Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.The Russia-Ukraine Cyber War in the Deep and Dark Web
published on 2022-03-09 08:53:46 UTC by Hagar MargolinContent:
Since the start of the war between Russian and Ukraine, many have referred to it as the first large scale hybrid war, where the warfare involves both cyber attacks and boots on the ground. Already days before the first Russian forces entered Ukraine, cyber attacks linked to Russia targeted Ukrainian sites. These attacks continued as the war evolved, and were followed by counter attacks against Russian sites.
The majority of this cyber war is conducted by Advanced Persistent Threat (APT) groups, dozens of collectives such as hacktivists, hacker groups, and known ransomware gangs including Conti and ComingProject. Each of them has sided with either Russia or Ukraine over the past weeks.
In addition to using social networks to communicate with the public, many of these groups have turned to the dark and deep web as a safe space to coordinate attacks against specific sites or chat channels associated with either Russia or Ukraine, often in an effort to take them down.
Which deep and dark web platforms are used by hacker collectives?
Many hacker collectives use platforms such as popular hacking forums, paste sites, chat applications such as Telegram and dedicated hacking sites built specifically to support the cyber war efforts of either side.
These platforms are used for:
- Leaking of sensitive information belonging to the other side, including those of government agencies, the militaries of the two countries, political bodies, private companies and other groups that identify with either Russia or Ukraine.
