Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Happy 12th Birthday, KrebsOnSecurity!
published on 2022-12-29 22:35:36 UTC by BrianKrebsContent:
KrebsOnSecurity turns 12 years old today. That’s a crazy long time for an independent media outlet these days, but then again I’m bound to keep doing this as long as they keep letting me!
Thanks to your readership and support, I was able to spend more time in 2022 on some deep, meaty investigative stories — the really satisfying kind with the potential to affect positive change. Some of that work is highlighted in the 2022 Year in Review review below.
Until recently, I was fairly active on Twitter, regularly tweeting to more than 350,000 followers about important security news and stories here. For a variety of reasons, I will no longer be sharing these updates on Twitter. I seem to be doing most of that activity now on Mastodon, which appears to have absorbed most of the infosec refugees from Twitter, and in any case is proving to be a far more useful, civil and constructive place to post such things. I will also continue to post on LinkedIn about new stories in 2023.
Here’s a look at some of the more notable cybercrime stories from the past year, as covered by KrebsOnSecurity and elsewhere. Several strong themes emerged from 2022’s crop of breaches, including the targeting or impersonating of employees to gain access to internal company tools; multiple intrusions at the same victim company; and less-than-forthcoming statements from victim firms about what actually transpired.
JANUARY
You just knew 2022 was going to be The Year of Crypto Grift when two of the world’s most popular antivirus makers — Norton and Avira — kicked things off by installing cryptocurrency mining programs on customer computers. This bold about-face dumbfounded many longtime Norton users because antivirus firms had spent years broadly classifying all cryptomining programs as malware.
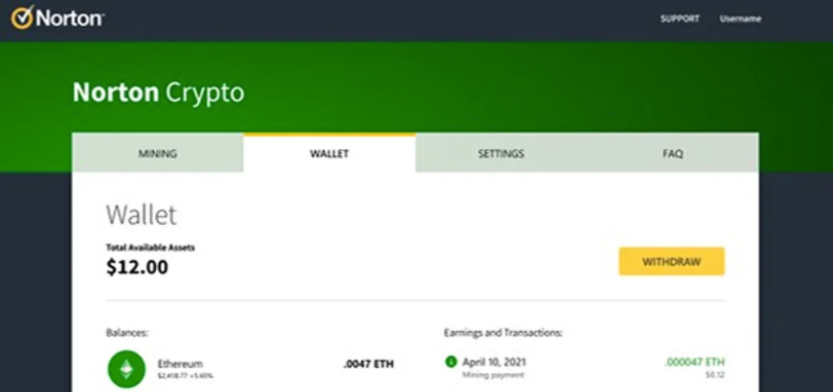
Suddenly, hundreds of millions of users — many of them old enough to have bought antivirus from Peter Norton himself back in the day — were being encouraged to start caring about and investing in crypto. Big Yellow and Avira weren’t the only established brands cashing in on crypto hype as a way to appeal to a broader audience: The venerable electronics retailer RadioShack wasted no time in announcing plans to launch a cryptocurrency exchange.
By the second week of January, Russia had amassed more than 100,000 troops along its southern border with Ukraine. The Kremlin breaks with all tradition and announces that — at the request of the United States — it has arrested 14 people suspected of working for REvil, one of the more ruthless and profitable Russian ransomware groups.
Security and Russia experts dismiss the low-level arrests as a kind of “ransomware diplomacy,” a signal to the United States that if it doesn’t enact severe sanctions against Russia for invading Ukraine, Russia will continue to cooperate on ransomware investigations.
The Jan. 19th story IRS Will Soon Require Selfies For Online Access goes immediately viral for pointing out something that apparently nobody has noticed on the U.S. Internal Revenue Service website for months: Anyone seeking to create an account to view their tax records online would soon be required to provide biometric data to a private company in Virginia — ID.me.
Facing a backlash from lawmakers and the public, the IRS soon reverses course, saying video selfies will be optional and that any biometric data collected will be destroyed after verification.
FEBRUARY
Super Bowl Sunday watchers are treated to no fewer than a half-dozen commercials for cryptocurrency investing. Matt Damon sells his soul to Crypto.com, telling viewers that “fortune favors the brave” — basically, “only cowards would fail to buy cryptocurrency at this point.” Meanwhile, Crypto.com is trying to put space between it and recent headlines that a breach led to $30 million being stolen from hundreds of customer accounts. A single bitcoin is trading at around $45,000.

