Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.How Can Monitoring the Dark Web Help Detect Threats against Critical Infrastructure?
published on 2022-08-31 09:09:12 UTC by Hagar MargolinContent:
We have covered various dark web trends over recent months, including the increase in the number of attacks launched by cybercriminal groups who use ransomware for extortion.
In their early days when the scope of their activity was still limited, they mainly targeted individuals and small organizations, mostly for personal reasons rather than for financial gain. But with time, we have seen these groups adapting their ransomware activities to target large companies and enterprises to maximize their profit.
Since then, they spread their activities to target the public sector, such as hospitals and government bodies. This development has not spared infrastructure companies around the world that have also experienced a huge increase in the number of cyberattacks. We don’t expect this trend to slow down because ransomware groups know that many people depend on infrastructure, which will put a lot of public pressure on such companies to give in to their high demands.
Case Study: Thames Water
There have seen an increasing number of attacks against infrastructure companies over the past year. After the news spread about the attack against UK-based regulated water company South Staffordshire PLC, we decided to take a look and see what we can find on this industry on the dark web.
A day before this attack was in the news, a ransomware group named Cl0p posted an announcement (see image below), in which they claim to be behind an attack against a water supplier in the United Kingdom, but curiously enough, they stated that their attack was launched against Thames Water, the UK’s largest water supplier.
In the post, which was published on the official site of the group, they claim that they managed to breach the company’s system for months and air some of the failures in the security conduct of Thames Water, and its vulnerabilities.
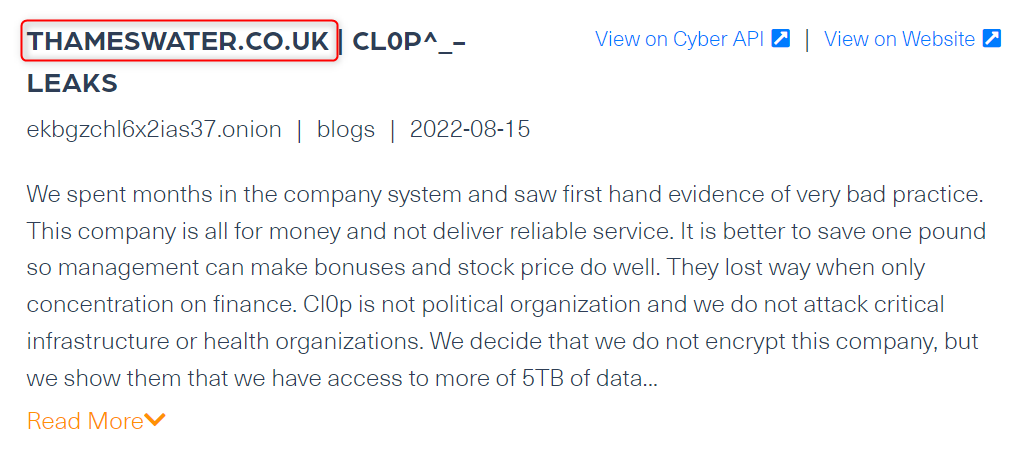
Although this group claims to not encrypt files belonging to critical infrastructures or healthcare organizations, they do threaten to publish over 5TB of data from the company’s data unless they are paid a ransom and get to show Thames Water’s cybersecurity failures.
The post above is a good example of how fresh data from the deep and dark web can play a key role in monitoring real-time events, and provide organizations such as Thames Water with critical intelligence about threats before they hit their systems or reach the press.
Early indications for threats against Thames Water on the dark web
We used our Cyber API to search for mentions of compromised domains belonging to Thames Water, and we found important indications of potential cyber threats to the company on dark web marketplaces.
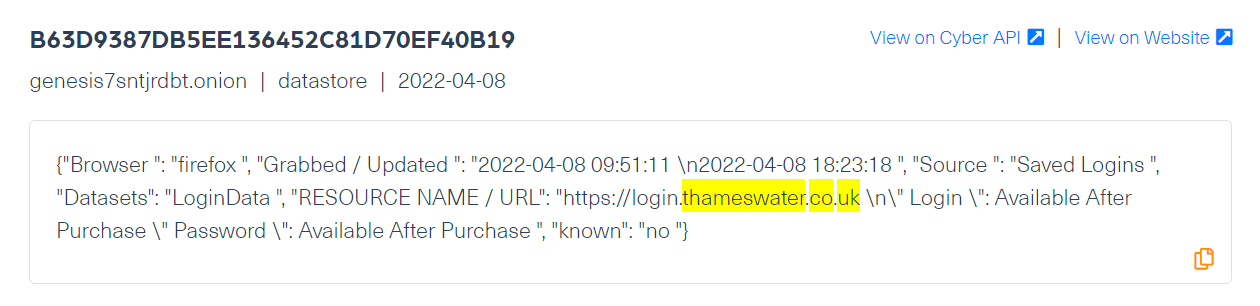
These domains were linked to traded stolen digital fingerprints, which refer to the information stored on the user’s browser, including cookies, login information from the websites the victim browsed, IP address, and other operating system details, which can be stolen by using malware. In this case, the traded stolen digital fingerprints may belong to employees of Thames Water, which if obtained, can help threat actors to gain malicious access to the company’s network.
