Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.The Dark Web in 2022: All You Need to Know About Data Leaks
published on 2022-12-07 09:06:06 UTC by Yuval ShibiContent:
The threat of data breaches has become one of the most widespread and damaging cybersecurity threats in the world today. During the past year, we have seen major breaches targeting all industries – governments, hospitals, automotive, cellular, TV, social media, retail, and software.
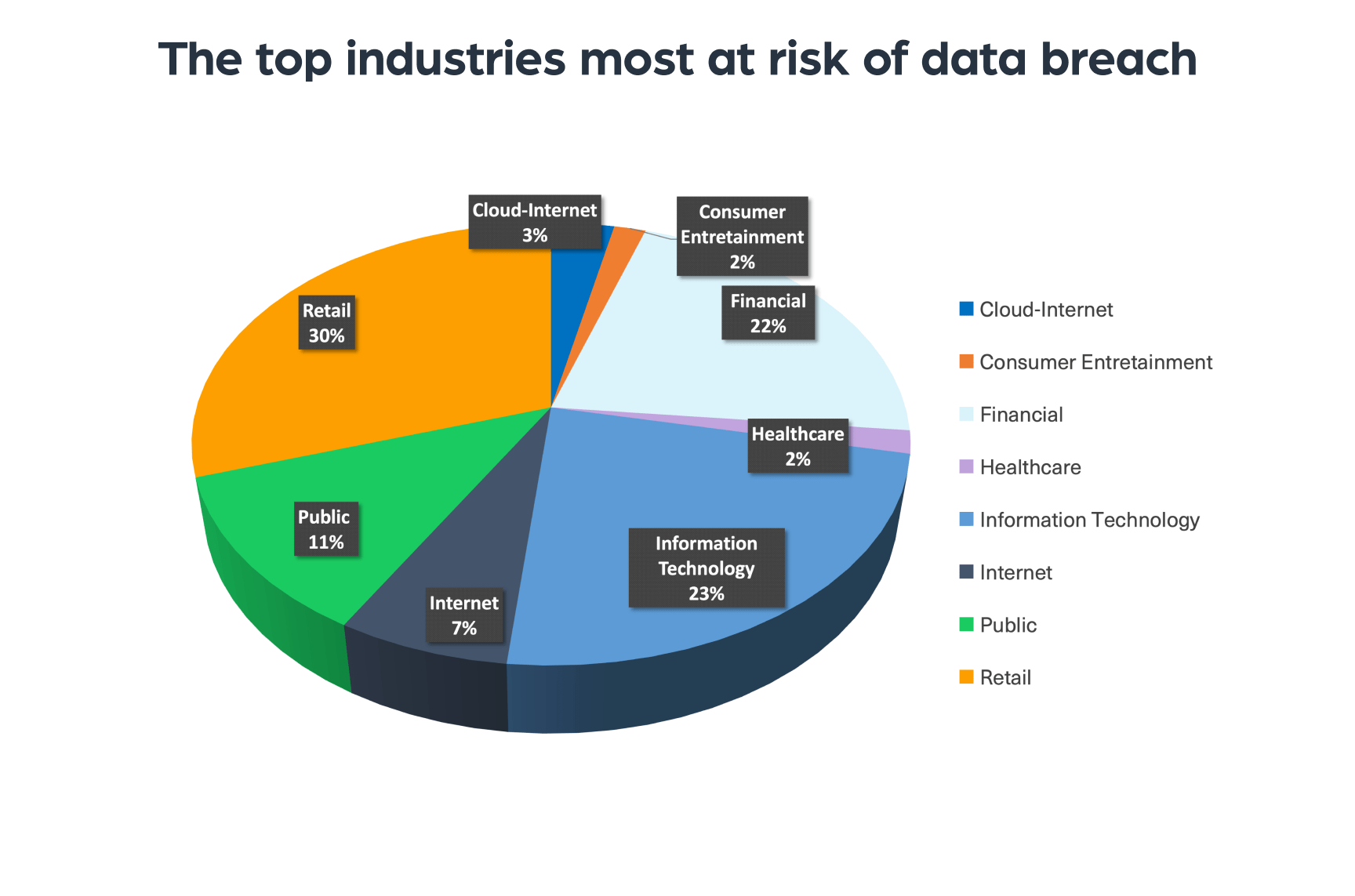
Cyberattacks and attempts to steal and sell data are sometimes aimed at specific targets (industries, executives), while other times they’re launched on any platform or domain the hackers can gain access to.
The main sources of leaked data
In 2022, RaidForums, one of the most popular sources for data breaches, was shut down and replaced with a new hacking forum, BreachForums, within days. There is an increasing amount of dark and deep web sources for data theft and trade. We can see it on hacker forums such as BreachForums and XSS, as well as on Marketplaces such as Russian Market and Genesis, chat applications such as Telegram, and paste sites such as PasteBin.
