Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.All About Business Email Compromise (BEC) in the Dark Web
published on 2022-04-06 12:19:57 UTC by Yuval ShibiContent:
In a recently published document, the FBI reports that Americans lost $6.9 billion to scammers and cyber criminals as a result of Business email compromise (BEC), ransomware, and cryptocurrency theft in 2021. That represents an increase of $2.7 million from 2020.
While ransomware and crypto scams have gained a lot of public attention, BEC has often been left out of public discussion.
What is Business Email Compromise (BEC)?
Business Email Compromise (BEC) is an email cybercrime scam that targets companies’ business email addresses in order to defraud a company. It is considered to be the biggest source of financial losses today according to the FBI’s Internet Crime Center (IC3), totaling $2.4 billion in 2021.
BEC is a common social engineering scam, which is conducted by spoofing or hacking the email account of a senior employee or executive. This information is then used by cybercriminals to send an email that appears to come from a known source and make a legitimate request in which they instruct the unknowing victim to approve payments, release client or employee data or simply transfer money to the scammer’s bank account. The goal of a BEC is either to defraud a company of funds or to obtain personally identifiable information (PII) to be used in future attacks.
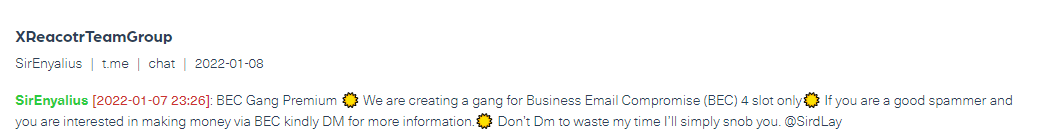
How is a BEC scam carried out?
Step #1: Obtaining the Personally Identifiable Information (PII) of executives
The first step cybercriminals and hackers take in conducting a BEC scam is to obtain the Personally Identifiable Information (PII) of an executive.
Take for example an executive’s email account. To carry out a BEC scam, the fraudster will first access the executive’s business email account since that is the entity with which that specific individual accesses all company meetings and platforms. The compromised email address leaves the executive, as well as the company, at risk and open to attacks and fraud.
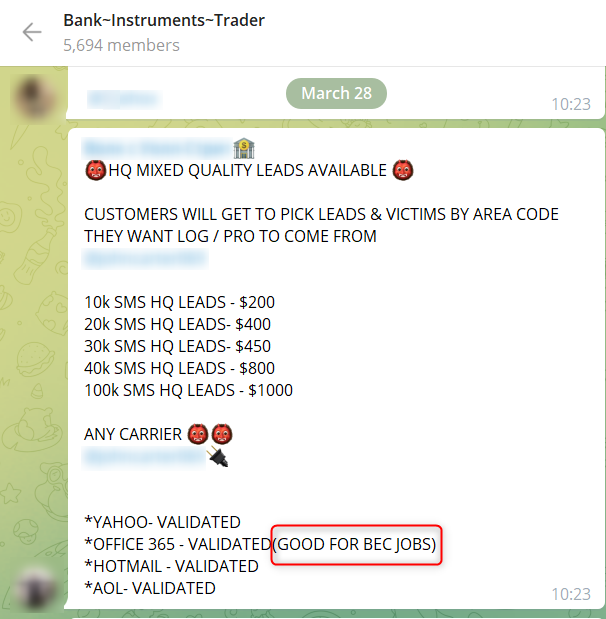
A Telegram actor offering PII for sale for committing BEC scams
There are two main ways to obtain executives’ PIIs – social engineering and cyberattacks.
Social engineering for PIIs
Social engineering includes a wide range of malicious activities conducted through human interactions, in which cybercriminals use psychological manipulation to trick users into making security mistakes or divulging sensitive information.
In the the mage, below you can see a thread of a discussion between threat actors over the Evilginx2 social engineering method on the dark web hacking forum Dread.
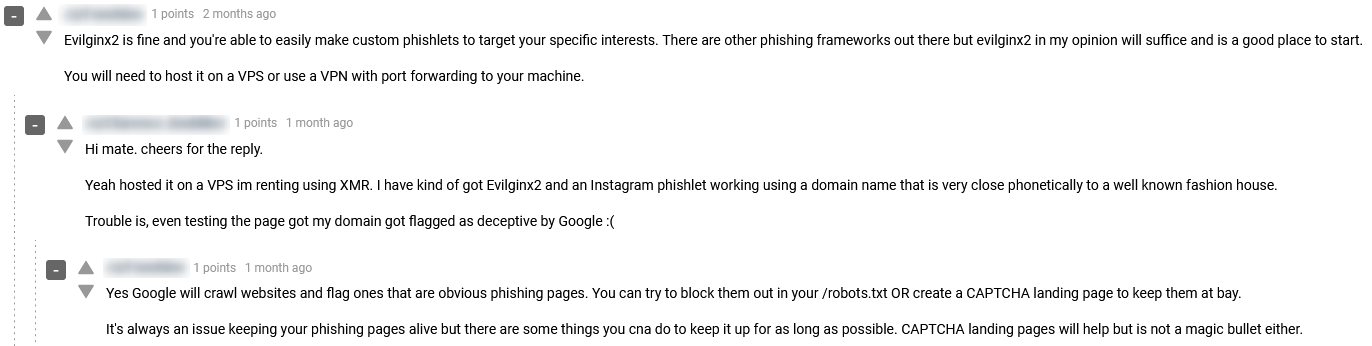
Evilginx2 is considered a Man-In-The-Middle attack, taking its name from the practice of hackers to put themselves between a website and the user to make it seem as if the exchange of information is normal. Using Evilginx2, cybercriminals can phish login credentials along with session cookies to bypass two-factor authentication, and by that gain access and control business accounts or an executives’ email, as part of their BEC scam.