The following screenshot is an example of digital fingerprints belonging to Thames Water being traded on Genesis, which we crawled several months ago:
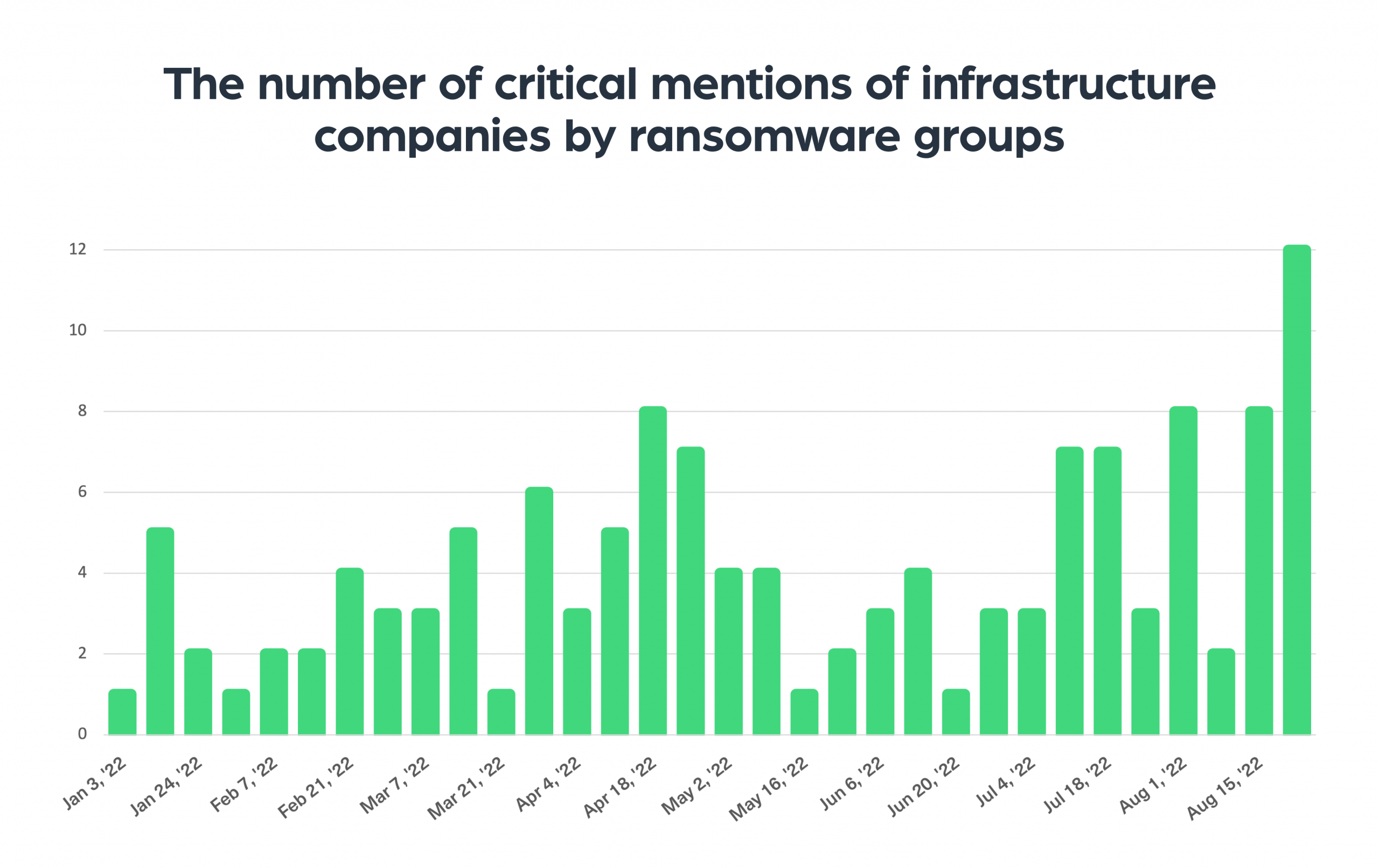
To gain a wider overview, we ran a few queries in our system and found a significant increase in the number of critical mentions of infrastructure and resources companies, by ransomware groups.
