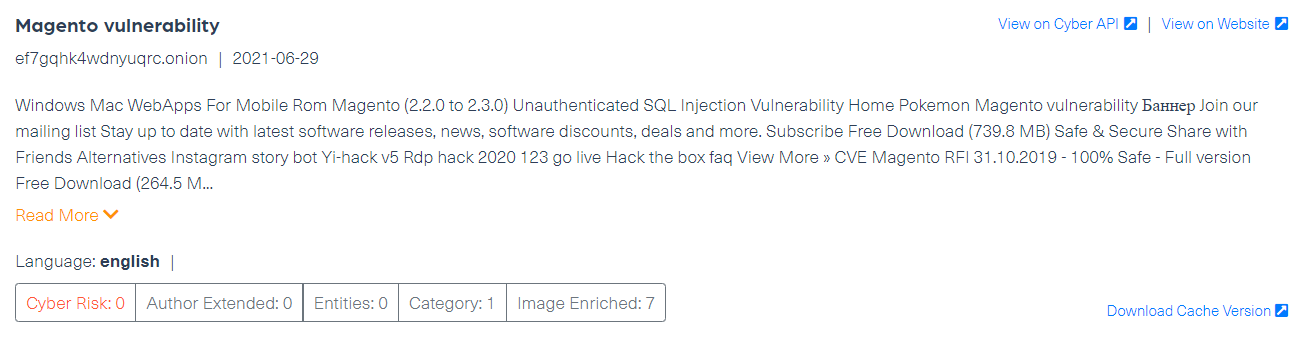
The trade of shell backdoor
According to reports, the hacker left 19 backdoors on the system, used to run any PHP code on the compromised sites. We found several posts by threat actors who traded webshell backdoor to Magento’s platform. A backdoor shell is a malicious piece of code that can be uploaded onto a site to gain access to files stored on the site. Once it is uploaded, the hacker can use it to edit, delete, or download any files on the site, or upload their own.
The first example is from dark web hacking forum Exploit, published in May 2021:
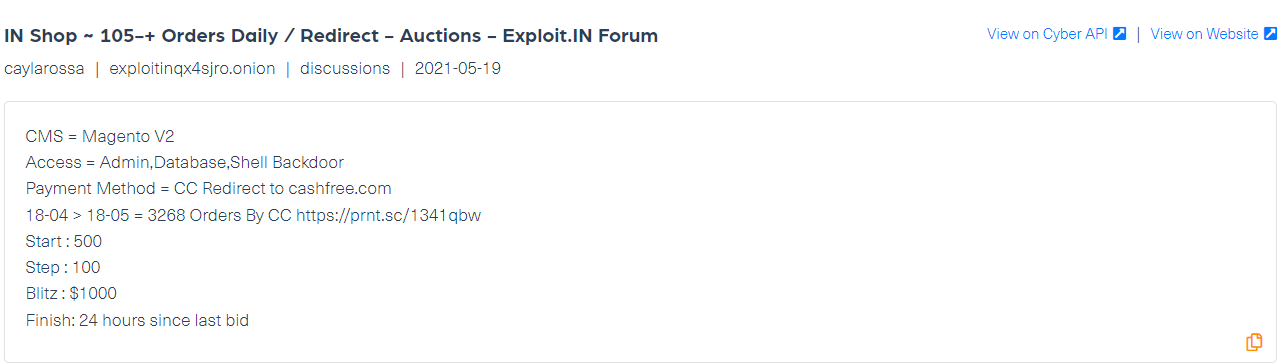
We found another post published by a threat actor who was selling webshell to Magento’s platform on the popular hacking forum Raidforums:
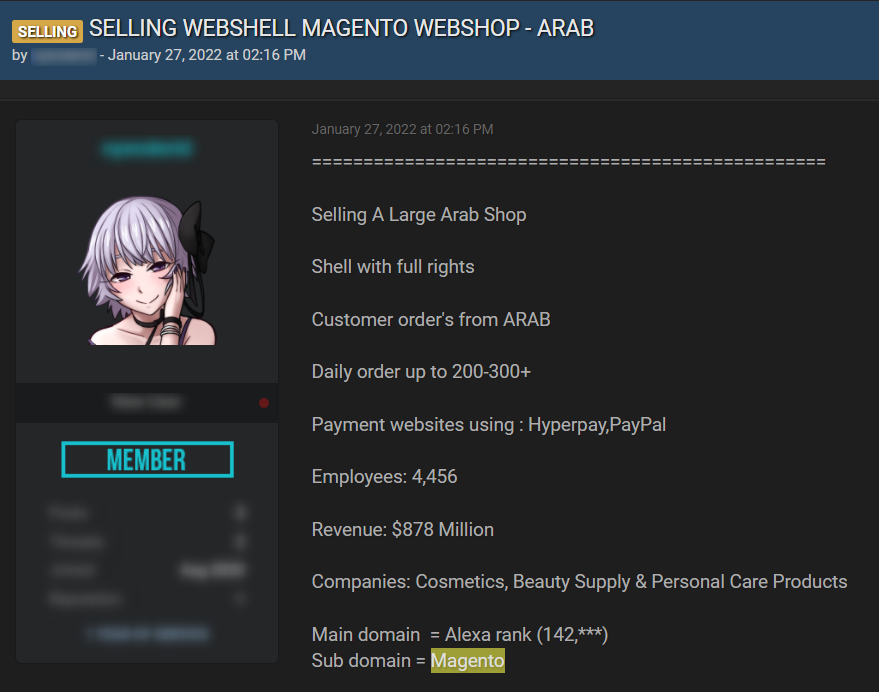
