Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.What are the Biggest Cyber Threats to Banks on the Dark Web?
published on 2022-09-21 14:02:40 UTC by Hagar MargolinContent:
No business or industry is immune to cyber threats. Year after year, the rate of threats only continues to increase, and become more sophisticated.
The financial industry, and the banking sector, in particular, is among the most popular targets for cyberattacks because of the potential profit that is on the line. Only this week, the British Digital Bank Revolut reported a highly-targeted cyberattack that has affected over 50,000 customers.
Why are banking firms one of the most targeted sectors by cybercrime?
- Banks store a lot of sensitive information relating to their customers in their internal databases. In comparison to companies in other industries, cybercriminals may generate the largest amount of revenue from stealing that information, which makes attacking bank firms more worthwhile.
- Finance data or wire transfers have become more accessible with the growth of financial technologies and platforms such as mobile payments and online banking. There are now more platforms than ever before, as well as many other infrastructure systems and portals operated by banking firms, which provide more room for cybercriminals to exploit.
- Since banking firms hold a lot of sensitive client information, they are more likely to pay ransom in case they are hit by a cyberattack in an attempt to protect their clients, prevent data loss, and maintain their reputation. According to VMware’s 2022 Modern Bank Heist Report, 63% of financial institutions that reported being victimized by ransomware last year paid the ransom.
Threats against banking institutions on the dark web
By using our Cyber API, which indexes real-time data from dark web networks, we have been able to identify a clear upward trend which indicates that there is an increase in the number of potential cyber threats banks are facing in 2022. The following chart shows the volume of mentions of banks on deep and dark websites which show the high risk banks are facing today:
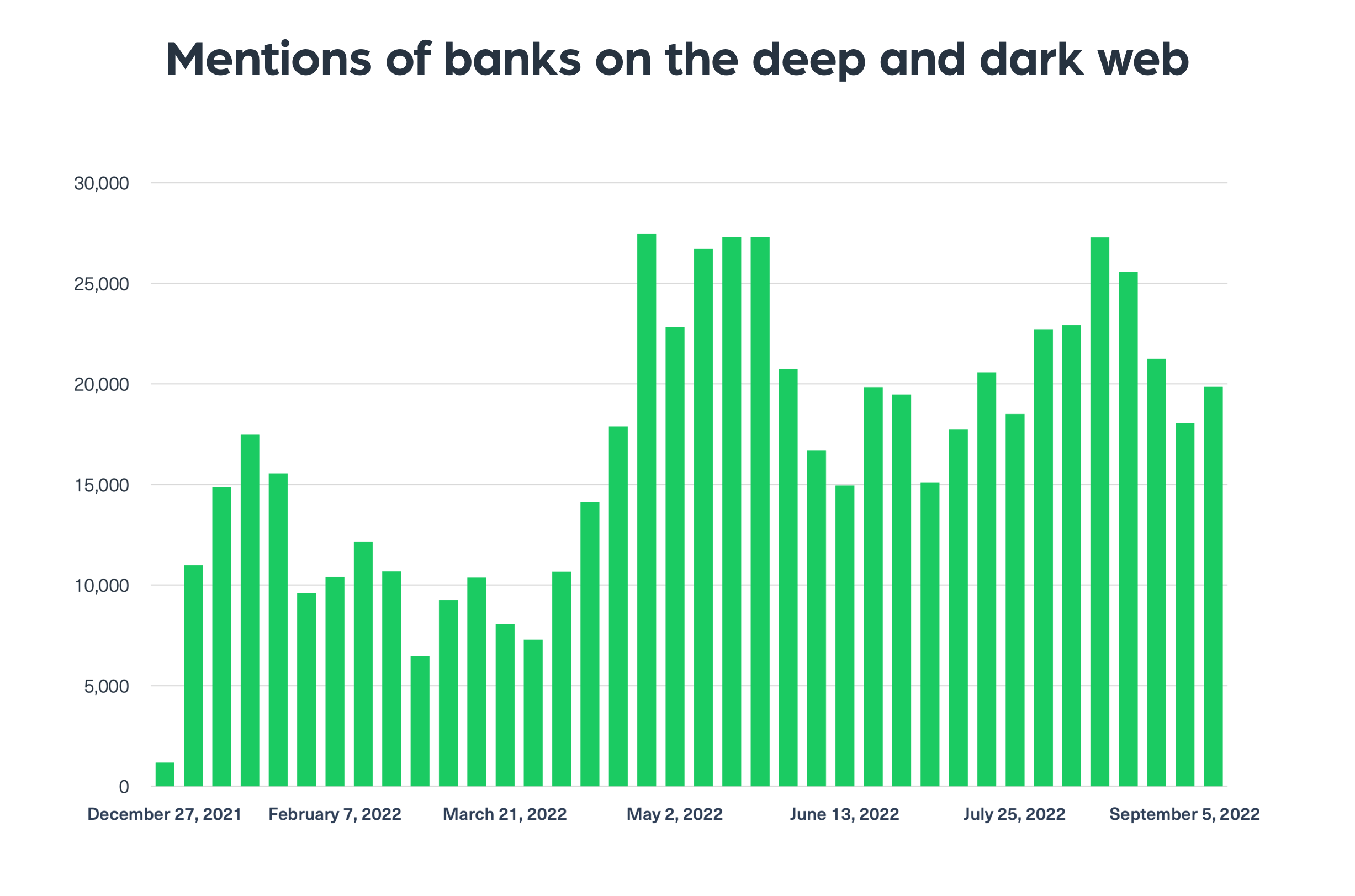
Let’s take a deeper dive into the top threats banks are facing on the dark web.
