Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Exclusive: Leaked Employee Accounts Traded ahead of Portland’s Biggest Theft
published on 2022-06-08 12:58:43 UTC by Hagar MargolinContent:
The biggest theft in the history of the Portland government took place in late April, totaling around $1.4 million. According to the official announcement from Portland’s Office of Management and Finance, this was caused as a result of a cybersecurity incident, in which an unauthorized threat actor gained access to an email account belonging to the Portland Housing Bureau. It then fraudulently diverted the payment that was supposed to reach Central City Concern, a homeless services nonprofit that helps cover costs associated with affordable housing projects.
The incident appears to be the latest in a growing cybercrime known as BEC (Business Email Compromise), an email cybercrime scam that targets companies’ business email addresses in order to defraud a company. The BEC scam is considered to be the biggest source of financial losses today, according to the FBI’s Internet Crime Center, totaling $2.4 billion in 2021.
What dark web threats could indicate that Portland Housing Bureau’s email account was compromised?
The trade of digital fingerprints belonging to employees of the Portland Housing Bureau
The unlawful access to email accounts of the Portland Housing Bureau may have been gained with the stolen digital fingerprints of one of their employees. We can find digital fingerprints belonging to the Portland Housing Bureau traded on marketplaces in the dark web. Most of them relate to the information stored on the user’s browser, including cookies, login information from the websites the victim browsed (such as usernames and passwords), IP address, and other operating system details, which can be stolen by using malware.
By using the digital fingerprints of an employee of a particular organization, cybercriminals can breach the organization’s system.
The following log (in the image below), which was crawled from Russian Market, the leading marketplace for the trade of stolen digital fingerprints, is linked to the State of Oregon, Portland. Another important fact to note in this example is that one of the login details mentioned in the log is related to the official domain of the city of Portland. This can link it to the event as it could belong to one of its employees, Portland Housing Bureau, for example.
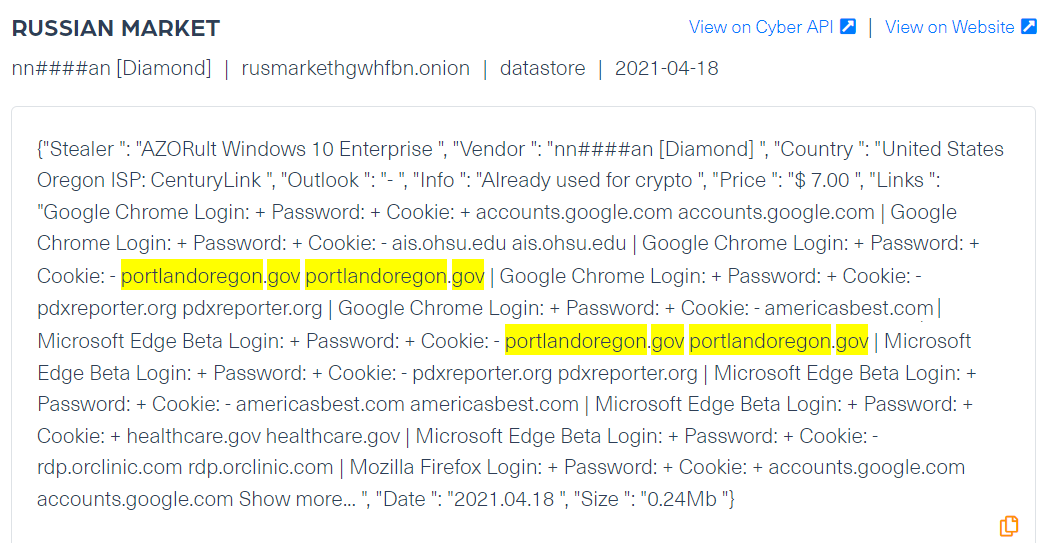
The cybercriminal can use that account to access sensitive data about the organization and the employee the account belongs to. It can include an employee’s email login details, or the details of the organization’s official email address, which was the case in the Portland Housing Bureau incident. This information is directly related to the process of monitoring domains in the dark web, which is key to protecting an organization or its brand.
The trade of breached email accounts that may belong to Portland Housing Bureau employees
One of the most common ways to gain unlawful access to private accounts is by trading breached databases that contain compromised accounts. Monitoring companies’ identifiers in the dark web can lead to posts containing stolen databases which list their company’s name, domain or unique IP address.
When it comes to monitoring the dark web for suspicious activity around governmental organizations, the search needs to be broader, in order to find this kind of posts.
