Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.The Emerging Threats to Healthcare Providers in the Dark Web
published on 2022-04-06 10:04:10 UTC by Hagar MargolinContent:
With the number of cyber attacks increasing over the past year, one industry is increasingly becoming a prime target for cybercriminals – the healthcare industry. Over the past three years alone, the number of U.S. patients whose records have been compromised as a result of a cyber attack tripled, from 14 million in 2018 up to 45 million in 2021.
By using Webz.io’s Cyber API, we have been able to score the deep and dark web and identify some of the top risks healthcare providers and institutions are facing in these hidden corners of the web.
So what are the top cyber risks the healthcare industry is facing on the deep and dark web?
Ransomware attacks
Like other industries, the healthcare industry is also a favorite ransomware target. An increasing number of healthcare institutions woke up one day to find cybercriminals have encrypted their files and are demanding they pay a steep ransom in return for decrypting the files.
For healthcare service providers who require access to patient records, prescriptions, and other critical information, this scenario can pose a serious risk as it seriously undermines their ability to provide quality patient care in real-time. In some situations, a ransomware attack can also put people’s lives at risk. These extreme conditions can lead healthcare providers to pay the ransom cybercriminals demand for decrypting the data they had hacked. This makes healthcare providers an easy prey for ransomware groups.
Who are the top ransomware groups to target healthcare providers?
We used our dark web data feeds to find out which are the top ransomware groups that target healthcare providers over the past year. We found the leading four groups included Conti, Lockbit, Vice Society, and Hive.
In the post below, taken from the Lockbit ransomware group’s site, you can see the group announced they had attacked a healthcare service provider, CompuGroup Medical, one of the leading eHealth companies in the world.

Although the main goal of most ransomware groups is monetary gain, there are still a few groups who include either all or the majority of the healthcare sector under their taboo list, excluding them from their “target list”.
In the following screenshot taken from a ransomware group site, Babuk, on the Tor network, the ransomware group claims they won’t attack hospitals, alongside non-profit organizations, schools and small businesses. Note that “private plastic surgery clinics” and “private dental clinics” are still valid targets according to their list.
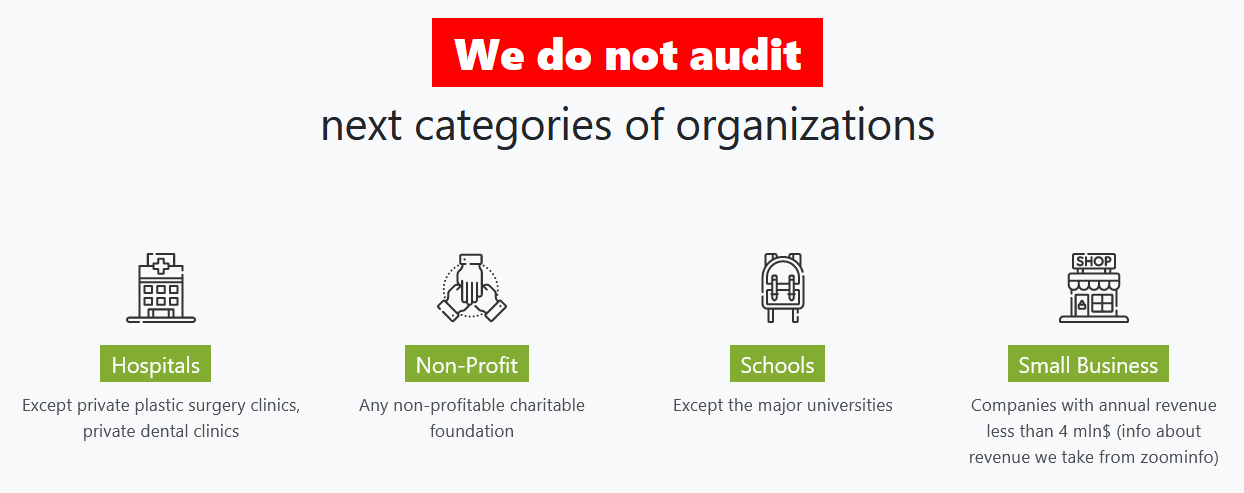
Data Breaches
Having enormous patient data available, breaching the systems of healthcare institutions such as hospitals, is increasingly becoming profitable for cybercriminals. Once they gain access to sensitive data they sell it for a significant amount of money.
