Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Disneyland Malware Team: It’s a Puny World After All
published on 2022-11-16 17:32:00 UTC by BrianKrebsContent:
A financial cybercrime group calling itself the Disneyland Team has been making liberal use of visually confusing phishing domains that spoof popular bank brands using Punycode, an Internet standard that allows web browsers to render domain names with non-Latin alphabets like Cyrillic and Ukrainian.
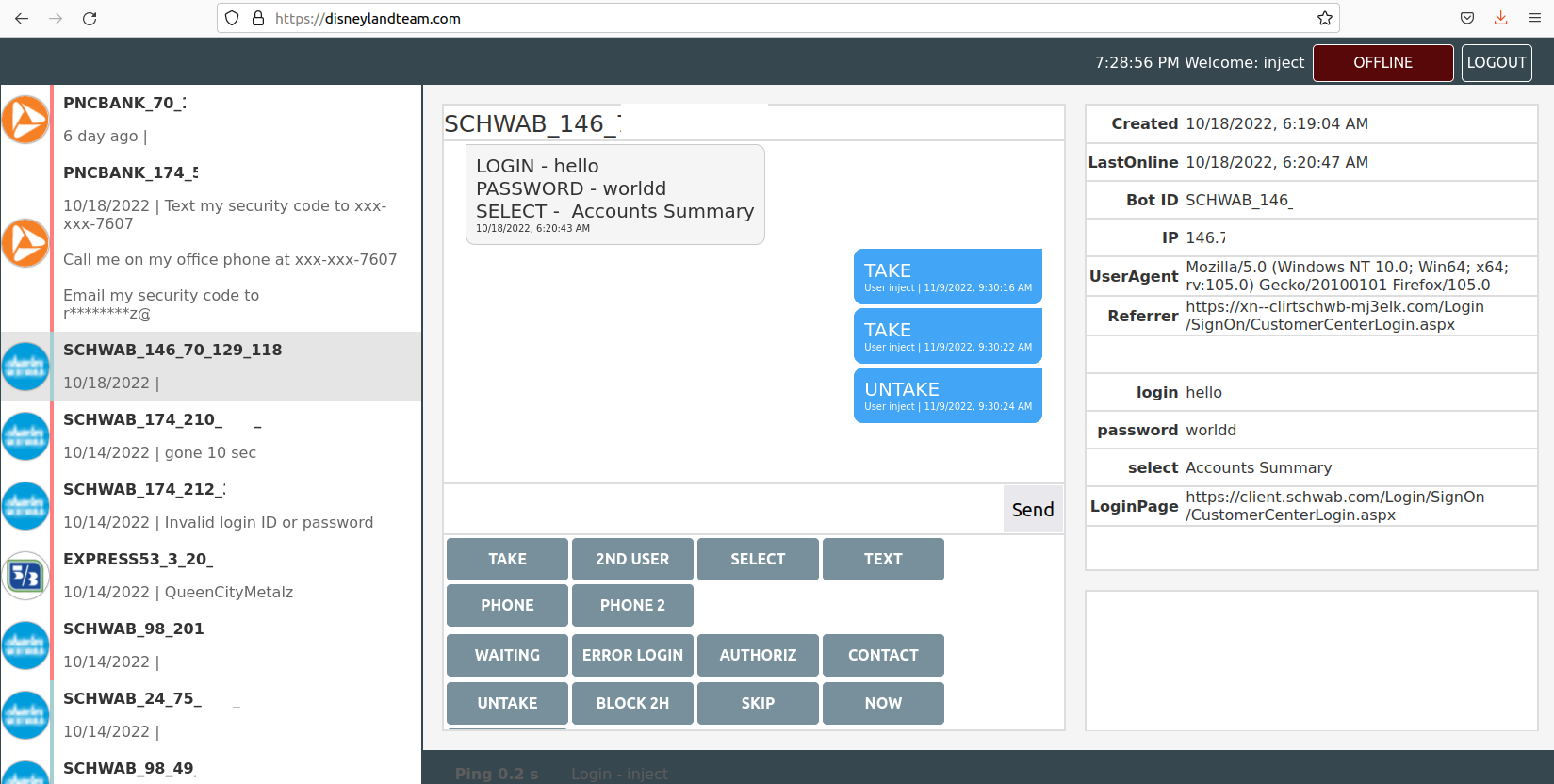
The Disneyland Team’s Web interface, which allows them to interact with malware victims in real time to phish their login credentials using phony bank websites.