As you can see in the chart below, August 2022 is the month with the higher number of ransomware attacks against infrastructure companies over the past six months:
We have also taken a look at the countries most affected by ransomware attacks against their infrastructure organizations over the past year, which you can see in the next chart:
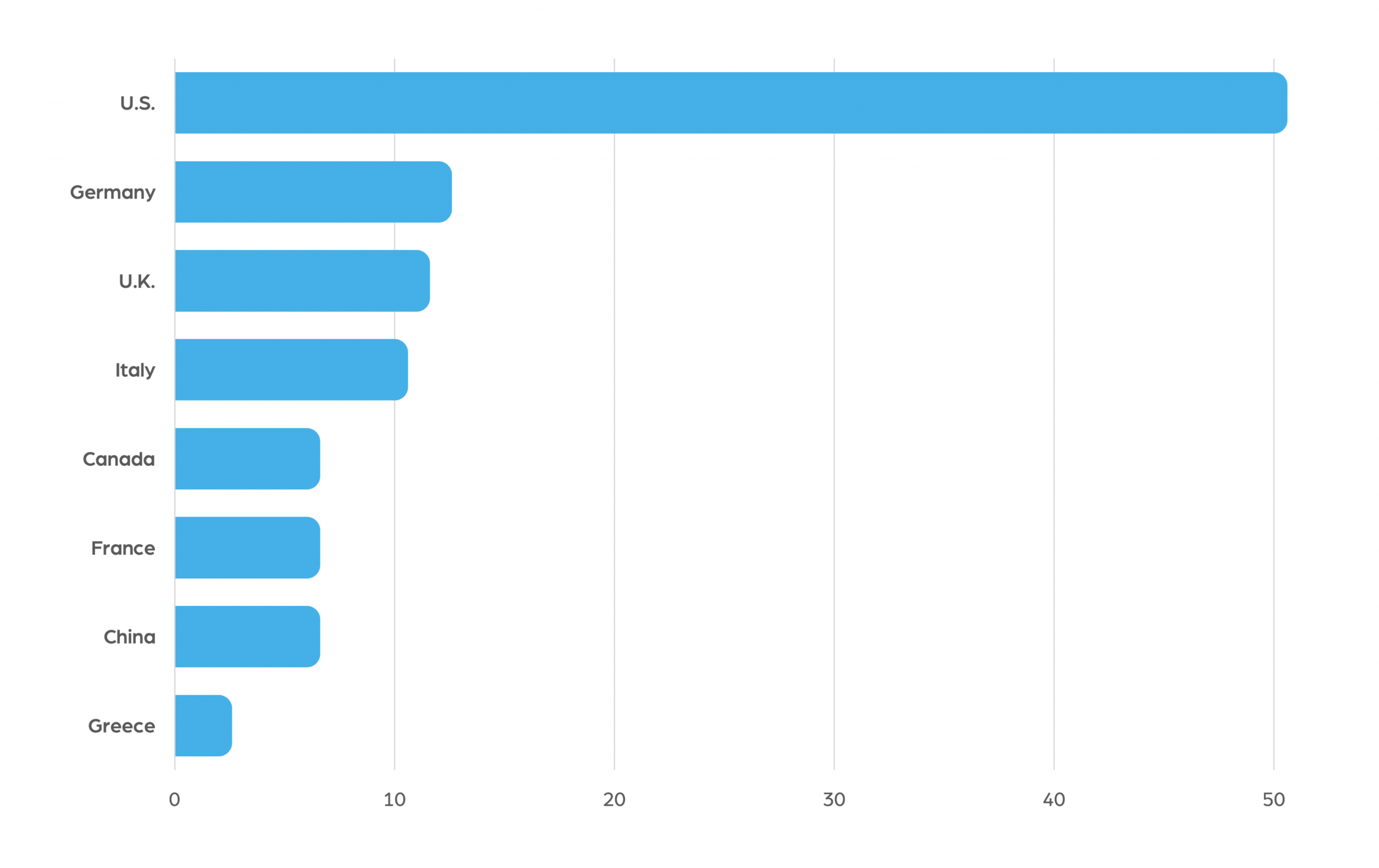
According to our records, US infrastructure companies were the number one target of ransomware groups this past year. They were followed by German infrastructure companies and British ones, who came second and third respectively.
With the growing economic crisis and climate change which have a direct impact on global resources, any attack directed against infrastructure companies can have a grave effect on millions of people, the economy, and the environment. This is why we expect to see the need for monitoring threats against these organizations on the deep and dark web to increasingly become critical to many countries and companies across the globe.
https://webz.io/dwp/how-can-monitoring-the-dark-web-help-detect-threats-against-critical-infrastructure/
Published: 2022 08 31 09:09:12
Received: 2022 09 06 14:53:51
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 16
