Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.New Ransomware Group: RansomHouse – Is it Real or Fake?
published on 2022-05-16 07:34:17 UTC by Hagar MargolinContent:
The first quarter of 2022 has seen a lot of cyberattacks, with RaaS (Ransomware as a Service) being the most common form of cyberattacks these days.
The deep and dark web continues to be a favorite space for new ransomware gangs, whether they are brand new groups with new infrastructure or re-brand of an existing group. Whether they are old or new, most ransomware groups operate very similarly. For example, some of those have already built their own Tor site, where they publish the targeted organizations they’ve allegedly attacked, including leaking some of the databases they claim to have compromised (assuming that the negotiation for getting a ransom by the victim failed).
But a question that has been recently raised is whether these are real or fake ransomware gangs?
One of the new ransomware groups whose credibility has been put in question is RansomHouse. So far, the group has published 4 samples of alleged stolen data from 4 companies (see image below) on their site on Tor. These companies are:
- SLGA, a local Canadian liquor and gaming authority
- Jefferson CU, a local U.S. bank
- AHS, a German handling service provider
- Dellner, a Swedish railroad equipment manufacturer
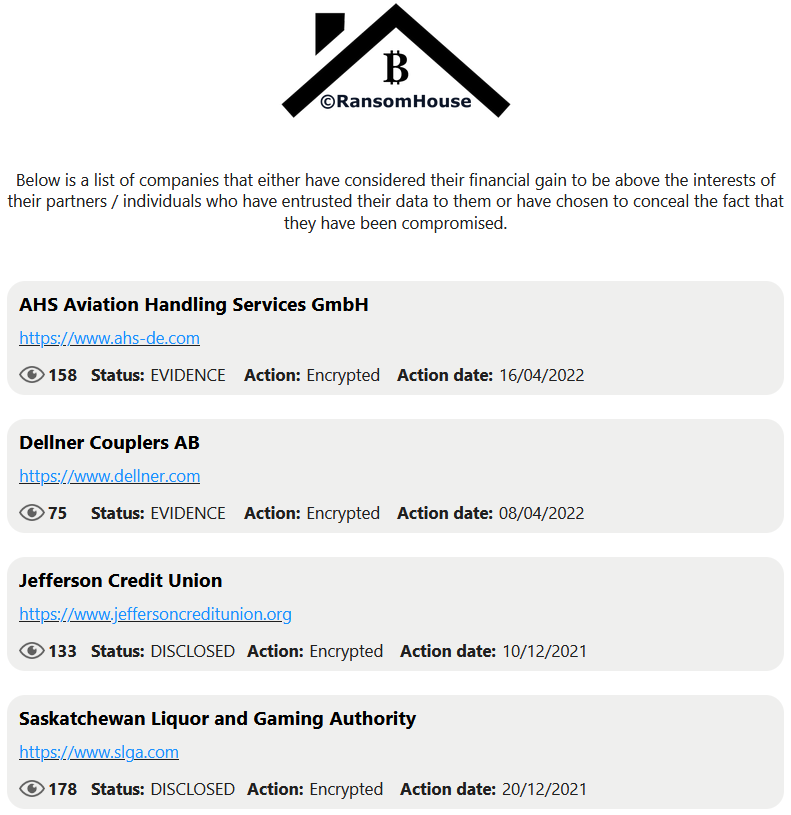
Users on Twitter, Telegram, and dark web forums have been debating whether RansomHouse is a real ransomware gang that is responsible for attacking and stealing those databases, or an extortion group that buys leaked databases from a third party and tries to extort the victims by demanding a ransom fee in return for not leaking the data to the public.
How can you verify whether a ransomware group is real or fake?
Step #1: Use Publicly available records and announcements
The very first step should be to check the details that are publicly available. For example, have the companies suffered a ransomware attack?