The last example is taken from Magbo, another dark web marketplace where actors post shell backdoors on a daily basis, allowing access to a wide range of websites and services. When a backdoor is attributed to an entity, in this case – Magento, we consider it to be an early indication that the software is at risk of a data breach.
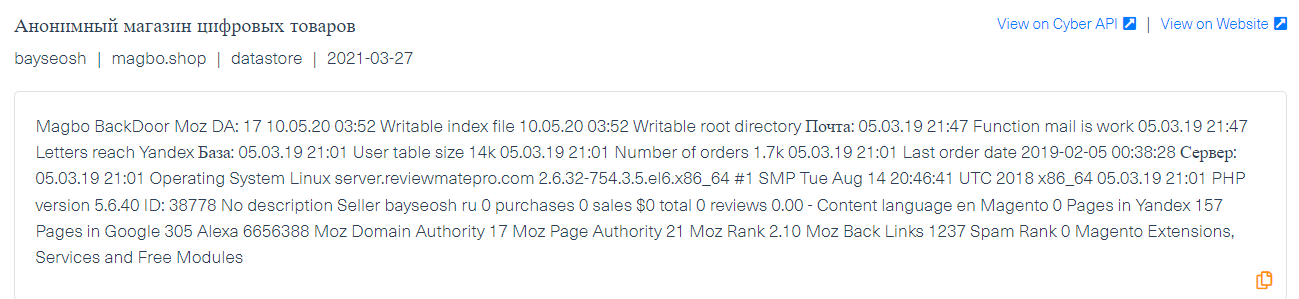
What data was leaked following the Magneto breach?
We used our Cyber API to search for leaked information following this latest Magento breach. We were able to find various leaks of user and admin data belonging to different e-commerce websites.
Below you can find an example of one of these posts, listing customer emails, names and user IDs, that were retrieved from mediaxpress.net, one of the hundreds of domains that were breached.
