Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.The Top 5 Hacker Groups to Watch in 2023
published on 2023-01-11 12:54:24 UTC by Avishag YulevichContent:
Hacker groups, also known as hacking collectives and APT groups, are organized groups of individuals who use their technical skills to engage in illegal or unauthorized activities online. These hackers carry out a variety of illegal activities, including the launch of DDoS attacks, or exploiting organizations’ security vulnerabilities by installing malware, ransomware, and others.
These types of groups are professionally organized like any other organization. They have a clear agenda and business model. They use platforms to share their (criminal) activity, issue press statements, and more.
In 2022, the number of hacking groups increased globally, and it is expected that this upward trend will persist into 2023.
There are two types of hacking groups that we expect to see more of in the next year: hacktivists and data extortion groups. Let’s look at the main groups from both types of hacking groups we should pay closer attention to this year.
What are the Top 5 hacker groups we should monitor in 2023?
From all of the hacking groups that fall under hacktivism and extortion/ransomware groups, there are a few that stand out. We decided to list the active groups that we think rank high according to a few parameters, including the volume of their hacking activities, their sophistication, and the severity of their attacks.
Here are the top 5 hacking groups, in no particular order:

Brief Bio: LockBit 3.0
- Established: September 2019 (Lockbit2.0, was launched on March 22 before it re-emerged as LockBit 3.0)
- Type: Ransomware group
- Agenda: Financially motivated
- Main platforms: Tor blog
LockBit is one of the biggest and most prominent ransomware groups today. They are also the group responsible for the development and distribution of the LockBit ransomware available as a Ransomware-as-a-Service (RaaS), a triple-extortion method. This means the group has affiliates who carry out attacks using ransomware and split the earnings between the LockBit developer team and the affiliates.
Their attacks, whether they are carried out by the group or by affiliates, target organizations across the globe including high-impact cyberattacks of both the public and the private sector. The group is known for its sophisticated tactics, which include using multiple methods of distribution, such as phishing emails and exploit kits, to deliver the malware to victims.
The group maintains a dark web blog where they announce their attacks and release their victims’ data. They post their attacks with information about the attacked domain with a ransom demand and a countdown to pay it.
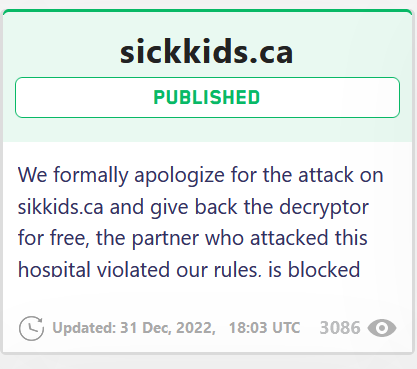
The group claims to be “ethical”, they state that they will not target healthcare, education, charitable, or social service organizations. Recently, they held up to their promise when they gave back a decryptor for free to a children’s hospital that was attacked by one of their affiliates who violated their rules.

Brief Bio: Killnet
- Established: January 2022
- Type: Hacktivists
- Agenda: Pro-Russian activism
- Main platforms: Telegram, in the past they also had an official website
Killnet is a pro-Russia hacker group known for its DDoS (distributed denial of service) attacks against anti-Russian governments and targets, especially NATO countries, such as the Romanian government.
The group’s DDoS attacks cause service outages lasting several hours or even days. Killnet operates a Telegram channel under the name “WE ARE KILLNET” for important announcements.
According to the group, their mission is to create a blockchain-based data warehouse to safely store the data without fearing law enforcement or big tech regulations. They used blockchain smart-contract technology using the Ethereum network for this warehouse.

