Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.The Top 5 Telegram Chat Groups and Channels in 2022
published on 2022-05-16 11:43:13 UTC by Yuval ShibiContent:
Since its launch as an anonymous chat application in 2013, Telegram has attracted many cybercriminals. It evolved into a platform that hosts a large volume of illicit content, some of which originates from the dark web. The platform is used for a wide variety of illegal activities and many cybercriminals use it as a preferred platform to conduct their activities.
How Telegram became a safe space for threat actors
After Edward Snowden revealed government surveillance, Telegram was launched in 2013 with the mission to protect private conversations and data from third parties (such as governments). Later on, after the WhatsApp privacy policy scandal in 2021, Telegram became one of the trending apps to replace WhatsApp, while its high privacy standards attracted brand-new users, threat actors.
Unsurprisingly, features such as full anonymity, including the ability to forward messages anonymously and the ability to set up a username in order to protect users’ phone numbers, made it one of the top chat applications of choice for many criminals.
What type of illicit content can be found on Telegram?
Among the main illegal activities that take place on Telegram, you can find:
- Hacking – trade and discussion of hacking-related topics, including malware, vulnerabilities, and ransomware.
- Data loss – Compromised data of brands or individuals which is offered for sale.
- Financial fraud – Stolen accounts, stolen credit cards, fake money, and tutorials to help other financial fraudsters.
- Drug and illicit traffic – Including vendors who trade in prescription drugs, weapons, and other illegal products.
- Radical and extremist discussions – Terror and extremist discussions, racist content such as right-wing movements, neo Nazis, and radical Islamic groups.
With more dark web content posted on Telegram, many dark web threat actors such as hacker groups and ransomware groups operate on Telegram in addition to their original platforms, such as their own sites on Tor.
An example of that is Arvin Club, a ransomware group that has its own website and has lately joined Telegram too, where it opened its own channel:
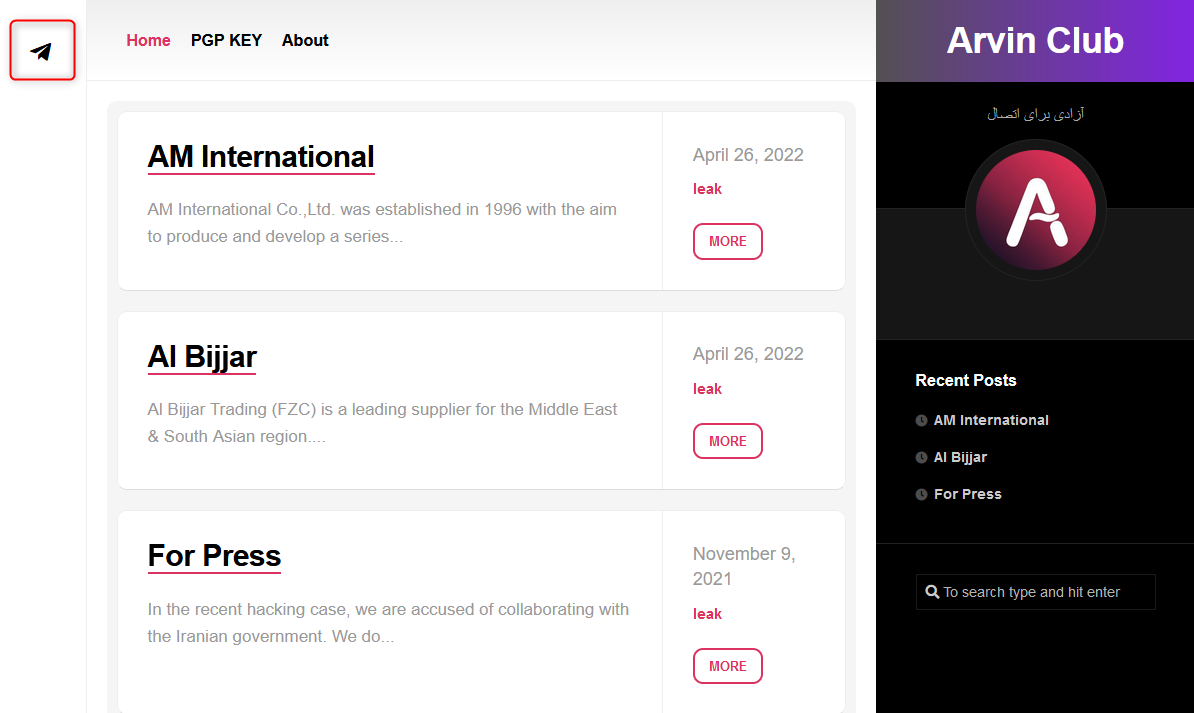
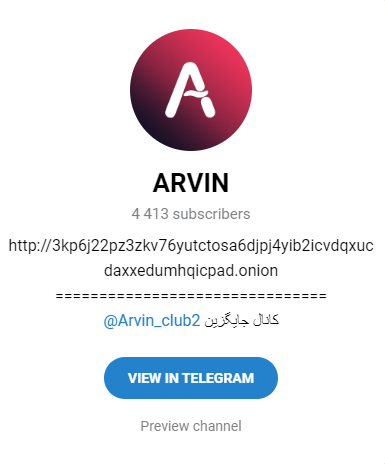
There are many popular and active groups and channels among threat actors and cybercriminals.
We searched for different types of illicit content on Telegram and ranked the top 5 chat groups and channels (in no particular order) by topic:
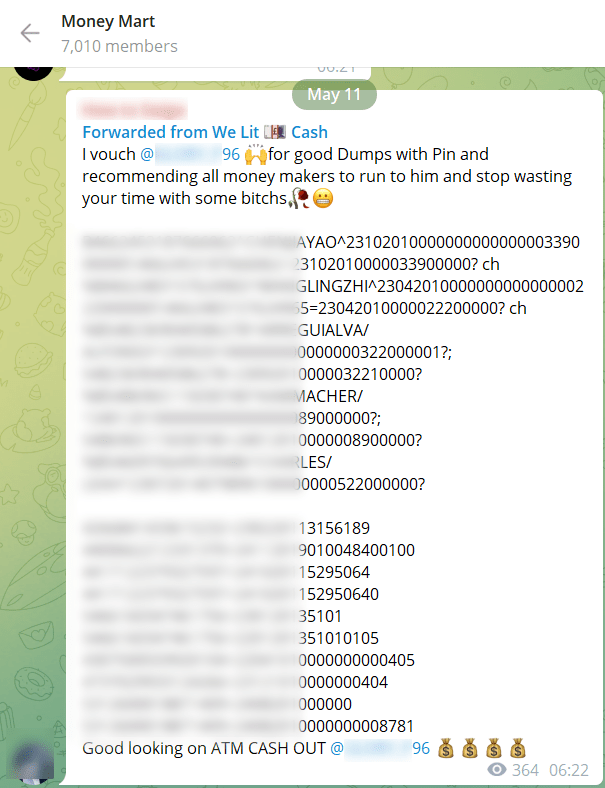
1. Money Mart
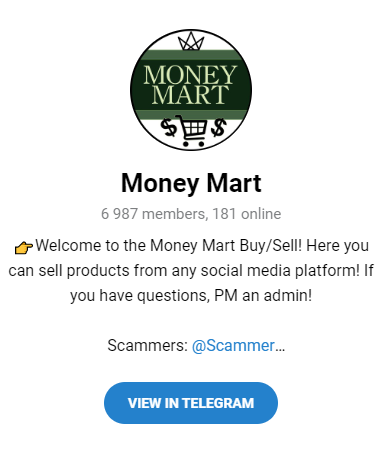
Group Name: Money Mart
Main Language: English
Statistics: 7K members
Topics of interest: Financial fraud and carding link: https://t.me/MoneyMartOG
The Money Mart is a group used as a space to trade PII (personally identifiable information) that has been obtained through carding, credit card leaks, compromised bank account information, and money laundering.