- Discussions and planning of future attacks – many discussions involve rallying and inciting people to attack one of the sides.
The main method we use to find these indicators is by monitoring domains and IP addresses of targeted entities.
Suspicious deep and dark web activities ahead of the war
By using our enrichment tools, we monitored domains, and found a rise in discussions on attacks against Russian and Ukrainian targets in the deep and dark web.
A simple search we ran on dozens of thousands of domain addresses associated with Ukraine (such as sites with the “gov.ua” suffix) showed (see the graph below) an increase in the number of mentions of these sites in December and January. This was followed by a huge spike starting in late February when the conventional war first broke. These numbers remain high until today.
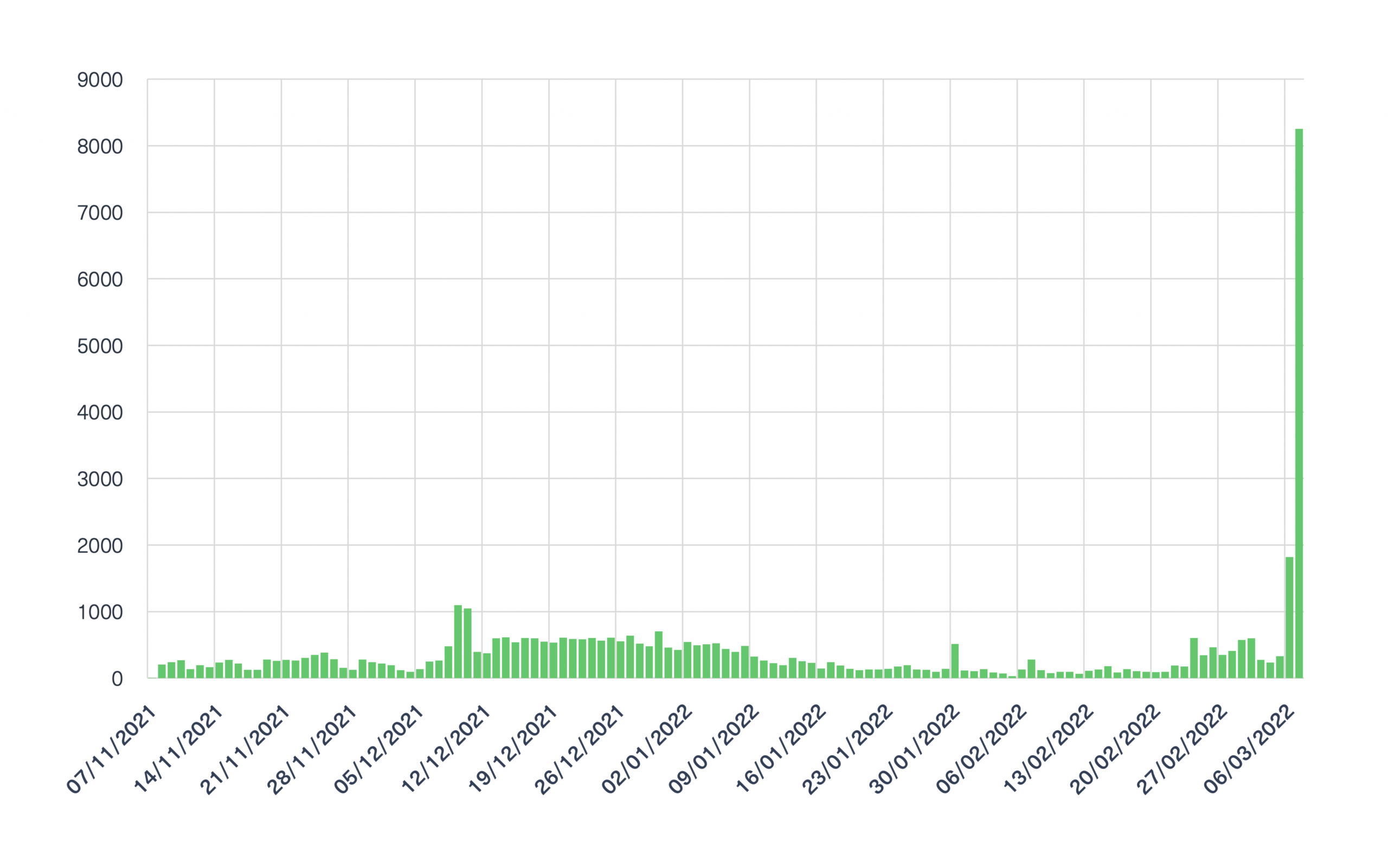
This trend is a clear indication that Ukrainian agencies, organizations and companies were discussed and targeted in the deep and dark web.
If we look closely, the spike in December-January can be linked to the mass cyberattacks launched against dozens of Ukrainian government sites on January 14. It is then no accident that a sharp rise in domain mentions began in December.
In line with the high number of mentions of Ukrainian domains in the graph above, we could find many examples of the content that mentions Ukrainian domains on the dark web, such as the one in the image below:
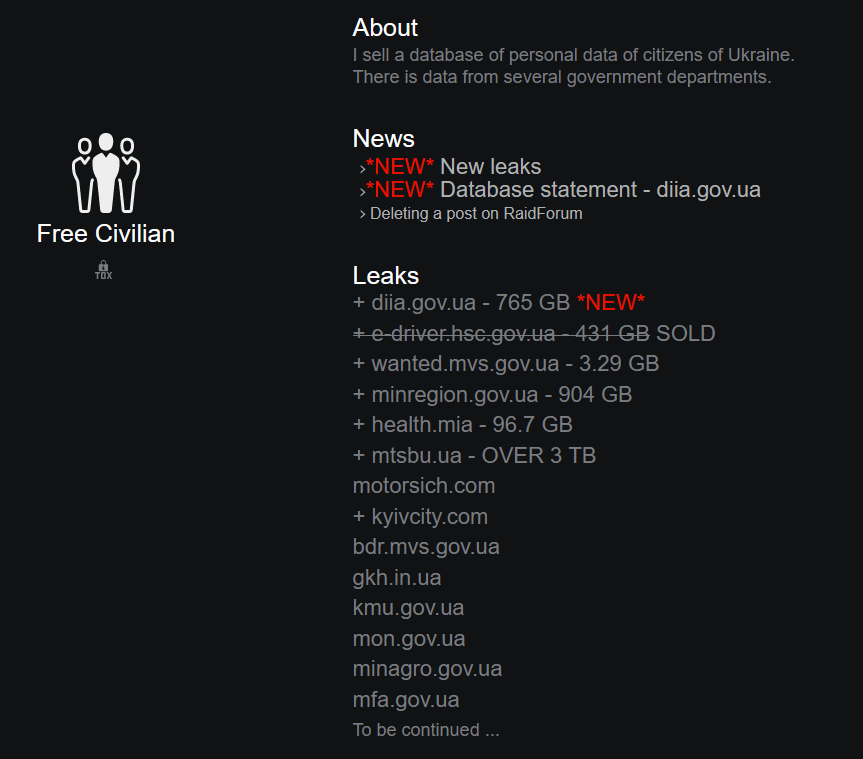
In this post, you can see a list of databases of Ukrainian government ministries and private companies which were compromised as a result of the cyber attacks.