Cyberattacks targeting sensitive information/PIIs
The fraudster gets access to personal or sensitive information about individuals, usually the CEO, C-levels and executives. To obtain this information, the fraudsters usually target HR employees, who often have access to this type of data, or hacking forums where such data is offered for sale. This data may be used at a later stage to launch other attacks such as CEO Fraud, a spear-phishing email attack in which the attacker impersonates the CEO.
Below you can see an example of a post where a hacker published a 280M data breach which includes email addresses, phone numbers, home addresses and other PIIs. This is a common way to obtain compromised accounts belonging to executives, which can be used to conduct BEC scams in the future.
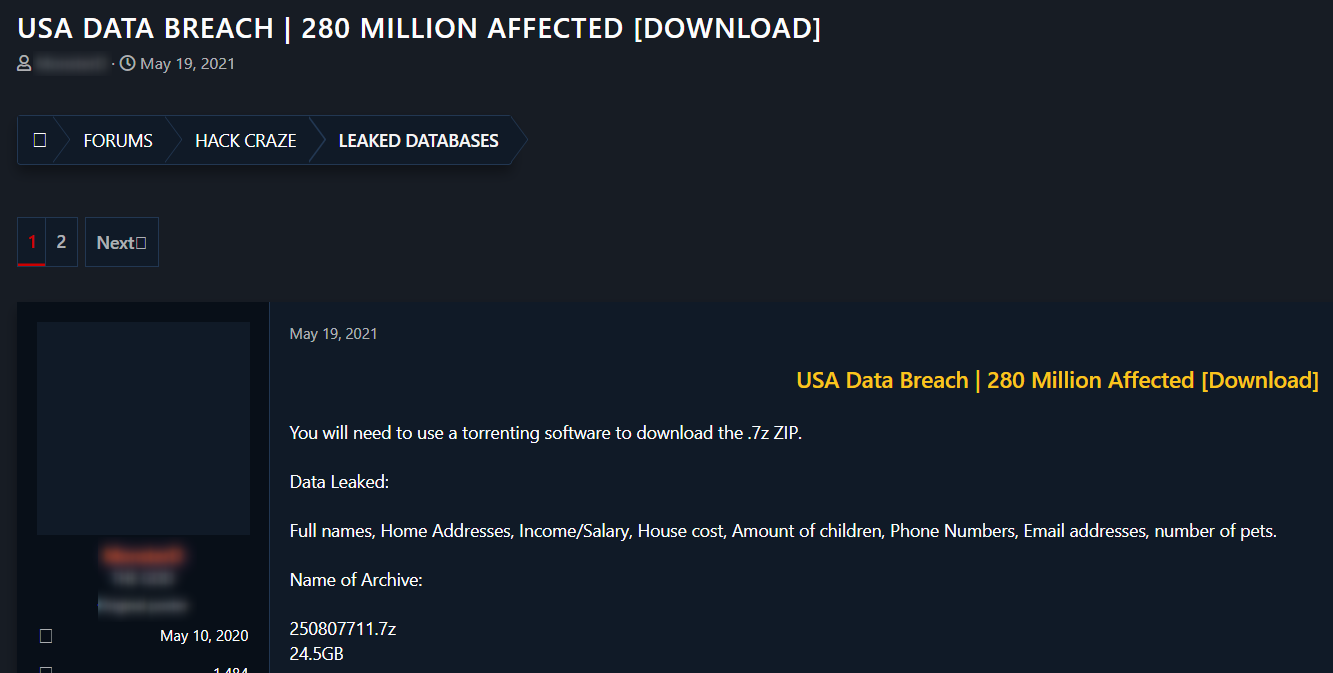
Compromised email addresses originating from hacking forums can be found on our Data Breach Detection API.
Step #2: Carrying out the BEC scams
Once the fraudsters gain access to a compromised email account, they can conduct the BEC scam by either of the following ways:
- CEO Fraud
- False Invoice Scheme
Then they request payments to be sent to accounts that are owned by them. It is important to note that these scams contain no malicious links or attachments that direct the employees or executives to a harmful virus page. They solely rely on human interaction as they impersonate the victim. That’s why they often pass under the radar of traditional anti-malware and other cybersecurity software such as antiviruses.