What are the top cyber threats for banks on the dark web?
Ransomware
One of the most popular and destructive types of cyberattacks in recent years is ransomware attacks.
Ransomware, which is a type of malicious malware, is designed to penetrate into the system of an organization, steal its internal information and encrypt the files so they won’t be accessible anymore. In return for decrypting the files and for not leaking out the compromised data, the cybercriminals are likely to demand a ransom from the victim, which makes this business usually very profitable and popular.
Due to the sensitive nature of data banks usually save on their customers, ransomware gangs consider banks to be attractive targets. According to an APWG’s report, while most sectors saw a decrease in the overall number of ransomware attacks against them in 1Q2022, the financial services industry saw a 35% increase in the number of attacks during that same time.
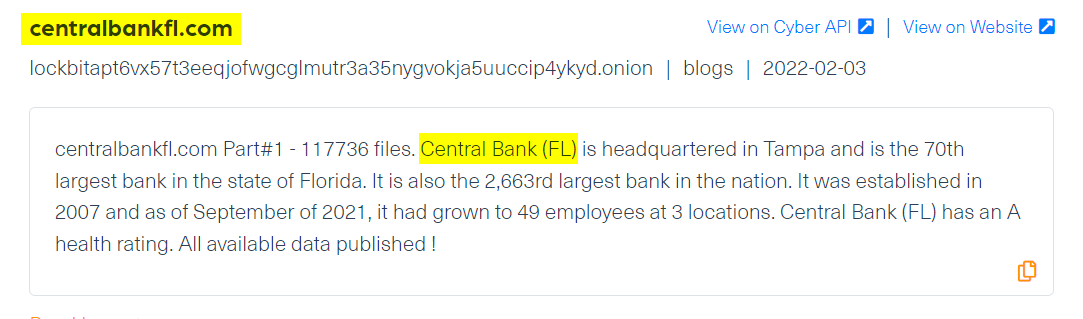
A notable example of a ransomware attack against a bank in the past year was that of the Central Bank of Florida. The bank announced already in February that an unauthorized party accessed consumer data, and ransomware group Lockbit took responsibility for the attack and leaked the first part of the compromised files:
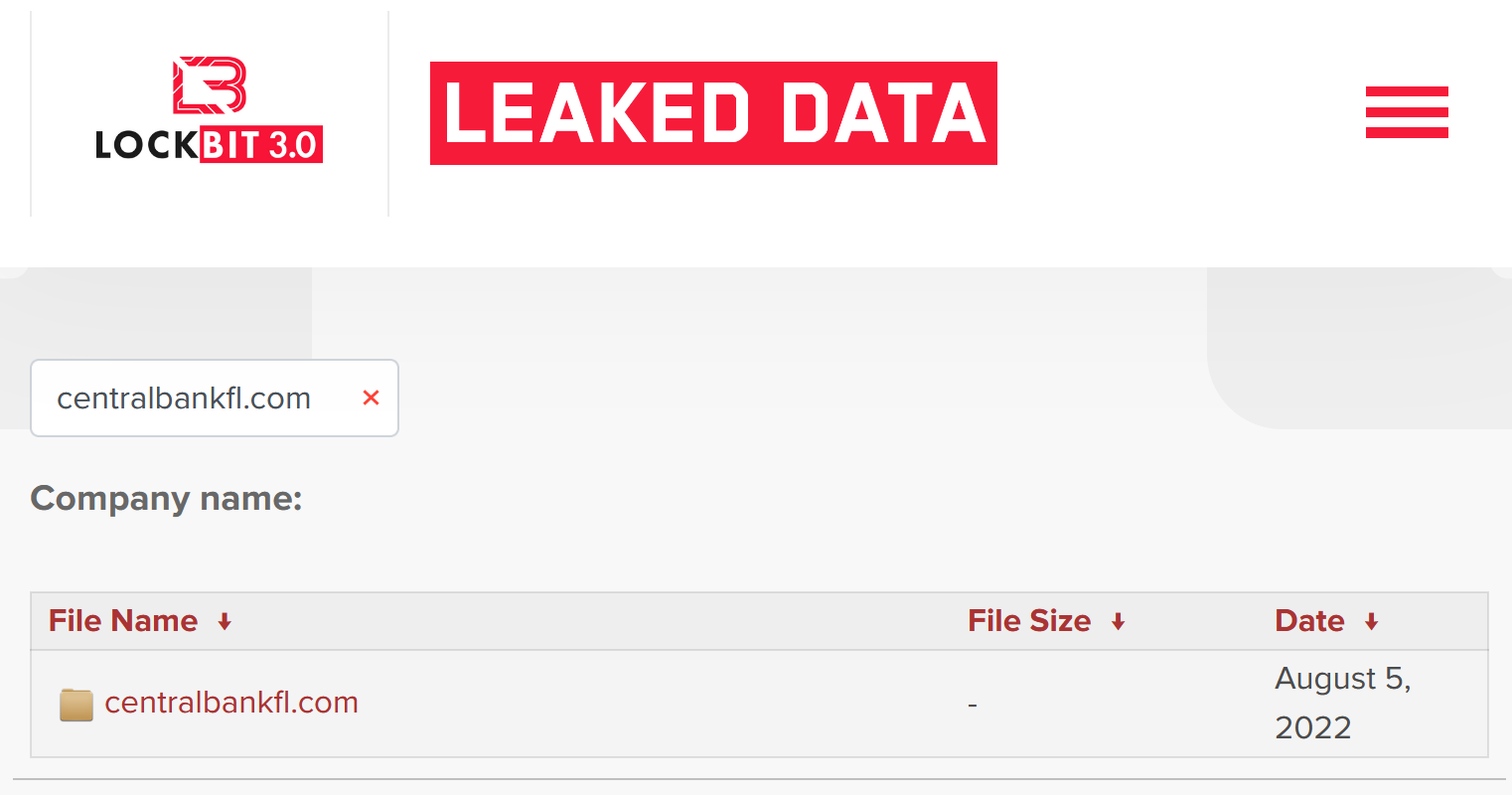
Last month, the group leaked the second part of the compromised data on their Tor website:
Phishing
