Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Supply Chain Risk: Lessons To Learn from Hubspot’s Breach
published on 2022-04-06 11:40:23 UTC by Liran SoraniContent:
In today’s global markets, most organizations use different vendors, producers, suppliers and other third parties. These organizations are interconnected, and so are their cybersecurity defenses. In some cases, it only takes one compromised employee’s personal information to affect the entire networks of global enterprises.
So where can you find the weak link?
If the personal information of one employee can lead to a serious supply chain breach, the question is where can that information be found. Over the years, cybercriminals have developed effective tools to compromise user databases. Identity data, such as social security numbers (SSN), ID numbers and other personally identifiable information (PII), can be easily found and traded on the deep and dark web in different forums, marketplaces, as well as chatting applications.
Cybercriminals are increasingly using PIIs to defraud or access sensitive data belonging to organizations or their activities.
Only recently, we witnessed a major attack targeting Toyota’s supply-chain, where two of its suppliers Kojima and Denso Crops, were attacked by two ransomware gangs, resulting in a serious security breach and damage to Toyota’s global production.
The Hubspot Data Breach
The latest supply chain attack hit Hubspot, one of the world’s largest customer relationship management (CRM) companies. The company was compromised after cybercriminals used one of its employee’ account to access around 30 portals belonging to several of Hubspot’s cryptocurrency customers, including BlockFi, Swan. The data they stole included personal information such as names, emails, addresses, phone numbers, and other PIIs.
