Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Revealed: The 1B Data Leak Post Everyone Has Missed
published on 2022-07-20 10:26:24 UTC by Yuval ShibiContent:
A massive database containing the personal information of 1B Chinese citizens was offered for sale on two dark web hacking forums on June 28, two days before the post the media claimed to be the original leak.
This mass breach of personal identifying information, likely one of the largest leaks in history, included names, addresses, national ID numbers, phone numbers, and incident reports of a billion Chinese residents.
Using Webz.io’s Cyber API, we looked to find the original post and discovered the database was published on two dark web hacking forums Ramp and Exploit, two days before the post the media quoted.
The next post (see below) is the database the media claimed to be the original leak:
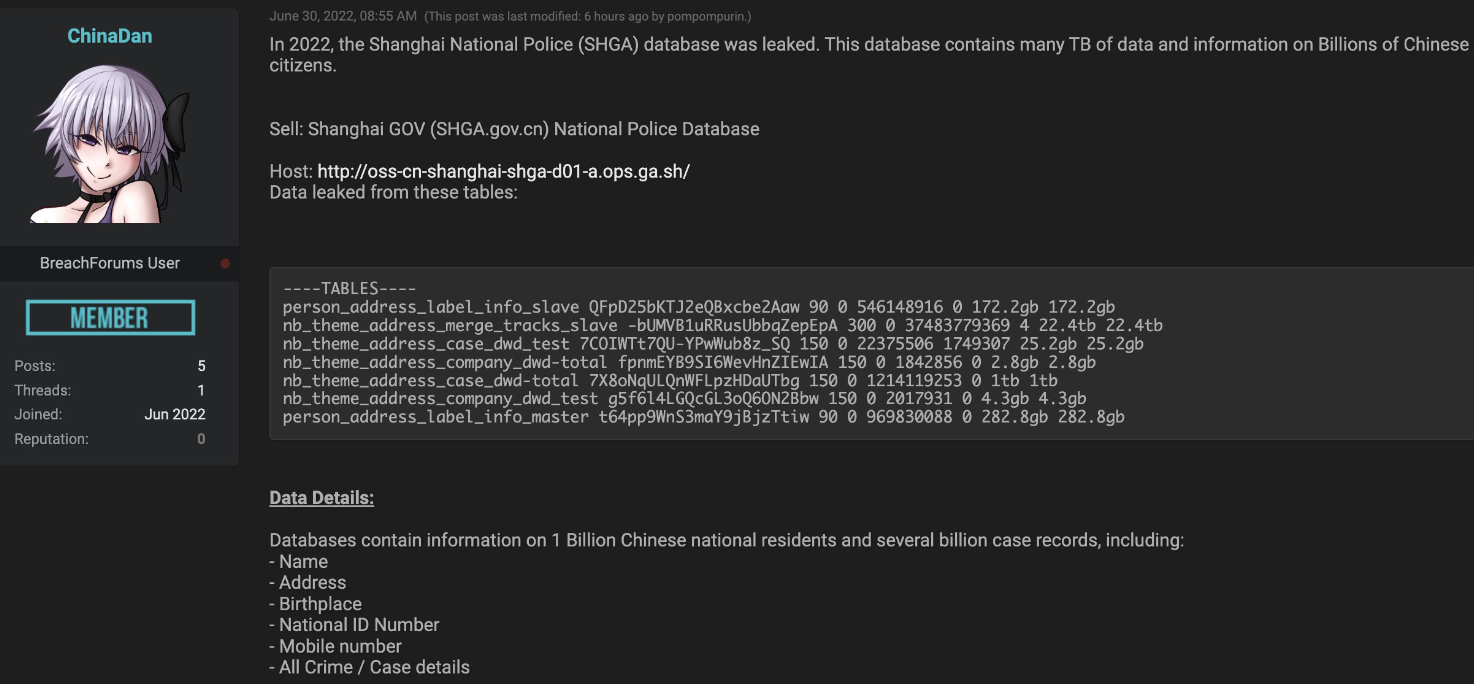
This database was published by a threat actor who goes by the name ChinaDan on breached.to, and the file was removed hours later. It was first offered for sale for 10 Bitcoins (equal to about $200,000).