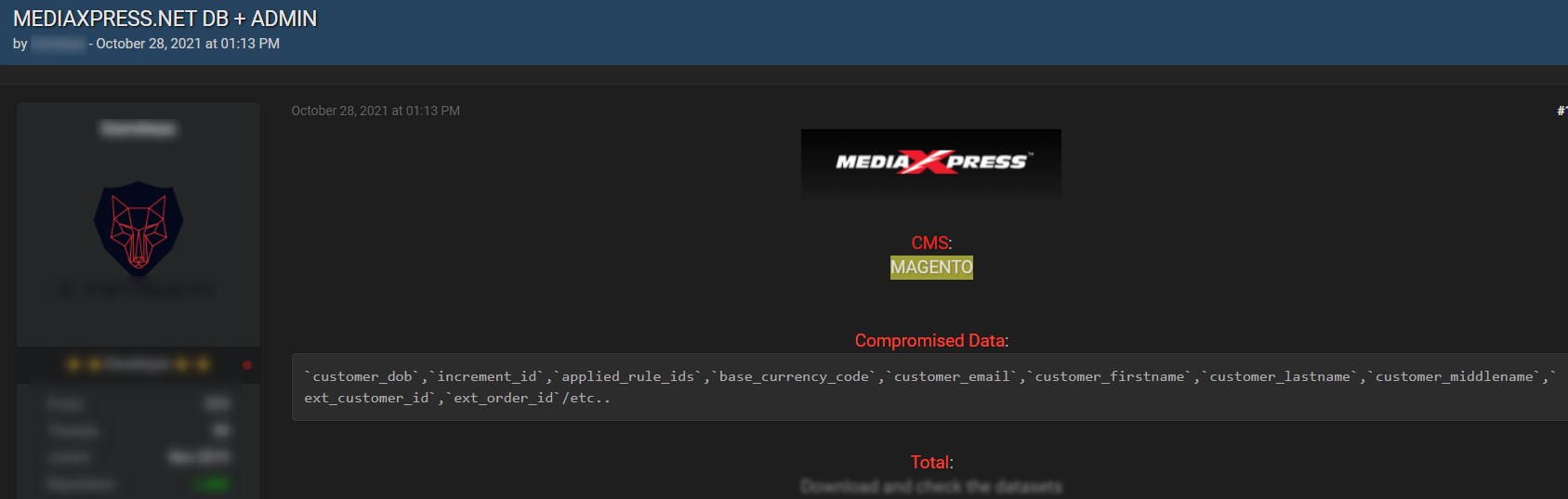
In addition to this type of posts offering the leaked data for sale, we have also been able to find posts offering stolen Magento user accounts on the hacking forum Exploit – after the breach occurred.
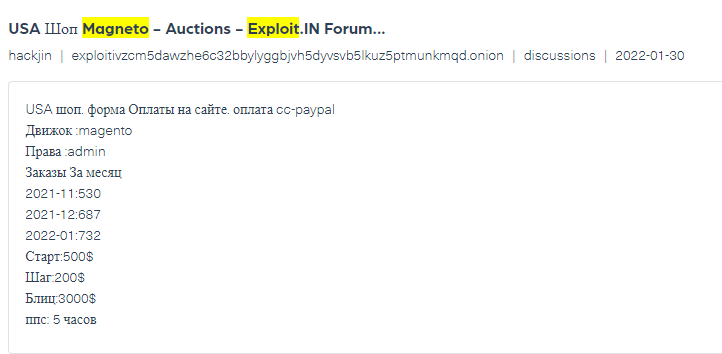
The amount of information we found before the breach is the perfect example of supply chain risk that can be prevented with close monitoring of dark web activities and discussions. As many companies continue to use various third party services, their need to track the trade of these vulnerabilities before they are exploited only increases. It is the only way to stay ahead of hidden threats and take action in real time to prevent hacking attacks in the future.
https://webz.io/dwp/revealed-the-warning-signs-ahead-of-mass-breach-of-e-commerce-sites/
Published: 2022 02 22 18:00:25
Received: 2022 02 22 18:50:50
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 18
