Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Behind the PayPal Breach: Credential Stuffing on the Dark Web
published on 2023-02-01 12:29:14 UTC by Yuval ShibiContent:
The recent Paypal breach, which affected 35,000 users, highlighted a threat of credential stuffing. The hackers were able to compromise customers’ data by using PII that was compromised in previous breaches. Among the PII exposed are usernames, email addresses, SSNs, dates of birth, and more.
What is credential stuffing?
Credential stuffing is a cyberattack that involves the use of credentials obtained from a data breach on one service to attempt to log into any related or unrelated service. The attack uses bots to automate login into large databases by employing the same password for multiple online accounts, which is known as “password recycling”. This form of attack is based on the assumption that many users reuse usernames and passwords across multiple services.
The PayPal attack was carried out by using bots that automatically ran lists of credentials which they “stuffed” into the PayPal’s login portal.
Where do dark web users share credential stuffing content?
Credential stuffing is widely discussed across deep and dark web platforms. You can see this in the pie chart below that breaks down the leading platforms that host related content:
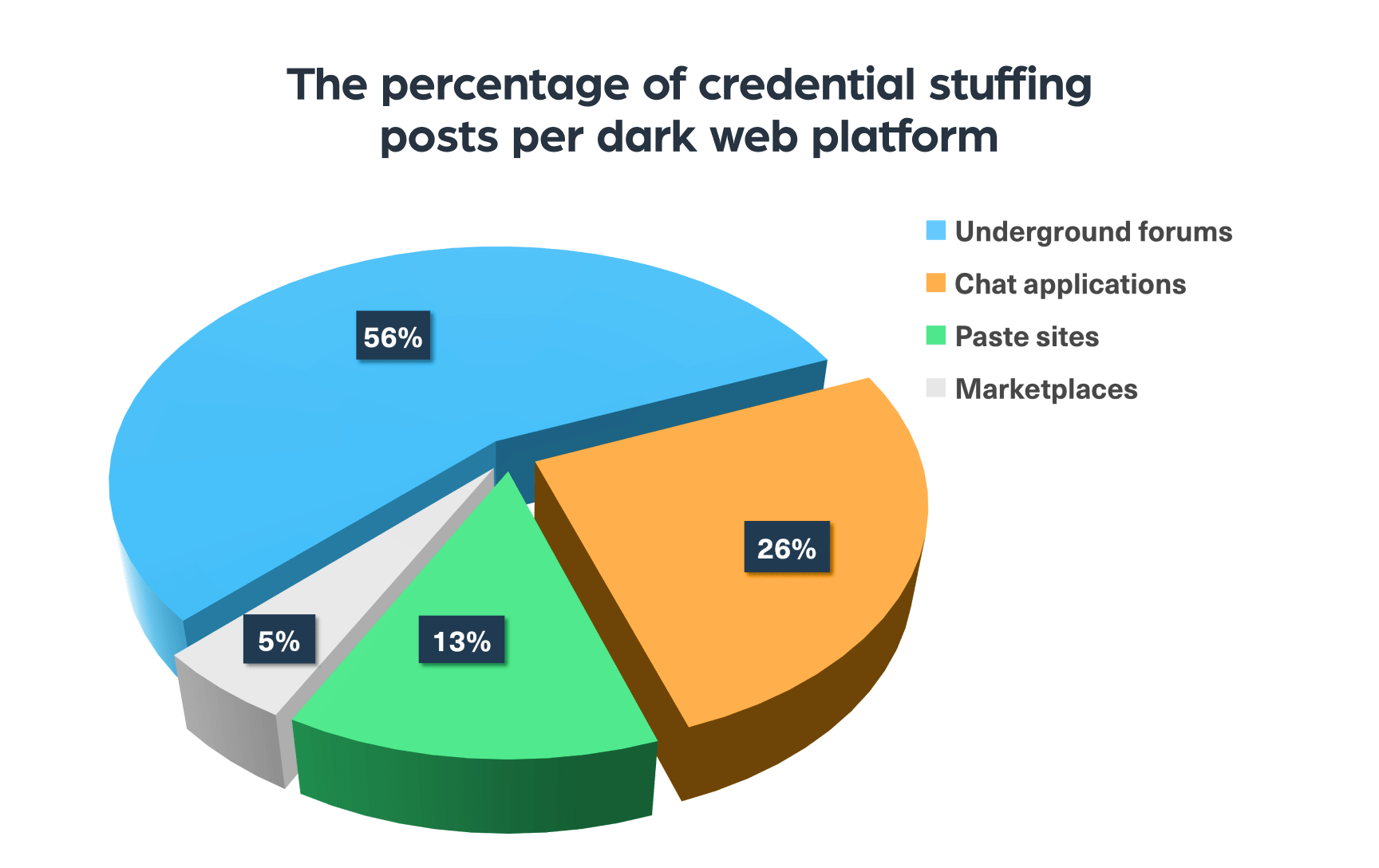
The most popular dark web platforms for discussions of credential stuffing
Let’s briefly review the platforms we saw in the chart above and give a few examples of such sites:
- Underground hacking and carding forums such as Cracked, BreachForums, and CRDPRO, which host dedicated threads for this topic
- Chat applications like Telegram, where data breaches and financial fraud have been a common issue for years
- Marketplaces, including Kingdom Market and WeTheNorth, where you can find tutorials for fraudulent activities and leaked databases like login details are sold.
