Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Local Government – do you have a plan in place if you fall victim to a cyber-attack?
published on 2022-06-29 10:31:32 UTC byContent:
Cybercriminals have shown repeatedly that they love data, and the more sensitive it is the more money they can extort if they steal, encrypt, or restrict access to it.

Local governments hold millions of gigabytes of this type of data – including financial and legal information, sensitive planning details, confidential medical data, data relating to children at risk and even vulnerable women – including locations of domestic violence refuges.
And poor cyber security has led to numerous high-profile attacks against councils in the past few years. The London Borough of Hackney was subject to a ransomware attack in 2020 in which personal staff data was released, land registry information was scrabbled, and local authority payments had to be halted. Sensitive personal data also led to a year long police operation to try and mitigate the risks to individuals caused by the loss and publication of this data.
More recently in 2022 an Essex based local government organisation was subject to a man in the middle attack where they paid almost £4 million to a criminal gang, thinking that they were paying a trusted supplier. Only quick thinking and action meant that they did not lose the money permanently.
As more services go online and information becomes digitized the challenges faced by local governments and the solutions to the areas of attack become more complicated. But a key part of any local government strategy is ensuring that you have a plan when things go bad.
As Maya Angelou famously said,
“Hoping for the best, prepared for the worst….”
What is incident response?

It will often start with a member of staff asking, ‘Why can’t I open my files?’
But remember that many cyber-attacks are conducted by stealth, and they will not always want to be found. So, the first consideration is ‘Do we have a process to proactively look for cyber-attacks even when everything is operating normally?’ As a member of the ECRC you will receive free updates about vulnerabilities that have been flagged by other organisations specifically to help the wider community. Including you.
For many companies today, the first time they realise they need an Incident Response Plan coincides with the time that they realise they don’t have one. The plan itself is simply a document containing the details of key personnel who you can contact if you are worried that you have been victim of a cyber-attack. It also contains key information to help you move through the various stages of containment and then recovery. Having a good response plan means that you are more likely to come through the experience more quickly and efficiently and with less of your systems exposed to the hack. And the responsibility for establishing and maintaining a plan is down to the business owner and not the managed service provider you use for your IT.
If you find that you have been breached, you may never find out exactly how – what is important is that at that point the criminals still have access to your network. The wrong decisions now could have a devastating effect on your business, and you could face additional, financial, and reputational loss if you don’t make the right decisions next.
As can be seen in the below diagram you will start in the triage stage of the breach, trying to figure out what the scale of the breach is and the impact now and in the future.
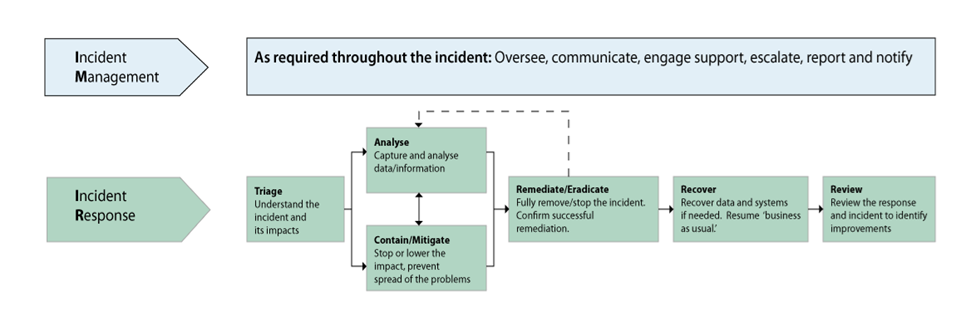
What can I do now?
Increasingly cyber experts are accepting that blocking all cyber-attacks is not an achievable outcome and that it makes sense to be prepared for when the breach occurs. Being well prepared for a breach is a key step in making yourself resilient in the online world.
To save you the time of having to start one from scratch – go to our tools section and download an incident plan for free. All you have to do is read it and fill in the key bits of information and you have a document that you can rely on if the worst actually happens.

Practice Practice Practice
Once you’ve got an incident response plan prepared the next stage to establish your readiness is to try it out in a safe environment. The National Cyber Security Centre’s Exercise in a Box is an excellent starting point. This exercise will help you to check out how well you and your business can respond to a cyber-attack.
Further guidance & support

You can contact the Cyber Resilience Centre for guidance and support through our e-mail enquiry system.
Join our growing community by signing up for our free core membership. Core members receive regular updates which include the latest guidance, news, and security updates. Our core membership has been tailored for businesses and charities of all sizes who are based across the seven counties in the East of England. Our site also contains numerous guidance and tools that can be accessed free for charge.
You may have access to some sort of IT support within your business and we recommend that you speak to them now to discuss how they can implement cyber resilience measures on your behalf. And find out if a response plan is currently held for your business and whether it is still in date!
Finally, whilst we would suggest that you don’t rely on insurance alone to protect you from all of the worlds cyber threats, it would be prudent to check what, if any insurance you have and what it actually covers. It could prove invaluable to help you quickly navigate through those early hours of an incident and should form part of the organisation response to an incident of this type.
Incident Reporting
All the police forces across the Eastern region have dedicated specialist cybercrime teams who are highly trained and experienced in investigating cybercrime and at putting the victim’s needs at the forefront of the investigation.
Report all Fraud and Cybercrime to Action Fraud by calling 0300 123 2040 or through the online portal. Forward suspicious emails to report@phishing.gov.uk. Report SMS scams by forwarding the original message to 7726 (spells SPAM on the keypad).

https://www.ecrcentre.co.uk/post/local-government-do-you-have-a-plan-in-place-if-you-fall-victim-to-a-cyber-attack
Published: 2022 06 29 10:31:32
Received: 2022 07 23 00:32:59
Feed: The Eastern Cyber Resilience Centre
Source: National Cyber Resilience Centre Group
Category: News
Topic: Cyber Security
Views: 16