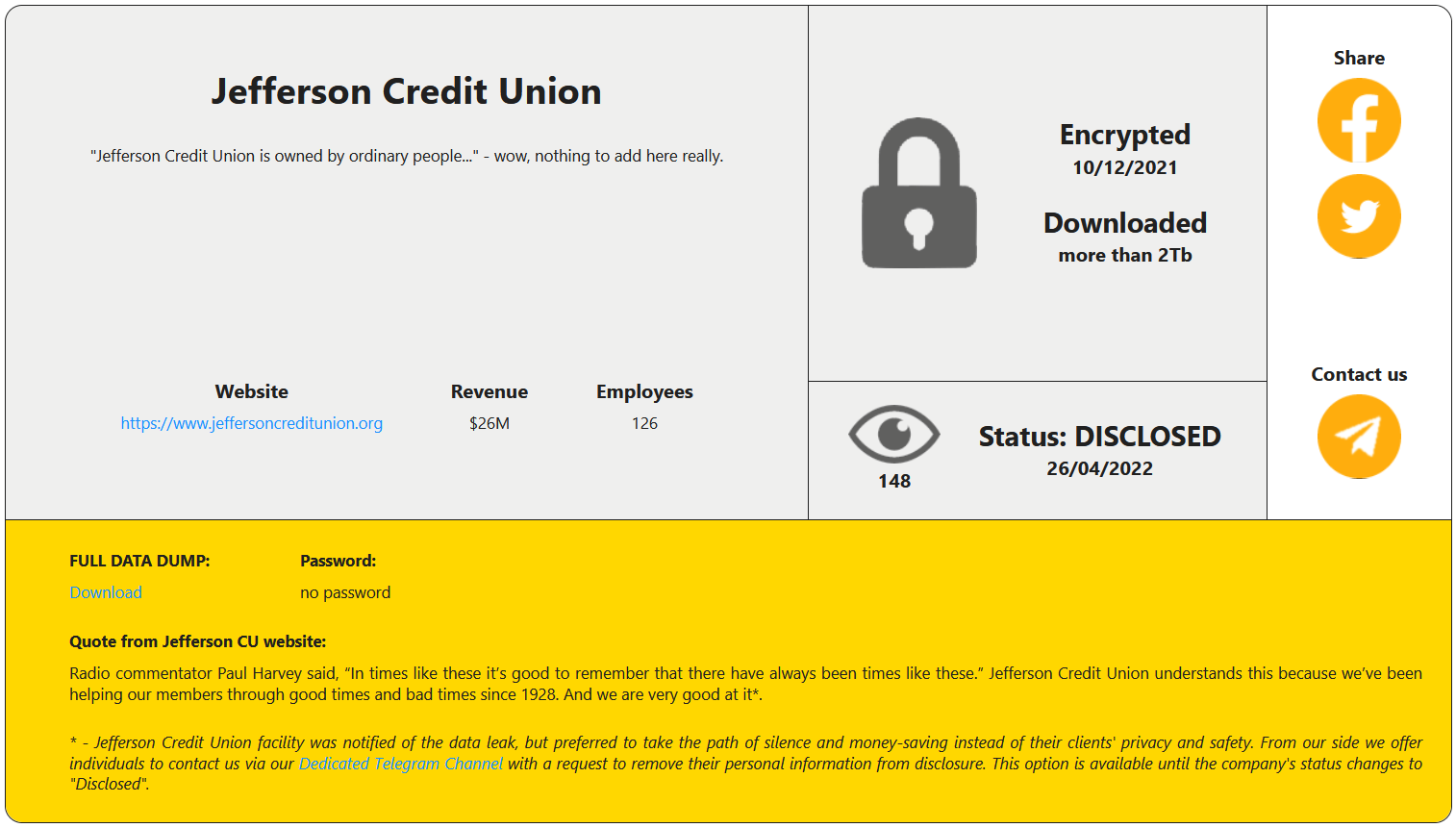
According to an announcement made by Jefferson Credit Union, they admitted that they were hit by a ransomware attack, in which the company’s files were encrypted. According to CBC News, RansomHouse affiliates contacted SLGA, claiming to have encrypted the authority’s system using ransomware.
As for AHS, they were targeted by a cyberattack but whether it was a ransomware attack remains unknown. Deliner has not yet clarified whether they suffered a cyberattack at all.
None of these announcements are damning evidence that the RansomHouse group was behind the attack. They could’ve hired ransomware from a different gang to carry out the attack, or they could not have even been involved in these attacks at all.
In order to get proof that this ransomware group is a valid, real ransomware group, we need to turn to the spaces where ransomware and other cybercriminal groups operate every day – the deep and dark web. Using Webz.io’s Cyber API, we took a closer look at RansomHouse in an effort to trace their activities and find out whether they are a real ransomware group or not.
Step #2: Use Deep and Dark Web to trace the activities of ransomware groups
There are various places on the deep and dark web where you can start studying ransomware groups more closely. We first started with the obvious option- their site.