- Paste sites such as PasteBin, where you can find tutorials and stolen credentials posts.
How does the dark web help cybercriminals to conduct credential stuffing?
The dark web is the number one digital resource cyber criminals turn to for tools and methods to launch cyberattacks, including credential stuffing.
In order to conduct a credential stuffing attack the threat actor needs two primary components: compromised data from past breaches and a dedicated bot for credential stuffing to target the platforms:
Data breaches
Many cybercriminals trade leaked databases and compromised accounts on the dark web. With the rise in the number of data breaches, we see an increase in the number of leaked data offered on the dark web, even for free, available to anyone. The main deep and dark web places to find leaked accounts are hacking forums, marketplaces, chat applications, and paste sites.
Dedicated bot
The web is full of cheap bots hackers can easily use to automatically run compromised login details and match them with existing accounts on different platforms.
The next image shows a threat actor offering a credential stuffing tool on hacking forum Cracked:
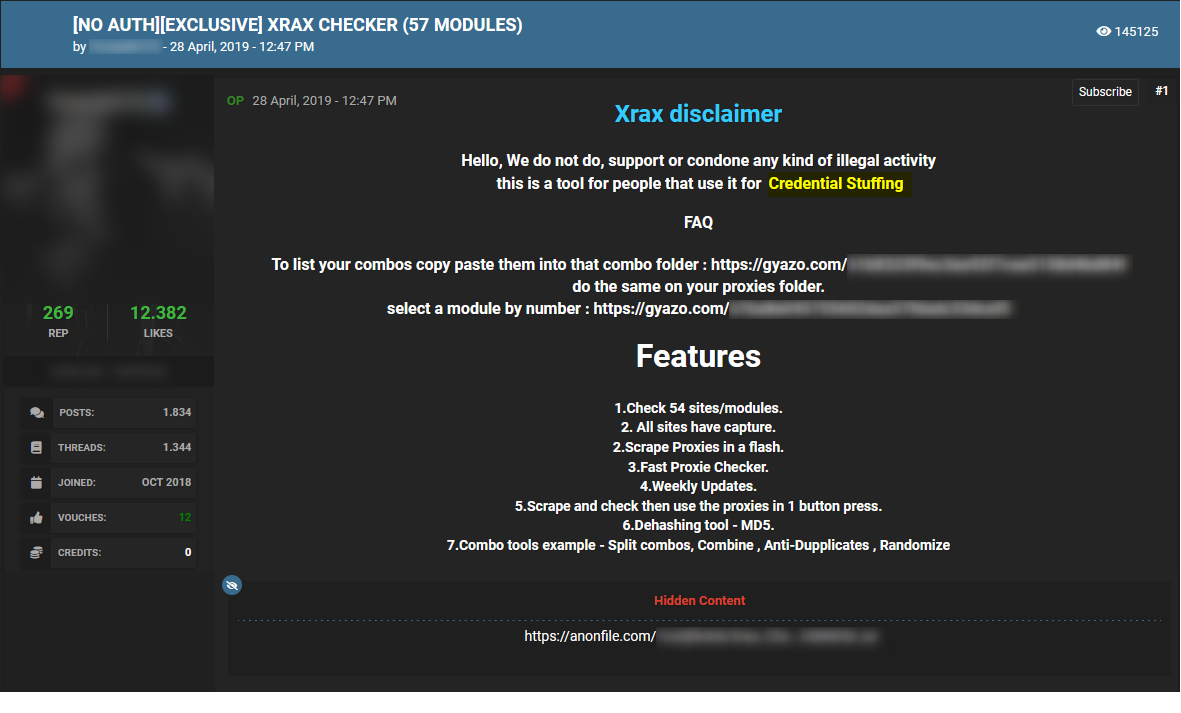
These types of posts facilitate credential stuffing and enable any interested threat actor to carry out such attacks.
How easy is it to use compromised data to conduct credential stuffing attacks?
