Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.All You Need to Know about IOC Monitoring on the Dark Web
published on 2022-07-20 13:56:53 UTC by Hagar MargolinContent:
With cybercrime activity on the rise, real-time monitoring of Indicators of Compromise (IOCs) has become critical for organizations. IOCs serve as indicators of potential security threats to a system or network, whether it’s data breaches, ransomware attacks, account takeover (ATO), phishing attempts or any kind of cyber threats.
Why is monitoring IOCs important?
- It can help organizations, information security professionals and system administrators to better detect intrusion attempts or other malicious activities on their systems.
- Real-time IOC alerts can help prevent potential cyberattacks or limit damages by identifying and mitigating attacks in early stages. It can also provide them with critical time to better manage the event and possible outcomes.
- After an event is managed, the IT professionals can share information they gathered from the event to improve incident response and computer forensics for future events.
How should you monitor IOCs?
The deep and dark web and some chatting applications are the main platforms used by cybercriminals. We see a wide range of potential IOCs (exposed data logs) that serve as an early indication of threats to organizations and enterprises. Monitoring such platforms for organization and brand identifiers is the key to effective brand protection.
What types of IOCs can you find on the deep and dark web?
Nowadays, the most common indicators of compromise on deep and dark web platforms are companies’ IPs and domains. They often appear in leaked databases published on these platforms or as part of stolen digital fingerprints that are put up for sale. They sometimes also appear in posts cybercriminals publish, expressing their plans to attack specific organizations or past attacks.
With the growing number of cyberattacks, more and more threat hunting and monitoring teams look to these spaces to find early indications of emerging threats.
How can real-time dark web alerts help threat hunting and monitoring teams?
Early detection of cyber threats starts with monitoring IOCs. Because most of IOC discussion and trade can be found on the deep and dark web, it is the best place to find early indications and mentions of IOCs. Monitoring domains and IPs in particular are classic examples of real-time indicators we provide to organizations and companies to boost their threat intelligence.
Let’s review some examples we have recently found of leaked domains and IPs:
Leaked IPs
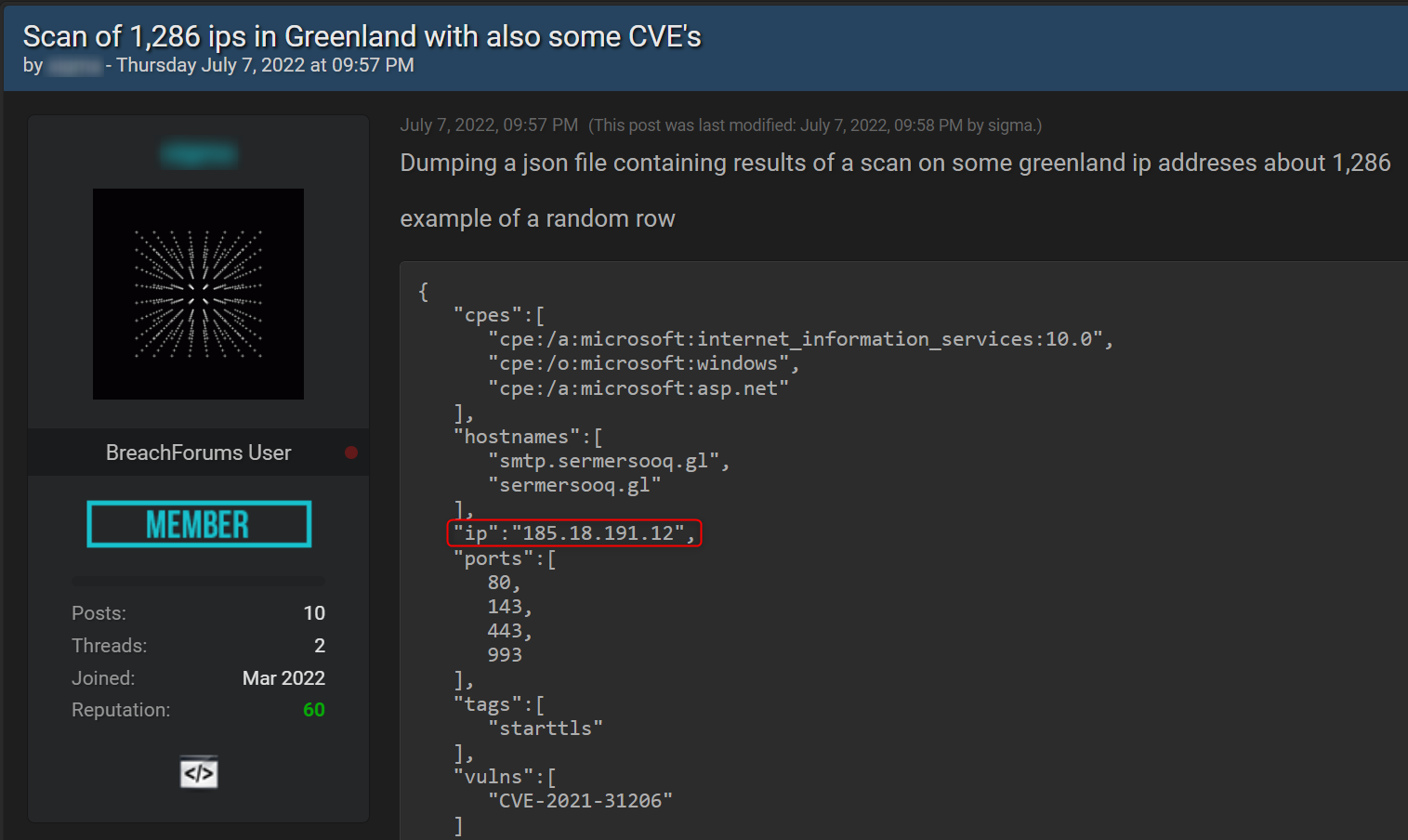
Leaked Greenland IPs for sale
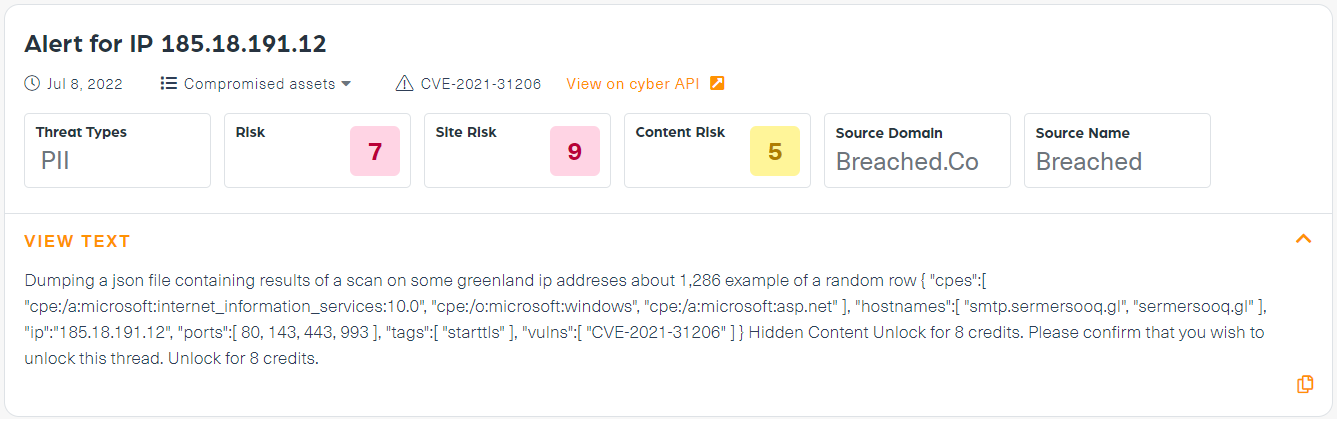
What does the data show?