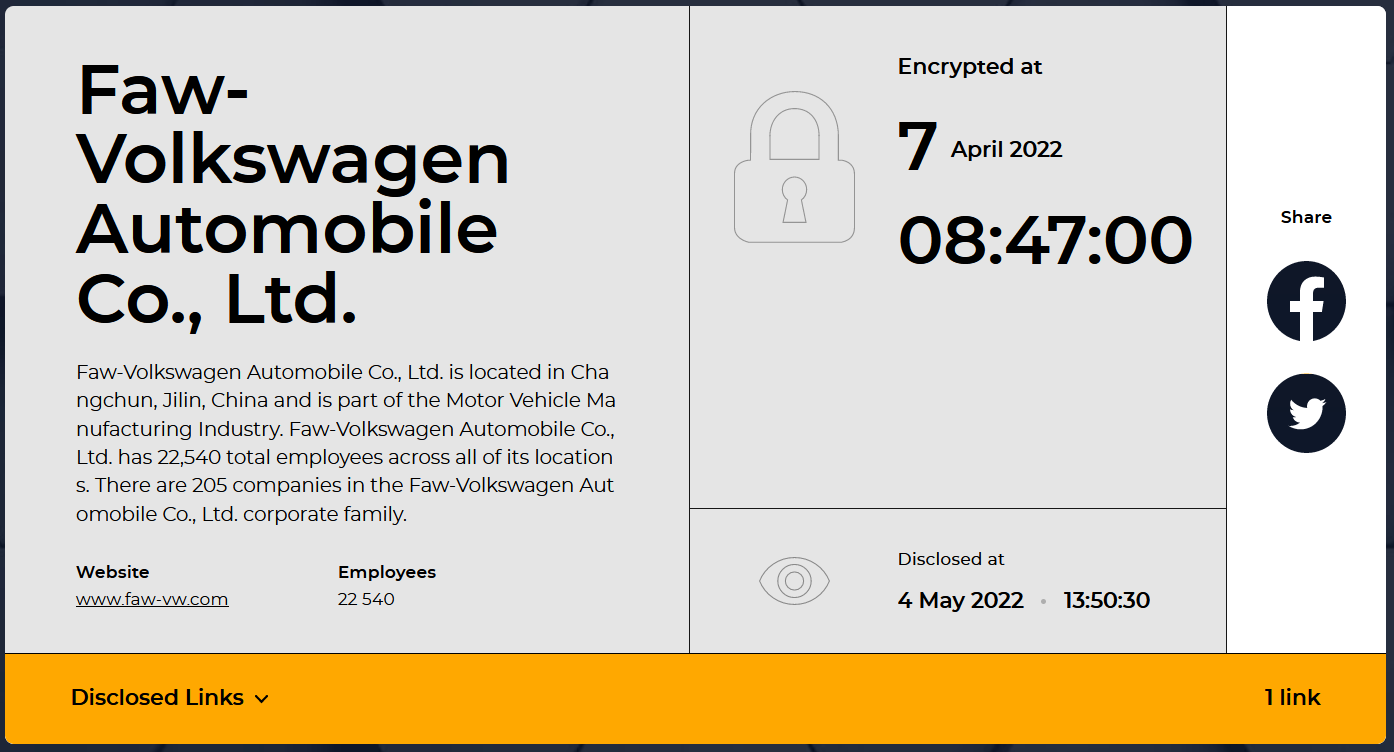
The site of the RansomHouse group
We found the official site of the RansomHouse group on the Tor network. Here was the very first unusual finding we traced. If you look at the images below, you can see a strong resemblance between the design and layout of the site used by the RansomHouse group and the one Hive ransomware gang uses. Some would say that it could be an indication that the RansomHouse group is either an extension of Hive or that they work for a group that is also behind the Hive ransomware.
RansomHouse on Telegram
Next, we turned to the deep web and took a look at Telegram, where RansomHouse, like many other cybercriminals groups, including ransomware gangs, also operates.
How do they use Telegram?
- A private user – the group is operating a private user on Telegram to allegedly communicate and negotiate with the victims regarding the ransom fee
- A Telegram channel – is used to announce the names of the companies they attacked and threaten to expose their data.
- A group – this is a highly unusual group RansomHouse use for PR relations, where they’re communicating with verified journalists and share exclusive information a few hours or even days before the leak is published on the platforms they maintain.