The stolen databases are often sold on the deep and dark web. In the image below, you can see a post that was very recently published on the new hacking forum Breached.co, which claims to be the new version of the known hacking forum Raidforum that was recently seized. In the post, a threat actor under the username DataExpert offers a database with about 1.5M stolen records of patients of one of the largest healthcare groups in Singapore, Singapore Health Services for $2750.
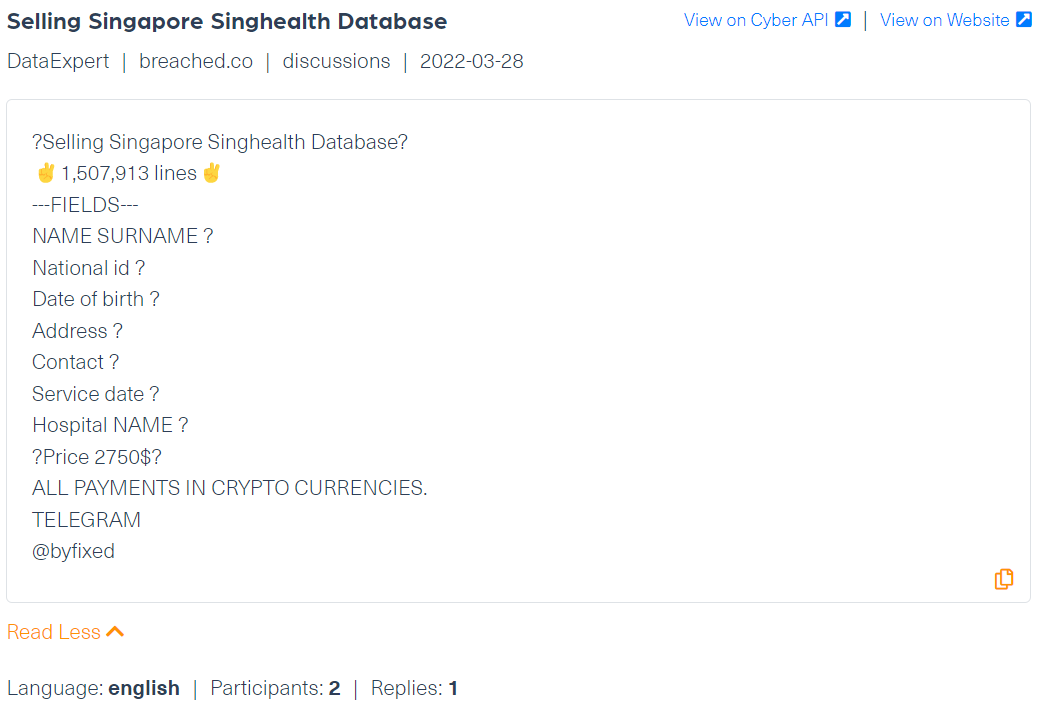
Although the original post was taken down, the screenshot above is taken from Webz.io’s Cyber API which crawled the content before it was removed.
Accessing this type of sensitive information enables threat actors to commit fraud by identity thefts. In addition, this data loss can cause reputational damage and lead to other financial loss in the future.
Business Email Compromise (BEC)
Business Email Compromise (BEC) is a financial cybercrime that uses compromised email belonging to an employee, often an executive or CEO, to defraud organizations, employees, customers and partners. By pretending to be an authorized employee, threat actors can get healthcare employees to disclose sensitive information, and even make financial transactions to malicious actors.
In the following screenshot, taken from ZeroPaste, a paste site, you can see that a business email account, belonging to the CEO of Augusta Health, an American medical center located in Virginia, was leaked. The post also includes an IP address, phone numbers and hashed passwords which apparently belong to the CEO and/or to the hospital.