The first example is of leaked IPs in Greenland (see the post below) which were put for sale on a known hacking forum. The threat actor is offering a wide range of leaked IPs, including some extended details such as the hostnames (domain name assigned to a host computer) and services they belong to.
What actions can be taken following an alert?
- Stage One – Take urgent measures to protect mentioned leaked IP addresses.
- Stage Two – An alert about the mention of this leak can send you to check further – and find that, in this case, the threat actor claims that there are vulnerabilities that may be linked to some of those leaked IPs and mentions more specifically CVE-2021-31206.
- Stage Three – Take urgent actions to patch the vulnerability mentioned.
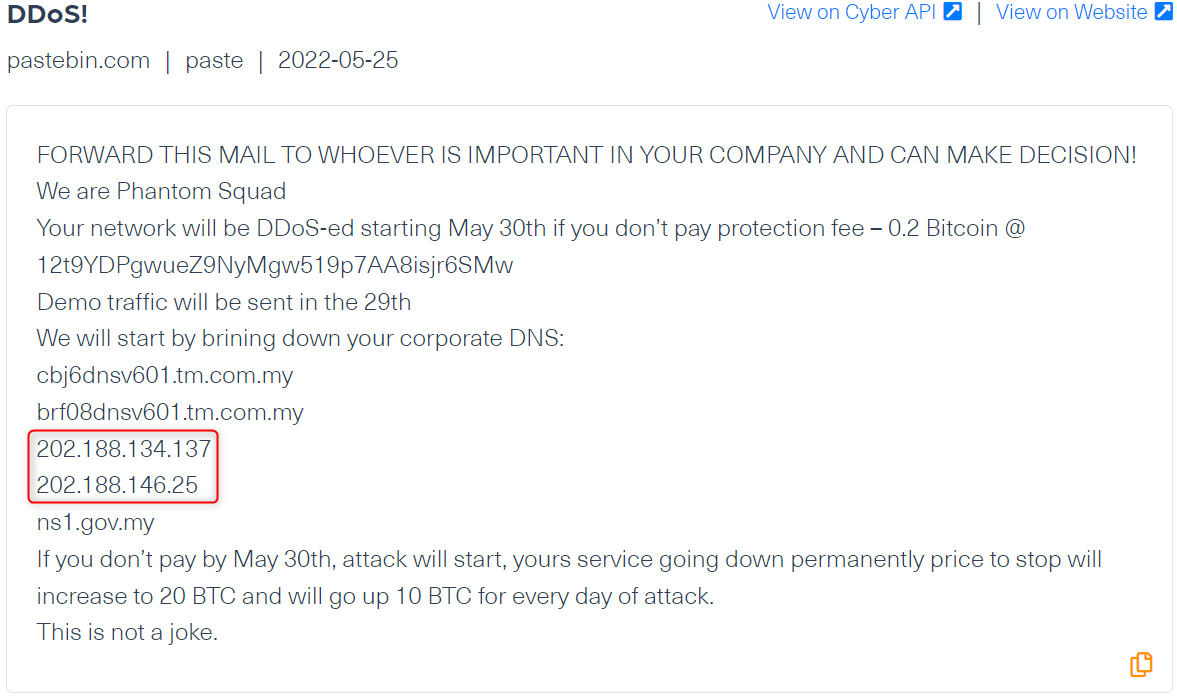
Telekom Malaysia Berhad’s IP Under Threat
What does the data show?
A ransom note was recently published on Pastebin allegedly by the known hacking group, Phantom Squad (after a 5 years hiatus) who threatened to launch a cyberattack against “Telekom Malaysia Berhad”, a Malaysian telecommunications company. In that note, they targeted the company, saying they will permanently shut down their DNS (domain Name system) by launching DDoS attacks if their ransom isn’t paid.
What actions can be taken following an alert?
Monitoring the IP would help to protect Telekom Malaysia Berhad better by detecting a threatening note which does not mention the name of the company.
After detecting this cyber threat, in time, the company earns critical time to mitigate or even prevent it altogether.
