Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Why Did Hacking Group Killnet Attack Romanian Government Sites?
published on 2022-05-16 12:57:19 UTC by Liran SoraniContent:
Websites belonging to key Romanian ministries were hit by a series of cyberattacks. A pro-Russian hacking group, Killnet, claimed responsibility for the strategic attack. It came after previous attacks and threats against pro-Ukraine entities and a lot of hostile chatter on the deep and dark web.
Here’s what we know.
What sites were targeted?
The Killnet attack, which took place on April 29, targeted various strategic websites belonging to the Romanian Government, including:
- gov.ro – the Romanian government’s domain
- mapn.ro – the domain of the country’s Ministry of Defense
- politiadefrontiera.ro – the domain of the Romanian Border Police
- cfrcalatori.ro – a site belonging to Romania’s National Railway Transport Company
- otpbank.ro – a domain that hosts the Romanian site of a commercial bank operating in Romania
What was the method of the attack?
The hackers used a DDoS (Distributed Denial of Service) attack, which automates mass network requests, usually from different sources, to overwhelm the targeted network (a website or online service). The aim is very clear – to disrupt the network and put other legitimate requests in timeout.
Who are Killnet?
Killnet was formed in January 2022. The group are considered to be pro-Russian programmers. Their first post was published on January 23 on a known TOR Russian forum – Rutor.
They announced the new botnet “killnet”.They said it will be for distributed encrypted method of storing data.
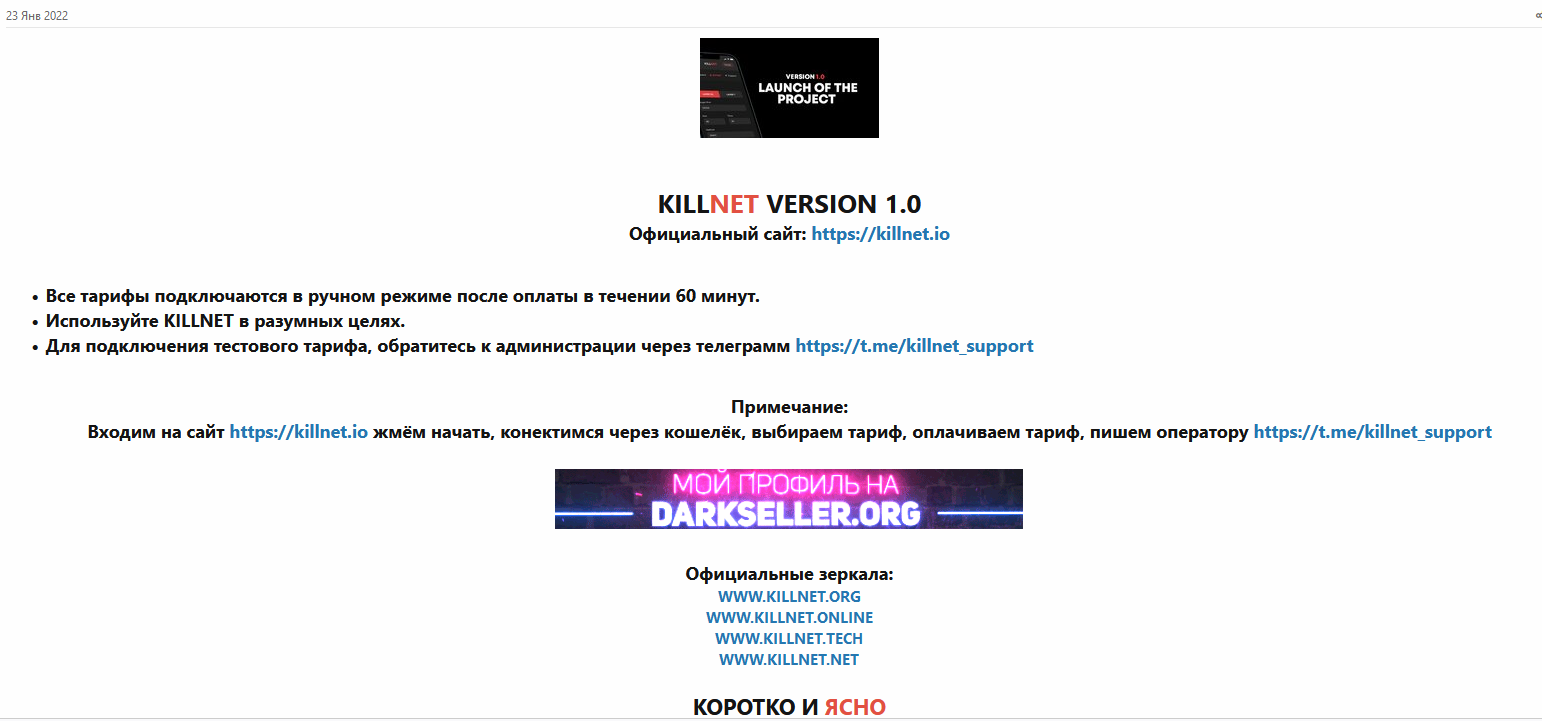
They also opened a Telegram group under the name “WE ARE KILLNET” for important publications
their official Telegram channel:
Their mission (according to their posts) is to create a blockchain-based data warehouse to safely store the data without fearing law enforcement or big tech regulations. They used blockchain smart-contract technology using the Etherium network for this warehouse.
