Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.OSINT Feed: The Missing Piece in the SOC Puzzle
published on 2022-08-10 12:32:09 UTC by Liran SoraniContent:
Over the past years, we have witnessed the acceleration of digital transformation, with more and more organizations shifting their business models and technology to keep up with demands and competition. Many of the solutions they use led to a shocking amount of enterprise data being shared over the web, on the cloud, and sometimes with external vendors.
Statistically speaking, today there is more compromised organizational data than ever before. Data that can put the enterprise at risk and generate high losses both in revenue as well as reputation.
How can cybersecurity keep up?
The first SIEM (Security Information and Event Manager) was invented in the late 1990’s with a promise to solve IDS (Intrusion Detection Systems) alert overload and streamline the growing number of false positives.
These solutions have evolved over the years, offering more sophisticated tools, solutions and methodology to address the same pain points.
But cyberattacks are constantly shifting, as cybercriminals increasingly use more anonymized and sophisticated methods. Threat actors also continuously communicate, create and collaborate with other hackers. This makes even the most advanced and automated solution too slow to stay ahead.
The next challenge of cyber threat intelligence solutions
In the face of these challenges, namely the cybercriminals’ technical sophistication and the growing number of cyber threats, today’s SOCs (Security Operations Centers) developed their practices and systems to ingest as many logs as possible – to create more queries and by that – receive more actionable alerts for SOC analysts.
Sounds simple, right? The reality rarely is. Because more logs does not equal more security. In fact, more logs can clutter and overburden analysts with noise and false positives that makes creating actionable insights a daily struggle.
Another challenge SOCs are facing today is that criminals are shifting to TTP techniques, meaning once they get access to a restricted host, they do not leave any traces behind to help the breached organization locate and block the breach.
Take for example a Windows server, cybercriminals today are able to write a malicious script by using existing tools and run them with a power shell which gives it extended permissions.
This type of exploitation is harder to uncover as the threat actor is using the same trusted tools on the host, which means that the only way to detect it is by carrying out a behavioral analysis on the host or to gather intelligence on these types of activities from the dark web and cyber criminals discussions sources.
Is the SOC dead?
A SOC is often seen as tiers or separate teams (such as the blue team, red team, and threat hunting team). The only way SOCs can keep up with the constantly changing cybercriminal world and technology is by integrating their solutions and ensuring seamless collaboration between the tiers and teams.
The SOAR platform has already started this trend when it automated and fused different threat feeds.
What is often overlooked is the need for high quality intelligence data.
How can dark web intelligence help?
Because cybercriminals are always looking for new attack techniques, they regularly collaborate and share tips before the event, and trade compromised assets after the attack.
Quality dark web intelligence is key to identifying new threats against organizations and to monitoring and managing already compromised assets. It has a major influence in both the pre-and post Cyber Kill Chain process.
The image below proposes a new type of collaboration to help boost preemptive and early identification of new threats and quicker and better detection of compromised assets.
