Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Exclusive: The Top 10 Companies Facing Risks in the Dark Web
published on 2022-02-22 19:22:14 UTC by Liran SoraniContent:
Hacking forums remain the main place where hackers trade information, techniques, malicious codes, tools and new compromised assets.
In recent years, we have seen a growing number of mentions of leaked domains in the deep and dark web. Cybercriminals are mostly targeting online and popular brands, and offer everything from log sessions or user credentials to phishing kits and botnet cloud services. All of these are used to breach online domains.
The threat actors are building their reputation but most importantly, they can trade this information for a few dollars to thousands of dollars per item. The risk is high as eventually each account or backdoor can serve as a channel to a bigger breach.
In this post we will reveal the top 10 organizations whose assets were traded and discussed in the deep and dark web over the past six months.
The list is long and includes thousands of compromised organizations, including private companies, Fortune 100 companies and websites.
The most common compromised entity is the account. It is usually traded together with login credentials or cookies for a few dozens of dollars per item. Once it’s sold or leaked it can be used by more sophisticated hackers to breach highly confidential or sensitive information or perform a spear phishing, an email or electronic communications scam targeted against other servers in the organization.
To determine which companies are at greater risk of a breach or a cyber attack, we searched for the top 10 domains that were compromised over the last 6 months.
In the list below you can find the top 10 domains at risk:
| Company | Domain | No. of Mentions | Service Type | Potential Risk |
|---|---|---|---|---|
| accounts.google.com | 24,928 | Social Service | Phishing, doxing, blackmailing, financial assets at risk, business compromised | |
| instagram.com | 20,107 | Social Service | Phishing, doxing, blackmailing, financial assets at risk, business compromised | |