Phishing is a social engineering technique cybercriminals use to trick users into divulging their personal information. The most common phishing attack against the financial sector targets their customers by sending them fake messages or emails disguised as their bank or other financial institution. This then directs the victim to a fake website that looks identical to the official site. Once the victim accesses the fake web page and fills in their login credentials, the cybercriminal is able to obtain them, and access the victim’s personal account.
According to Vade’s annual phishing report from earlier this year, the financial industry was the most impersonated industry in 2021, representing 35% of all phishing pages. This comes as little surprise since we can find many phishing tools readily available on the deep and dark web. Among the tools, we can find are phishing kits and phishing tutorials which are frequently sold at affordable prices, and enables cybercriminals to plan and execute phishing attacks with little effort. We can find those kits and tools being sold in hacking forums, dark web marketplaces, and chat platforms. Without dark web monitoring, companies may continue operating for some time before they will detect the phishing scam that compromised their systems.
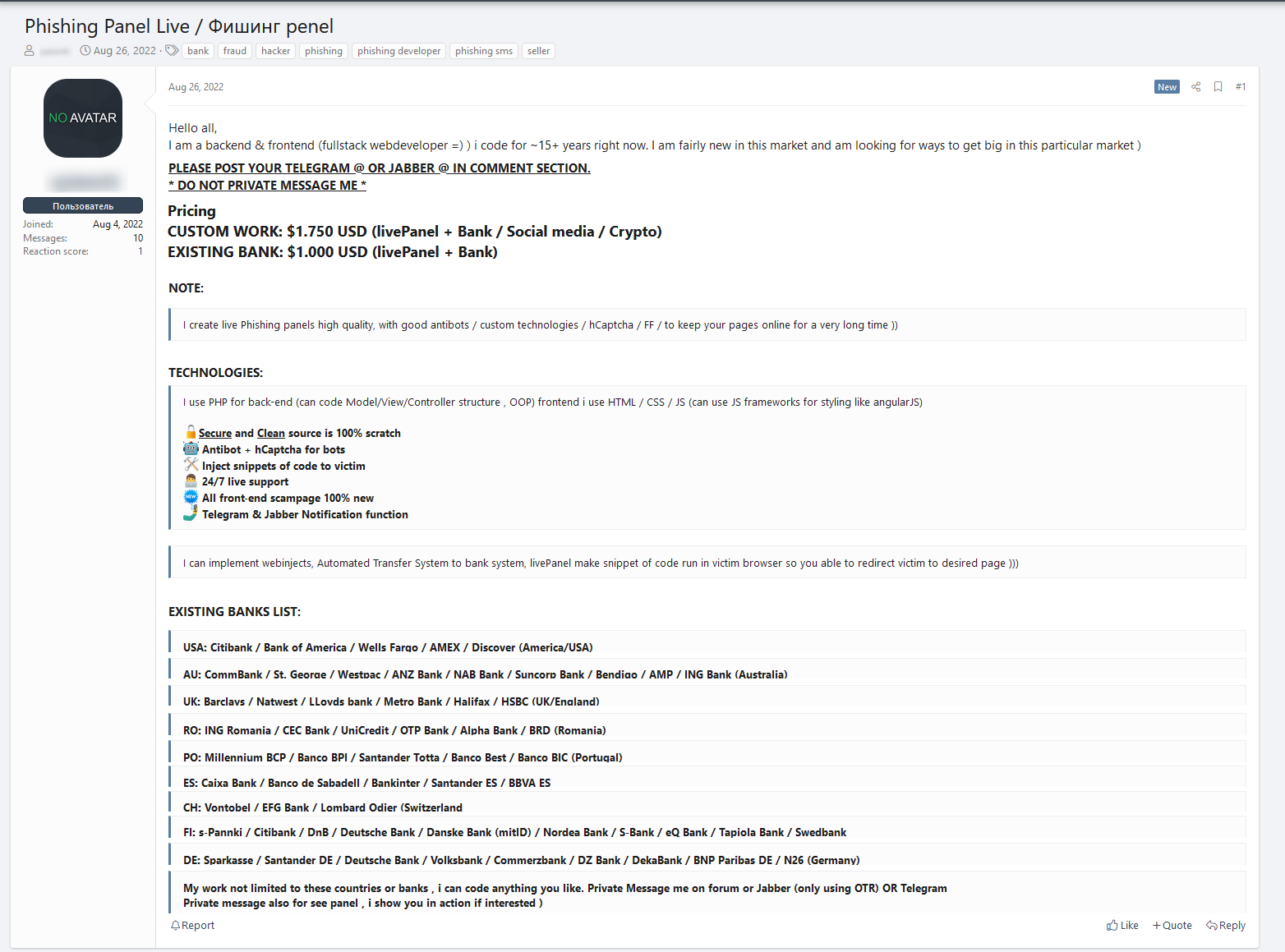