Why did Killnet attack Romanian government domains?
By closely tracking the group’s activity on the deep and dark web, we could find a few indications that Killnet were planning anti-government attacks, and more specifically, attacks against pro-Ukrainian entities.
On February 9, they announced their main mission on Rutor, which is to create a DDoS botnet available to all, some of the users have already tried their botnet, and some even requested to add more features.
But then, on February 25, only a day after Russia’s invasion of Ukraine, we found the first sign that Killnet was going to target the government sites of pro-Ukraine governments and organizations.
After hacking the famous Anonymous site, Killnet released a video, which they published on Anonymous’ site on Tor, where they claimed that the internet is full of disinformation and that “Everything that is happening now in the world… had to happen sooner or later,” blaming the situation on the United States, the European Union, and the current Ukrainian government.
From that point on, Killnet geared its attacks at Ukraine.
In early March, the group attacked websites belonging to the Ukrainian government. Next, they issued warnings and threats against NATO and other European organizations that support Ukraine. This all led to their latest attack in late April against a list of strategic Romanian governmental websites.
We can also find the trend when we use our Cyber API to search for mentions of gov.ro domains (shown in the chart below) on Tor, the open web and Telegram in the lead up to the attack:
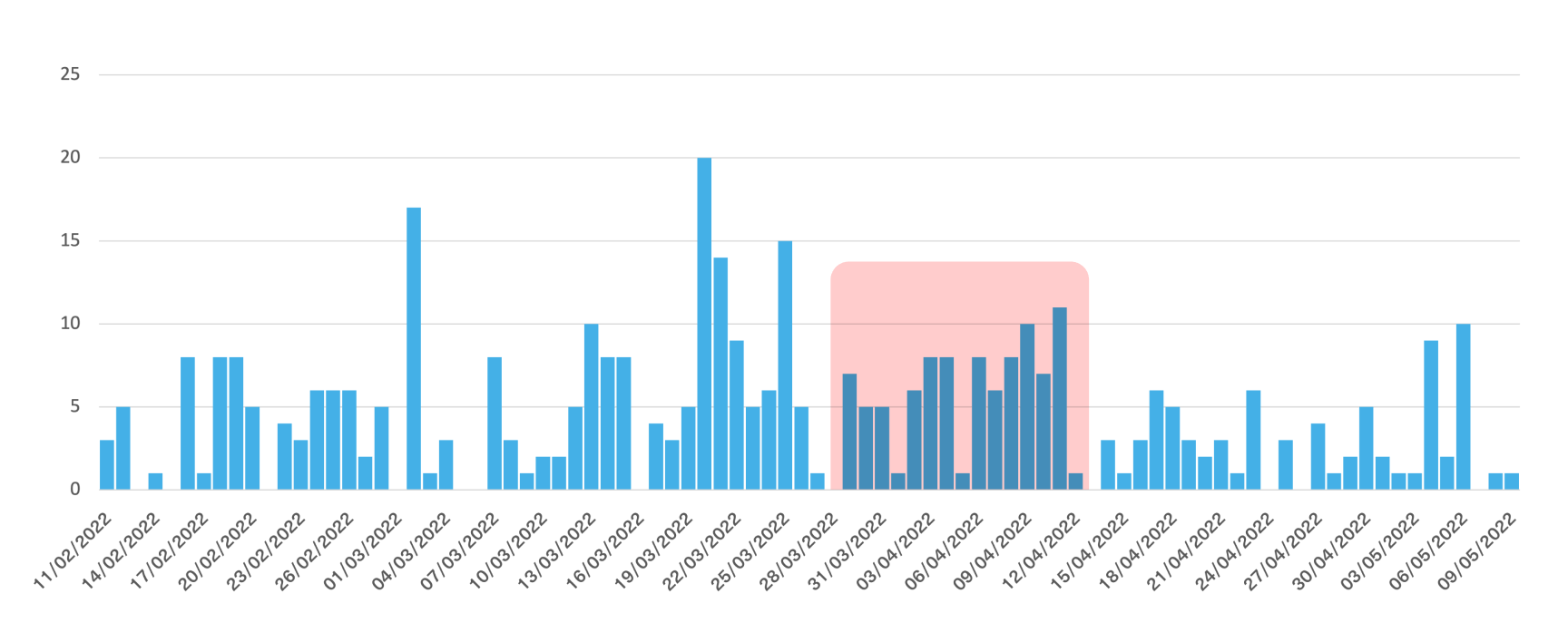
The majority of the mentions of Romanian governmental domains appeared on Russian hacking forums and marketplaces such as Russian Market, Genesis, and 2Easy.
This chart shows that by tracking mentions on the deep and dark web, you can collect intelligence on upcoming attacks against organizations, enterprises, and people as threat actors continue to organize attacks on dark web forums, chat apps, and marketplaces.
https://webz.io/dwp/why-did-hacking-group-killnet-attack-romanian-government-sites/
Published: 2022 05 16 12:57:19
Received: 2023 02 08 12:46:26
Feed: Webz.io Dark Web Posts Dark Web News
Source: Webz.io Dark Web Posts
Category: News
Topic: Dark Web
Views: 34