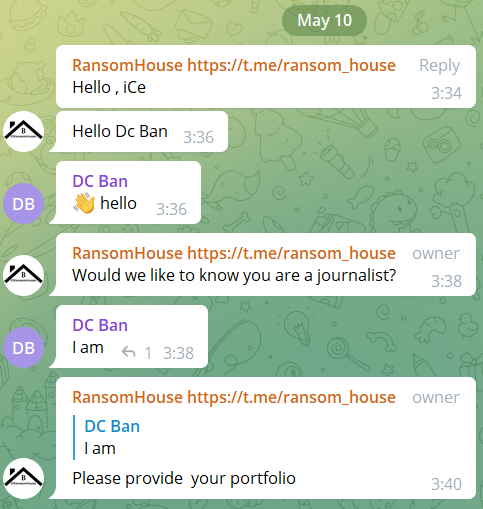
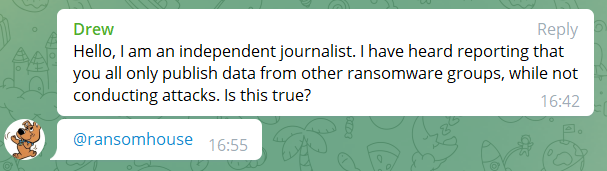
In the image below, you can see that one of the members on the PR group RansomHouse maintains on Telegram, has recently asked the ransomware group if they are responsible for the cyberattacks they mention on their platforms or if they just publish data from other ransomware groups. So far, RansomHouse hasn’t responded.
The group also uses Telegram for other PR campaigns. For example, they post messages on several cyber groups on Telegram where they announce the names of the latest data leak victims and publicize their Tor sites and Telegram groups.
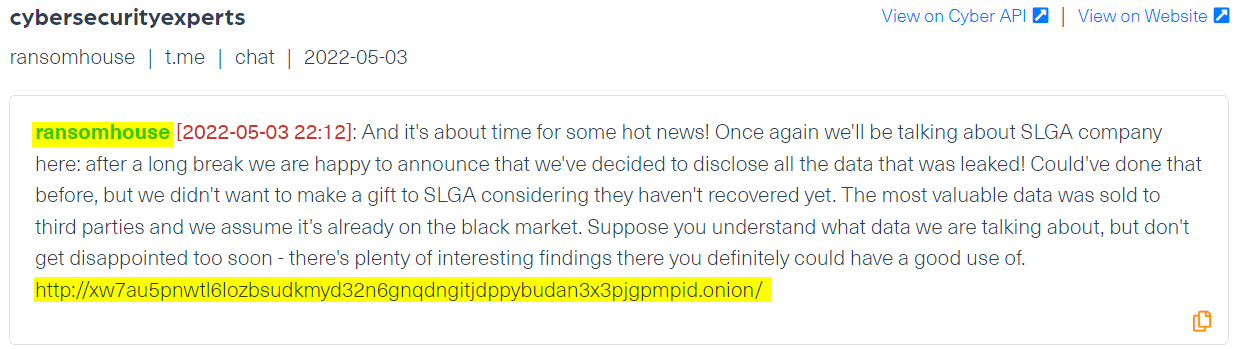
You can see an example of these types of “PR campaigns” on Telegram in the following image, where RansomHouse gang announces that the leak of SLGA’s data is up on the “Cyber Security experts” group on Telegram:
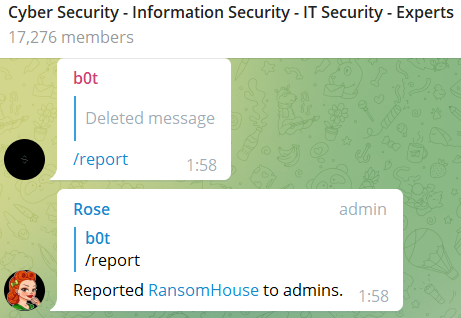
Many of these posts were quietly removed by the admins of the groups, shortly after they were published. Because even on the dark and deep web, threat actors are reported and blocked if they violate the terms of the community.
In the next image you can see how several members reported on Ransomhouse on one of the Telegram groups they posted their “PR messages”:
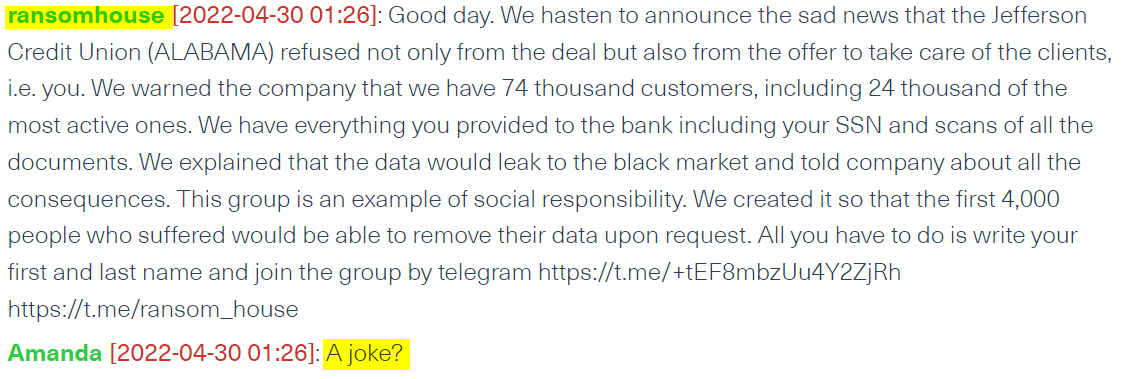
It is important to note that RansomHouse have never explicitly claimed that they were the group who hacked the victims, which puts in question their status as a “ransomware group”.
