Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.“I want to be a volunteer, download my resume to see what I can do.”
published on 2022-03-02 14:31:19 UTC by fionabailContent:
And what I can do is infect you with malware if you click that link.
Charities are key targets for cyber criminals, not only because they receive money, which is generally the motive behind cybercrime, but because they can lack the technical expertise to protect their systems. This means that when cyber criminals are looking for vulnerabilities, Charities are likely to be found within the cross hairs.

The most common form of cyber attack is the phishing email.
According to the Cyber Breaches Survey 2021, 79% of cyber-attacks are identified as phishing by Charities and some are reporting attacks every week.
What is phishing?
Phishing is a catch all term for any attack where the criminal pretends to be someone else. So, this could be a telephone call from “your bank”, a text message about “your delivery” or an email about “your unpaid invoice”.
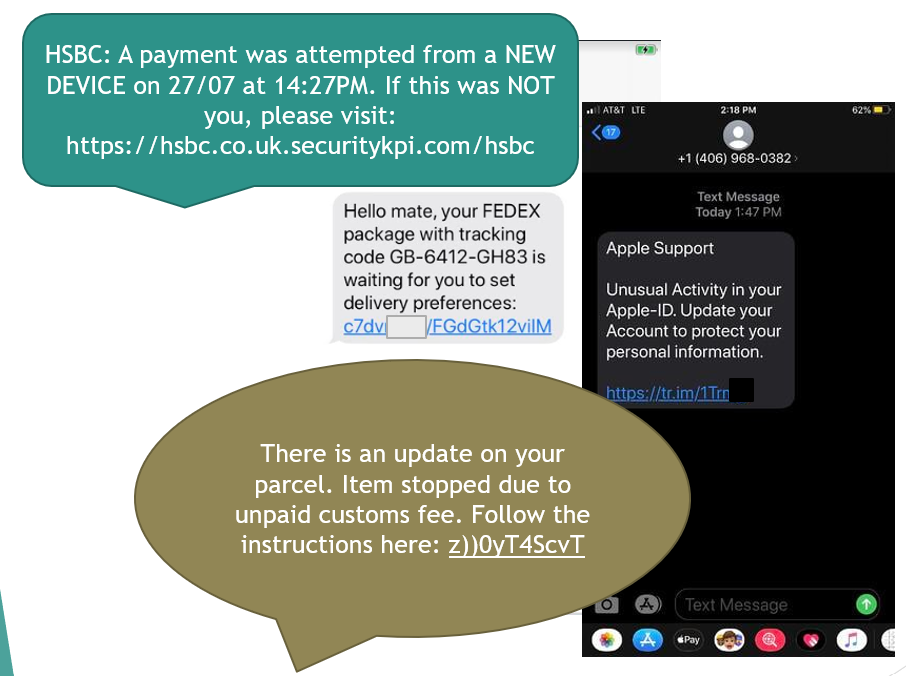
What has changed with phishing attacks?
Previously many phishing attacks were easy to spot, with bad spelling and grammar and coming from an email address that was clearly not the supposed senders. But this has changed, with criminals becoming very aware of how we are using technology and what makes us act before thinking.
Spear phishing, where emails are personalised to the recipient, are becoming the norm, with data breaches giving criminals access to personal information we thought was safe.
Have you checked to see if you and your charity has been involved in a data breach and what criminals might know about you? Visit haveibeenpwed.com and check your email and telephone number. You might be surprised at what information there is about you.

What should I look for in a phishing email?
If a message contains any of the following, really think before you click:
- Urgency “you must do this now” – here the attacker is trying to induce you to panic so that you don’t question the action being asked of you
- Authority – messages appearing to come from a boss, colleague or company you engage with regularly, or with information they shouldn’t have unless they are genuine (your IP address for example)
- Mimicry – attackers send messages that exploit your daily habits such as “please review your calendar entry – click here”
- Curiosity – enticing you with something like “breaking news”
What can I do to protect my charity from phishing attacks?
Your staff can be the best defence against phishing attacks. Being confident in recognising and reporting phishing attacks is key. Make staff awareness a priority. The NCSC has a free online awareness package which could be a great way to introduce the subject to new starters or volunteers.
Make sure staff know how to report a phishing attack.
Have a plan to deal with a successful attack. Sophisticated phishing campaigns can be incredibly difficult to spot, and no one can be perfect 100% of the time, so making sure your staff are able to report falling victim of a phishing campaign is essential. You want them to report as soon as they realise, rather than waiting until a forensic investigation identifies it.
The National Cyber Security Centre (NCSC) have created an enterprise Outlook add-in for staff to be able to report email phishing directly from their email box. The NCSC will the actively seek to disrupt the criminals sending these messages, protecting you from them as well as the wider community.
And you can report more than emails.
- Reporting a suspicious website - https://www.ncsc.gov.uk/section/about-this-website/report-scam-website.
- Reporting a suspicious email – forward to report@phishing.gov.uk
- Reporting a suspicious text message – send to 7726. This free-of-charge short code enables your provider to investigate the origin of the text and take action, if found to be malicious.
Top tips
- Don’t click on links within emails – go to that system independently instead. Then you will go to Microsoft instead of micrs0fft.
- Don’t allow macros to run – these are frequently used to hide malware
- Don’t open attachments that you weren’t expecting or can’t confirm where they have come from
- Always confirm financial transactions independently. So, if you get a change of banking request, call the company up using trusted method (not the ones within the email). And if the finance director really needs money transferring, they won’t mind you double checking to ensure your charity doesn’t lose its donations.
Further guidance & support
The Eastern Cyber Resilience Centre provides both individual and corporate internet discovery so you can see what information could be used to craft that phishing attack. We also provide Staff Awareness Training, but did you know your local police protect officer might be able to do this too? We train and mentor local university students, so when we say affordable, it really is. Find out more here.
The Eastern Cyber Resilience Centre is a not-for-profit membership organisation, run by policing, with the intention of increasing cyber resilience of SMEs within the East of England.
You can contact the Cyber Resilience Centre for guidance and support through our e-mail enquiries@ecrcentre.co.uk or use our online booking system to make an appointment with one of our team.
We also provide free guidance on our website and we would always encourage you to sign up for our free core membership. Core members receive regular updates which include the latest guidance, news, and security updates. Our core membership has been tailored for businesses and charities of all sizes who are based across the seven counties in the East of England.
Policing led – business focussed.
https://www.ecrcentre.co.uk/post/i-want-to-be-a-volunteer-download-my-resume-to-see-what-i-can-do
Published: 2022 03 02 14:31:19
Received: 2022 03 02 14:31:38
Feed: The Eastern Cyber Resilience Centre
Source: National Cyber Resilience Centre Group
Category: News
Topic: Cyber Security
Views: 13