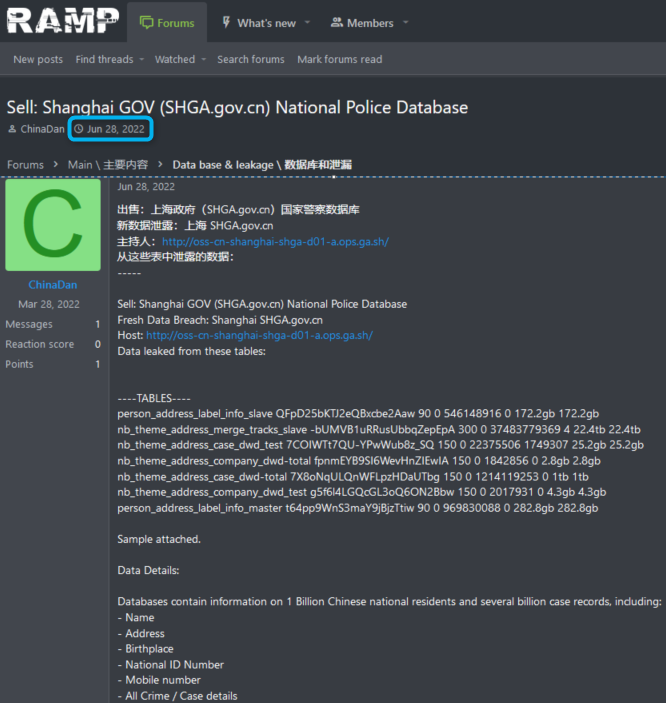
But in this exclusive report, we bring you the first post that was published, by a threat actor under the same name, ChinaDan on Ramp:
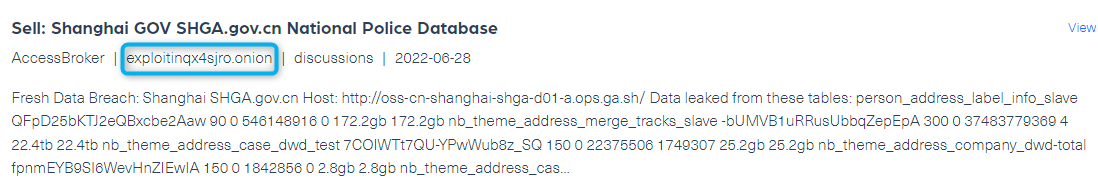
The database was published again on the same day, only 4 hours later, by a different threat actor named AccessBroker on dark web forum Exploit:
How was the data breached?
According to reports, the data was left publicly accessible and unsecured for over a year, between April 2021 and June 2022, until ChinaDan exposed it. According to cyber security experts, the hacker was able to access the data due to an unprotected Kibana instance that was non-password-protected since the end of 2020. After being exposed for over a year, the data suddenly disappeared and was replaced with a ransom note.
How can crawled dark web posts reveal the full picture?
Dark web forums provide a valuable source of information for monitoring threats in real time. One of the main challenges when tracking the footsteps of threat actors and potential threats like a data leak, is the ability to find posts as they are often removed. This is a challenge that can be overcome when using dark web feeds. Because we crawl content in near real time, our customers are able to access posts that have been removed or changed and get the full context. This is how intelligence and cybersecurity teams can gain a deeper understanding of potential threats, the complete meaning of an alarming post , its risk, and the necessary steps they need to take to protect their assets.
https://webz.io/dwp/revealed-the-1b-data-leak-post-everyone-has-missed/
Published: 2022 07 20 10:26:24
Received: 2023 02 08 12:46:25
Feed: Webz.io Dark Web Posts Dark Web News
Source: Webz.io Dark Web Posts
Category: News
Topic: Dark Web
Views: 15