Larry David, the comedian who brought us years of awkward hilarity with hits like Seinfeld and Curb Your Enthusiasm, plays the part of the “doofus, crypto skeptic” in a lengthy Super Bowl ad for FTX, a cryptocurrency exchange then valued at over $20 billion that is pitched as a “safe and easy way to get into crypto.” [Last month, FTX imploded and filed for bankruptcy; the company’s founder now faces civil and criminal charges from three different U.S. agencies].
On Feb. 24, Russia invades Ukraine, and fault lines quickly begin to appear in the cybercrime underground. Cybercriminal syndicates that previously straddled Russia and Ukraine with ease are forced to reevaluate many comrades who are suddenly working for The Other Side.
Many cybercriminals who operated with impunity from Russia and Ukraine prior to the war chose to flee those countries following the invasion, presenting international law enforcement agencies with rare opportunities to catch most-wanted cybercrooks. One of those is Mark Sokolovsky, a 26-year-old Ukrainian man who operated the popular “Raccoon” malware-as-a-service offering; Sokolovsky was busted in March after fleeing Ukraine’s mandatory military service orders.
Also nabbed on the lam is Vyacheslav “Tank” Penchukov, a senior Ukrainian member of a transnational cybercrime group that stole tens of millions of dollars over nearly a decade from countless hacked businesses. Penchukov was arrested after leaving Ukraine to meet up with his wife in Switzerland.

Tank, seen here performing as a DJ in Ukraine in an undated photo from social media.
Ransomware group Conti chimes in shortly after the invasion, vowing to attack anyone who tries to stand in Mother Russia’s way. Within hours of that declaration several years worth of internal chat logs stolen from Conti were leaked online. The candid employee conversations provide a rare glimpse into the challenges of running a sprawling criminal enterprise with more than 100 salaried employees. The records also reveal how Conti dealt with its own internal breaches and attacks from private security firms and foreign governments.
Faced with an increasing brain drain of smart people fleeing the country, Russia floats a new strategy to address a worsening shortage of qualified information technology experts: Forcing tech-savvy people within the nation’s prison population to perform low-cost IT work for domestic companies.
Chipmaker NVIDIA says a cyberattack led to theft of information on more than 71,000 employees. Credit for that intrusion is quickly claimed by LAPSUS$, a group of 14-18 year-old cyber hooligans mostly from the United Kingdom who specialized in low-tech but highly successful methods of breaking into companies: Targeting employees directly over their mobile phones.
LAPSUS$ soon employs these skills to successfully siphon source code and other data from some of the world’s biggest technology firms, including Microsoft, Okta, Samsung, T-Mobile and Uber, among many others.
MARCH
We learn that criminal hackers are compromising email accounts and websites for police departments worldwide, so that they can impersonate police and send legal requests to obtain sensitive customer data from mobile providers, ISPs and social media companies. That story prompts revelations that several companies — including Apple, Discord and Meta/Facebook — have complied with the fake requests, and draws the attention of Congress to the problem.
APRIL
It emerges that email marketing giant Mailchimp got hacked. The unknown intruders gained access to internal Mailchimp tools and customer data by social engineering employees at the company, and then started sending targeted phishing attacks to owners of Trezor hardware cryptocurrency wallets.
The FBI warns about a massive surge in victims from “pig butchering” scams, in which flirtatious strangers online lure people into investing in cryptocurrency scams. Investigative reports reveal pig butchering’s link to organized crime gangs in Asia that attract young job seekers with the promise of customer service jobs. Instead, those who show up at the appointed time and place are kidnapped, trafficked across the border into neighboring countries like Cambodia, and pressed into a life of indentured servitude scamming others online.