Carding is a form of financial fraud that involves stealing credit card numbers, bank account numbers, and other personal information online and using it for money laundering and other illegal purposes.
In this example, an actor posts stolen credit card details for free and requests payment for additional services.
2. KelvinSecurity
Group Name: KelvinSecurity
Main Language: English
Statistics: 1,408 members
Topics of interest: Hacking (Tools, Newspapers, Scripts, Hacking Methods)
Link: https://t.me/kelvinsecteam
KelvinSecurity is a place for hackers to discuss, share information, consult, and make sure they are up to date with all the latest hacking-related news, as well as on the latest breaches and vulnerabilities. We see discussions and trade of exploits and vulnerabilities, code reviews and hackers sharing tips, threat actors speaking about similar groups to expand their knowledge with, hacking guides and tutorials, and all information relevant to sustaining and growing the hacking community.
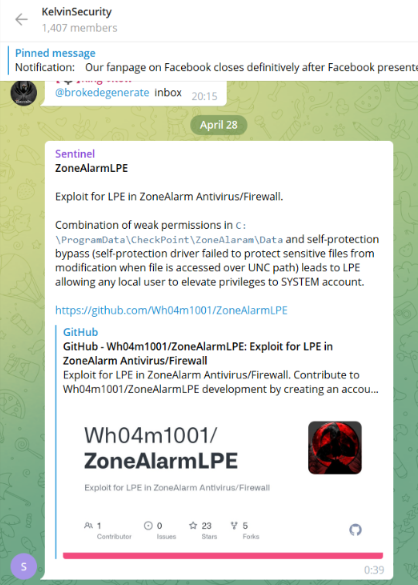
The following example is just one of many malicious posts that are written in the group on a daily basis. The hacker shares an Exploit for LPE (Local privilege escalation) in ZoneAlarm antivirus.
This is a security issue in Check Point’s free edition of ZoneAlarm antivirus and firewall solution that allows a user with limited rights on the machine to inject and execute code with the highest privileges. In simple words – the hacker enters the remote machine with limited user rights, and with the exploit, he gains admin rights in the machine – which can cause serious damage, data breach for example.
3. We Leak Database
Group Name: We Leak Database
Main Language: English
Statistics: 8K+ subscribers
Topics of interest: Data leaks
Link: https://t.me/weleakdatabase
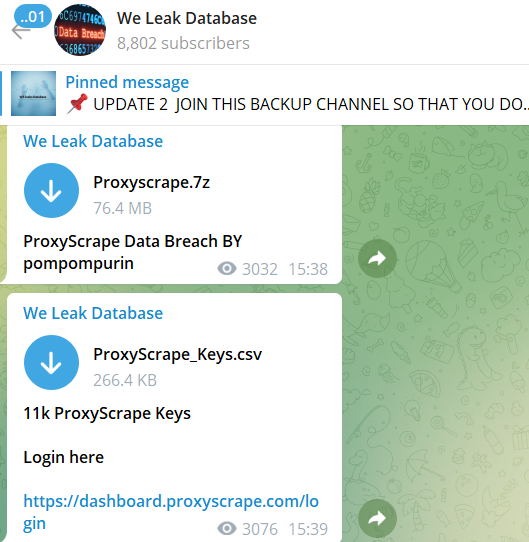
We Leak Database is a Telegram channel any cybercriminal would visit when interested in leaked databases. As seen in the example below, personal and sensitive information is leaked or offered for sale on a daily basis, making it extremely accessible and easy to download or buy stolen personal data on Telegram.
We Leak Database offers different types of compromised data available for downloading. Some of the data belong to individuals and some to organizations, such as business email addresses, login details to different services, credit card details, etc.
