Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Into the Dark Web: Behind Toyota’s Supply Chain Disruption
published on 2022-03-23 11:17:04 UTC by Avishag YulevichContent:
As one of the world’s largest automobile manufacturers, Toyota Motor Corp. has a diverse supply chain to support its business operations with over 300 suppliers.
Over the years, Toyota has integrated some of its suppliers into its operations, but still kept many third-party vendors under contract. That means that like many other companies with complex supply chains, Toyota has to rely on the quality and stability of its supplier’s cyber security systems.
With today’s interconnected networks, cybercriminals are becoming increasingly efficient in identifying the weakest link in a supply chain, knowing that the biggest damage can come from compromising the smallest business unit.
But finding these threats isn’t an easy task.
Take for example the post below taken from hacking forum Exploit. The threat actor is offering VPN access to what he describes as “a company [that] specializes in the sale and maintenance of Kia, Mazda, Mitsubishi, Toyota and Lexus vehicles.” Although he doesn’t mention the company’s name, which is a typical move by hackers on such forums, the post makes it clear that in case this company is breached, it will affect Kia, Mazda, Mitsubishi and Toyota.
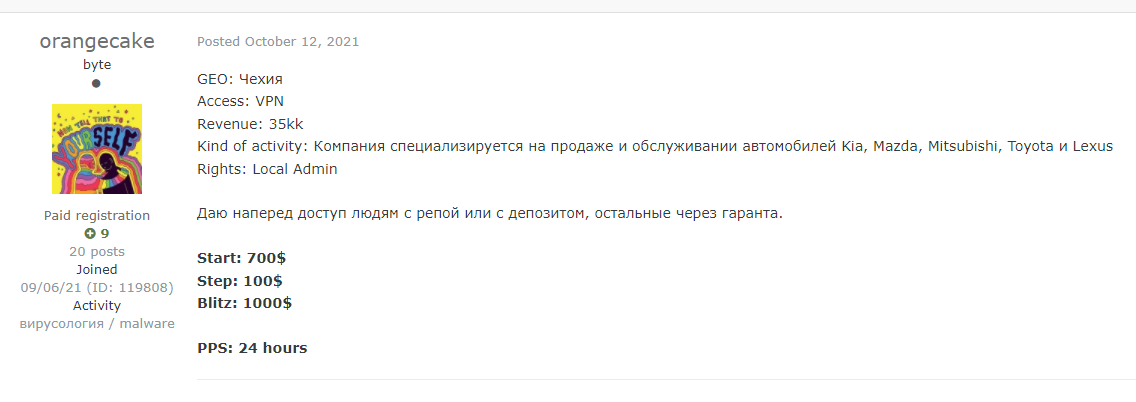
The recent cyber attacks against Toyota’s suppliers
Recently, two Toyota suppliers were hit by cyber attacks, two weeks apart, resulting in a complete halt to the company’s production.
One of the attacks targeted Kojima Industries Corp., a manufacturer of automotive parts, and the other hit Denso Corp., a global automotive manufacturer.
The image below is taken from the Pandora leak site that was recently created on the TOR network. Pandora group has already posted several leaks on the site, one of them, dated March 16, is Denso’s leak.