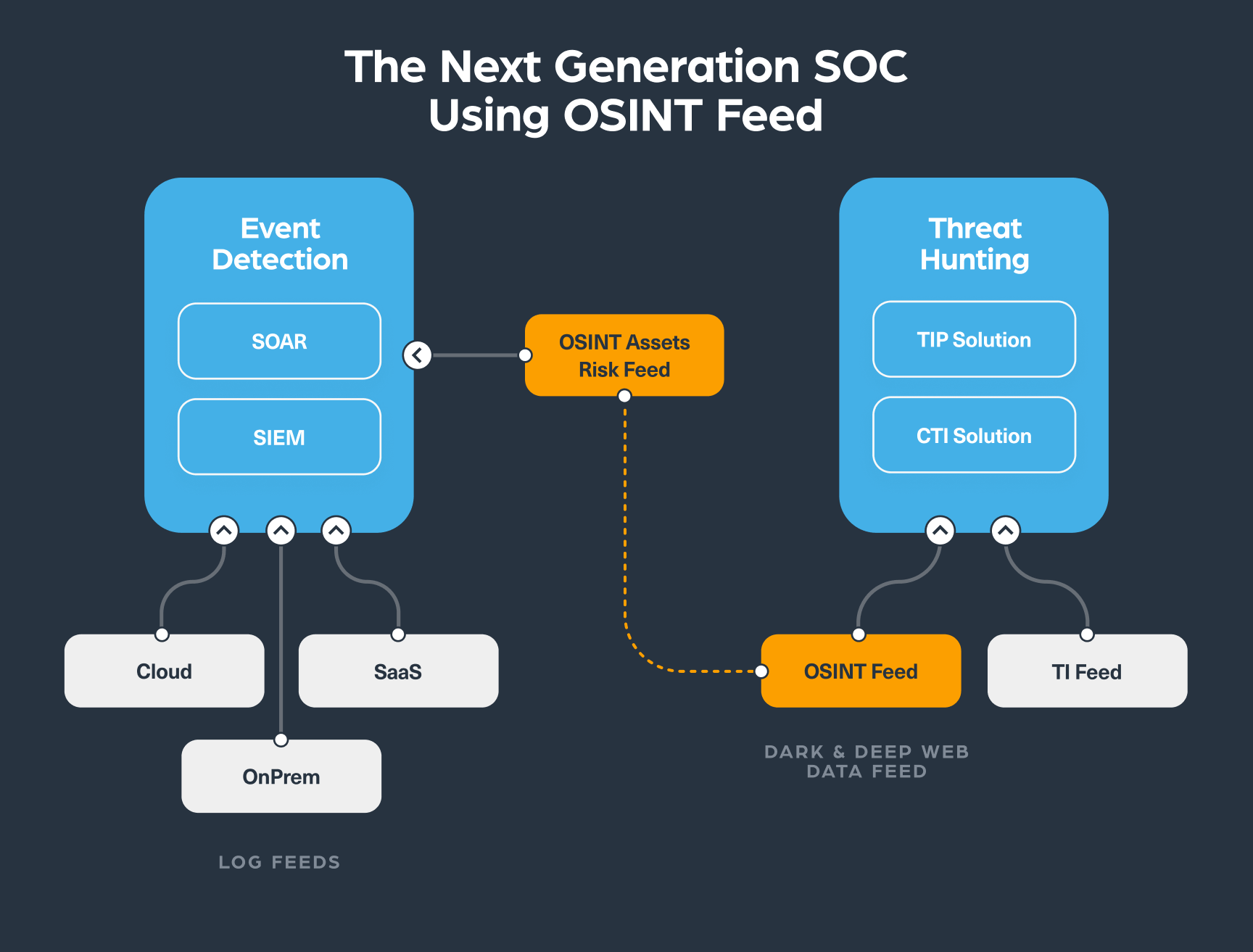
The OSINT feed (in the image above) represents open, deep and dark web data – it’s a continuous intelligence feed that is generated by searching for organizations’ digital assets such as domain or IP or event IoC such as CVE or hashes and continuously monitor them to find new types of risk or threat.
One of the main advantages of using such a feed is that it allows the two different SOC teams, the event detection team and threat hunting team, to collaborate. It can be integrated into an event monitoring solution by using log events with a risk score, which is generated by aggregation models that identify an anomaly. This high quality alert is then submitted to the threat hunting team to enrich the context of the specific alert. Because each risk alert will have a unique ID, members from any team can easily track the event in the systems and, when necessary, send relevant high risk threats for immediate actions or deeper investigation.
This type of collaboration reduces the need for human involvement in the process and refines the quality of alerts that are being processed by the teams.
How can an OSINT risk feed help SOC teams?
Connecting an OSINT risk feed into both event detection and threat hunting solutions can help:
- Reduce noise and focus on the important threats
- Help to identify the threat ahead of time
- Mitigate the threat more efficiently
- Create better collaboration processes between the teams with minimal human intervention
How would an OSINT integrate into a SOC operation?
There are four stages in a typical case scenario when using an OSINT feed. Let’s take a look at an example of a phishing threat:
Step #1: Detection
The event detection team received multiple signals on a phishing threat to a website belonging to one of their customers from the OSINT feed. This would mean that either a cybercriminal is offering a new tool for a specific domain for sale or a threat actor posted a question around that specific domain on a dark web forum.