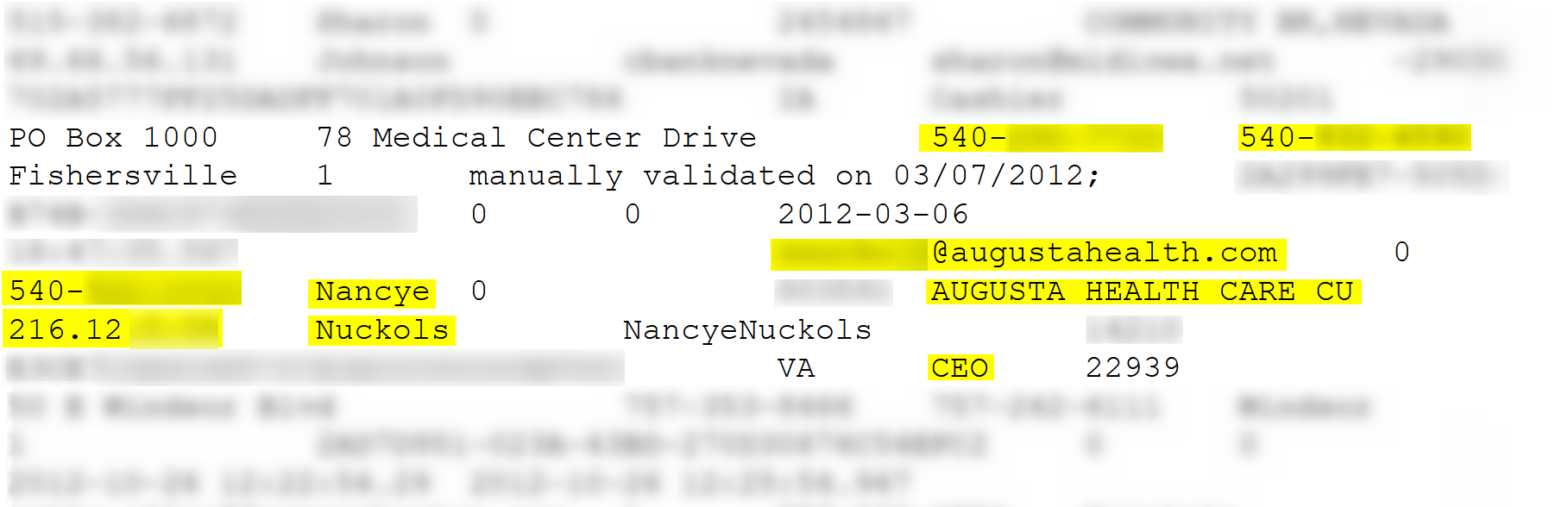
Vulnerabilities and exploits
Organizations around the world are aware of the dangers of hidden vulnerabilities, whether in their systems or on a specific device. But when it comes to the healthcare sector, vulnerabilities pose an even greater risk as their management systems and technological medical devices are used to treat and save human lives. A malicious access to one of their systems can have serious implications.
One of the recently discovered critical vulnerabilities to hospital systems belongs to the Hospital Management System 4.0 (HMS), a computer system that helps manage healthcare information effectively and assists in the task completion of health care providers.
This specific vulnerability (CVE-2022-24264) refers to the SQL-injections which the information management system suffers from. This vulnerability enables hackers to gain access to all information stored on the system, including sensitive information about the system’s customers.