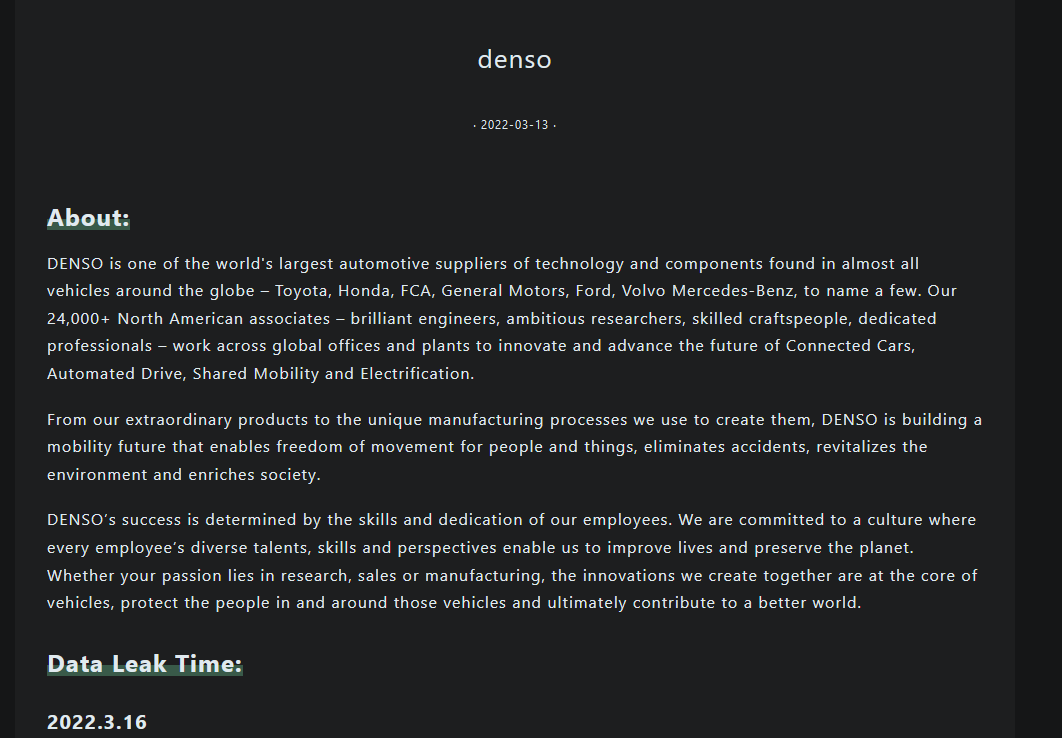
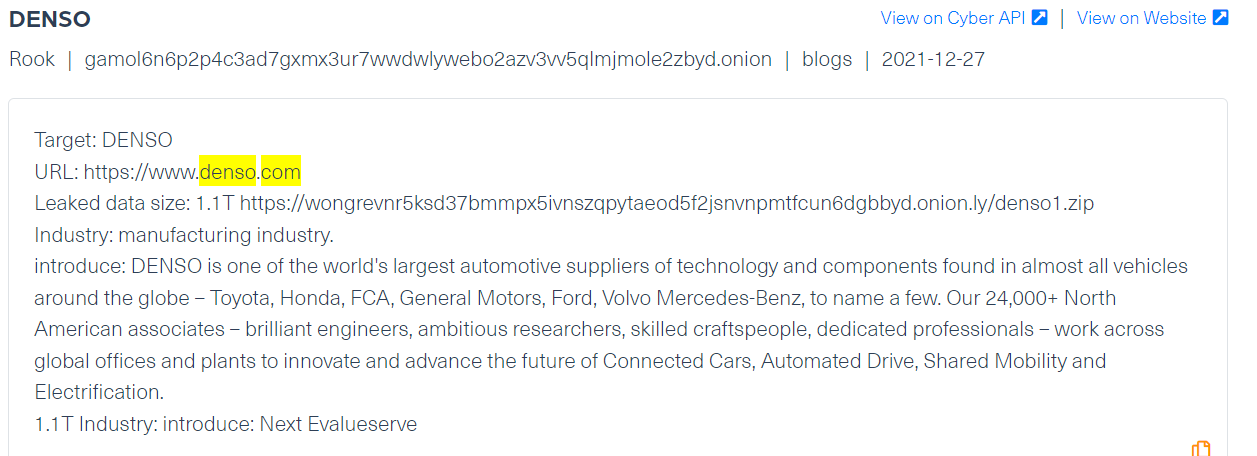
This is not the first time Denso suffered a breach. A few months earlier, in late 2021, they were victims of a ransomware attack, launched by the Rook ransomware group:
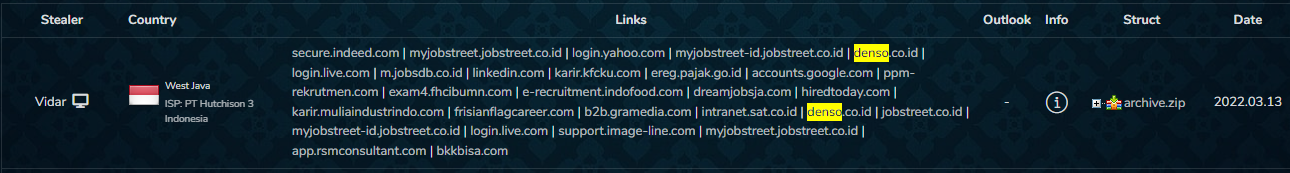
Following these attacks, we used our Cyber API to look for early signs that Denso was at risk of a cyber attack.