| YouTube | youtube.com | 19,892 | Social Service | Phishing, doxing, blackmailing, financial assets at risk, business compromised |
| twitter.com | 16,321 | Social Service | Phishing, doxing, blackmailing, financial assets at risk, business compromised | |
| facebook.com | 14,158 | Social Service | Phishing, doxing, blackmailing, financial assets at risk, business compromised | |
| Debrid-Link | debrid-link.com | 13,169 | File Hosting | Sensitive documents at risk, financial risk |
| Virus Total | virustotal.com | 11,648 | Antivirus Service | A part of phishing process |
| Microsoft | login.live.com | 11,218 | Email Service | Sensitive documents s at risk, financial risk, business compromised |
| Discord | discord.gg | 8,730 | Social Service | Phishing, doxing, blackmailing, financial assets at risk, business compromised |
| Sellix | sellix.io | 8518 | Online Retail | Phishing, financial Risk |
Most of the top compromised domains are either social accounts or content-service based (file hosting, mail service and others). In most of the cases, this will be the first step a hacker takes to gain access to a highly sensitive information by using phishing attack, account takeover (ATO), ransomware attack and others.
The following is an example from Russian Market (stealer logs section):
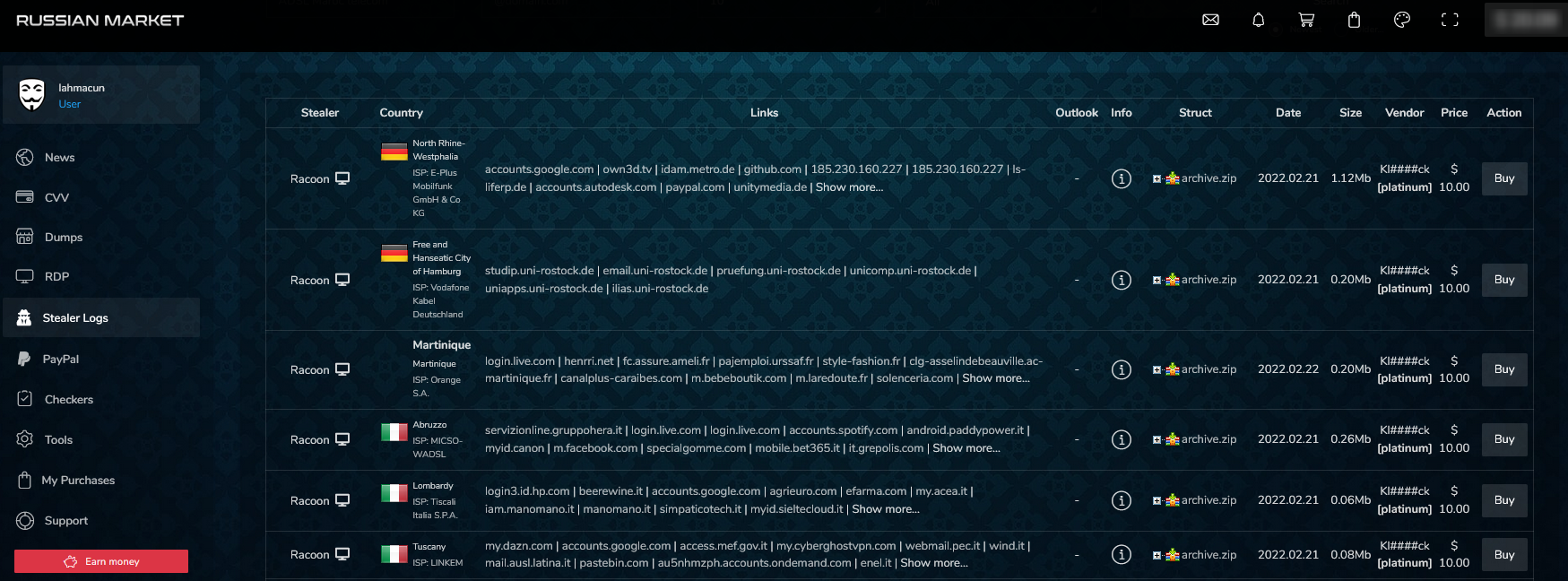
Most of these accounts are associated with enterprises and organizations so the impact of a compromised domain is not only affecting individuals but also businesses.
Below we list an example from Webz.io’s repository which shows how a compromised domain is being traded in BHF.IO, a hacking forum that offers leaked assets and malicious cyber services.
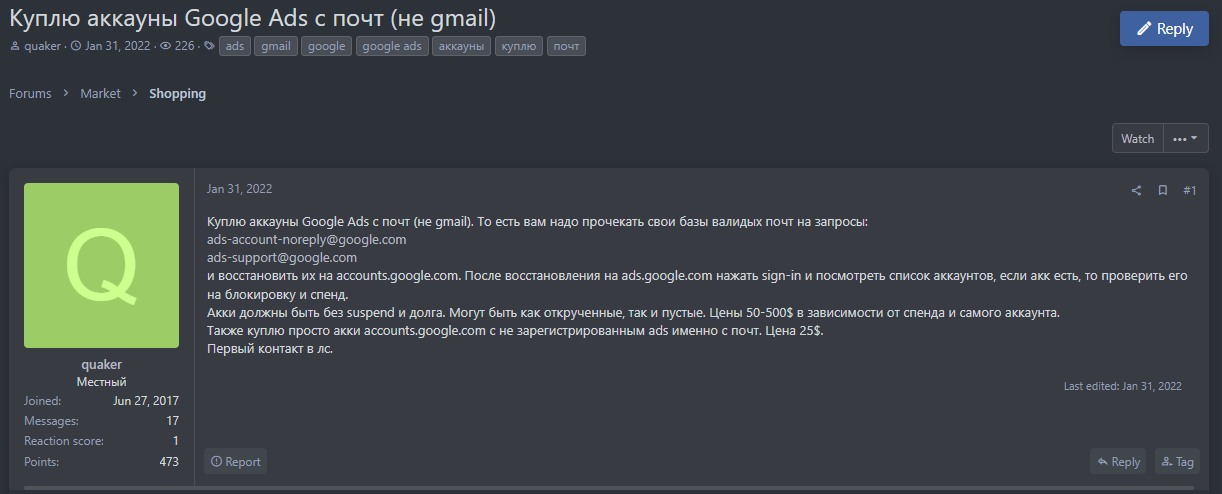
Using Webz.io, companies can regularly monitor the deep and dark web to trace emerging cyber threats and take action to mitigate financial and reputational risks in real time.
https://webz.io/dwp/exclusive-the-top-10-companies-facing-risks-in-the-dark-web/
Published: 2022 02 22 19:22:14
Received: 2022 02 22 19:30:50
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 17