Let’s take a quick look at each of these sources.
Hacker forums
Hacking forums are fertile ground and the most common platforms cybercriminals use to trade stolen data, along with software vulnerabilities, hacking tutorials, etc. In terms of performance and data demands, threat actors are becoming more professional. Often, they won’t purchase data without a sample or proof of the value of the data they sell. Users who publish false information will be banned, which can be seen happening regularly on hacking forums.
Chatting apps
Chat applications are deep web platforms in which stolen data is traded and spread among cybercriminals. Threat actors are increasingly using instant messaging platforms, such as Telegram, for communication, and we see more and more data loss-related activity taking place on them.
Paste sites
Pastes are popular platforms for data loss-related activities due to the anonymity they provide to cybercriminals.
During 2022 we have witnessed the disorganized jungle of data breach activity undergoing further standardization in hacking forums, chat applications, and paste sites, as more and more cyber threat actors request and provide data that fit into certain categories.
To make both the search and the trade of stolen data more orderly and professional, hackers these days are expected to provide information to prove the value of the stolen data.
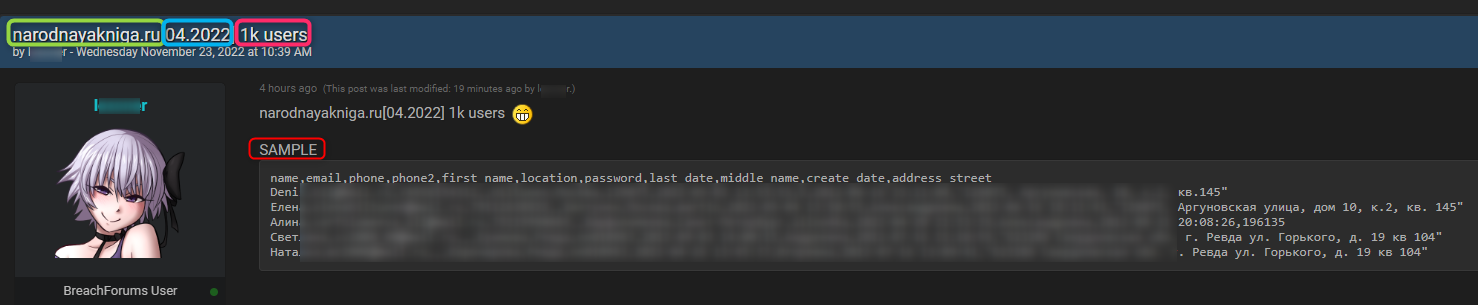
Some of the information they are required to provide include:
- The name of the hacked domain or platform
- The number of users that were breached
- The fields of compromised data that are found in the leaked document
- The date on which the data was originally breached, and whether or not it’s a repost
- A sample of the data to prove the value of the leak
Below is an example of a post published on BreachedForums, which publicizes a breach – which includes the details listed above:
The lifecycle of stolen data on the dark web
Data that has been stolen typically goes through a reposting process, which eventually decreases its value over time. First, the stolen data is usually offered for sale, then it is leaked for free, and finally, it is posted as part of a “combolist”.
Here’s a quick overview of the process:
- Leaks for sale – The more valuable the stolen data is the more likely it is to first be sold on the deep and dark web and not offered for free. The more useful and large-scale the data is, the higher its pricing will go.
- Lekas for free – When leaked data is sold, there is a high probability that it will, later on, be posted for free download on the deep and dark web since over time leaked data loses some of its value and starts to circulate among dark web users.
- Combolists – Following the publication of a leak for free, compromised account credentials can be collected by threat actors along with many more leaked entities under a new list called a combo list.
Data stores
Data stores are dark web marketplaces that only sell data – stolen sensitive data, such as stolen credit card details, bank account details, etc. These types of stolen data eventually enable threat actors to access a brand’s network/server/accounts, etc.
The first and major difference between stolen data entities that are posted on datastores compared to the other sources mentioned above, is the way they are stolen. While in the first-mentioned sources leaked data is posted as a breach of a domain or stolen credentials. In data stores, like Russian Market, the platforms are fed by RedLine malware. The RedLine Streamer is a stealer that steals almost any kind of valuable information on the computer, starting with browser-saved passwords.