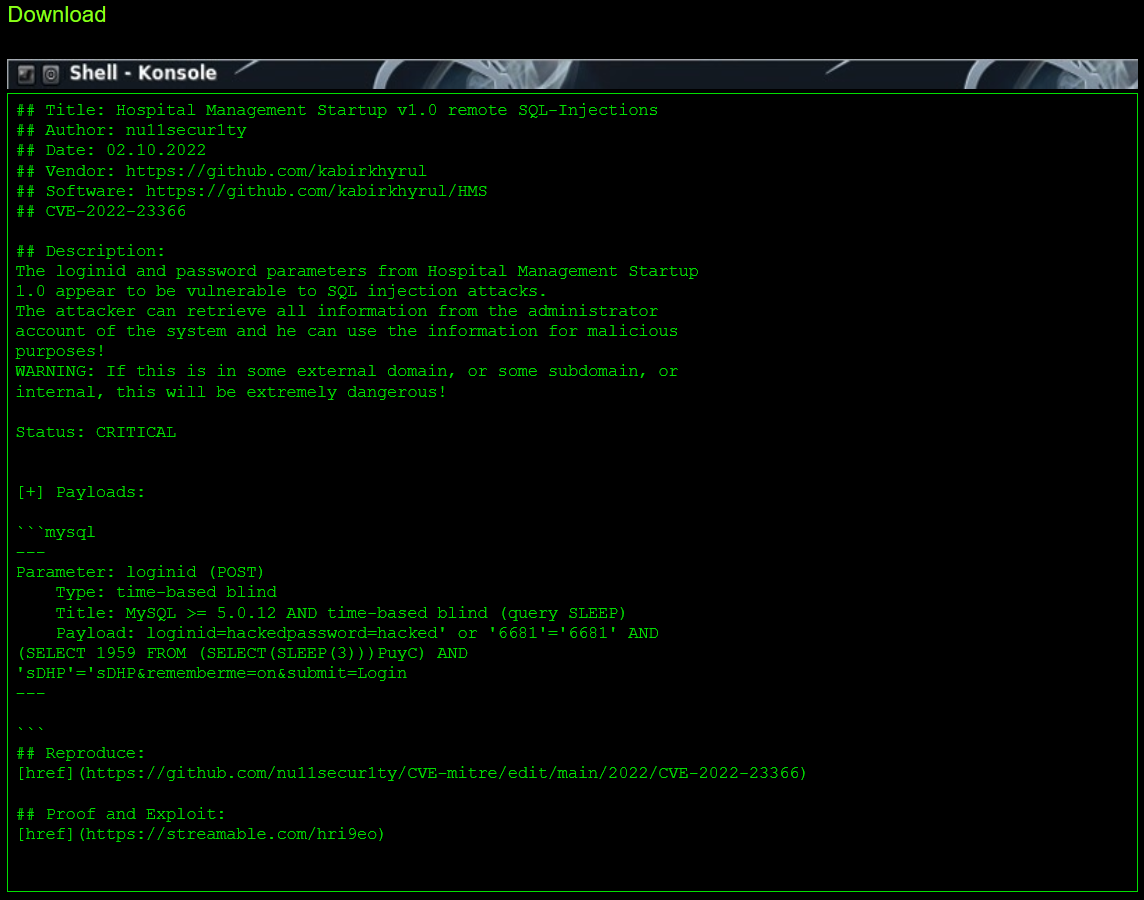
When it comes to healthcare, medical devices can also provide an easy entry point for cybercriminals. With many devices primarily designed to cater to and support the needs of modern healthcare, they aren’t designed with security in mind.
Even though these devices may not actually contain sensitive information like patient data, which cybercriminals are seeking, they can be used to launch an attack on a server that does contain valuable information or even cause damage to the device itself.
In the following example, a post mentions a vulnerability that is found in Philips MRI machines. Unlawful access to these machines can ultimately lead to compromising the healthcare bodies which are using it.
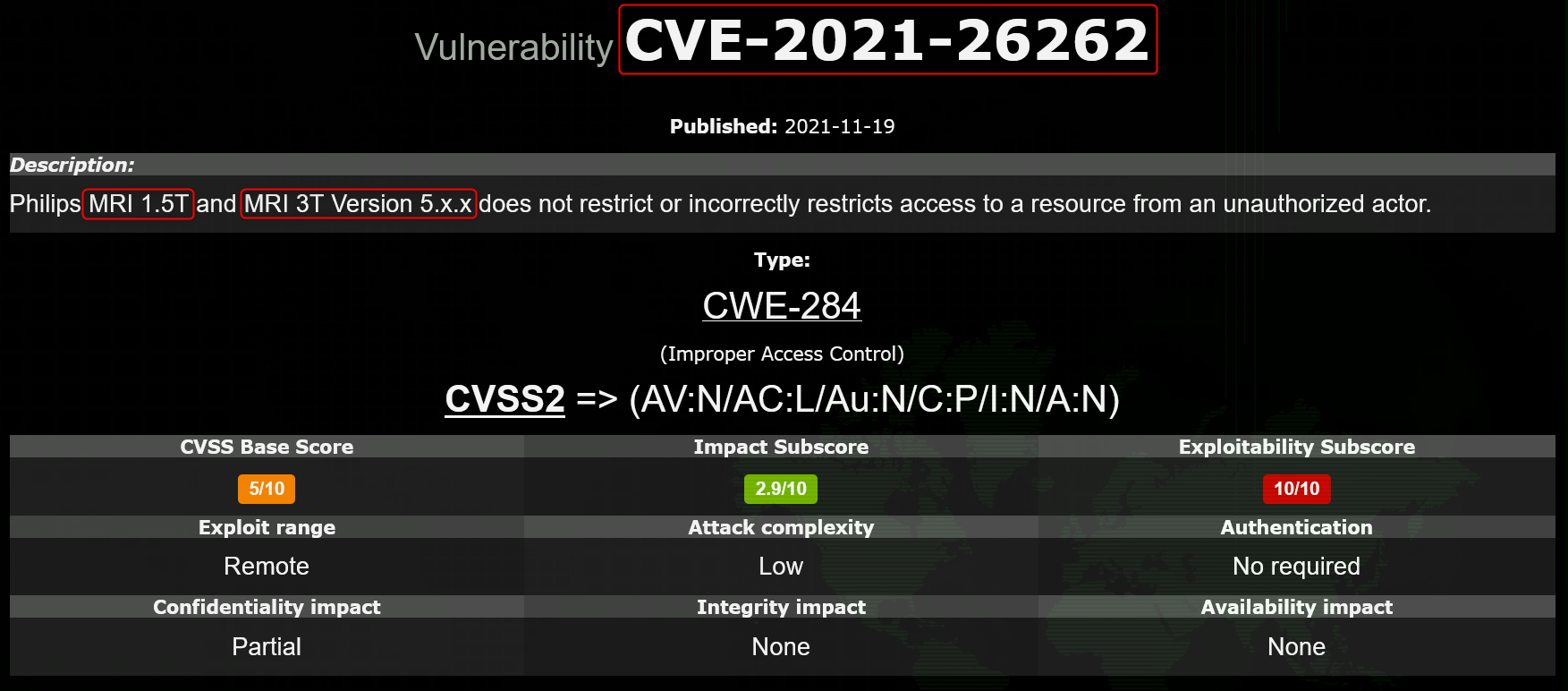
DDoS attacks
DDoS attacks, short for Distributed Denial of Service, involve the use of multiple TTPs (Tactics, Techniques, and Procedures) by threat actors to disrupt the normal traffic of the targeted network and overwhelm it to the point of a complete crash. This network disruption, similar to a ransomware attack, can disrupt ongoing patient care, as it also prevents access to critical patient-related information.