The Disneyland Team uses common misspellings for top bank brands in its domains. For example, one domain the gang has used since March 2022 is ushank[.]com — which was created to phish U.S. Bank customers.
But this group also usually makes use of Punycode to make their phony bank domains look more legit. The U.S. financial services firm Ameriprise uses the domain ameriprise.com; the Disneyland Team’s domain for Ameriprise customers is https://www.xn--meripris-mx0doj[.]com [brackets added to defang the domain], which displays in the browser URL bar as ạmeriprisẹ.com.
Look carefully, and you’ll notice small dots beneath the “a” and the second “e”. You could be forgiven if you mistook one or both of those dots for a spec of dust on your computer screen or mobile device.
This candid view inside the Disneyland Team comes from Alex Holden, founder of the Milwaukee-based cybersecurity consulting firm Hold Security. Holden’s analysts gained access to a Web-based control panel the crime group has been using to keep track of victim credentials (see screenshot above). The panel reveals the gang has been operating dozens of Punycode-based phishing domains for the better part of 2022.
Have a look at the Punycode in this Disneyland Team phishing domain: https://login2.xn--mirtesnbd-276drj[.]com, which shows up in the browser URL bar as login2.ẹmirạtesnbd[.]com, a domain targeting users of Emirates NBD Bank in Dubai.
Here’s another domain registered this year by the Disneyland Team: https://xn--clientchwb-zxd5678f[.]com, which spoofs the login page of financial advisor Charles Schwab with the landing page of cliẹntșchwab[.]com. Again, notice the dots under the letters “e” and “s”. Another Punycode domain of theirs sends would-be victims to cliẹrtschwạb[.]com, which combines a brand misspelling with Punycode.
We see the same dynamic with the Disneyland Team Punycode domain https://singlepoint.xn--bamk-pxb5435b[.]com, which translates to singlepoint.ụșbamk[.]com — again phishing U.S. Bank customers.
What’s going on here? Holden says the Disneyland Team is Russian-speaking — if not also based in Russia — but it is not a phishing gang per se. Rather, this group uses the phony bank domains in conjunction with malicious software that is already secretly installed on a victim’s computer.
Holden said the Disneyland Team domains were made to help the group steal money from victims infected with a powerful strain of Microsoft Windows-based banking malware known as Gozi 2.0/Ursnif. Gozi specializes in collecting credentials, and is mainly used for attacks on client-side online banking to facilitate fraudulent bank transfers. Gozi also allows the attackers to connect to a bank’s website using the victim’s computer.
In years past, crooks like these would use custom-made “web injects” to manipulate what Gozi victims see in their Web browser when they visit their bank’s site. These web injects allowed malware to rewrite the bank’s HTML code on the fly, and copy and/or intercept any data users would enter into a web-based form, such as a username and password.
Most Web browser makers, however, have spent years adding security protections to block such nefarious activity. As a result, the Disneyland Team simply tries to make their domains look as much like the real thing as possible, and then funnel victims toward interacting with those imposter sites.
“The reason that it is infeasible for them to use in-browser injects include browser and OS protection measures, and difficulties manipulating dynamic pages for banks that require multi-factor authentication,” Holden said.
In reality, the fake bank website overlaid by the Disneyland Team’s malware relays the victim’s browser activity through to the real bank website, while allowing the attackers to forward any secondary login requests from the bank, such as secret questions or multi-factor authentication challenges.
The Disneyland Team included instructions for its users, noting that when the victim enters their login credentials, he sees a 10-second spinning wheel, and then the message, “Awaiting back office approval for your request. Please don’t close this window.”