We came across mentions of Denso in two different login credential marketplaces with dozens of mentions. The oldest post dates back to March 2020 and the latest one was posted March 13, 2022, on the same day the breach was published. This is an indication that it is probably not related to the attack but at the same time, it shows Denso is still exposed to cyber threats.
With supply chain risk proving to pose a real threat to business operations around the world, our cyber team took a closer look to see if there are other Toyota suppliers at risk of future cyber attacks.
What supply chain risks is Toyota still facing?
A short list of Toyota’s suppliers include Tesla Motors, Bridgestone Americas, Infineon Technologies, Microchip Technologies, Renesas, Panasonic and Mitsubishi.
By using Webz.io’s Cyber API, we have been able to find mentions of all these companies in the dark web.
Here are a few examples of the cyber risks we have found:
Vulnerabilities
We tracked several posts on the Cxsecurity site which provide tutorials on how to exploit vulnerabilities. Here is one example involving a Mitsubishi CVE:
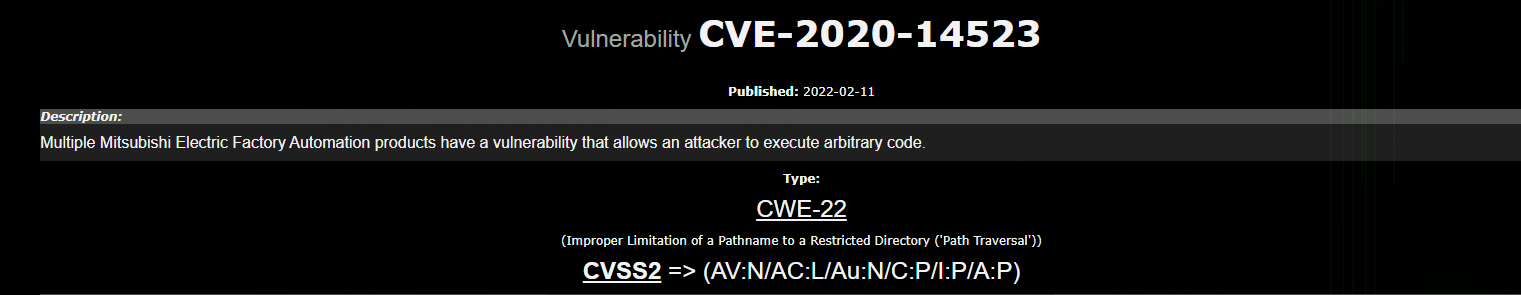
Malware
Below is an example of malware threats, which was taken from Magbo, a dark web marketplace used by threat actors to post shell backdoors on a daily basis. These shell backdoors allow access to a wide range of websites and services.
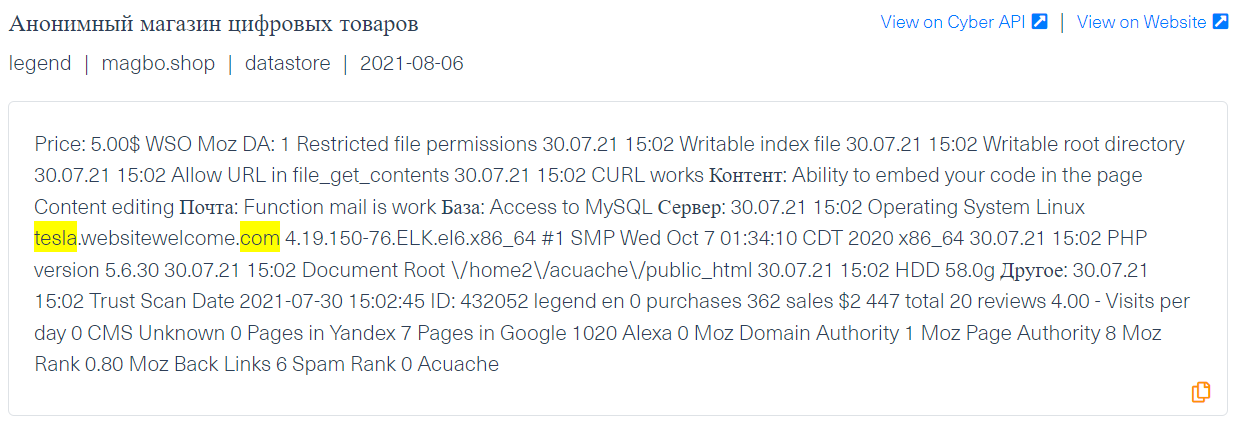
In this example, the threat actor offers a shell that enables its users to embed a code into a Tesla page. It has a similar operational pattern as the keylogger that steals users credentials or cookies that can give unlawful access to the site.
