Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Be alert to a new highly-sophisticated PayPal phishing kit
published on 2022-07-27 10:13:41 UTC byContent:
A new phishing kit has been used to leverage poorly-secured websites designed using WordPress to harvest a vast quantity of personal information. Are you at risk?

The level of information requested from the fake PayPal pages exceeds the typical credential-stealing nature of threat actors and seeks to acquire significant payment and personal data relating to individuals.
The attack begins by exploiting WordPress websites with low security to install a file management plugin, which then allows the phishing kit to be uploaded to the compromised website.
This is further complimented with the method of cross-referencing IP addresses for domains of legitimate companies, including some in the cybersecurity sector.
The fake PayPal pages have been created with an extremely high level of authenticity, as shown below:
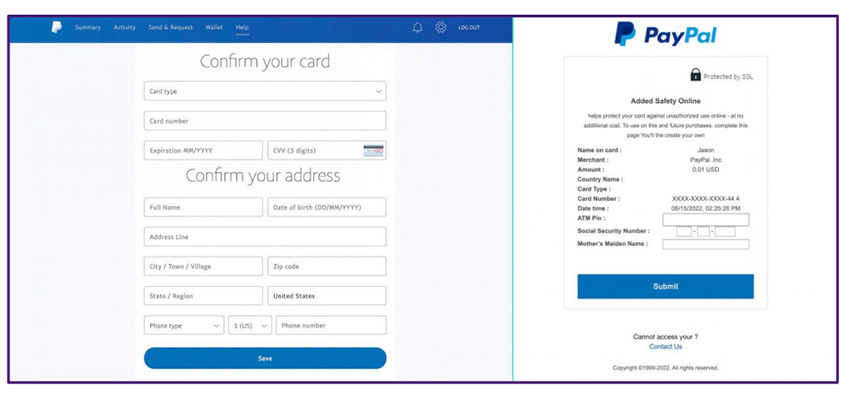

For added authenticity, victims are taken to a replica PayPal page with a CAPTCHA-style challenge where the characters of a slightly distorted image are required to be entered into a text box.
Following this, the next page requests PayPal login details which are delivered directly to the threat actors.
The phishing kit doesn’t stop there though, with a message on screen suggesting that the users PayPal account has “unusual activity”, and they are redirected to a further page requesting many more personal details such as bank card numbers, CVV, PIN details and confirmation of security questions including mother’s maiden name.
Further information is then requested where the user is asked to provide their email and password to “link their PayPal account” which would allow a threat actor to bypass multi-factor authentication (MFA) of PayPal and provide full access to the victims’ email address and any further MFA on other accounts set up to verify via the email.
This can be used to then pivot to other targets and exploit the victim further.
Finally, the user is prompted to supply identity documents with a realistic page containing full instructions on how to photograph identification documents and upload them.
Successfully gathering these documents by a threat actor, along with the huge level of detail already gained, would be highly valuable and could allow the threat actor the ability to commit high value fraud and/or money laundering.
These details would additionally be sufficient to open bank accounts, cryptocurrency trading accounts or clone payment cards.
This campaign shows the levels that threat actors are prepared to go to obtain personal and financial information of potential victims. The use of the CAPTCHA request at the very beginning of the process is thought to dupe potential victims and from there on in they believe they’re on the genuine PayPal website.
Organisations are encouraged to increase training to highlight the professionalism of these phishing kits to avoid personnel falling victim to the campaigns. Personnel should be advised to check the domain name displayed and ideally type in the correct URL in a new tab to ensure the security of their accounts.
Reporting
Report all Fraud and Cybercrime to Action Fraud by calling 0300 123 2040 or online. Forward suspicious emails to report@phishing.gov.uk. Report SMS scams by forwarding the original message to 7726 (spells SPAM on the keypad).
https://www.emcrc.co.uk/post/be-alert-to-a-new-highly-sophisticated-paypal-phishing-kit
Published: 2022 07 27 10:13:41
Received: 2022 08 01 02:52:19
Feed: The Cyber Resilience Centre for the East Midlands
Source: National Cyber Resilience Centre Group
Category: News
Topic: Cyber Security
Views: 25