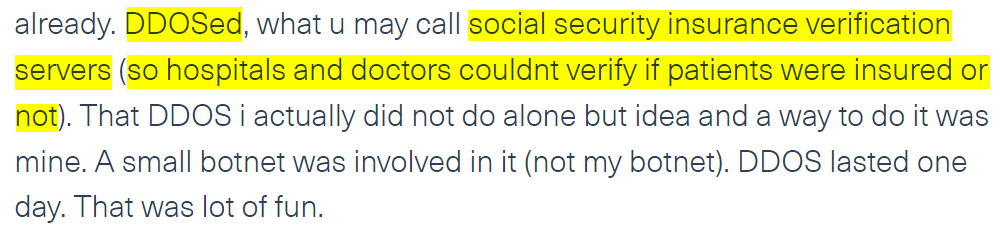
In the following post, published on an imageboard, NanoChan, a threat actor discusses the variety of cyber attacks he committed. One of the attacks he mentions is a DDoS attack he carried out against a social security insurance verification server, which blocked healthcare providers from accessing necessary patient information.
Insider threats
Similarly to other industries, the healthcare industry is often overlooking the possible dangers that lie within the company – individuals, often employees. Many healthcare bodies are complex and include a long list of employees, contractors and business partners who are privy to confidential information. Although each individual or body has limited access and can see a different type of data, large volumes of sensitive information are accessible to more than a few people. The list is long, from information about patients to medical equipment and financial forms, insider information of this nature can harm the organization as soon as it leaks out.