Compromised accounts
Denso login credentials are not the only ones up for sale in the dark web. Countless companies are appearing in login credential marketplaces and hacking forums. Among them, you can find other Toyota suppliers, such as Bridgestone Americas, Infineon, Microchip Technologies, Renesas.
We have found compromised login credentials which increase the risk of unlawful access to their network and a possible data breach.
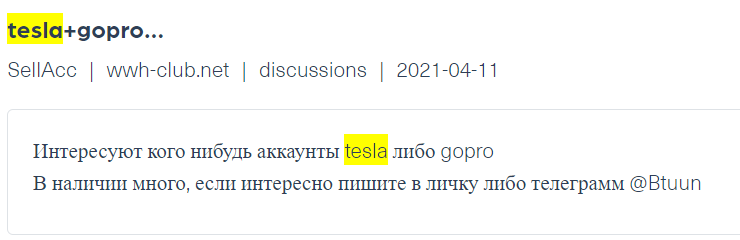
In the next example (see image below), a threat actor is offering compromised Tesla accounts on Wwh-club, a Russian hacker forum, the image is taken from Webz.io’s Cyber API:
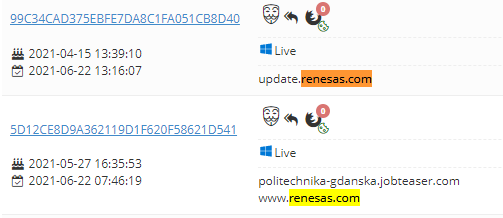
Here are other examples for login credentials belonging to Renesas and Tesla and Bridgestone appearing on 3 different login marketplaces: Russian Market, Genesis and 2easy:
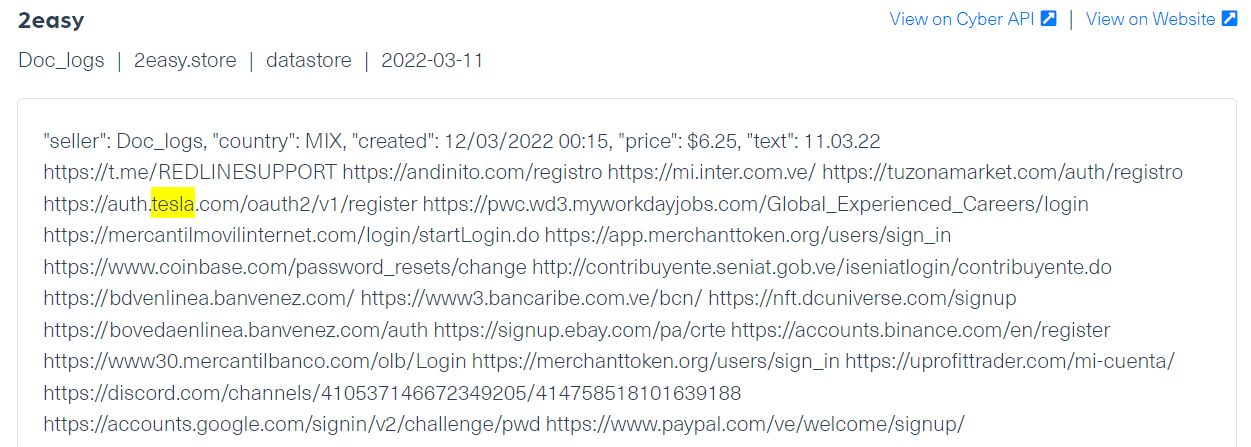

All of the examples we have listed represent a very small part of supply chain risks that can be found in the dark web. We witness tens of thousands of company identifiers mentioned in a negative or potentially dangerous context every day.
Monitoring deep and dark web data can help companies not only track mentions that are directly linked to their own business but also threats to their suppliers that can also threaten their organization. A reliable and wide coverage of deep and dark web data is key to learning about emerging threats and even preventing imminent attacks in today’s interconnected world.
https://webz.io/dwp/into-the-dark-web-behind-toyotas-supply-chain-disruption/
Published: 2022 03 23 11:17:04
Received: 2022 03 24 09:31:12
Feed: Webz.io Dark Web Posts All
Source: Webz.io Dark Web Posts
Category: News
Topic: Cyber Security
Views: 4