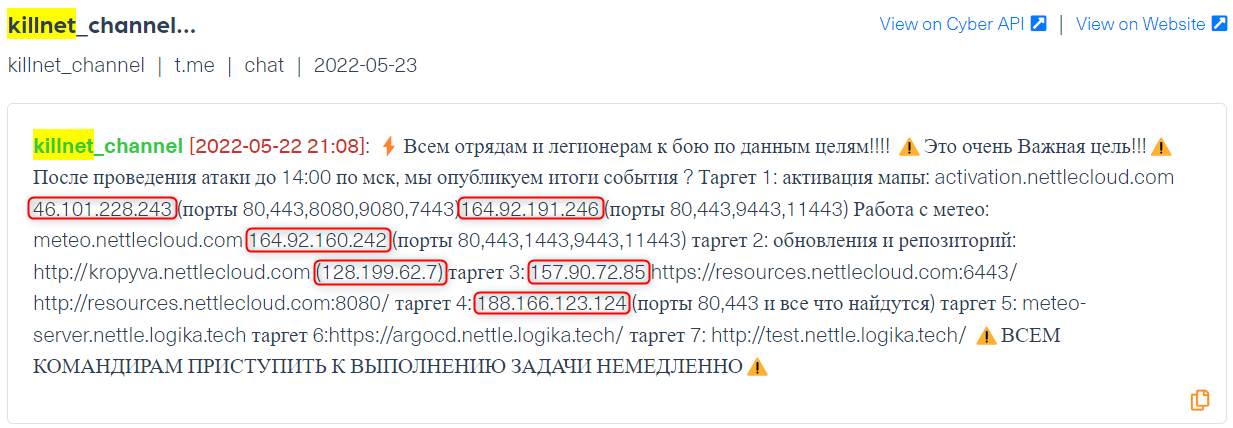
European IPs targeted by pro-Russia hackers
What does the data show?
The post below was published on a Telegram channel by Killnet, a pro-Russian hacking group. In it, the group announced a real time DDoS attack against six targets whose host names and IP addresses related to European assets amid the war between Russia and Ukraine. The main purpose of the post was to rally supporters to join this attack.
What actions can be taken following an alert?
The targeted European organizations and their cybersecurity teams can take immediate actions to mitigate the DDoS attacks as they unfold.
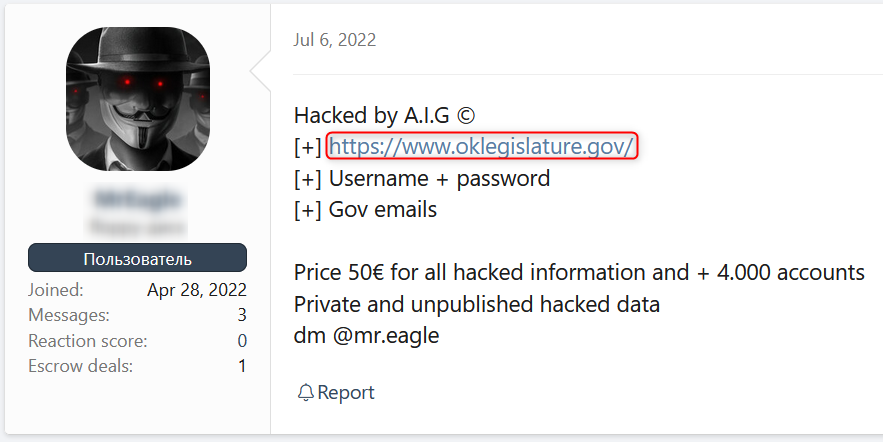
Compromised Domains
Oklahoma Legislature’s Website
What does the data show?
The following post offers for sale leaked login details (usernames and passwords) belonging to users of the website of the state legislative branch of the U.S. state of Oklahoma. This post, which appeared on dark web hacking forum XSS, indicates that the website had already been hacked before the details were stolen and leaked.
