Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Quickpost: Cracking PDF Owner Passwords
published on 2022-06-27 00:00:00 UTC by Didier StevensContent:
I added code to John the Ripper to crack PDF owner passwords (JtR cracks PDF user passwords only).
Source code can be found here.
Compiled Windows (Cygwin) and Linux (Ubuntu) executables can be found here.
This change introduces a new format: $pdfo$.
There is no tool for the moment to create this format. Just use pdf2john.pl to create a $pdf$ hash, and then change it into a $pdfo$ hash. To crack the owner password, one needs to recover the user password first.
This is the illustrated process:
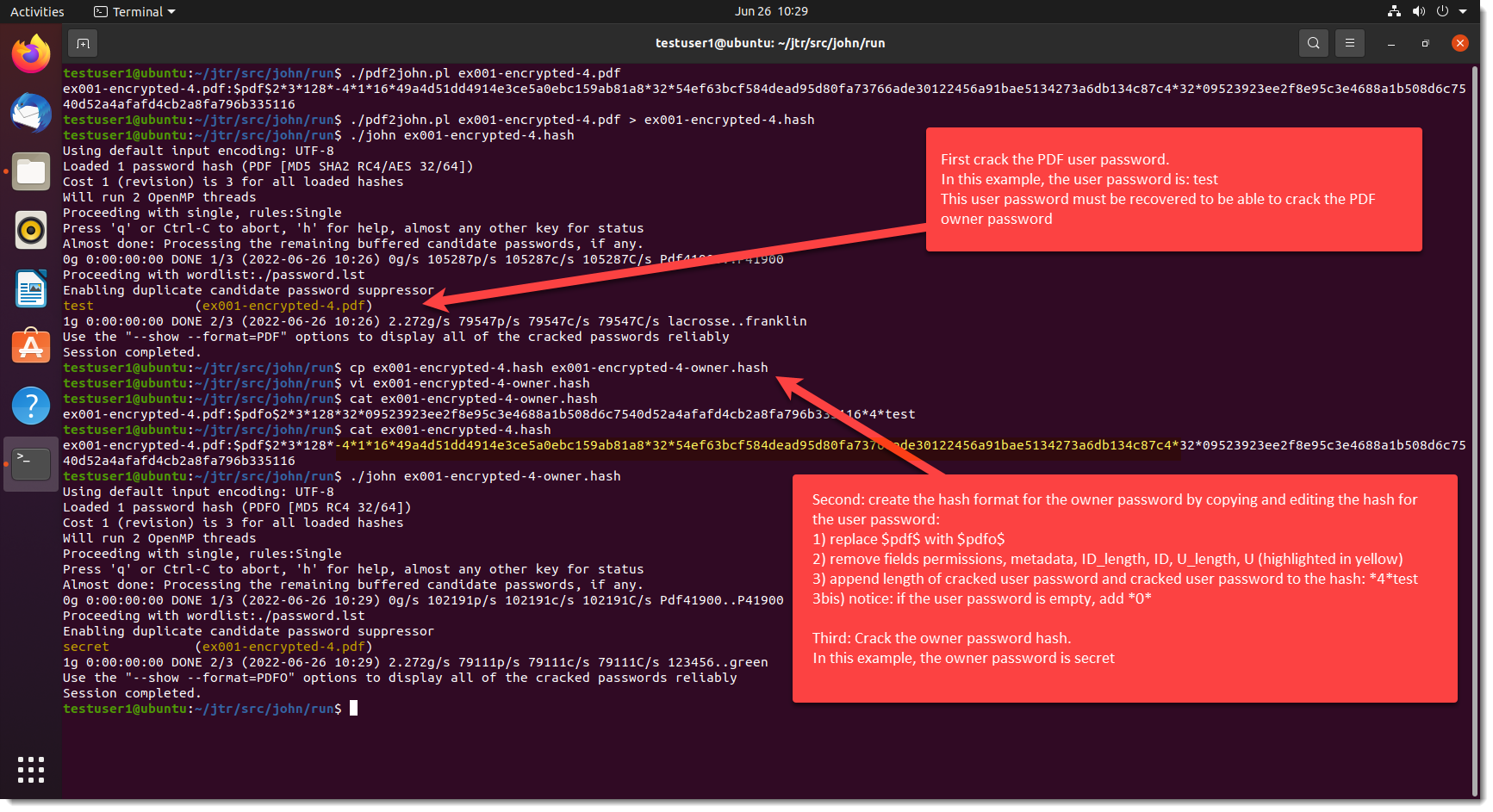
There will be a PR for this change.
Cracking PDF owner passwords is just an academic exercise (writing this code was also just an exercise), as tools like QPDF can decrypt PDFs encrypted with a PDF owner password only without requiring the cleartext PDF owner password as argument.
Quickpost info
https://blog.didierstevens.com/2022/06/27/quickpost-cracking-pdf-owner-passwords/
Published: 2022 06 27 00:00:00
Received: 2022 06 27 00:09:15
Feed: Didier Stevens
Source: Didier Stevens
Category: Cyber Security
Topic: Cyber Security
Views: 11
