Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Dark Web Discussions on Log4j Vulnerabilities
published on 2022-01-25 17:38:28 UTC by Liran SoraniContent:
Recently, the global media has been covering the implications of critical Log4j vulnerabilities extensively. The Log4j, an open source software provided by the Apache Software Foundation, records errors and routine system operations and communicates diagnostic messages about them to users and system administrators
This software has been used by many organizations over the years, including: Amazon, Apple, iCloud and others. The vulnerability includes a code injection through user configuration settings that can create a reverse shell out of the target server or control the target in other ways.
Our cyber team decided to take a closer look at these vulnerabilities in the dark web.
While the vulnerability was first recorded as a CVE on November 26, 2021, the first real Zero-Level alert was applied only on December 10, 2021.
Using our dark web data, we tracked high activity around the same time. We were able to find discussions between threat actors over the Log4j exploits in technical groups on Telegram and on 4Chan on the very same day, on December 10 (see the graph below) .
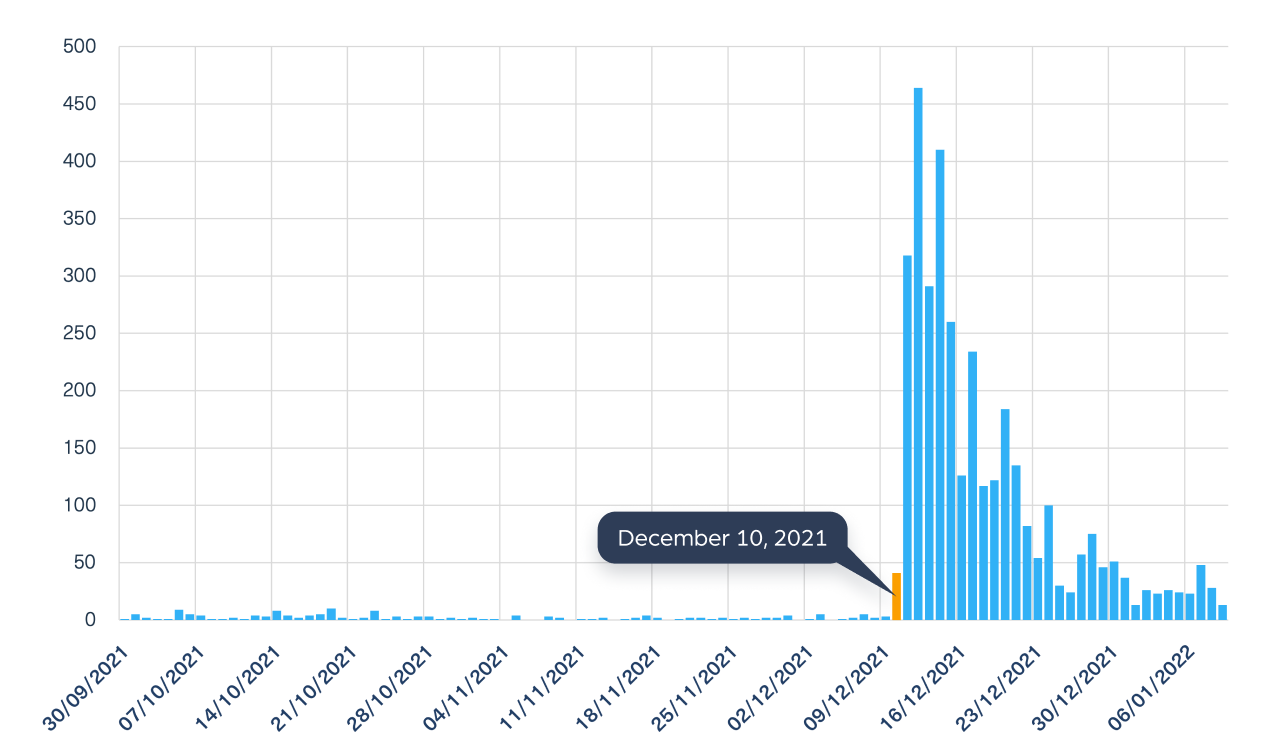
We also took an even closer look and sorted these discussions on the Log4j vulnerability on the dark web according to CVE names:
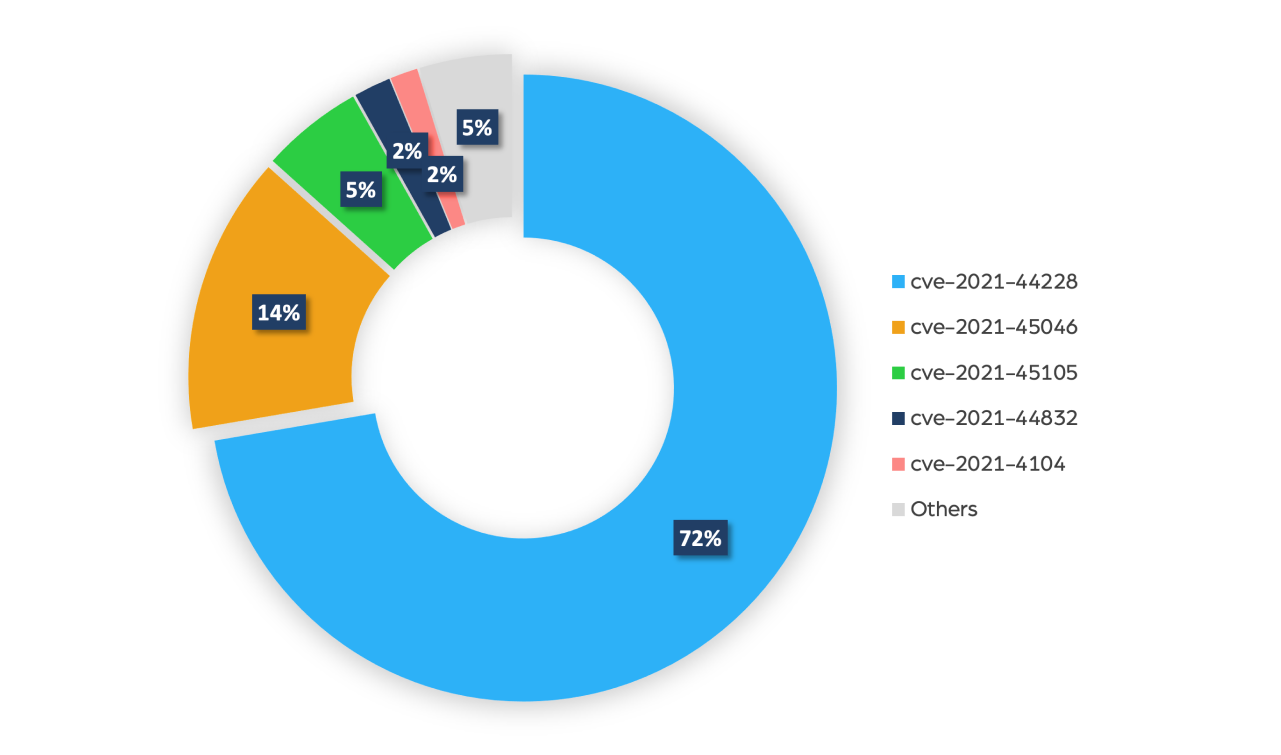
By looking at the pie chart above, we can clearly see that the vast majority of the discussions circle around the latest, high risk CVE-2021-44228, a critical configuration vulnerability. About 14% of them were about CVE-2021-45046, which is an incomplete fix to the CVE-2021-44228.
This high level of activity is a clear indication that servers around the world are at high risk, forcing many to take immediate action and run updates using the latest patches to mitigate this risk.
This type of data helps MSSPs and threat intelligence systems create alerts and notify their customers by identifying immediate risks that are used by criminals on the dark web.
https://webz.io/dwp/behind-the-news-dark-web-discussions-on-log4j-vulnerabilities/
Published: 2022 01 25 17:38:28
Received: 2022 02 23 08:31:17
Feed: Webz.io Dark Web Posts Web Intelligence
Source: Webz.io Dark Web Posts
Category: News
Topic: Web Intelligence
Views: 19