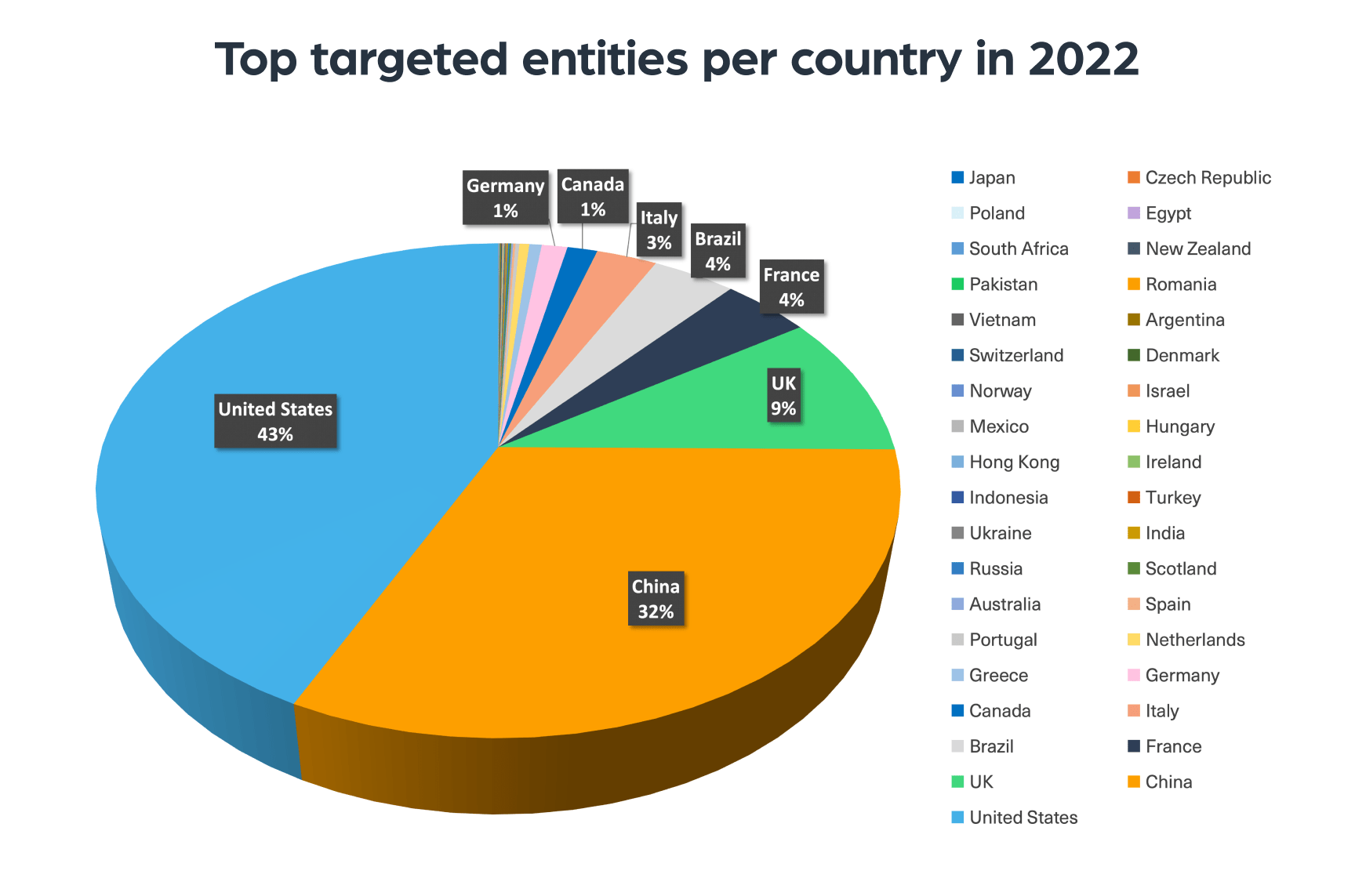
What countries were most targeted in 2022?
In the chart below we see an overview of the top countries whose entities were most leaked in 2022. Most leaked data was stolen from the US, China, the UK, France, Brazil, Italy, Canada, and Germany. Russia, Ukraine, and Indonesia were targeted on a similar level. The least leaked entities were from Sweden, the Czech Republic, and Japan.
Leaked data as a gateway to other data breaches
There are different risks and consequences that a data breach can lead to, depending on the type of data stolen and its scale. When credentials or any sensitive information is leaked, threat actors can use it to hack into the system again from a different penetration point, leading to repeated data breaches and at times further mass leaks. Take for example ransomware attacks, which are often launched through the theft of admin credentials for internal networks.
How can monitoring the dark web help prevent your next data breach?
With the rise in the number of data breaches, the need for timely and quality intelligence has become critical to keeping the data of enterprises, organizations, and individuals safe. Proactive monitoring is the best way to collect early indicators to prevent the next data breach.
Webz.io’s Cyber API, which provides structured and enriched deep and dark web data, helps organizations track high-risk signals related to data leaks. Webz.io’s Data Breach Detection API helps complete the picture and boost your intelligence with a repository of compromised credentials that were leaked, such as emails, passwords, usernames, credit card numbers, phone numbers, passport numbers, and SSNs.
https://webz.io/dwp/the-dark-web-in-2022-all-you-need-to-know-about-data-leaks/
Published: 2022 12 07 09:06:06
Received: 2023 02 02 06:25:41
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 3