Brief Bio: Desorden
- Established: September 2021
- Type: Hacking group
- Agenda: Financially motivated
- Main platform: Hacking forums
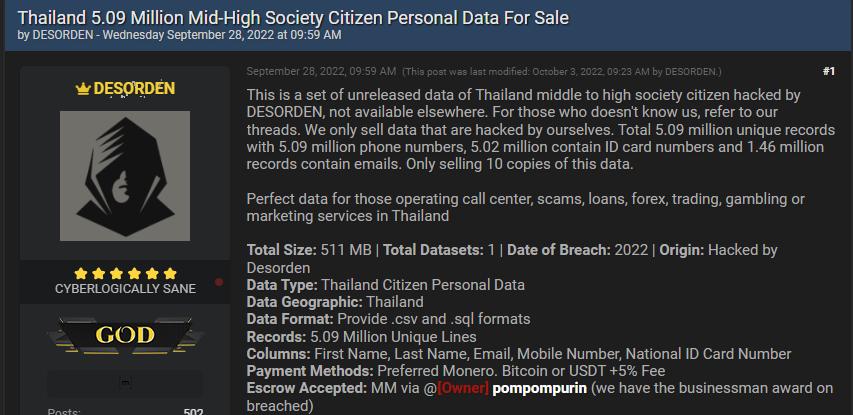
Desorden (Disorder in Spanish, previously known as ChaosCC), is a financially motivated hacker group. The group first emerged under the new name Desorden in September 2021, on Raidforums. Today the group maintains users under that name on several popular English-speaking hacking forums, where they share their attacks and ransom demands, and offer databases for sale. The group gained an excellent reputation among the cybercriminal communities due to their successful operations and the unique data that they share and offer for sale.
Desorden acts against high-revenue enterprises, supply chains, and public services in Asia. As their name suggests, their attacks and the extraction of sensitive organizational data of supply chains create disorder and chaos affecting many parties that go far beyond the specific victim they targeted.
The group’s latest attacks were against multiple Thai-based organizations, listed in what seems to be a region-based attack.
Their long victim list includes Acer, SkyNet.com.my, Malaysia Logistics, ABX Express Enterprise, and more.
Brief Bio: BlackCat/ALPHV
- Established: November 2021
- Type: Ransomware
- Agenda: Financial motives
- Main platform: Tor blog
ALPHV, also known as BlackCat and Noberus, is a major established ransomware-as-a-service (RaaS) family of Russia-linked ransomware affiliates.
Their ransomware is used by cybercriminal groups to launch attacks against governments and critical infrastructure organizations, as well as the energy, finance, construction sectors, and others.
The ransomware is offered as a RaaS by the group in dark web hacking forums. The affiliates pay a percentage of the profits they gain from using the ransomware to the ALPHV operators in return for their malware and services.
ALPHV affiliates implement multiple extortion techniques in addition to the encryption of the files on the victim’s network. These techniques include the upload of stolen victim data to a dedicated leak site, and blackmailing with DDoS attacks if they fail to comply with their ransom demands.

Brief Bio: Anonymous
- Established: 2003
- Type: Hacktivists
- Agenda: Activism
- Main platforms: Twitter, 4chan, and paste sites
Anonymous is probably the most known group out of all of today’s APT hacker groups. However, unlike other ones, Anonymous is not an organization but a decentralized, non-hierarchical movement with no single leader. Anonymous hackers are united by their common goal of social justice, reflected in the group’s intimidating motto: “We are Anonymous. We are Legion. We do not forgive. We do not forget. Expect us.”
An individual or group known as Anonymous first gained notoriety as a hacktivist through their involvement in “Project Chanology,” a series of actions targeting the Church of Scientology. More recently, they have been involved in cyber activities related to the ongoing conflict between Russia and Ukraine, including hacking into the websites of RT (a Russian state-controlled news network), the Russian Defense Ministry, and various Russian TV channels.
What to expect in 2023?
In 2023, we expect to see more and more activity from APT hacking groups. This will be the result of the increased use of cloud-based services, Smart Factory, and the Internet of Things, which can make it easier for attackers to gain initial access to a network and move within it. Existing groups will also keep updating their attack techniques, and new groups will emerge. With their main activities, today taking place on the deep and dark web, global intelligence organizations and enterprises today use Webz.io’s structured dark web data to monitor the activities of hacker groups in near real-time.
https://webz.io/dwp/the-top-5-hacker-groups-to-watch-in-2023/
Published: 2023 01 11 12:54:24
Received: 2023 02 02 06:25:41
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 3