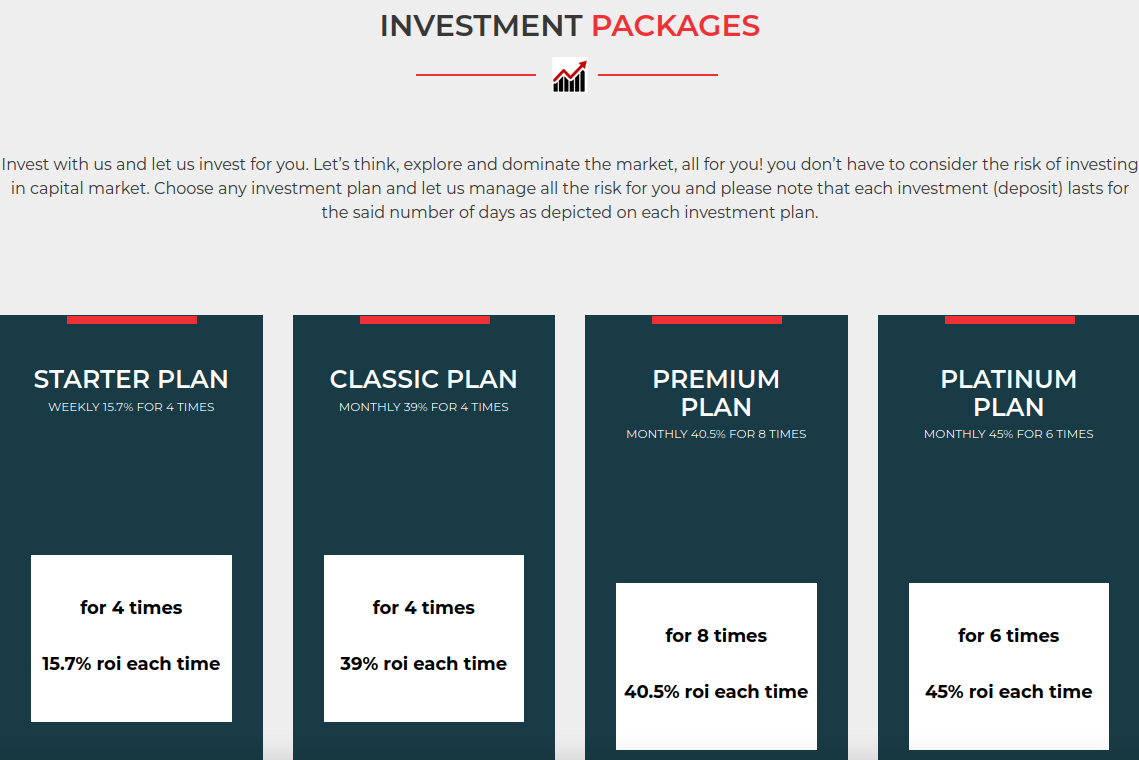
The now-defunct and always phony cryptocurrency trading platform xtb-market[.]com, which was fed by pig butchering scams.
KrebsOnSecurity reports that hackers who specialize in filing fake police requests for subscriber data gained access to a U.S. Drug Enforcement Administration (DEA) portal that taps into 16 different federal law enforcement databases.
The government of Costa Rica is forced to declare a state of emergency after a ransomware attack by Conti cripples government systems. Conti publishes nearly 700 GB worth of government records after the country’s leaders decline to pay a $20 million ransom demand.
JUNE
KrebsOnSecurity identifies Russian national Denis Emelyantsev as the likely owner of the RSOCKS botnet, a collection of millions of hacked devices that were sold as “proxies” to cybercriminals looking for ways to route their malicious traffic through someone else’s computer. Emelyantsev was arrested that same month at a resort in Bulgaria, where he requested and was granted extradition to the United States — reportedly telling the judge, “America is looking for me because I have enormous information and they need it.”

The employees who kept things running for RSOCKS, circa 2016. Notice that nobody seems to be wearing shoes.
JULY
Big-three consumer credit bureau Experian comes under scrutiny after KrebsOnSecurity reveals identity thieves are reliably seizing control over consumer credit files by simply re-registering using the target’s personal information and an email address tied to the crooks. Two months later, Experian would be hit with a class-action lawsuit over these security and privacy failures.
Twitter acknowledges that it was relieved of phone numbers and email addresses for 5.4 million users. The security weakness that allowed the data to be collected was patched in January 2022.
AUGUST
Messaging behemoth Twilio confirms that data on 125 customers was accessed by intruders, who tricked employees into handing over their login credentials by posing as employees of the company’s IT department.
Among the Twilio customers targeted was encrypted messaging service Signal, which relied on Twilio to provide phone number verification services. Signal said that with their access to Twilio’s internal tools, the attackers were able to re-register those users’ phone numbers to another device.
Food delivery service DoorDash discloses that a “sophisticated phishing attack” on a third-party vendor allowed attackers to gain access to some of DoorDash’s internal company tools. Thanks to data left exposed online by the intruders, it becomes clear that DoorDash was victimized by the same group that snookered employees at Twilio, Mailchimp, CloudFlare, and dozens of other major companies throughout 2022.

Mailchimp discloses another intrusion involving targeted phishing attacks against employees, wherein hackers stole data on more than 200 Mailchimp customers. Web hosting giant DigitalOcean discloses it was one of the victims, and that the intruders used their access to send password reset emails to a number of DigitalOcean customers involved in cryptocurrency and blockchain technologies. DigitalOcean severs ties with Mailchimp after that incident, which briefly prevented the hosting firm from communicating with its customers or processing password reset requests.