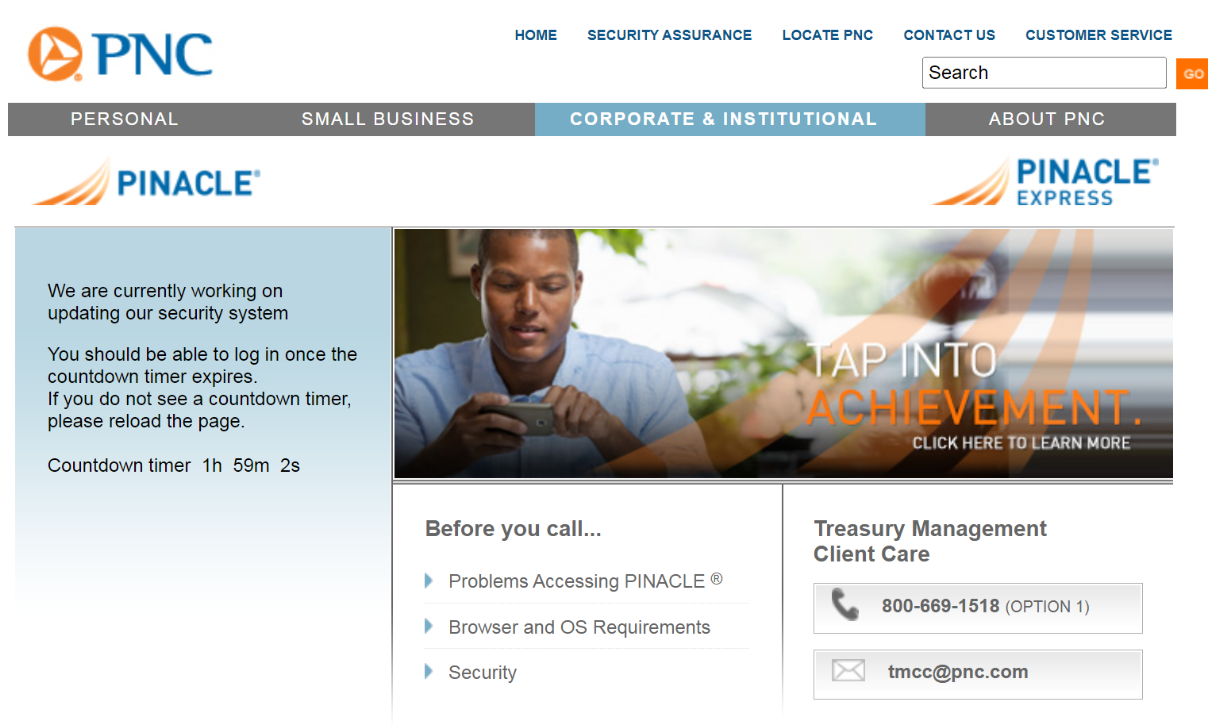
A fake PNC website overlay or “web inject” displaying a message intended to temporarily prevent the user from accessing their account.
The “SKIP” button in the screenshot above sends the user to the real bank login page, “in case the account is not interesting to us,” the manual explains. “Also, this redirect works if none of our operators are working at the time.”
The “TAKE” button in the Disneyland Team control panel allows users or affiliates to claim ownership over a specific infected machine or bot, which then excludes other users from interacting with that victim.
In the event that it somehow takes a long time to get the victim (bot) connected to the Disneyland Team control panel, or if it is necessary to delay a transaction, users can push a button that prompts the following message to appear on the victim’s screen:
“Your case ID number is 875472. An online banking support representative will get in touch shortly. Please provide your case ID number, and DO NOT close this page.”
The Disneyland user manual explains that the panel can be used to force the victim to log in again if they transmit invalid credentials. It also has other options for stalling victims whilst their accounts are drained. Another fake prompt the panel can produce shows the victim a message saying, “We are currently working on updating our security system. You should be able to log in once the countdown timer expires.”
The user manual says this option blocks the user from accessing their account for two hours. “It is possible to block for an hour with this button, in this case they get less frustrated, within the hours ddos will kill their network.”
Cybercrime groups will sometimes launch distributed denial-of-service (DDoS) attacks on the servers of the companies they’re trying to rob — which is usually intended to distract victims from their fleecing, although Holden said it’s unclear if the Disneyland Team employs this tactic as well.
For many years, KrebsOnSecurity tracked the day-to-day activities of a similar malware crew that used web injects and bots to steal tens of millions of dollars from small- to mid-sized businesses across the United States.
At the end of each story, I would close with a recommendation that anyone concerned about malware snarfing their banking information should strongly consider doing their online banking from a dedicated, security-hardened system which is only used for that purpose. Of course, the dedicated system approach works only if you always use that dedicated system for managing your account online.
Those stories also observed that since the vast majority of the malicious software used in cyberheists is designed to run only on Microsoft Windows computers, it made sense to pick a non-Windows computer for that dedicated banking system, such as a Mac or even a version of Linux. I still stand by this advice.
In case anyone is interested, here (PDF) is a list of all phishing domains currently and previously used by the Disneyland Team.
https://krebsonsecurity.com/2022/11/disneyland-malware-team-its-a-puny-world-after-all/
Published: 2022 11 16 17:32:00
Received: 2022 11 16 17:40:18
Feed: Krebs on Security
Source: Krebs on Security
Category: Cyber Security
Topic: Cyber Security
Views: 16