Because of their avoidance of the topic and the lack of clear proof that they are hacking unknowing victims, the debate continues to roll on the deep and dark web.
For example, a user of a popular hacking forum, XSS.IS, called Snaz claims that RansomHouse is only a data leak site, which is pretty common these days:
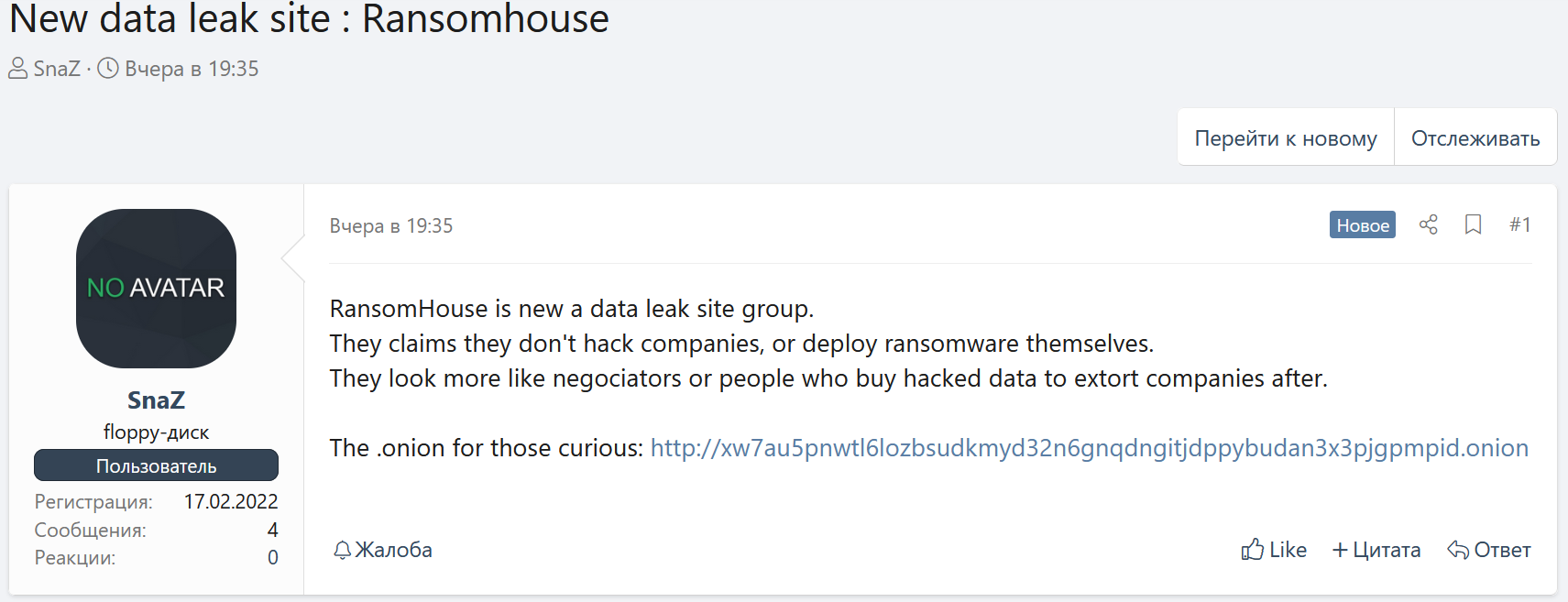
Whether RansomHouse is responsible for the attacks or not, it’s very important to closely monitor their activities and the activity of other cybercriminal groups. A broad coverage of the deep and dark web helps conduct deep actor profiling and gain relevant context to prevent emerging cyber threats.
https://webz.io/dwp/new-ransomware-group-ransomhouse-is-it-real-or-fake/
Published: 2022 05 16 07:34:17
Received: 2022 05 16 07:49:39
Feed: Webz.io Dark Web Posts Ransomware
Source: Webz.io Dark Web Posts
Category: News
Topic: Ransomware
Views: 10