This is considered a classical third-party cyber attack as Hubspot’s CRM system hosted the digital assets of its customers.
Although the breach was mitigated by HubSpot, the contact details the cybercriminals already breached can be reused by other cybercriminals to launch further attacks in the future.
Was Hubspot mentioned in the deep and dark web prior to the data breach?
The short answer is yes. Using Webz.io’s deep and dark web data feeds, we were able to track high activity around Hubspot mentions. Most of the activity took place in deep web forums and communities, such as cracked.io, as well as on Tor network sites including RussianMarket and Genesis.
Looking at the chart below, you can see an increase in the number of mentions of Hubspot in the deep and dark web dating back to the beginning of February. HubSpot reported about the attack they suffered on March 19.
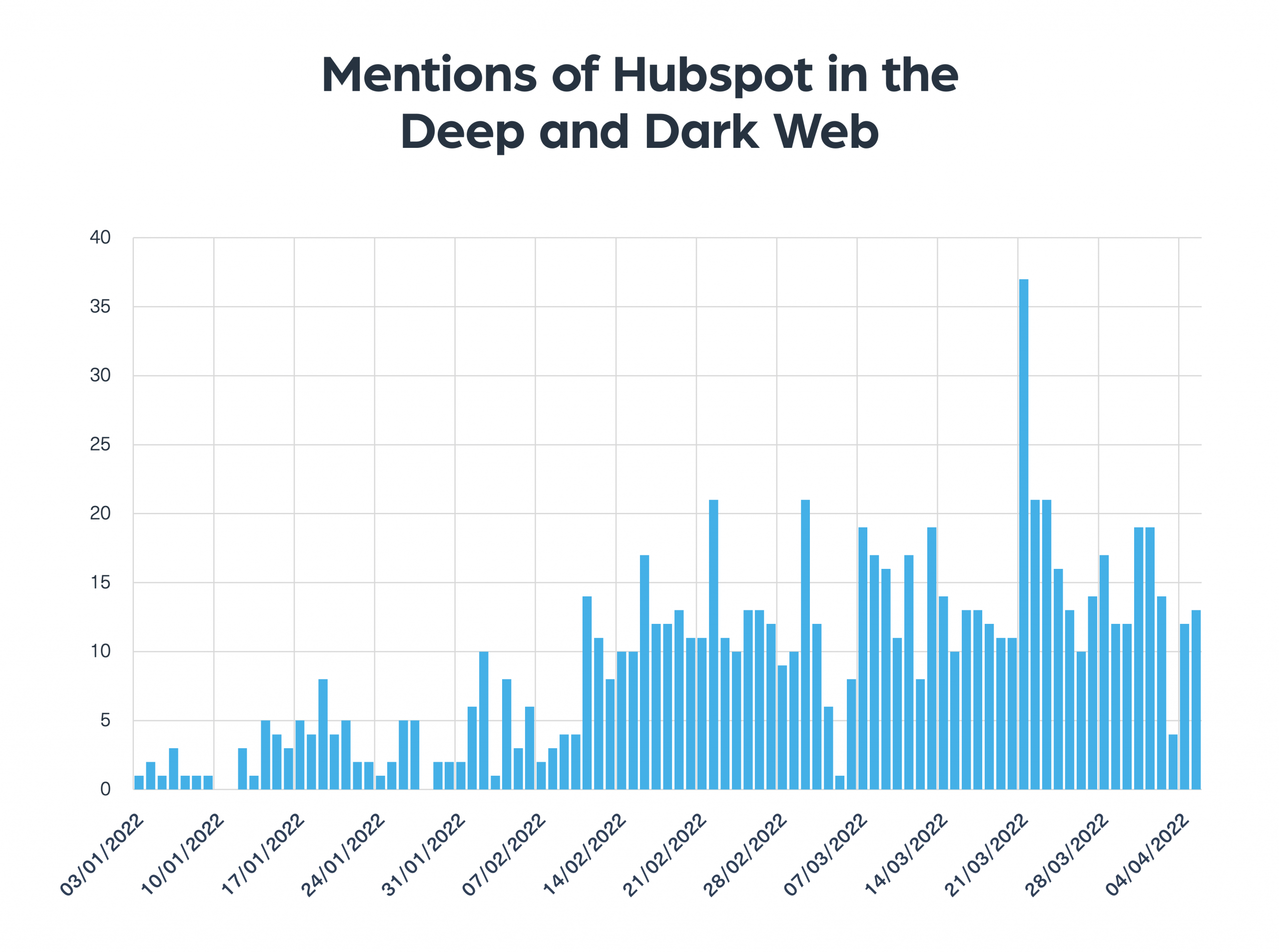
Looking at the chart, we can also see a clear trend towards an increase in the number of mentions in each cycle, which represents a potential event that can be further investigated by using Webz.io’s Cyber API.
Using our Data Segmentation feature, we can also list the top sites where Hubspot was mentioned in illicit and cybercriminal discussions over the past 6 months:
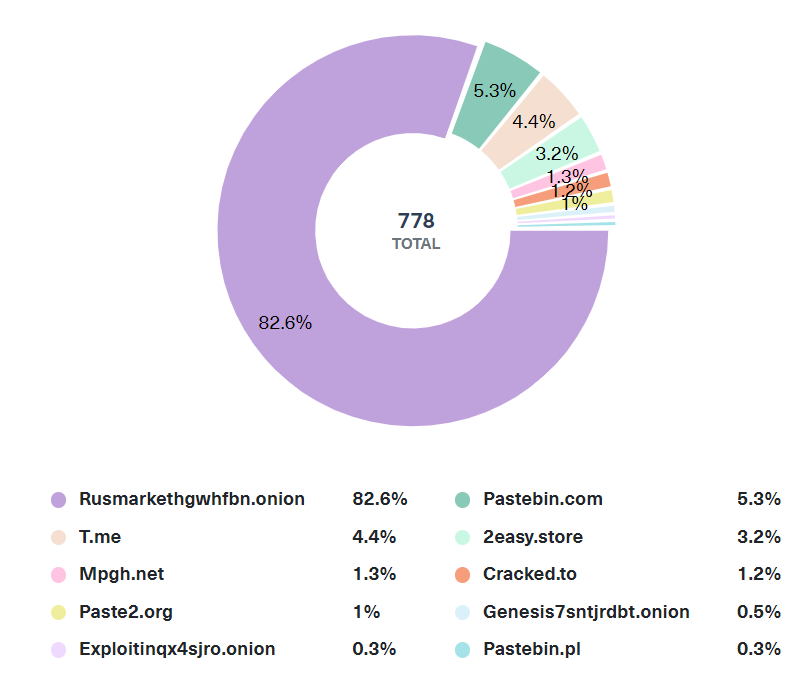
Examples of Hubspot mentions in the deep and dark
Before the attack
By monitoring our feeds, we were able to find Hubspot login credentials traded on dark web marketplace Russian market three weeks before the breach (see the post in the image below). These credentials could have been purchased by anyone on the dark web, including cybercriminals, enabling them to access the company’s assets. The post is dated February 28, three weeks before the breach was reported by Hubspot, on March 19.
