Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.How to Use Dark Web Data for Threat Actor Profiling?
published on 2022-03-09 11:43:29 UTC by Avishag YulevichContent:
Throughout history, monitoring illegal and criminal activities has evolved. In the past, investigating and identifying criminals used to involve various physical measures, such as physical surveillance and later – phone tapping. But in today’s digital world, where a big part of criminal activity has transitioned from the physical world to the cyberspace, tracking threat actors also involves gathering intelligence in the deep and dark web.
Defending against such threats requires prior good knowledge of threat actors who pose a risk. By monitoring their activities and chatter, you can gain insight into:
- Their targets
- The means they plan to use to achieve their targets
- Other collaborators, linked threat actors or the groups they’re associated with
- Gain identifying information that will enable cross-checking with other intelligence platforms
Based on this intel, law enforcement agencies and cybersecurity companies can start profiling threat actors in the deep and dark web.
How to use dark web monitoring to perform threat actor profiling?
There are various investigations that can be performed when using structured data from the deep and dark web.
Let’s take an example of a threat actor called “Sedy” and walk through the steps you can take with dark web monitoring to kickstart your threat actor profiling.
Step #1: Identify a threat on the dark web
Monitoring the activity of threat actors on the dark web helps identify early indications of threats and find key leads for further investigations. We use various techniques to do that, including phrases associated with illegal activities.
The result of this search found a post by a threat actor under the name Sedy on the hacker forums Raidforums. In the post, Sedy mentioned he has a hacking group for hire.
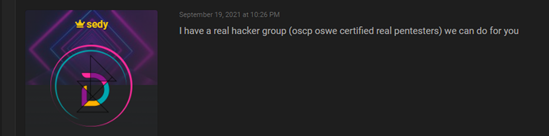
Step #2: Study and characterize the threat actor
Using an advanced query, we were able to retrieve over 100 posts written by Sedy over the past two years. The posts were written on 7 different hacker forums. The high volume of content we could find is an indication of the level of risk posed by the threat actor.
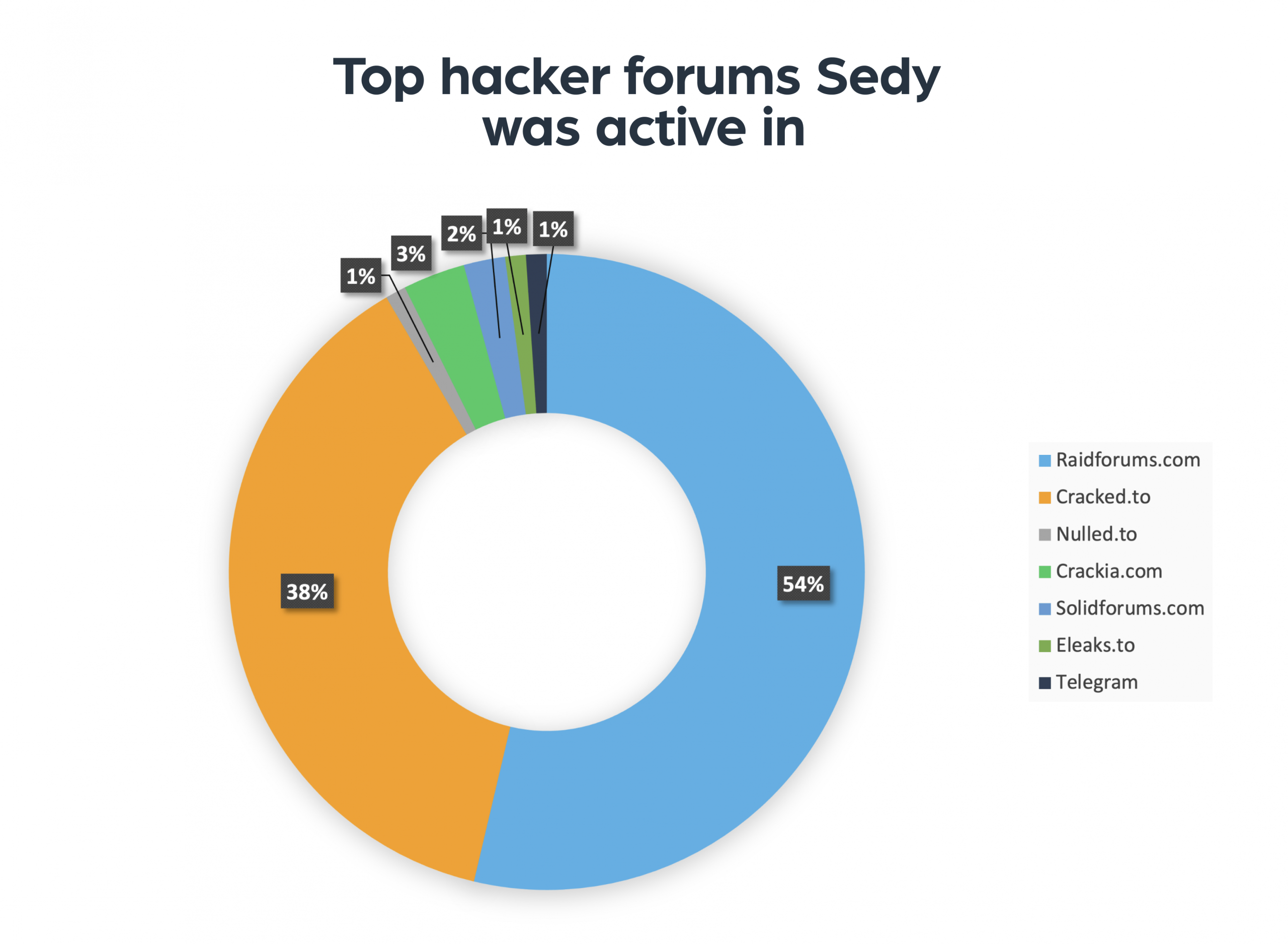
Step #3: Trace the threat actor’s contact details
The next step is to search whether the threat actor left any contact information in any of his posts. This information can include email addresses, phone numbers, links to profiles on other sites and more. We often find posts where threat actors share a crypto address they use to receive payments for their services while protecting their anonymity.