Take for example the following post, which recently appeared in a hacking forum. You can see that a threat actor offers to build custom phishing kits for a fee. His pricing list includes special prices for phishing kits for specific banks including Citibank, the Bank of America, and Wells Fargo.
Distributed Denial of Service (DDoS) Attacks
DDoS attack is an attempt by a threat actor to overwhelm a web server or network infrastructure with many requests in order to slow down or crash the service temporarily, preventing legitimate user requests from being processed.
According to a CloutFlare DDoS report, the banking industry was the second most targeted industry by DDoS attacks in 2022 Q2.
Just like ransomware attacks, DDoS attacks are also motivated by financial gain as many of them are driven by ransom demands. But another interesting motive for DDoS attacks, which have become very popular in recent years, is hacktivism. Here we refer to cyber attacks which are driven by political or social ideology. For example, one of the reasons for the rise of DDoS attacks against Banks in 2022 Q2 was the targeted attacks against Russian financial institutes in the aftermath of the Russian-Ukraine war.
The following post, which Webz.io crawled from a dark web hacking forum serves as the perfect example of targeted DDoS attacks against banks on the basis of hacktivism:
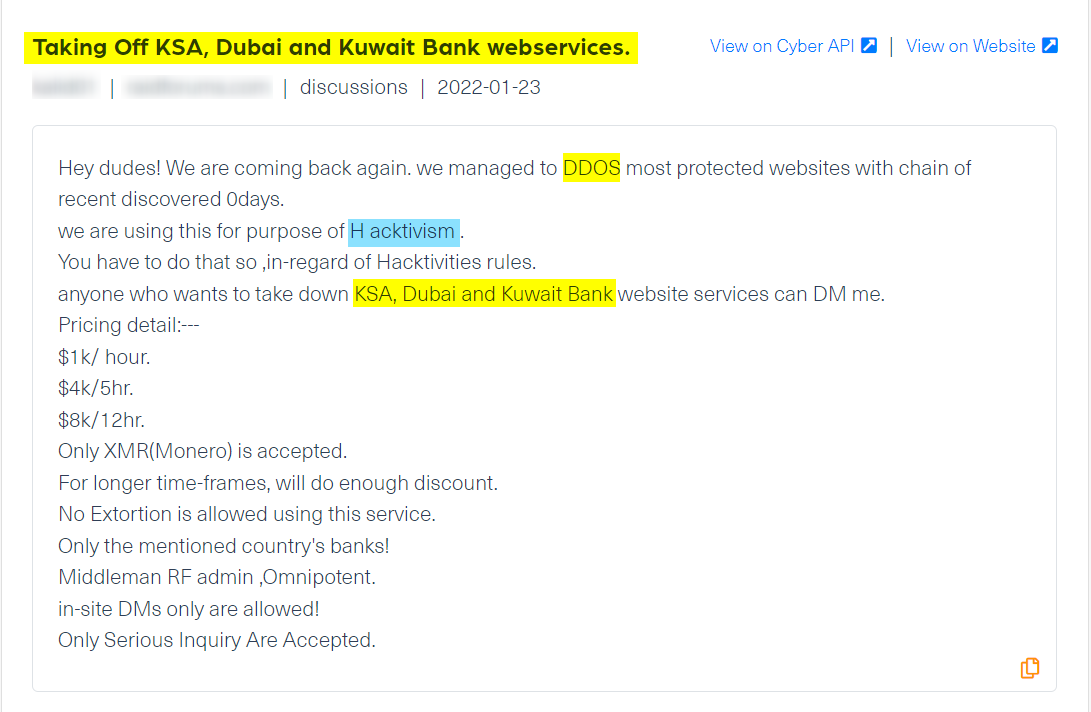
In this specific case, the bank website services of KSA (Kingdom of Saudi Arabia), Dubai, and Kuwait were the subject of the attacks.