The site, which operates on the Tor network is linked to a hacking group called Free Civilian, the same group that was behind the latest attacks, at least according to the message they left on the Ukrainian sites they had attacked.
Another example is a post on the known Russian hacking forum xss.is (see image below), where a Russian cybercriminal leaked sensitive information belonging to the operational command “North” of the Armed Forces of Ukraine (The Russian term: “ВСУ”).
The domain linked to Ukraine in this post belongs to a Ukrainian document-sharing site, which hosts sensitive Ukrainian military documents.
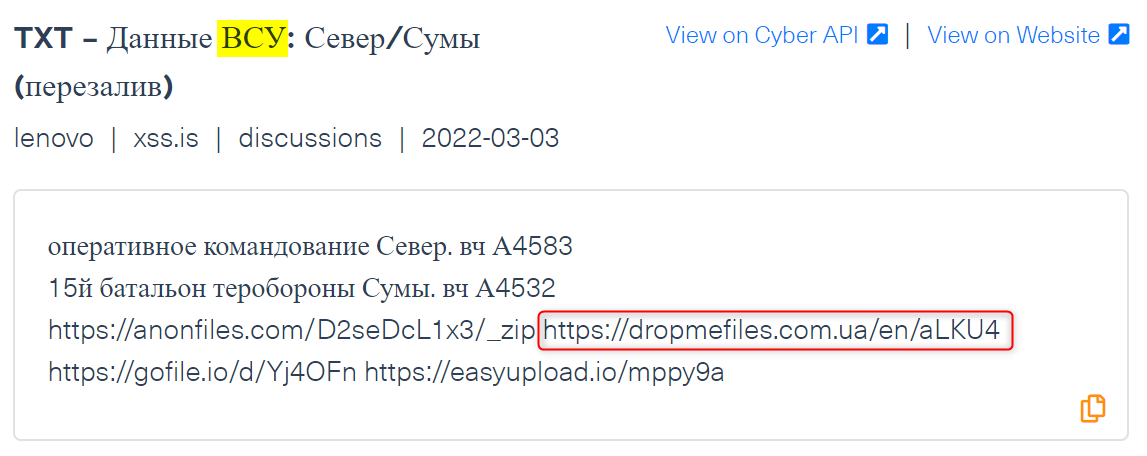
The Russia-Ukraine cyber war in the deep and dark web
As a result of the cyber attacks launched by groups associated either with Russia or with Ukraine, we could find a lot of compromised data and early indicators of other cyber attacks across the deep and dark web.
As mentioned before, monitoring IP addresses plays an important role in the process of identifying early indicators of cyber attacks. Our team searched for Russian IP addresses and we found a significant increase in the number of mentioned across the deep and dark web over the past month:
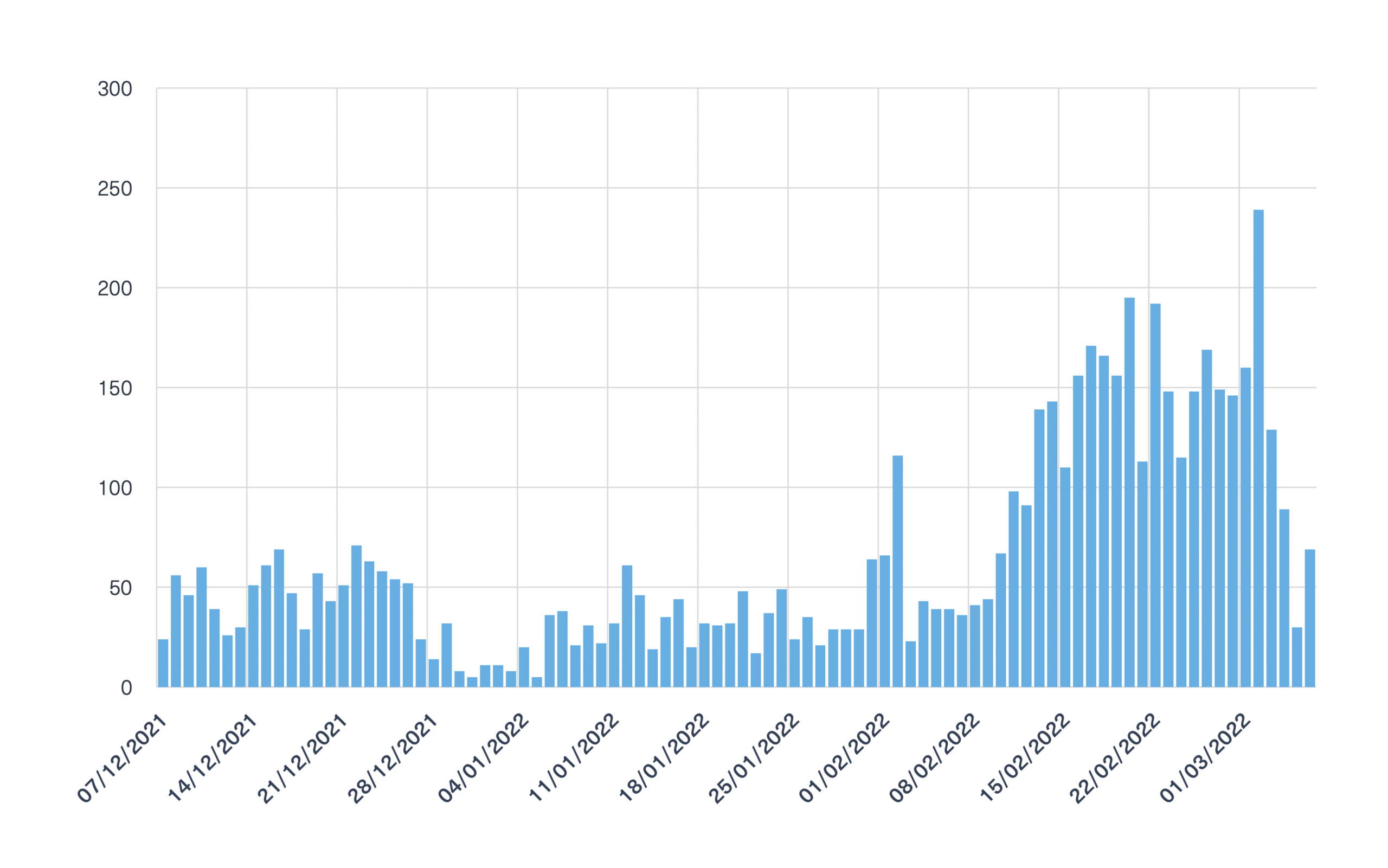
Many of the IP addresses associated with Russian sites were mentioned on paste sites, where a large number of targeted IP addresses can be anonymously distributed.