Password manager service LastPass discloses that its software development environment was breached, and that intruders made off with source code and some proprietary LastPass data. LastPass emphasizes the intruders weren’t able to access any customer data or encrypted password vaults, and that “there is no evidence of any threat actor activity beyond the established timeline,” and “no evidence that this incident involved any access to customer data or encrypted password vaults.”
SEPTEMBER
Uber discloses another breach, forcing the company to take several of its internal communications and engineering systems offline as it investigates. The intrusion only comes to light when the hacker uses the company’s internal Slack channel to boast about their access, listing several internal databases they claimed had been compromised. The intruder told The New York Times they got in by sending a text message to an employee while posing as an employee from Uber’s IT department. Uber blames LAPSUS$ for the intrusion.
Australian telecommunications giant Optus suffers a data breach involving nearly 10 million customers, including passport or license numbers on almost three million people. The incident dominates headlines and politics in Australia for weeks, as the hacker demands a million dollars in cryptocurrency not to publish the information online. Optus’s CEO calls the intrusion a “sophisticated attack,” but interviews with the hacker reveal they simply enumerated and scraped the data from the Optus website without authentication. After briefly posting 10,000 records from the intrusion, the hacker announces they made a mistake, and deletes the auction.
OCTOBER
A report commissioned by Sen. Elizabeth Warren (D-Mass.) reveals that most big U.S. banks are stiffing account takeover victims. Even though U.S. financial institutions are legally obligated to reverse any unauthorized transactions as long as the victim reports the fraud in a timely manner, the report cited figures showing that four of the nation’s largest banks collectively reimbursed only 47 percent of the dollar amount of claims they received.

Joe Sullivan, the former chief security officer for Uber, is found guilty of two felonies after a four-week trial. In 2016, while the U.S. Federal Trade Commission was already investigating a 2014 breach at Uber, another security breach affected 57 million Uber account holders and drivers. The intruders demand $100,000, but Sullivan and his team paid the ransom under the company’s bug bounty program, made the hackers sign a non-disclosure agreement, and concealed the incident from users and investors. The two hackers involved pleaded guilty in 2019; by this time, it has become a nearly everyday occurrence for victim companies to pay to keep a ransomware attack quiet.
NOVEMBER
A ransomware group with ties to REvil begins publishing names, birth dates, passport numbers and information on medical claims on nearly 10 million current and former customers of Australian health insurer Medibank. The data is published after Medibank reportedly declines to pay a US$10 million ransom demand.
DECEMBER
KrebsOnSecurity breaks the news that InfraGard, a program run by the U.S. Federal Bureau of Investigation (FBI) to build cyber and physical threat information sharing partnerships with the private sector, saw its database of contact information on more than 80,000 members put up for sale on an English-language cybercrime forum. Meanwhile, the hackers responsible were communicating directly with members through the InfraGard portal online — using a new account under the assumed identity of a financial industry CEO that was vetted by the FBI itself.
A cybercriminal starts selling account data scraped from 400 million Twitter users, including email addresses and in many cases phone numbers. The seller claims their data was scraped in late December 2021 using the same vulnerability that Twitter patched in January 2022, and that led Twitter to acknowledge the data scraping of 5.4 million user accounts earlier this year. Twitter no longer has a press office, and the company’s Chief Twit has remained silent about the 400 million claim so far, despite many indications that the data is legitimate.
Two days before Christmas, LastPass posted an update on its investigation into the August data breach, saying the intruder was able to use data stolen in the August breach to come back and copy a backup of customer vault data from the encrypted storage container. LastPass’s lackadaisical disclosure timeline and failure to answer follow-up questions has done little to assuage the fears of many users, leaving Wired.com to recommend users abandon the platform in favor of the password managers 1Password and Bitwarden.
Also two days before Christmas, KrebsOnSecurity notifies Experian that anyone can bypass security questions in their application for a free credit report, meaning identity thieves can access your full credit file with just your name, address, date of birth and Social Security number. Unfortunately, this static data on most Americans has been for sale in the cybercrime underground for years. Experian has yet to say whether it has fixed the problem, but expect to see a full report about this early in the New Year.
https://krebsonsecurity.com/2022/12/happy-12th-birthday-krebsonsecurity/
Published: 2022 12 29 22:35:36
Received: 2022 12 29 23:00:46
Feed: Krebs on Security
Source: Krebs on Security
Category: Cyber Security
Topic: Cyber Security
Views: 13