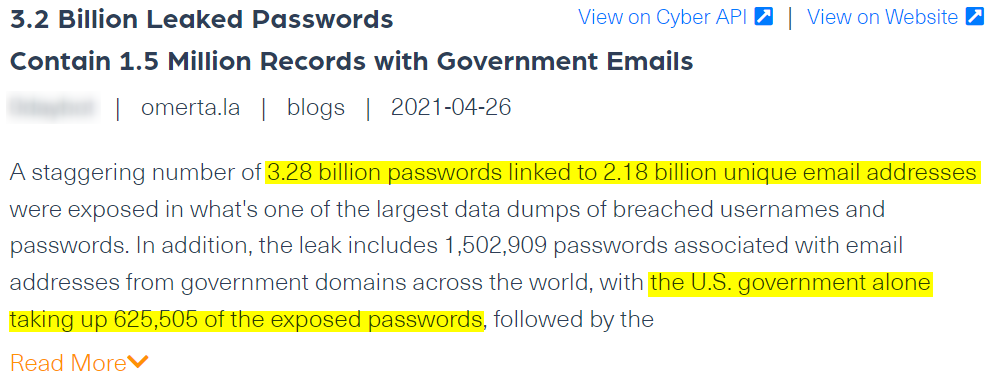
For example, the next post (shown below), states that there are more than 625K stolen emails accounts linked to the U.S. government, some of the compromised emails can be linked to local governments, such as that of the city of Portland.
Leaked accounts belonging to Portland Housing Bureau employees
We used our DBD (Data Breach Detection) endpoint, to check whether any identified personal information was stolen from Portland government employees as a result of a previous data breach. From a search we did, we found 458 email entities belonging to the official Portland city’s domain (portlandoregon.gov), which had been compromised.
The majority of them belong to Portland city employees, but also to those in the Portland Housing Bureau, for example – the email of the administrative services manager of Portland Housing Bureau. We could also find some emails associated with various Portland departments that were leaked, for example, one of the emails belongs to the Bureau of Development Services, and another one belongs to the Information Department of the City.
Leaks of executive’s accounts
Cybercriminals would often look to target executives’ email accounts because it would help them gain quicker access to sensitive information admin rights for complex operations, such as fraud.
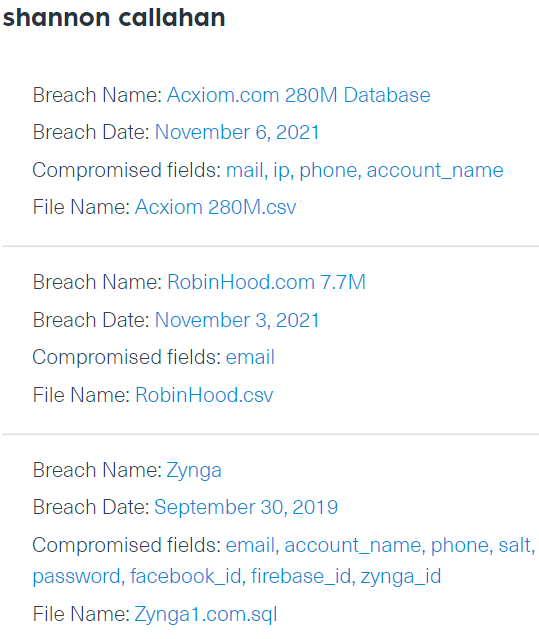
To see whether this may have been the case in this incident, we used our DBD endpoint to run a search for the name of the director of Portland Housing Bureau, Shannon Callahan. The query returned three incidents in which Shannon Callahan’s account had been leaked, in three different breaches between 2019 – 2021. The last one was in Acxiom’s breach.
In the image below, we can find each breach, which is represented by a specific domain that was compromised, and each lists the different compromised fields linked to Shannon’s account. By taking a quick look, we can see that her email, IP address and account’s password were leaked. Each of these details could be used by cybercriminals to access Shannon’s email account and work systems.
Other email accounts associated with the city of Portland that we took a look at were leaked in the Anxiom breach including the ones of Ted Wheeler, the Mayor of Portland, Michelle Kirby, Chief Financial Officer and Director of the Bureau of Revenue & Financial Services in Portland, and many other Portland government senior employees.
By using Webz.io’s Cyber API and Data Breach Detection API, we were able to Identify the potential risk of BEC scam associated with the city of Portland, and with the Housing Bureau. As in other cases, monitoring relevant mentions and incidents in the dark web is key to alerting of potential cybersecurity threats and events in real-time.
https://webz.io/dwp/exclusive-leaked-employee-accounts-traded-ahead-of-portlands-biggest-theft/
Published: 2022 06 08 12:58:43
Received: 2022 06 08 13:10:30
Feed: Webz.io Dark Web Posts All
Source: Webz.io Dark Web Posts
Category: News
Topic: Cyber Security
Views: 12