In the image below, you can see a post that was shared on Pastebin by an author affiliated with a group called Shadow Hunters who announced their plan to target sites associated with Russia:
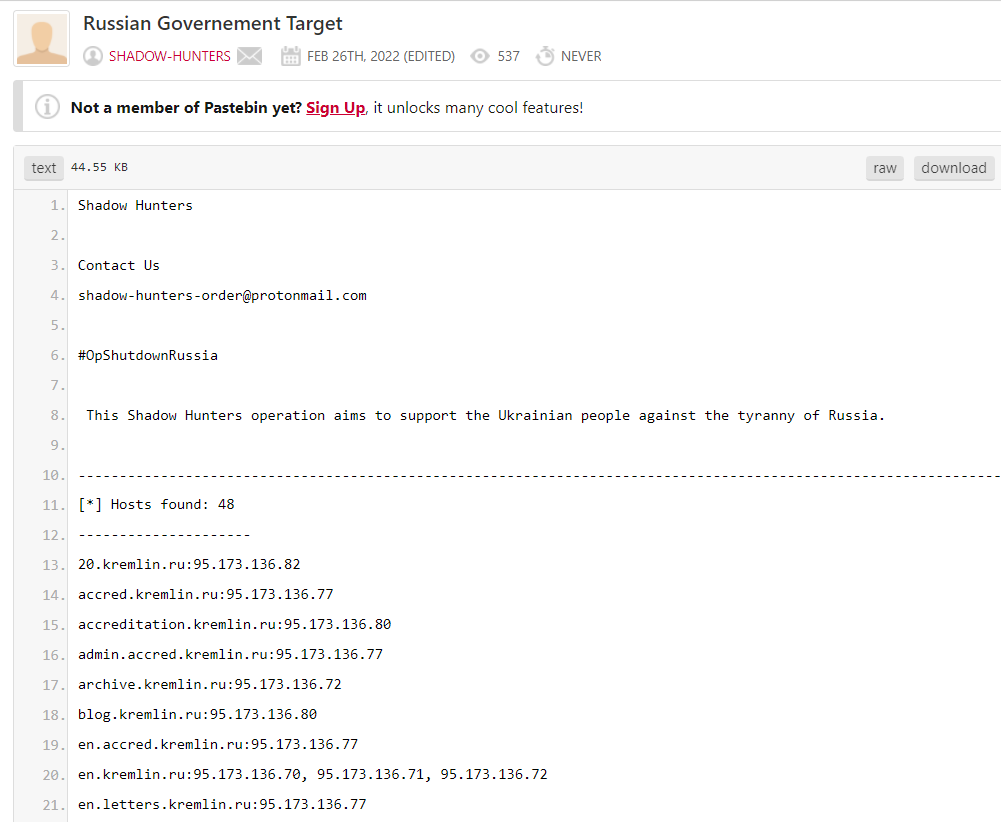
This paste contains hundreds of Russian domains attached with their associated IP addresses, which can be exploited in the future.
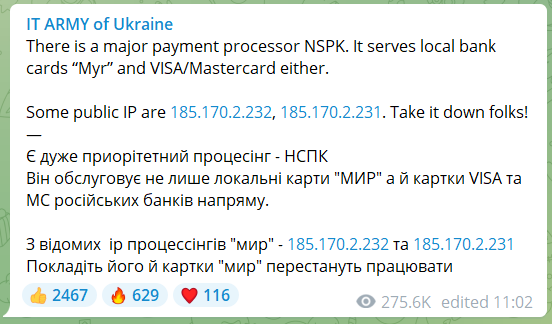
Below you can see another example of a targeted IP taken from “IT Army ok Ukraine” Telegram channel that was created specifically as part of the cyber warfare and consists of a large group of volunteers from Ukraine. Its purpose is to rally hackers to launch massive attacks on Russian IP addresses.
Why are there more Russian IOCs mentioned than Ukrainian IOCs?
After monitoring all these mentions of Russian and Ukrainian IOCs (Indicators of Compromise such as IP and domains), we found that the number of times Russian IOCs were mentioned was significantly higher than those of Ukraine.
There are a number of possible explanations to this gap:
- It may be an indication that Ukrainians find the deep and dark web as a useful space for mobilizing the masses to launch cyberattacks against Russian sites, while the Russians may use more secretive or encrypted tools to launch their attacks.
- The Ukrainians may have a wider audience across the world who support and assist them, which is why sensitive details belonging to Russia are so widely discussed on the darknets.
- Another possible assumption is that after targeting Ukrainian government sites, the Russians are more inclined to target western organizations (in particular American organizations) or even to counterattack organizations who targeted Russia directly, as some of the pro-Russian collectives have indicated.
Hybrid warfare and the deep and dark web
The war between Russia and Ukraine is the first time we have seen a hybrid war of this size, which involves cyber attacks and two rival cyber hacktivist camps maneuvering in the deep and dark web. More than ever before, this war has proved that cyber warfare is an integral part of international warfare and conflicts.
With the deep and dark web being used by cybercriminals as the main platforms for messaging, communicating, and sharing illegal and inciting content, the need for real time, contextualized data monitoring is only growing.
Monitoring domains and IPs are classic examples of real-time indicators we provide to organizations and companies to boost their threat intelligence.
https://webz.io/dwp/the-russia-ukraine-cyber-war-in-the-deep-and-dark-web/
Published: 2022 03 09 08:53:46
Received: 2022 03 09 09:13:14
Feed: Webz.io Dark Web Posts All
Source: Webz.io Dark Web Posts
Category: News
Topic: Cyber Security
Views: 19
