Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.How can ransomware affect Human Resource organisations?
published on 2022-06-21 10:03:32 UTC by Paul LopezContent:
HR companies and recruitment agencies alike have some really challenging cyber vulnerabilities - they receive thousands of emails and file attachments from job seekers and aspiring talent every day.
And their role dictates that they have to read these emails and open file attachments. And any one of these e-mails could contain that all important piece of malware that launches a ransomware attack against the business.

They are also really attractive targets to cyber criminals.

The HR department of any organisation holds vast amounts sensitive personal data and financial information that may be of value to criminals. There’s personally identifiable information such as home addresses, bank details, dates of birth and National Insurance numbers that criminals can collect and use for their nefarious activities. Not only can they attack, or target employees personally, but also use this information to launch phishing attacks against the business or its partners in the future.
In fact, this is exactly what happened in 2018 when a well-known UK business’ online recruitment system became the target of a cyber-attack. The following data leak exposed biographical and contact details stored in their databases, which subsequently affected other parts of their organisation.
The cost to the business is estimated to have been in the hundreds of thousands of pounds to fix.
What is ransomware?
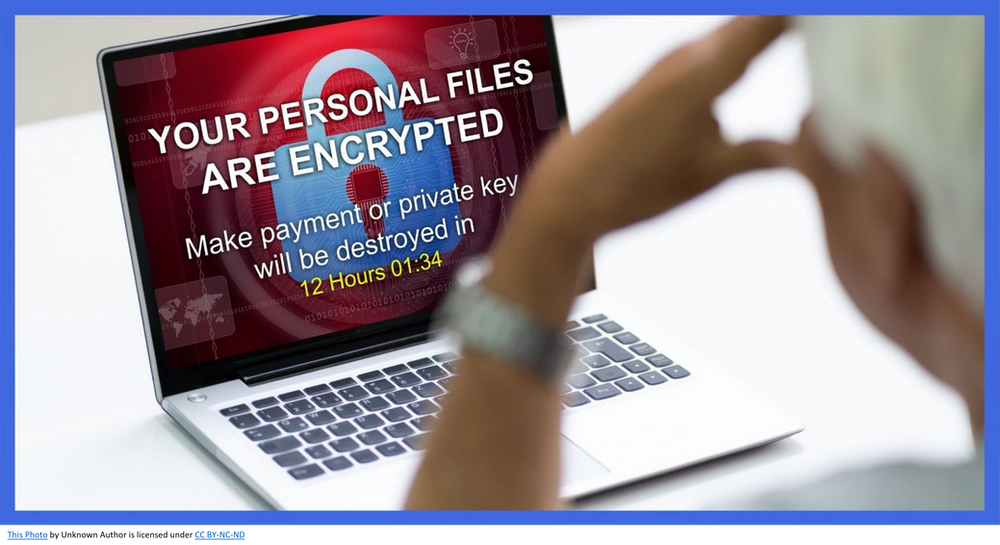
Simply put this is a malicious attack against a network where the criminals get access to data and either steal it, threaten to delete it, or encrypt it. The criminals will then demand a payment for the return of the data. Imagine how this could affect your HR business. Sensitive applicant and staff data as well as financial details for the companies you represent could all be compromised or lost.
The reality is that ransomware is now viewed as a business model and many entities behind these attacks will present themselves as being on the same side as the victim. So, in return for the payment your organisation will often be supported through a process which will return the data that has been encrypted / stolen. It is worthy of note that paying the ransom does not guarantee the return of the data and certainly does not guarantee that it won’t be sold on or published at some point in the future. Also, your network will still be infected, and you are more likely to be targeted again in the future.
The paying of the ransom has moral and ethical undertones that may not be immediately apparent when you are faced with such an attack. Consider the fact that you may be financially supporting terrorists or criminals by paying the ransom.
Goldeneye Ransomware – an HR nightmare
This is a recent example of cybercriminals posing as job applicants as part of a phishing campaign to infect victims in corporate human resources departments with ransomware.

The initial email contained a short message from the fake applicant, directing the victim to two attachments. The first was a cover letter within a PDF which doesn't actually contain any malicious software but is intended to reassure the target that they're dealing with a standard job application. However, the second attachment is an Excel file supposedly containing an application form but which in fact contains the malicious Goldeneye payload.
Upon opening the Excel attachment, the target is presented with a document which claims to be 'Loading' and requires them to enable Macros to view the file. When Macros are enabled, Goldeneye executes a code and begins encrypting the users' files before presenting them with a ransom note.
Like many ransomware strains, this one emanated from Russia. But the important lesson here is that you should never open a link or attachment on an e-mail unless you have verified the source. As explained above this is really difficult for the HR business as it is the cornerstone of their operating model.
Can you protect yourself from these attacks?
As demonstrated in Goldeneye, ransomware is always preceded by an attack on the network itself, commonly through a phishing e-mail or brute force attack. These attacks are increasing in complexity and sophistication meaning that defence against these dark arts needs continual review.
But the key points for protection to remember are:
- Look at the free tools and guidance available on the ECRC site
- Make your network resilient and practice good cyber hygiene – using Cyber Essentials (CE) principles - in particular, use strong passwords and multi-factor authentication if you can.
- Make sure Staff Awareness Training is up to date – spotting a phishing e-mail early will prevent a lot of pain further on down the line
- Make sure all staff know the symptoms of an ongoing ransomware attack and respond quickly to it using a prepared incident response plan. Download a free template on our site.
- Identify common points of failure across the network – patch vulnerabilities and restrict access from malicious sites and IP addresses – speak with you MSPs about this and don’t assume that it will be done automatically.
What next?
The impact of a successful attack against your website or network can be catastrophic and lead to website downtime, loss of data and permanent loss of reputation. But all is not lost.
So, what can I do?
Here at the centre, we would advise you to do the following now
- Join our growing community by signing up to free core membership. You will be supported through implementing the changes you need to make to protect your organisation and staff.
- Look at improving your overall cyber resilience through the free Little Steps pathway we provide to Cyber Essentials – the basic government backed kite mark standard for cyber security. A company operating under Cyber Essentials processes will have 99% of common cyber attacks either fully or partially mitigated. Join the centre as a free member and we will take you as far as the CE certification process. And if you want to pay for the assessment, we can refer you one of our Trusted Partners – all regionally based cyber security companies that can help you become accredited.
https://www.ecrcentre.co.uk/post/how-can-ransomware-affect-human-resource-organisations
Published: 2022 06 21 10:03:32
Received: 2022 06 21 10:12:08
Feed: The Eastern Cyber Resilience Centre
Source: National Cyber Resilience Centre Group
Category: News
Topic: Cyber Security
Views: 13