Financial identity theft
Selling financial identity theft is the most common cyber threat to banking and financial institutions on the deep and dark web. Here we refer to the act of exploiting an individual’s personal information for financial gain. There are a variety of ways for carrying out this type of attacks such as using different malware or phishing methods, gaining access to leaked databases with stored credit card information, or even manual skimming with illegal card readers.
What are the most common types of financial identity theft that exist in the deep and darknet?
Credit card dump
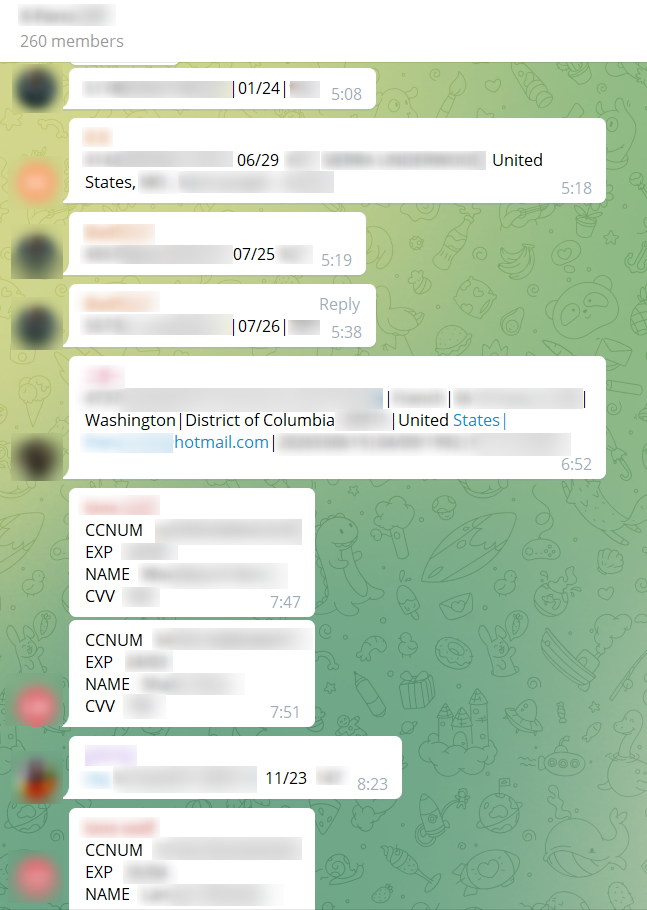
This is a type of crime in which credit card information is stolen from customers and put up for sale. Using the stolen information, the cybercriminal can also make fraudulent purchases online. Since the beginning of the year, we have crawled around one million stolen credit card numbers; most of them were leaked on Telegram groups. Here’s one example:
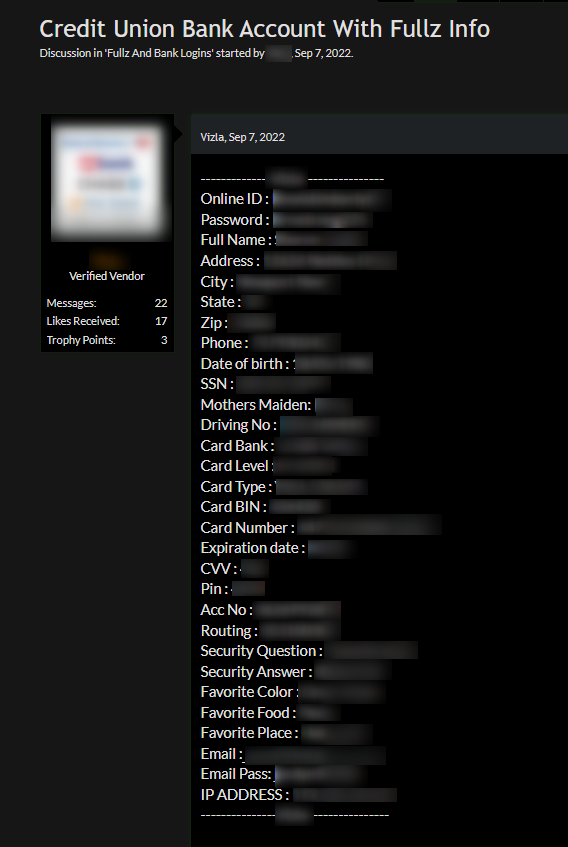
Bank drops
This is the act of using stolen bank account details, such as full name, date of birth, driver’s license details, contact information, SSN, financial account number, and credit score in order to open fake bank accounts. The whole package of this stolen information is called “Fullz” and is being sold on dark web marketplaces and hacking forums at affordable prices. They may be used by cybercriminals to store stolen money that will cover their tracks or to steal money by ordering credit cards fraudulently. This is hard for victims to detect sometimes, as in some cases, they will not receive a bill or statement if a new account is created with their stolen bank account details.