By reviewing Sedy’s posts, we can identify several contact details he left online. Here we could find the threat actor’s Instagram account, Discord account, Discord shop and Telegram account:
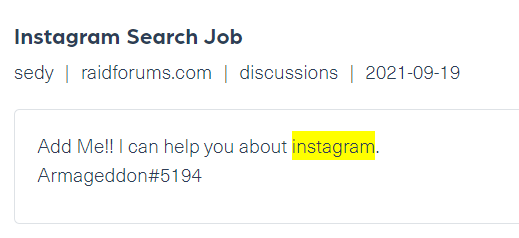
Sedy revealed his Instagram account in a post on Raidforums, the image is taken from Webz.io’s playground 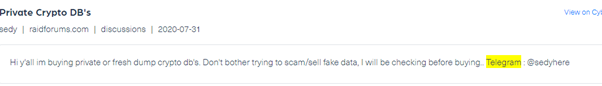
Sedy posted his Telegram account on a different post on Raidforums, the image is taken from Webz.io’s playground
These pieces of information can be used to track the footsteps of the threat actor across the deep and dark web.
Step #4: Expand your investigation to find the threat actor’s “hidden” posts
Using advanced queries, we can dive even deeper to track threat actors who use different names on different sites.
For example, we ran a query for posts that were written by Sedy using his Telegram account, which we discovered in the previous step (#3), under the name “sedyhere”:
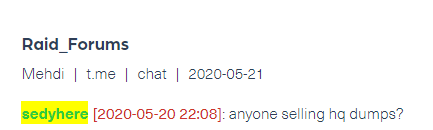
When we ran the initial query to find Sedy’s posts, we detected a post from Telegram as well, under the author: Sedy. This may indicate that this threat actor has more than one Telegram account.
Step #5: Cross-check and link threat actors
In this step, we’d look for different threat actors who shared the same contact information or shared the same content on different platforms. These links can play a crucial role in any further investigation, since cyber criminals often use anonymous avatars and regularly change their names.
Running a query on Sedy’s contact information, we retrieved 4 different posts from 4 different authors that mentioned the same contact details. This could mean that Sedy has more identities on the dark web or that he has other partners in crime.
These findings provide you with a good basis to perform a deeper and comprehensive threat actor profiling.
Final tips
Threat actor profiling is a long process which starts with contextualized and comprehensive data.
But where should you start?
Tip #1: Don’t forget about the scope of your data
The wider the scope, the more content you can cross-check, and run to identify cybercriminals. To find these elusive cybercriminals, you’ll need to dive deeper into the secret world of threat actors. Our customers run these investigations across millions of dark web sites, forums, marketplaces, chatting applications, alternative social media platforms, paste sites and more.

Tip #2: Your investigation is as good as the quality of your data
The deep and dark web are messy spaces with a lot of spam and clutter. For an effective and quality investigation, make sure you use structured and enriched data feeds that will enable you to run advanced queries and retrieve noise-free, contextualized and accurate results.
One thing is for certain; With cybercriminals increasingly using the deep and dark web for illegal trade and illicit activities, the use of deep and dark web feeds becomes key to tracking the activity of threat actors online.
https://webz.io/dwp/how-to-use-dark-web-data-for-threat-actor-profiling/
Published: 2022 03 09 11:43:29
Received: 2022 03 09 12:50:43
Feed: Webz.io Dark Web Posts All
Source: Webz.io Dark Web Posts
Category: News
Topic: Cyber Security
Views: 4