Like every cyberattack, launching credential stuffing attacks has its own challenges. A major challenge is the two-factor authentication (2FA) tool. This identity and access management security method, which is known to many of us, requires two forms of identification to access platforms and data. In the case of PayPal, the first identification would be the login details and the second one could be a text message or an email. This means that even if a threat actor gained access to stolen login user details, he won’t necessarily manage to take over the account as it requires another step.
We can see such a challenge in the picture below, published on the popular hacking forum BreachForums:
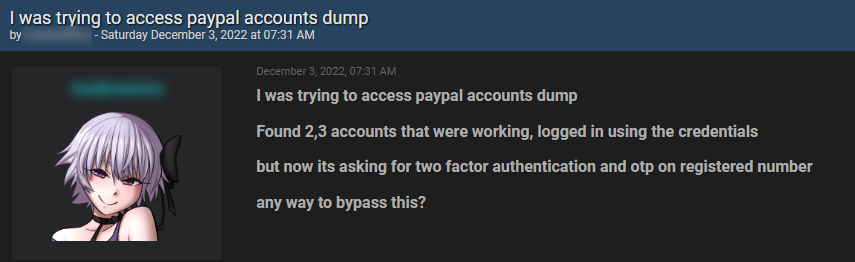
According to the threat actor, he obtained a few account PayPal login details but was unable to gain final access due to the two-factor authentication and OTP (one-time password) verification that PayPal uses.
Yet the 2FA does not offer complete protection from hackers, as there are ways to overcome these verification steps.
Below you can see an example of a post published on the popular carding forum BlackBones, where a threat actor offers an OTP (one-time password) bot for sale:
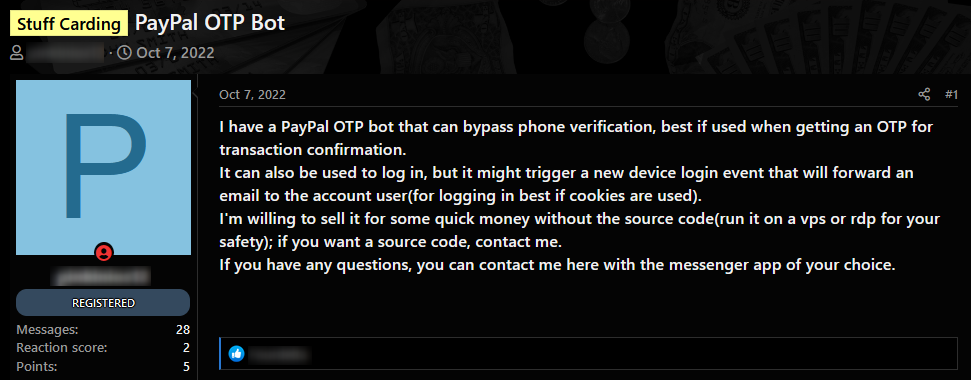
The OTP bot enables attackers to extract one-time passwords from consumers by automatedly communicating with them, in an attempt to trick them into handing over the information required for login or account takeover.
In this case, the bot is customized to bypass PayPal’s 2FA in order to get access to the victim’s account. This post is what we call an early indicator, as it was posted in October 2022, only 3 months before the PayPal breach. It may have been used by hackers to abuse PayPal accounts. The bypass method explained in the post can support future credential stuffing, enabling cybercriminals to use this bot to implement future credential stuffing.
Why is credential stuffing harmful to organizations?
Credential stuffing attacks can cause significant damage to organizations, including:
- The loss of sensitive information – when hackers successfully gain access to an organization’s systems using credential stuffing, they can steal sensitive information such as financial data, personal information, trade secrets, and other confidential information.
- Reputational damage – a breach of an organization’s systems can erode customer trust and confidence in the organization. Customers may be hesitant to conduct business with an organization that has experienced a data breach, which can lead to decreased sales and revenue.
- Financial loss – credential stuffing attacks can result in financial losses for organizations, either through direct theft of funds or fraudulent activity using stolen information. Organizations may also need to spend money on remediation efforts, such as hiring cybersecurity experts to repair the damage caused by the attack.
How can monitoring the dark web help prevent credential stuffing?
Monitoring the dark web is a key component of protecting against credential stuffing attacks, alongside implementing security measures such as regular monitoring of login activity or two-factor authentication that even is not enough sometimes, as we saw.
Today, fraud detection brands, online payment platforms, and individuals face various challenges when safeguarding users’ data, including keeping up with the constantly changing fraud updates and identifying the latest information that was breached.
By monitoring darknet networks, organizations can stay informed about new threats and emerging trends in the cybercrime landscape. The intelligence they can collect can assist them in proactively detecting any leak of their own information or that of their customers on these hidden platforms.
https://webz.io/dwp/behind-the-paypal-breach-credential-stuffing-on-the-dark-web/
Published: 2023 02 01 12:29:14
Received: 2023 02 01 18:05:03
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 13