Backdoors Attacks
A backdoor is a security vulnerability that is able to remotely bypass an organization’s existing security systems and gain access to corporate systems without the need for authentication. The backdoor attack is designed not to be detected so easily, which also allows the threat actor to keep a low profile, leaving no traces behind. Using a backdoor, the cybercriminals are able to take many malicious actions on the system such as deploying spyware and stealing sensitive information.
On the deep and dark web, there are many cybercriminals that were successful in gaining access to the internal systems of organizations by using various types of backdoors. But many of them would rather sell it to a third party instead of using them to attack.
The following post is an example of one of those cases in which a threat actor offers a backdoor to Tajikistan Commercial Bank for sale on a widely known hacking forum:
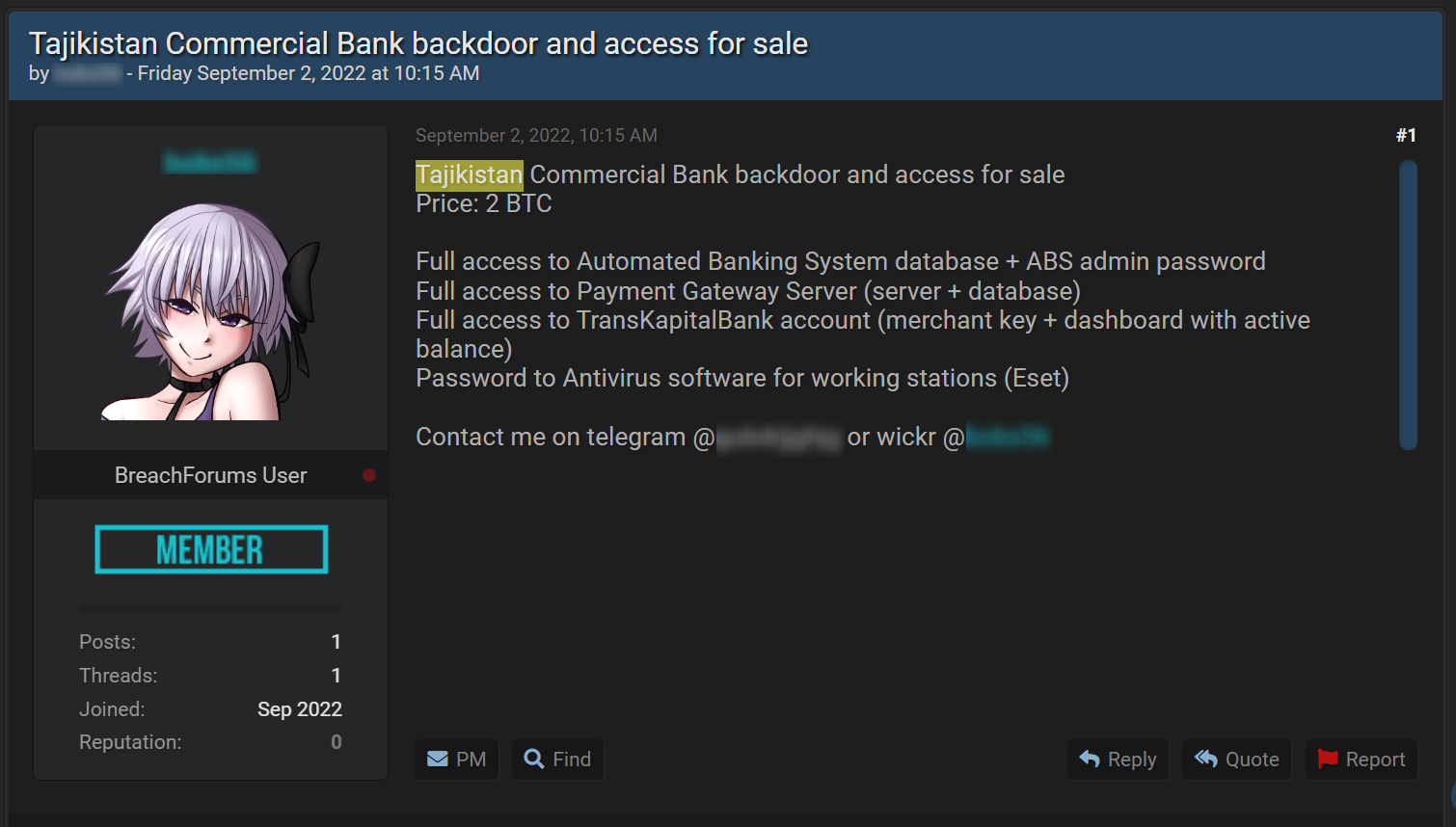
In the post, the threat actor specifies the type of access he managed to obtain into the bank’s system. If an organization monitors such existing backdoors in real-time, which are difficult to detect, it would be better positioned to minimize the damage and even prevent the cyberattack altogether.