4. Perth Ghetto Warriors
Group Name: ℙ𝔼ℝ𝕋ℍ 𝔾ℍ𝔼𝕋𝕋𝕆 𝕎𝔸ℝℝ𝕀𝕆ℝ𝕊
Main Language: English
Statistics: 1k+ members
Topics of interest: Drug trafficking
Link: https://t.me/perthghettowarriors
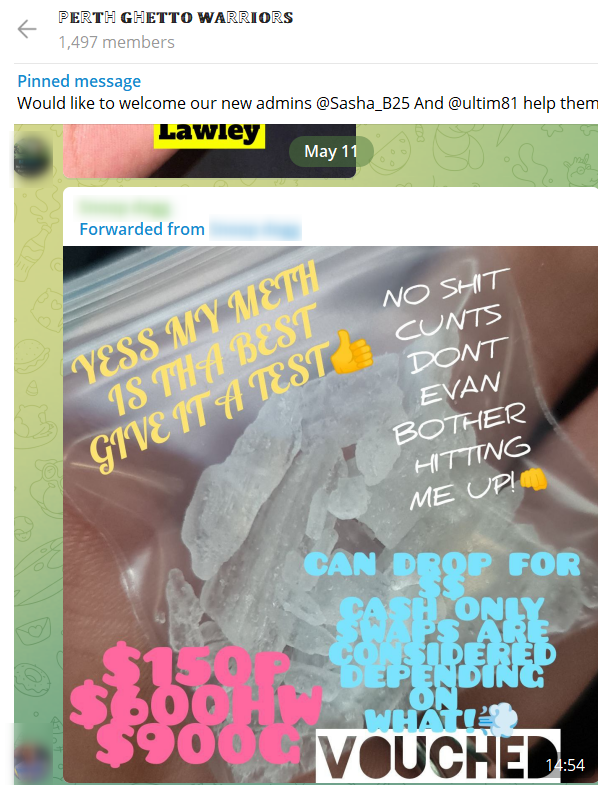
ℙ𝔼ℝ𝕋ℍ 𝔾ℍ𝔼𝕋𝕋𝕆 𝕎𝔸ℝℝ𝕀𝕆ℝ𝕊 is an active drug trafficking group, selling all kinds and sorts of drugs. For years, content about drug trafficking was regularly posted on Tor marketplaces but in recent years this content has shifted to Telegram groups such as this one.
The following example shows a drug dealer selling crystal meth.
5. /bant/ International Random – also Charlottes blog/ModP playground/Slayer
Group Name: /bant/ International Random – also Charlottes blog/ModP playground/Slayer Molochs appreciation
Main Language: English
Statistics: 1K+ members
Topics of interest: Extremism
Link: https://t.me/bantchan
/bant/ is known as an extremist group that offers a safe space for sharing opinions and inciting racist content against Jews, Muslims, the LGBT community, and several other ethnic groups.
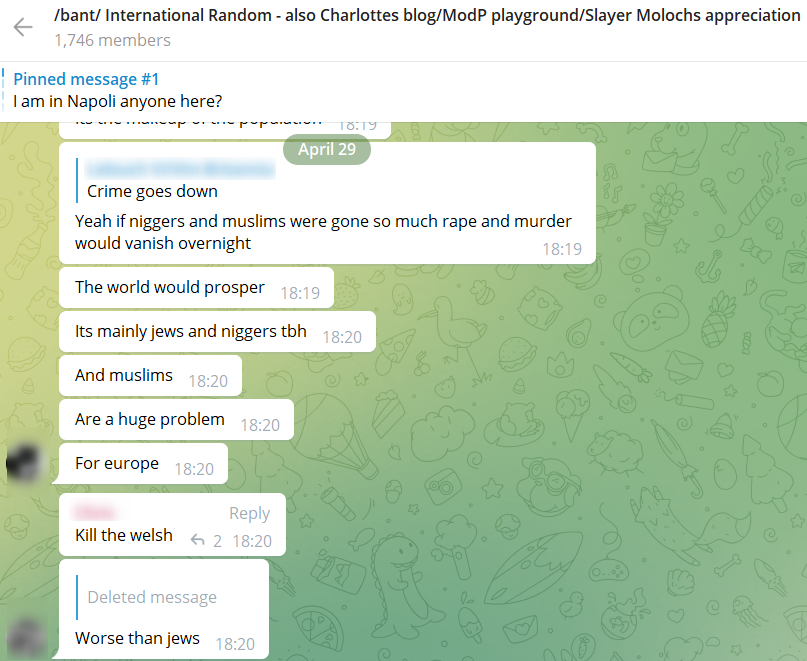
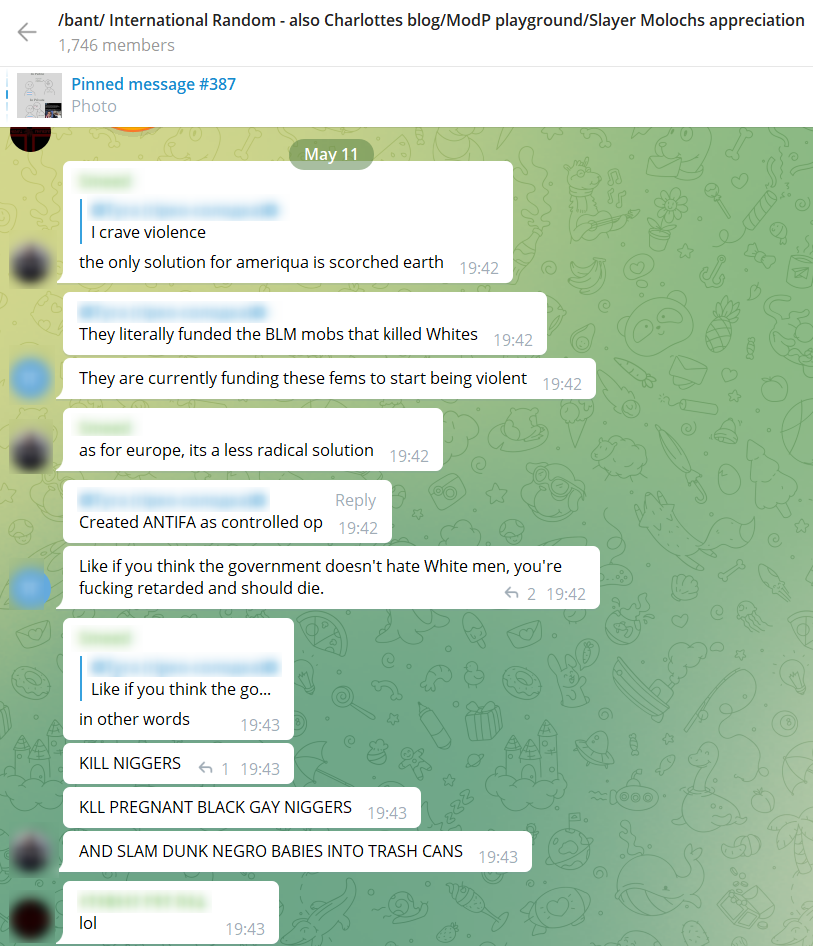
Although some of these Telegram groups and channels are technically open to the public, a large number of these groups are closed and their links are usually shared within specific communities. These standards allow many malicious groups to move their activity to Telegram, where they could freely discuss, exchange and even sell data without revealing their identity. While this has positioned Telegram as one of the favorite chatting apps for malicious groups, it has also made monitoring the platform increasingly challenging for law enforcement and security agencies.
Webz.io provides relevant and recent data from the deep, dark, and open web. Through our automatic discovery tools, cybersecurity organizations, law enforcement officials, and security agents can discover and monitor new threats in Telegram groups, channels, and other relevant sources with our Cyber API.
https://webz.io/dwp/the-top-5-telegram-chat-groups-and-channels-in-2022/
Published: 2022 05 16 11:43:13
Received: 2022 05 16 11:49:37
Feed: Webz.io Dark Web Posts Web Intelligence
Source: Webz.io Dark Web Posts
Category: News
Topic: Web Intelligence
Views: 22