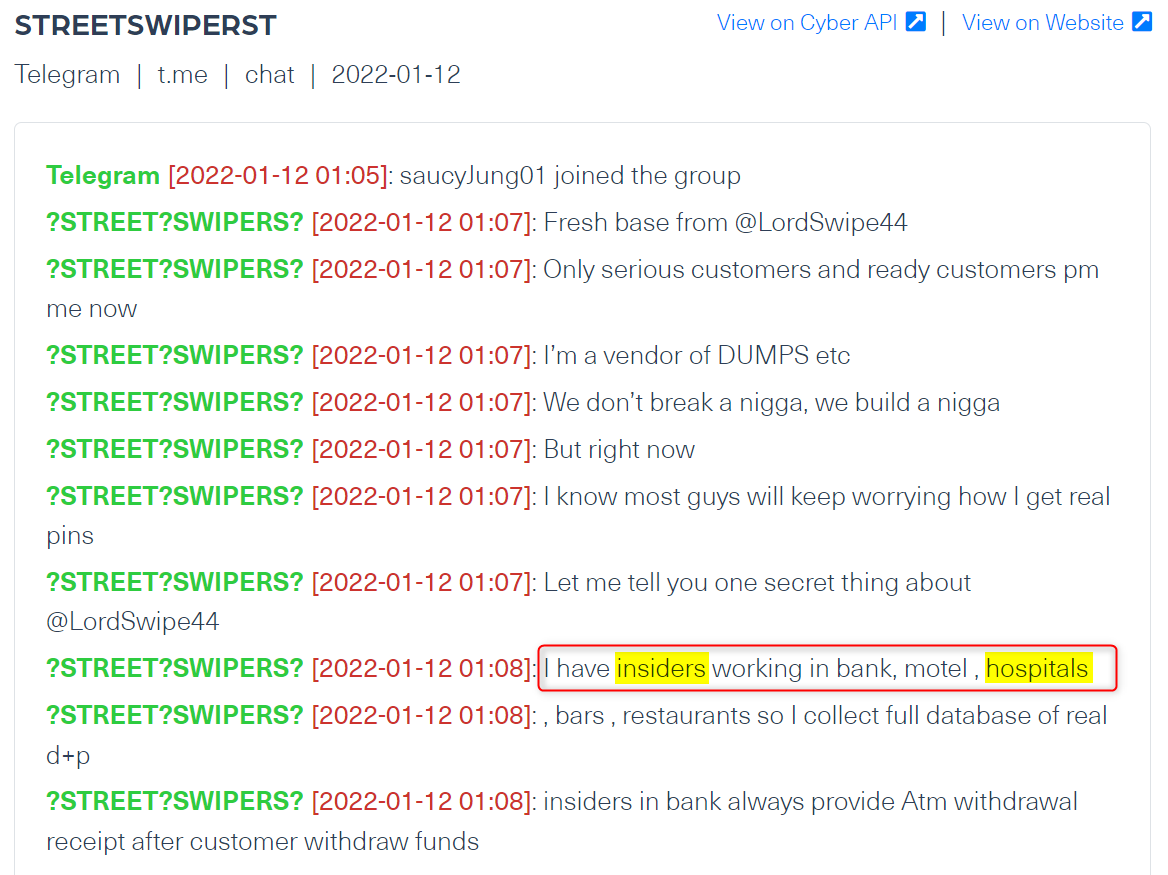
The chat in the image below was taken from a Telegram group, where the admin offers malicious services by insiders he runs in places like banks, motels as well as hospitals. The messaging took place only a few months ago, showing the threat insiders in healthcare service providers is still out there.
Why is the healthcare industry a prime target for cybercriminals?
There are several reasons behind the increase in the number of attacks launched against healthcare providers:
- There is a high demand for patient information
- The lack of budget for cyber security solutions in the industry
- The relatively high number of medical devices providing multitude of entry points for cyberattacks
- The need to access and share data remotely between healthcare institutions, which increases the risk of cyber attacks
- A lack of cyber security training and awareness among medical teams
- Unlike other industries, the stakes are high and can threat people’s lives which makes healthcare providers more inclined to pay ransom, making them an easy prey for cybercriminals
Monitoring emerging attacks or cyber risks on a continuous basis is paramount when it comes to protecting healthcare institutions. As cyber threats continue to rise, the only way to keep these critical services safe is by proactively tracking mentions in the deep and dark web.
https://webz.io/dwp/the-emerging-threats-to-healthcare-providers-in-the-dark-web/
Published: 2022 04 06 10:04:10
Received: 2022 04 06 12:50:16
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 15