Counterfeit
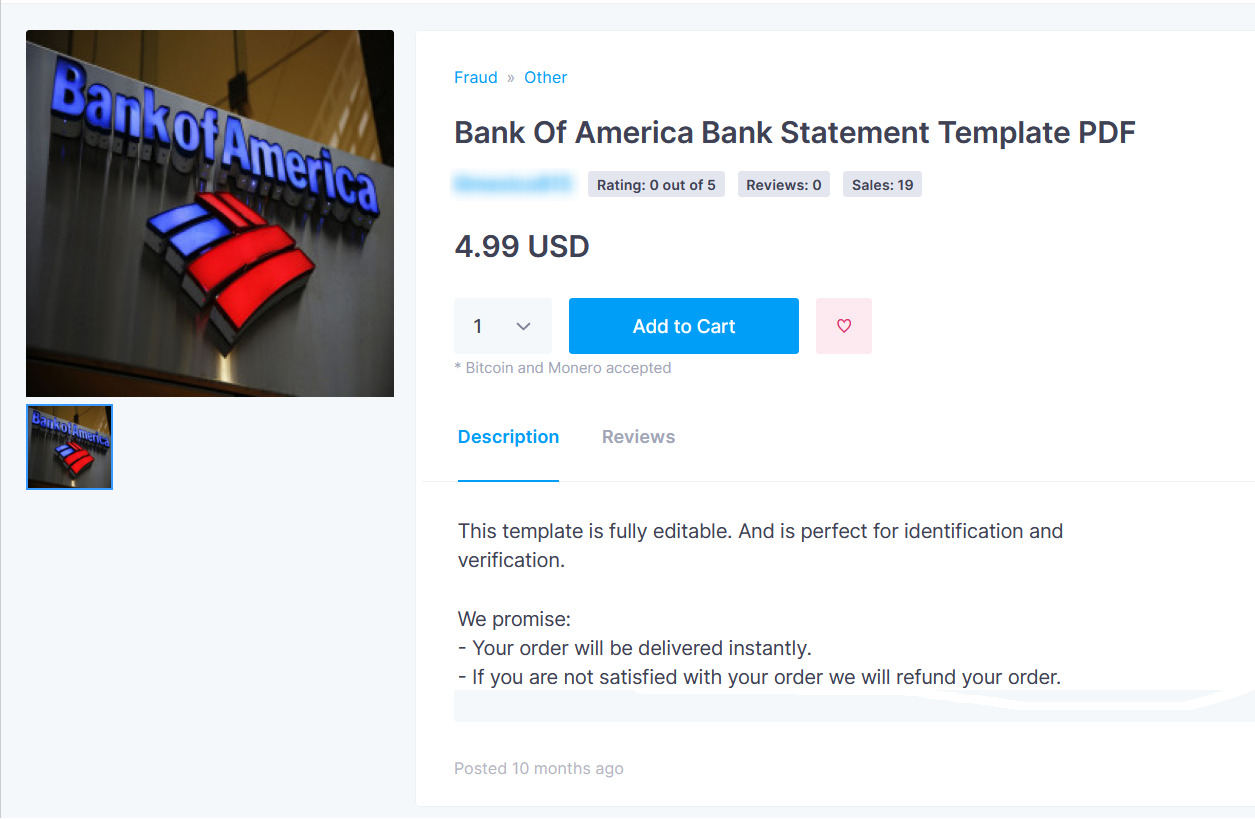
One of the popular products on dark web marketplaces that poses a threat to the financial sector is counterfeit enablers. Among the products that fall under this category are fake templates for bank and credit card statements, cheque copies, bank drafts, and even bank notes. Many of the documents are sold as PSD templates (usually pretty cheap) which the client can edit, and some of them are customized by the vendor for a higher price. These documents can be used by cybercriminals to commit a series of illegal activities such as bypassing online verifications.
Malicious insider threats
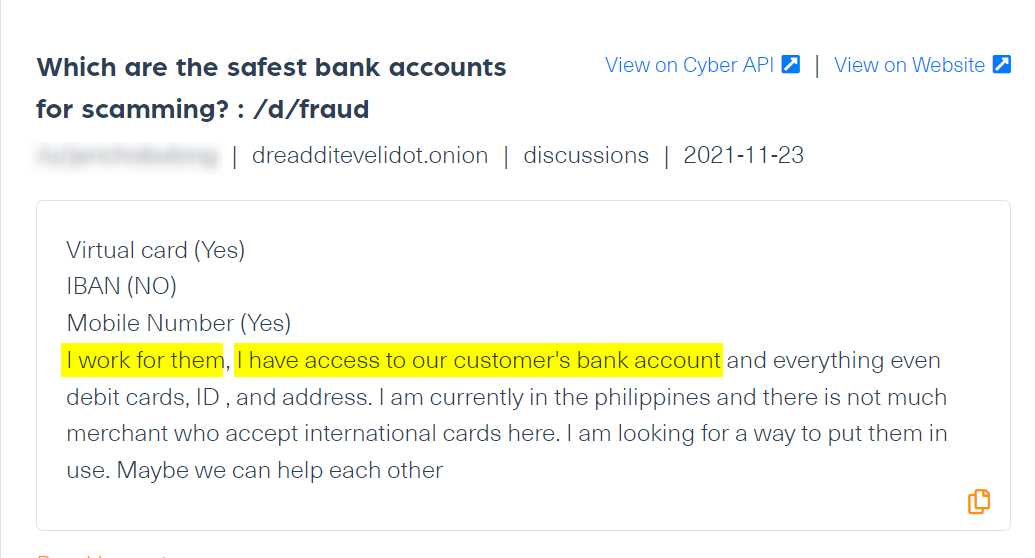
Malicious insiders are people with lawful access to internal tools, information, or systems within an organization who intentionally abuse this access (using legitimate credentials) for financial or personal gain. Malicious insiders are often current or former employees, contractors, or business associates. Insiders, whose main goal is usually making a profit, are either using their legitimate access to offer fraud services or sell the raw sensitive information they are able to access to a third party. In the financial sector, that sensitive information might be confidential customer information (such as bank account details) or other classified data related to the company.