What actions can be taken following an alert?
- Real time monitoring for domains allows organizations to manage the event as soon as possible in order to minimize the damage of the leak.
- Using this effective data breach detection method, threat intelligence teams can inform the relevant departments that will assist employees with the switch to new and stronger passwords and other media and crisis management bodies who’d assist with the possible fallouts from such a breach.
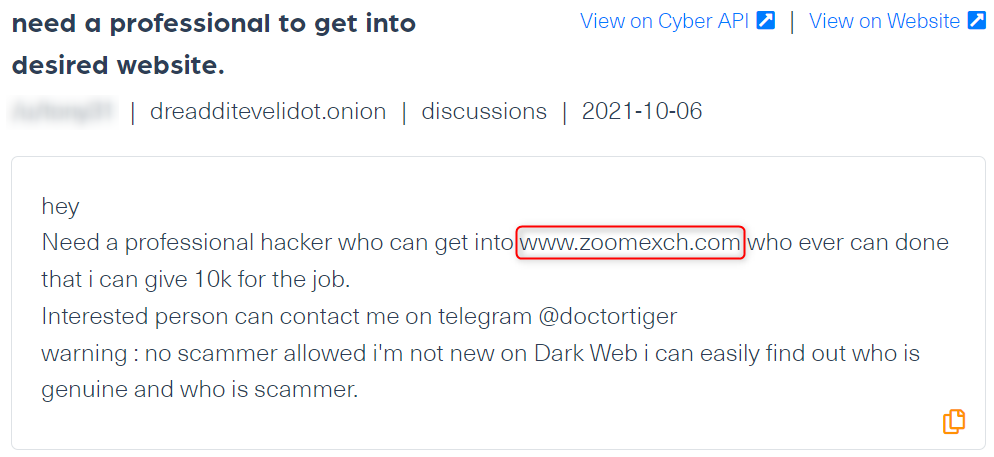
A hacker for hire for an attack against Zoomexch.com domain
What does the data show?
The next post shows a mention of a specific domain, Zoomexch.com in the context of a potential hacking threat in the making. A threat actor is looking for a hacker on dark web forum Dread to gain access to this site’s system.
What actions can be taken following an alert?
To put it simply, a real-time detection can prevent future cyberattacks against this site. It is clear that there is a real intent to hack into their system so an immediate action should be taken in this case.
How to use the deep and dark web to monitor IOCs in real-time?
There are different ways to use data from the deep and dark web to monitor IOCs, depending on the systems used to process the data. We offer three main endpoints to access IOCs from these dark corners of the web:
- Cyber API (Dark Web API) – An API that offers a powerful dark web feed covering millions of sites, forums, marketplaces and others sites in the deep and dark web.
- Data Breach Detection API – An automated search engine API which provides a single point search for leaked data going back up to 5 years.
- Dark Risk (NEW!) – our new push-alert system that provides real-time log files on real time mentions of IOCs (IPs and domains) in the deep and dark web and sends IOC teams indications of assets (IPs & domains) at risk.
A quick example of how our Dark Risk works
By running a partial or a full IP address/domain, you can get a real-time log file indicating critical IOC mentions in deep and dark web. This would include the threat type (per our AI: hacking, PII (Personally Identifiable Information), financial, data loss and counterfeit), a risk score (1-10), source domain (where the IOC was mentioned), source name and the original text.
For example, we used our Dark Risk system to run Greenland IP; once the IP was mentioned with a vulnerability we received this alert:
It is expected that over the coming years, more cybercriminals will turn to deep and dark web platforms to plan and organize cybercrimes and trade in malicious data. This means that an increasing number of IPs, domains and other company assets will be circulating on these spaces. This is why threat hunting and monitoring teams need to track IOCs linked to companies and enterprises to prevent cyberattacks.
https://webz.io/dwp/all-you-need-to-know-about-ioc-monitoring-on-the-dark-web/
Published: 2022 07 20 13:56:53
Received: 2022 12 04 14:47:01
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 20
