Welcome to our
Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.How Pakistan's Critical Infrastructure Was Hacked? - Technical Analysis
published on 2017-04-11 17:43:00 UTC by RafayContent:
There may be various motives for NSA hacking into Pakistan's internet infrastructure, intercepting and monitoring the traffic maybe one of the reasons. However, there is more to it. As per various leaks from Edward Snowden reveals couple of NSA's deadliest weapons and most notable being quantum-insert attacks. As per one of the leaked documents confirms this attack was being utilized in order to infect a target located in Miran Shah.
Quantum Insert Attacks
Quantum Insert Attacks are an example of Man on the Side Attacks which require precise positioning of attackers rogue servers (Monitor/Shooters) in order to win a race against legitimate servers to deliver malicious content. The success probability of this attack relies upon the placement of the server. The closer the malicious servers are placed to the target the more of chances of it winning the race against the legitimate servers.For instance, if a user based in Pakistan surfs Facebook.com, the PTCL or multinet being ISP would be technically closer to the target than the legitimate Facebook servers which has more probability of winning the race and delivering the malicious content. This happens to be one of the major reasons why NSA hacked into Pakistan's ISP in order to be technically closer to the target, hence increasing attack probability.
How Quantum Insert Attack Works?
Quantum Insert Attacks are not new; they are a type of TCP hijacking attacks that have existed in one form or another. In order to understand TCP hijacking attack, we have to understand how three-way handshake works.TCP being a connection-oriented protocol requires sender/receiver to establish a three-way handshake. If you type Facebook.com in your browser, one of the first steps browser takes is to perform a DNS query to find out the IP address associated with Facebook.com, the query returns 66.220.159.121. The client will then establish a TCP/IP three-way handshake to server 66.220.159.121.
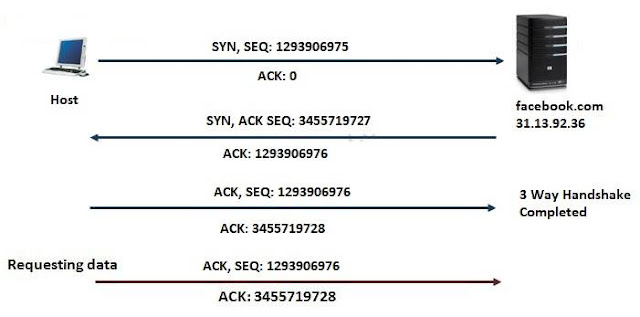
The following diagram illustrates how TCP/IP three-way handshake works:
i) Host A sends a packet with SYN flag, along with it, it also generates and sends a random ISN (Initial Sequence Number) i.e. 1293906975 along with an ACK=0.
ii) Host B, upon receiving the SYN, responds with SYN, ACK with its own random sequence number 3455719727 and increments Host A's sequence number by 1 and sends it back with ACK=1293906976
iii) The host A finally completes the three-way handshake by incrementing Host A's sequence number by one and sending back.
From above process, it is evident that for establishing three-way handshake both client and server will generate a random 32 bit sequence number from which it will start counting the segments transmitted.
Host B will only accept the segments from Host A when correct SEQ/ACK number is transmitted. In case, if an attacker obtains sequence numbers used for establishing session, they will be able to craft TCP packets containing the sequence number and using spoofing IP address it will make the receiving system believe that the segments have appeared from a legitimate host. This is known as TCP Hijacking
When the legitimate packet arrives afterwards, it will be discarded as it will have duplicate sequence number. One critical condition for its success is that the response from the malicious server must arrive before the legitimate response from the webserver, due to this very reason the placement of malicious server is critical for the success of this attack. From the document mentioned above, it was clear that the success ratio for the malicious response to arrive before the legitimate response based in Pakistan was approximately 48%.
Host B will only accept the segments from Host A when correct SEQ/ACK number is transmitted. In case, if an attacker obtains sequence numbers used for establishing session, they will be able to craft TCP packets containing the sequence number and using spoofing IP address it will make the receiving system believe that the segments have appeared from a legitimate host. This is known as TCP Hijacking
When the legitimate packet arrives afterwards, it will be discarded as it will have duplicate sequence number. One critical condition for its success is that the response from the malicious server must arrive before the legitimate response from the webserver, due to this very reason the placement of malicious server is critical for the success of this attack. From the document mentioned above, it was clear that the success ratio for the malicious response to arrive before the legitimate response based in Pakistan was approximately 48%.
From the above demonstration by Fox-it, it is clear that Quantum-Insert Attack requires two crucial components; the first is the monitor which sits and passively collects session information and feeds it to the shooter. The shooter then using the sequence/ACK number hijacks the session and tries to inject the malicious content into the TCP stream before the legitimate response.
As discussed before, placement of the monitor/ shooter is extremely crucial as they have to be near to the target and this happens to be one of the major reasons why NSA is particularly interested in hijacking ISP's for better placement of their monitor/shooter in order to win race against legitimate web-servers to inject malicious content.
Putting Pieces Together
1. NSA has hacked into various Internet Service Providers in order to deploy its passive traffic collection sensors or monitors around internet backbone.2. The huge chunk of data is then fed to analysis and co-relation engines such as XKEYSCORE.
3. Based upon the analysis of tools such as XKEYSCORE, a target profile is built, for instance "All TOR/VPN users in a certain area", "all PGP usage in Iran" etc. XKEYSCORE can also be queried for most frequent web searches and most frequently visited websites (HTTP).
4. Once the target has been selected and attack conditions have been identified; attack conditions can be for instance, all users based in F-8 Islamabad browsing http://www.torproject.org/. This information is then fed to monitors who once these conditions are met, would leak information to the shooter which then utilizes Quantum-Insert Attack in order to inject malicious response into HTTP response for http://www.torproject.org/ before the actual response arrives.
5. Once the target is compromised, the post-exploitation phase begins which is aimed at collection information as well as performing lateral movement inside of network.
Detection & Defenses
1. It is to be noted that HTTPS along with HSTS (Strict Transport Layer Security) would reduce the effectiveness of this attack. IPSEC VPN would also prevent this attack as it encrypts transport/application layer messages.2. One of the other ways to detect this attack would be to check for TTL (Time to Live) value of the IP Packet. When an IP packet is sent across the network, it sets the TTL value which is decremented by each hop. Since in this case the monitor/shooter would be near to the target, the TTL value of the spoofed packet would be less than the real packet.
3. Since, both the legitimate and malicious packets will arrive with same sequence number. We can create a signature on IDS/IPS to keep track of the segments for same sequence number.
http://www.rafayhackingarticles.net/2017/04/how-pakistans-critical-internet-Infrastructure-was-hacked.html
Published: 2017 04 11 17:43:00
Received: 2022 07 18 17:48:10
Feed: Ethical Hacking - Rafayhackingarticles
Source: Ethical Hacking - Rafayhackingarticles
Category: Cyber Security
Topic: Cyber Security
Views: 17