Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.How Can Monitoring the Dark Web Help Prevent the Next Cyber Attack?
published on 2022-06-29 10:19:04 UTC by Yuval ShibiContent:
In today’s reality when 30K companies are hacked every day, it is impossible to ignore the need to secure company assets.
According to the FBI’s 2021 Internet Crime Report, 847,376 businesses reported cyber attacks in 2021, totaling $6.9 billion – an increase of 7% in reported cyber attacks from 2020.
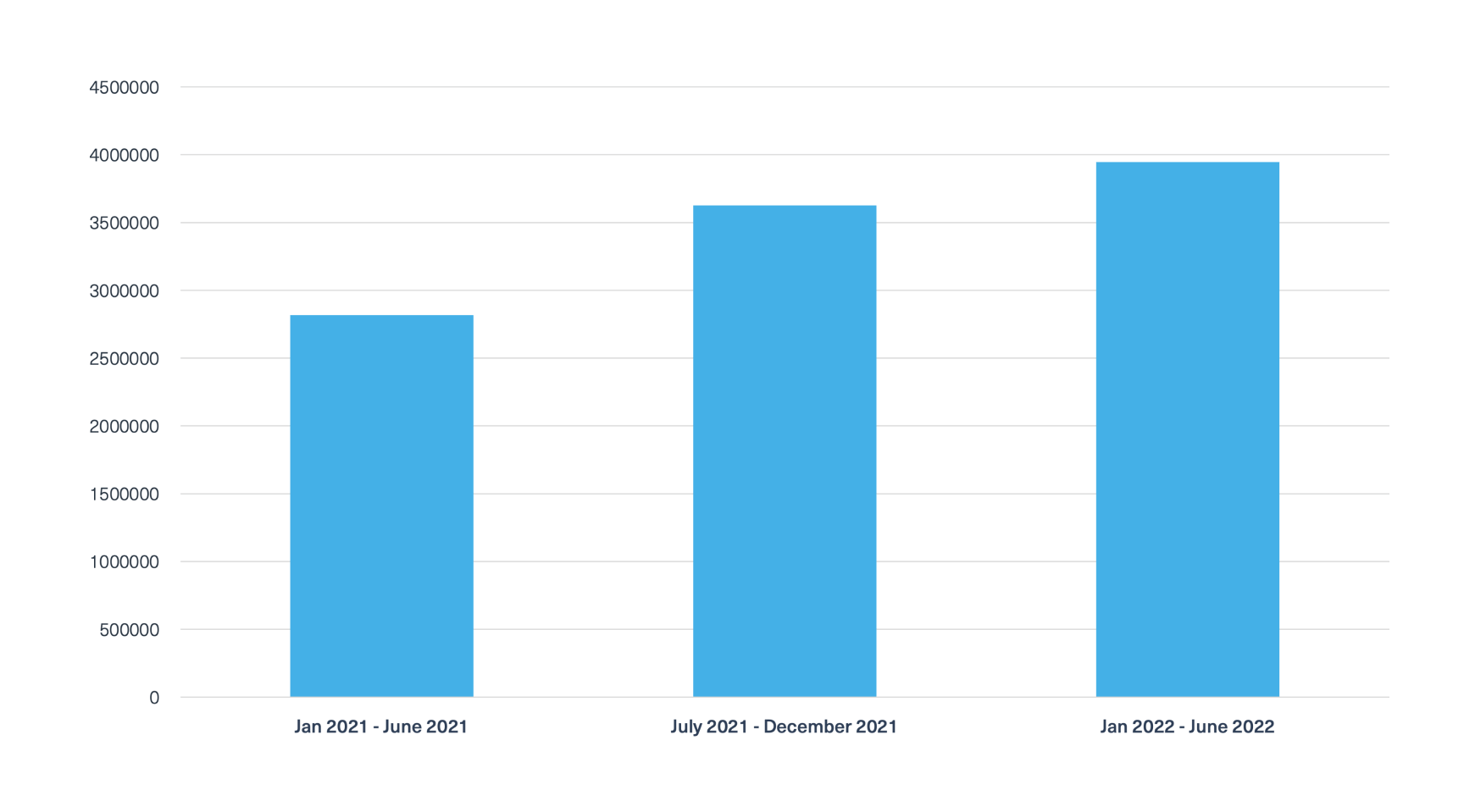
The volume of posts relating to companies’ compromised data on the deep and dark web is staggering. We used our deep and dark web data to search for posts that contain data leaks that relate to companies over 3 periods of 6 months:
How can a cyber attack harm a company?
A cyber attack can cause great harm to every company. Some of the implications are straightforward like money and data loss. But there are also other, less known implications, such as:
- Exposure to future attacks – data loss and service interruptions can expose companies to further malicious threats.
- Downtime and major service interruptions
- Reputational damage
How can an early indication from the dark web help prevent cyber attacks?