Example of BEC scam types
CEO Fraud
Fraudsters pose as the CEO or executive of a company either by email or by using the company’s internal chat platform. They then request funds to be transferred to their account.
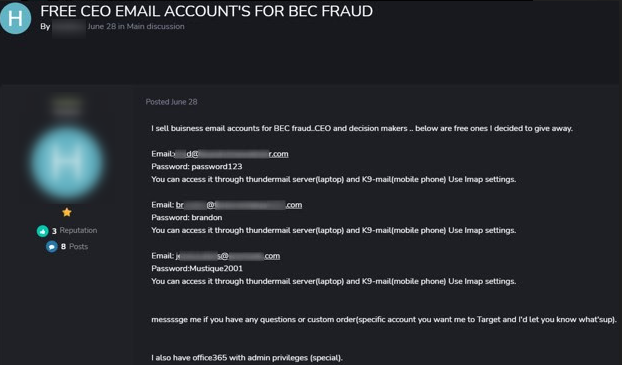
The following post shows a threat actor selling CEO accounts for BEC fraud on carding forum carder.tv:
False Invoice Scheme
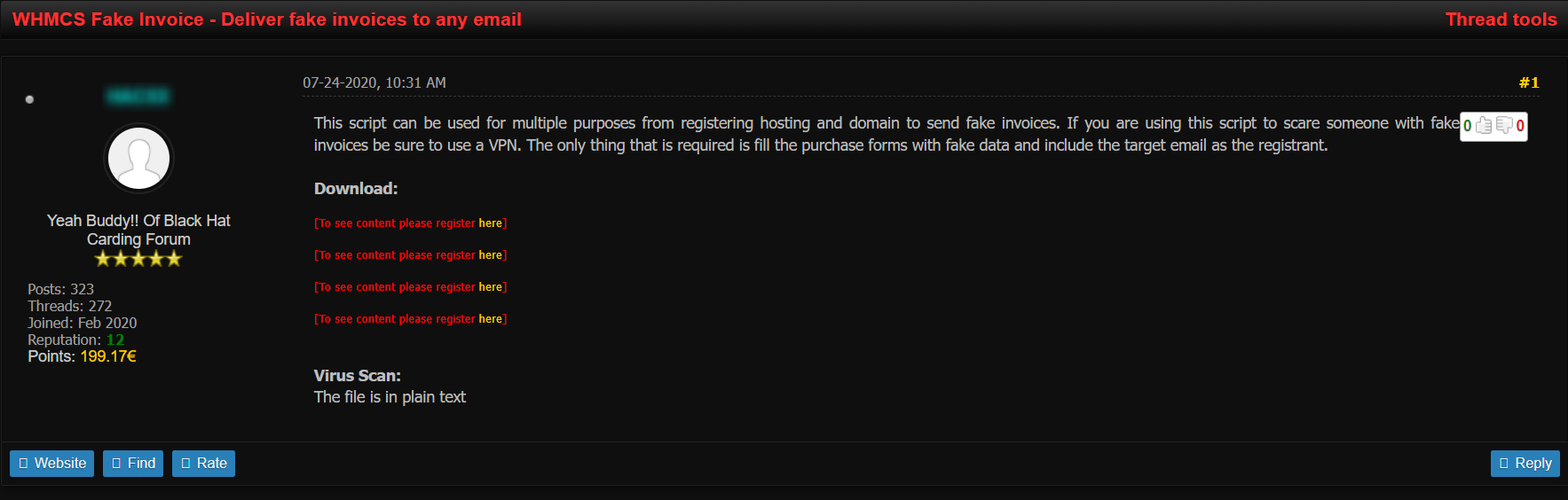
The False Invoice Scheme often targets companies with foreign suppliers. The scammers pretend to be their overseas supplier and request funds to be transferred to his accounts. The next post shows a threat actor posting a fake invoice script for multiple uses on dark web hacking forum Blackhat Carding:
Another way to carry out BEC scams is the Legal Representative Impersonation or Attorney Impersonation. In this BEC scam the scammers present themselves as a lawyer or a legal representative. The scam is typically aimed at junior employees, assuming that they are not knowledgeable enough to question the validity of the request.
By using Webz.io’s Cyber API and Data Breach Detection API, we were able to identify companies that are at risk of BEC scams. We helped companies monitor relevant mentions on dark web hacking and carding forums and marketplaces, as well as chatting applications like Telegram. It is common for cybercriminals to collaborate in order to perform these attacks, by asking and sharing advice and related guides, as well as selling or trading information to assist each other.
https://webz.io/dwp/all-about-business-email-compromise-bec-in-the-dark-web/
Published: 2022 04 06 12:19:57
Received: 2022 04 06 12:50:16
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 19
