Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.[SANS ISC] A ‘Zip Bomb’ to Bypass Security Controls & Sandboxes
published on 2022-05-20 10:05:12 UTC by XavierContent:
I published the following diary on isc.sans.edu: “A ‘Zip Bomb’ to Bypass Security Controls & Sandboxes“:
Yesterday, I analyzed a malicious archive for a customer. It was delivered to the mailbox of a user who, hopefully, was security-aware and reported it. The payload passed through the different security layers based on big players on the market!
The file is a zip archive (SHA256:97f205b8b000922006c32c9f805206c752b0a7d6280b6bcfe8b60d52f3a1bb5f) and has a score of 6/58 on VT. The archive contains an ISO file that, once mounted, discloses a classic PE file. But let’s have a look at the file… [Read more]
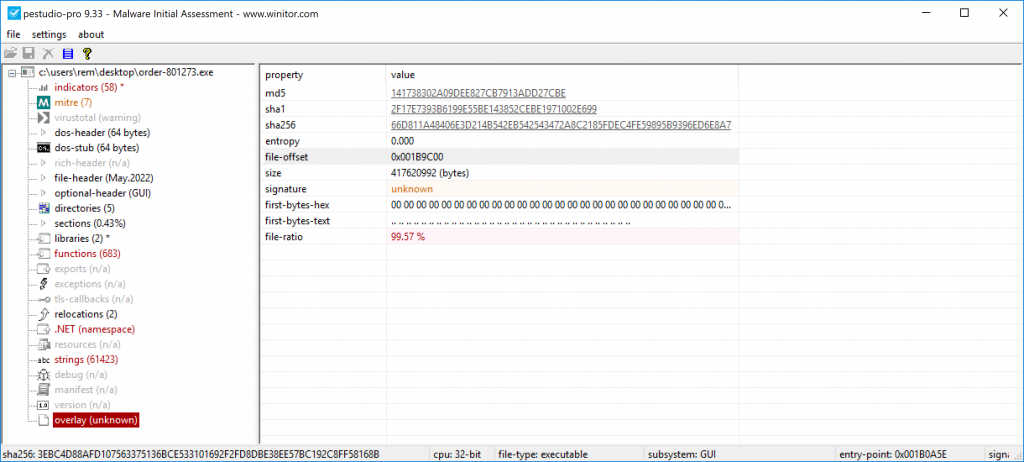
The post [SANS ISC] A ‘Zip Bomb’ to Bypass Security Controls & Sandboxes appeared first on /dev/random.
https://blog.rootshell.be/2022/05/20/sans-isc-a-zip-bomb-to-bypass-security-controls-sandboxes/
Published: 2022 05 20 10:05:12
Received: 2022 11 09 12:19:28
Feed: /dev/random
Source: /dev/random
Category: Cyber Security
Topic: Cyber Security
Views: 16
