Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Haveibeenpwned is being abused to exploit potential victims
published on 2022-08-17 13:40:15 UTC by philvilesContent:
The popular breach verification site www.haveibeenpwned.com (HIBP) has been cloned by a threat actor with the intention of harvesting credentials entered by visitors to the site.
The free website was set up by security expert Troy Hunt in December 2013 and now has over two million verified email subscribers.
It allows visitors to check if their email address has been seen in a reported data breach and provides details of those breaches to allow users to assess if their email address is at risk.
There is a further service on the site that allows users to discover if any passwords they may use have been observed in a data breach and therefore are likely to appear on “known password lists”.
The fake site used in the campaign (left) appears to be extremely similar in appearance to the genuine site (right).
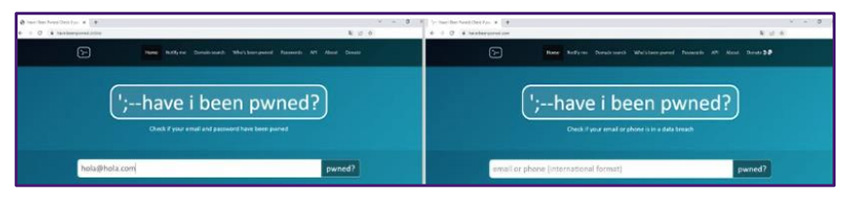
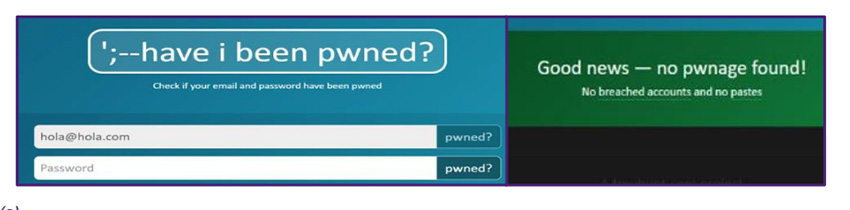
The cloned website, reported by a security team at welivesecurity.com, contains both email and password data fields together (below left). This makes it extremely simple and quick for the site’s owner to capture the full credentials of any users who complete the fields.
Once entered, the user is redirected to the genuine HIBP site with the good news message that their credentials have not been identified in a breach (below right).
Welivesecurity have obfuscated the top level section of the domain to avoid readers accidentally visiting the site.
It should be noted that further iterations of the URL may be different, but display pages of similar appearance.
The real site - and one which we at the EMCRC endorse - is https://haveibeenpwned.com
Reporting
Report all Fraud and Cybercrime to Action Fraud by calling 0300 123 2040 or online. Forward suspicious emails to report@phishing.gov.uk. Report SMS scams by forwarding the original message to 7726 (spells SPAM on the keypad).
https://www.emcrc.co.uk/post/haveibeenpwned-is-being-abused-to-exploit-potential-victims
Published: 2022 08 17 13:40:15
Received: 2022 08 17 13:51:50
Feed: The Cyber Resilience Centre for the East Midlands
Source: National Cyber Resilience Centre Group
Category: News
Topic: Cyber Security
Views: 3