Here’s an example of such an insider’s post relating to a bank in the Philippines:
Supply chain attacks
Supply chain attacks are carried out to breach a bank’s third-party vendor in its chain that is compromised. Usually, vendors take cybersecurity less seriously than their clients, and since they store sensitive data that belongs to clients, cybercriminals can exploit their vulnerability to attack the banks.
Since vendors are known to take fewer cybersecurity measures than their clients, they are an easier target to compromise. But the impact is far-reaching. Because third-party vendors store sensitive data of different clients, a single compromise could impact hundreds and sometimes thousands of companies.
Many banks use different vendors and third parties, making them susceptible to various attacks. From backdoor attacks to malware attacks and vulnerability exploitation, cybercriminals can use a weaker spot in their vendor’s system to access their own system.
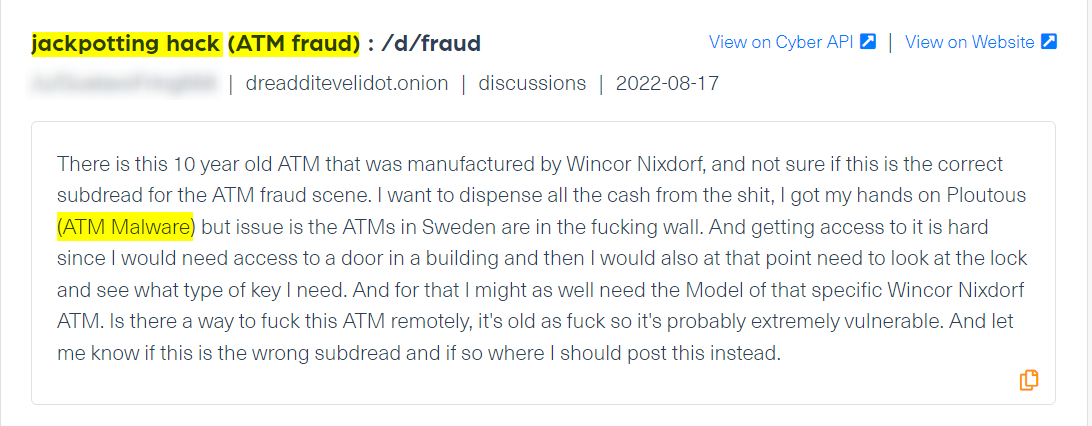
ATM jackpotting is one of the classic examples of supply chain attacks for banks, in which physical or software vulnerabilities in automated banking machines (which are manufactured by banks’ vendors) are exploited to disburse cash. This also requires physical access to an ATM machine. ATM jackpotting essentially allows criminals to access the machine’s cash reserves, which are not linked to the balance of any one bank account.
We can see many discussions about ATM Jackpotting on the deep and dark web, including the trade of guides. In the following post, a threat actor says he is planning to carry out an attack on an ATM manufactured by Wincor Nixdorf using Ploutus (ATM Malware). The actor also asks for advice from the dark web forum Dread members regarding some problems he encountered:
The deep and dark web platforms that consist of many different marketplaces, hacking discussions, and closed chat rooms are fertile grounds for the trade of malicious information. This includes the trade of hacking tools and exploits, malicious guides, phishing kits, special malware, compromised databases, and even zero days. Cybercriminals also use these platforms to share with fellow threat actors their intentions to carry out a certain cyber attack, some in an effort to get feedback, and others seek partners to carry out their attack. All this is taking place in the planning stage before and the beginning of the attack, but also during and after the attack. Monitoring these platforms to identify potential cyber threats, and an attack in the making is critical for any organization.
https://webz.io/dwp/what-are-the-biggest-cyber-threats-to-banks-on-the-dark-web/
Published: 2022 09 21 14:02:40
Received: 2023 02 08 12:46:25
Feed: Webz.io Dark Web Posts Dark Web News
Source: Webz.io Dark Web Posts
Category: News
Topic: Dark Web
Views: 21