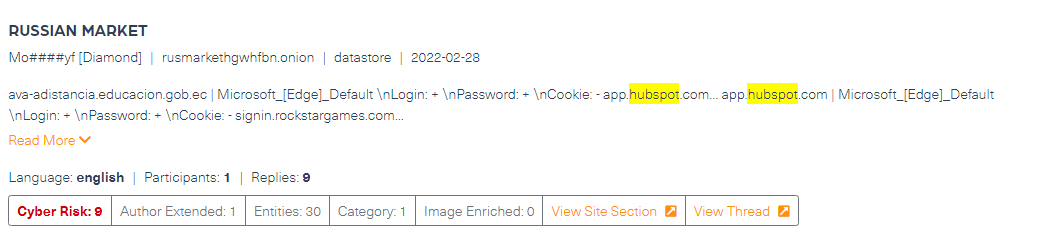
These types of posts are important indications that data is compromised, putting the mentioned company at risk of cyberattacks. Monitoring the dark web can help preventing or mitigating the type of attack Hubspot suffered.
After the attack
Below you can find a post published on Cracked.io on March 19, the same day the breach was reported, where a threat actor is looking to get access to the leaked data from the latest Hubspot breach:
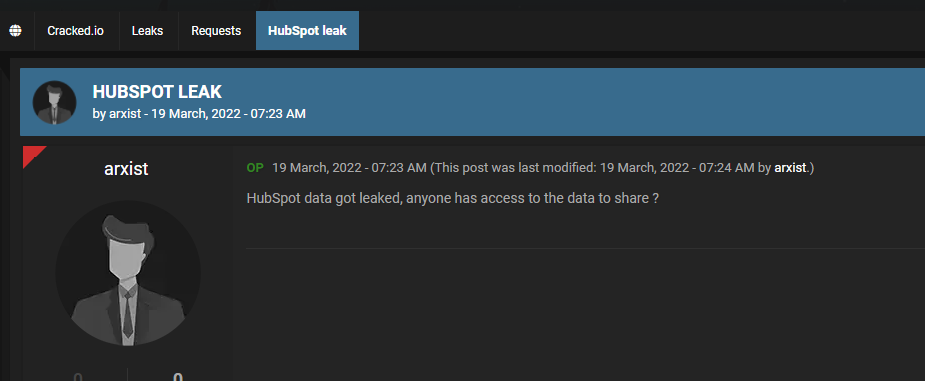
It is important to trace hacker forums after breaches and similar cyber events. Many times, we can see posts discussing and trading the leaked data right after the breach, most of the time on the same day. Some of the time, threat actors discuss details about their plans before the attack takes place or becomes public knowledge.
Using Webz.io’s dark web data feeds, leading enterprises and organizations protect their business and assets by proactively monitoring their third parties for potentially compromised data and alarming discussions, activities, and mentions in the deep and dark web.
https://webz.io/dwp/supply-chain-risk-lessons-to-learn-from-hubspots-breach/
Published: 2022 04 06 11:40:23
Received: 2022 04 06 11:49:48
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 20