Step #2: Validation
Once the Event Detection team receives several high risk alerts of the same category, they send an investigation request to the Threat Hunting team citing the same alert ID of the event found by the Event Detection team.
Step #3: Investigation
The Threat Hunting team are now well equipped with all the alerts required including information on the dark web domains that the criminals used to share information on, and the specific asset that was mentioned. This allows the team to immediately investigate further using the same OSINT feed to identify ways to mitigate the threat.
Step #4: Protection
Once the threat is identified, validated and its context is checked, the Threat Hunting team can prepare a list of action items to carry out, this is all done before the event actually takes place.
What happens when an attack has already taken place?
In case the attack has already happened, the same approach mentioned above can be applied to identify the compromised assets – which will allow the threat hunting team to examine the most relevant alerts that were validated by the event detection team to help take necessary actions to mitigate further impact.
How can Webz.io help?
Webz.io offers two feeds that address the needs of SOC teams:
- Cyber API – which includes open, deep and dark web data about IoCs and provide full structured context for OSINT investigation on risks against organizations and individuals
- Dark Risk API – A feed that converts open, deep and dark web data into high risk signals (in log files) that include relevant risk scores on different types of threats.
The two feeds compliment each other and provide rich information for impactful and effective investigations.
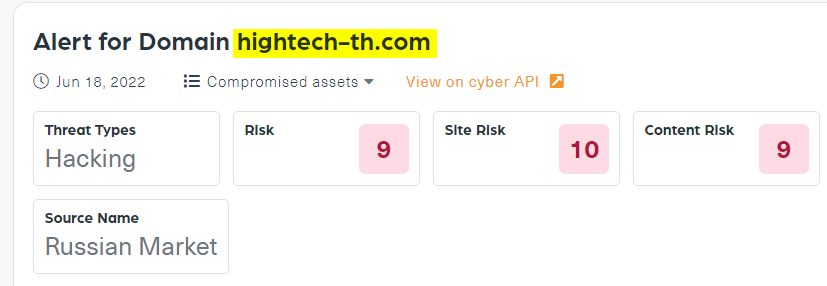
For example, the image below includes a screenshot of a Dark risk API alert. This high risk alert (9 out of 10) was created on June 18, 2022 after the “hightech-th.com” domain appeared on a dark web marketplace called Russian Market where cookies to the site (which provide access to the site) were up for sale.
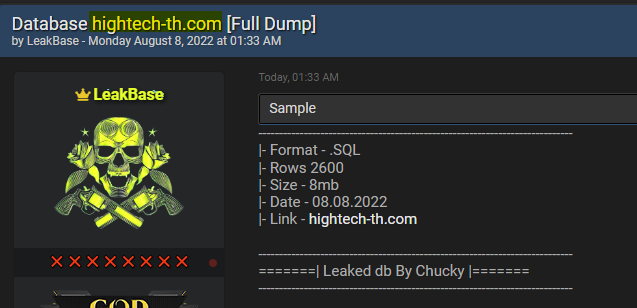
Below you can see a post that we could find by using our Cyber API, which shows that on August 8, 2022, that means two months after the Dark Risk Alert, the database of “hightech-th.com” appeared on hacker forum Breached.co. This could very well indicate that the threat actor gained access to the domain by using the cookies that were up for sale on the dark web, which was indicated by Webz.io’s Dark Risk alert.
In today’s world, where cybercriminals are constantly evolving their methods and SOC teams need to always stay one step ahead – gaining timely and quality intelligence on emerging threats is mission critical. They need information before, during and after the event. They need to stay on watch for new threats and plots by malicious actors.
Webz.io provides intelligence feeds that help event monitoring and intelligence solutions always stay ahead and protect against any upcoming cyber threat.
https://webz.io/dwp/osint-feed-the-missing-piece-in-the-soc-puzzle/
Published: 2022 08 10 12:32:09
Received: 2022 08 10 13:12:56
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 3