As Cyber analysts at Webz.io, we see early indicators of cyber attacks on a daily basis. The dark web is a space where vulnerabilities are posted and discussed along with matching exploits to specific platforms, services and domains. We can also see compromised data (brand-related and PII) that is found everywhere on the deep and dark web, including on marketplaces, hacker forums, paste sites, chat applications, and many other sites. Shared information of this type can lead to a data breach, and eventually a hacking attack.
Once brand-related data is published, threat actors can use them to access a system or launch other types of cyber attacks. Any valuable data a business possesses can be the target of cybercriminals, and that’s why companies need to monitor and detect related data on the deep and dark web so they can stay ahead of the threat actors.
What assets can be found on the dark web and how can they lead to attacks?
| Entities and Assets | Potential Attack |
| Company’s data – Strategic plans, network infrastructure, and written patents and scripts and codes. | + Data breaches and the leak of stolen data. + Malware attacks: ~ SQL Injection attacks. ~ Man-in-the-Middle (MITM) attacks. ~ DDoS attacks. + Ransomware attacks. + Fileless attacks. + Phishing and social Engineering attacks. + Zero-Day exploits. + Cross-Site Scripting (XSS) attack. |
| Company identifiers – Supply chain, services, domains, IPs, business email addresses and passwords, business phone numbers, bank accounts, credit card numbers, CVVs, and transactions. Employees/customers PII – Personally identifiable information such as residential address, SSN, and full names. | + Data breaches and the leak of stolen data. + Phishing and social engineering attacks. + Zero-Day exploits. + Credential reuse. |
The table above illustrates the types of brand-related data that is found on the dark web along with the entities and assets that each type of data includes, and the potential cyber attacks that can be conducted using them.
Examples of early indications can you find on the dark web
Below are examples of posts on the dark web, which feature brand-related data that could lead to an attack against enterprises:
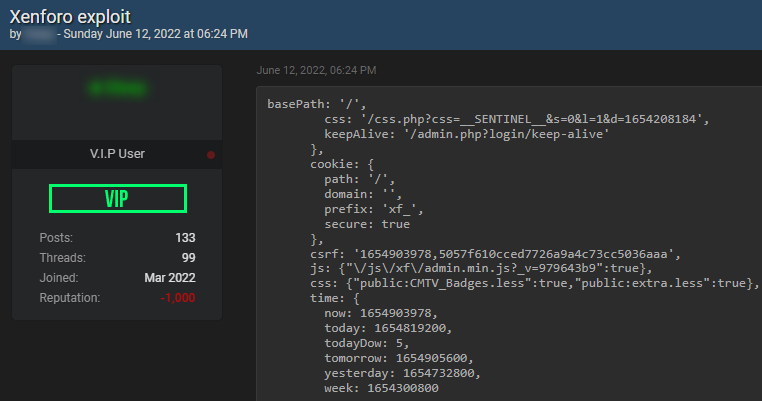
Exploit on a hacking forum
The next image shows a post a hacker published on breached.co offering a ready-to-use exploit script for the Xenforo.com platform:
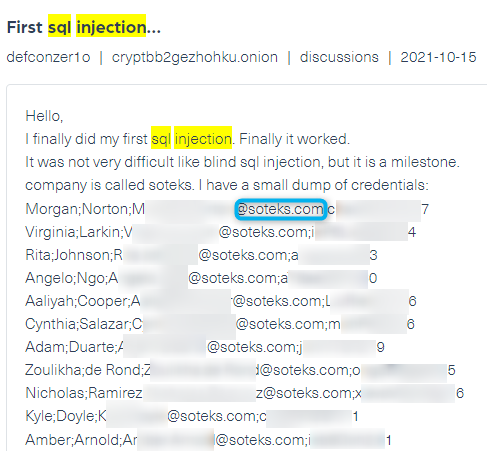
Leaked credentials
A threat actor discusses a successful SQL-injection attack in a post he shared on CryptBB, a Tor-based dark web hacking and carding forum. In the post (see below), he claims he breached the domain of the platform soteks.com, and published data belonging to users including names, email addresses, and passwords.
How can you detect early indications on the dark web and prevent cyber attacks?
The best way to detect company assets on the dark web is to consistently monitor the dark web for any leak or theft of data which could provide access to network systems and endpoints.
Here are two simple steps you can take to ensure you can detect early indications:
- Check if you or your customers have already been compromised – Visit Webz.io Cyber API, DBD and Dark Risk endpoints to run a query and see if anything comes up. If so, change passwords for any accounts that may have been compromised.
- Monitor dark web networks to prevent breaches – Threat actors publish and sell compromised data daily on several deep and dark web platforms. Make sure you continuously monitor for assets to detect them as soon as they are posted and take action in real time.
Cyber attacks are a threat to the stability and reputation of every business today. The recovery process from an attack can take a long time, money, and effort. It’s easier to monitor the dark web – and simply prevent them.
https://webz.io/dwp/how-can-monitoring-the-dark-web-help-prevent-the-next-cyber-attack/
Published: 2022 06 29 10:19:04
Received: 2022 07 26 07:12:27
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 12
