Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Revealed: The Dark Web Risk Score for Top VPN Providers
published on 2023-02-01 13:49:45 UTC by Liran SoraniContent:
VPN, which stands for Virtual Private Network, is a service many of us know and use. It refers to a technology used to establish a secure and encrypted connection over a public network, like the internet. While VPNs use encryption to protect data and mask the user’s IP address, they have also been scrutinized for their security risks.
Who uses VPNs?
Most of us at one point or another have used VPNs for various purposes.
In the business world, the leading VPN users include:
- Remote workers who want to access their company’s network from a remote location securely. This has become widespread since the beginning of the Covid–19 pandemic
- Companies and organizations to secure their network and protect sensitive data from cyber attacks
- Companies and individuals who want to bypass local restrictions and access geo-restricted websites
How secure is a VPN?
While using a VPN can provide privacy and security benefits, they are not flawless. Even reputable VPN providers can have security vulnerabilities, and there is always a risk of server compromise or configuration errors that can put user data at risk.
As always, we turned to the dark web to find out what threats we could find relating to VPNs. For this purpose, we examined what is considered by some as the leading VPNs, and used our Dark Web API to identify the level of risk of these VPN providers on the dark web (searching by mentions of digital assets).
The top VPN providers ranked by dark web risk score
We decided to rank each major VPN provider over the past 3 months according to the level of risk they face on the dark web. The score ranges from 1 (the lowest) to 10 the highest level of risk.
The calculation is based on two parameters:
- The number of mentions of the VPN provider within cybercriminal groups and sites on the dark networks, including underground forums and dark marketplaces.
- An average cyber risk score was given to individual posts based on their severity. That can refer for example to discussions around hacking or exploitation of VPNs, leaked VPN accounts, and CVEs that can be exploited to breach into VPN providers and intercept sensitive traffic.
As can be seen in the table below, most of the popular VPN providers are at medium to high risk:
| VPN Provider | Domain | No. of Malicious Mentions | Total Risk |
| CyberGhost VPN | cyberghostvpn.com | 7,238 | 7 |
| PrivateVPN | privatevpn.com | 500 | 6 |
| ExpressVPN | expressvpn.com | 112,361 | 6 |
| Hotspot Shield | gohotspotshield.com | 60,900 | 5.5 |
| PiaVPN | privateinternetaccess.com | 1,126 | 5.5 |
| StrongVPN | strongvpn.com | 387 | 5 |
| Surfshark | surfshark.com | 55,595 | 5 |
| NordVPN | nordvpn.com | 301,341 | 5 |
| IPVanish | Ipvanish.com | 149,654 | 5 |
| Atlas VPN | atlasvpn.com | 54 | 4 |
As we can see from the table above, no VPN is really safe. In fact, the majority of the leading VPNs we reviewed are facing many varying levels of risks on the deep and dark web.
Let’s review some examples of risks VPNs are facing on the dark web.
Example #1: Malicious discussions about FortiClient CVE
A recent FortiClient CVE, CVE-2022-42475, was shared in a known Russian hacking forum XSS. The CVE was officially published on January 2, 2023, and was already discussed 10 days later. The publisher shared the information to discuss how the exploit can be maliciously used to compromise organizations. Other forum members engaged and commented in order to understand how it works.
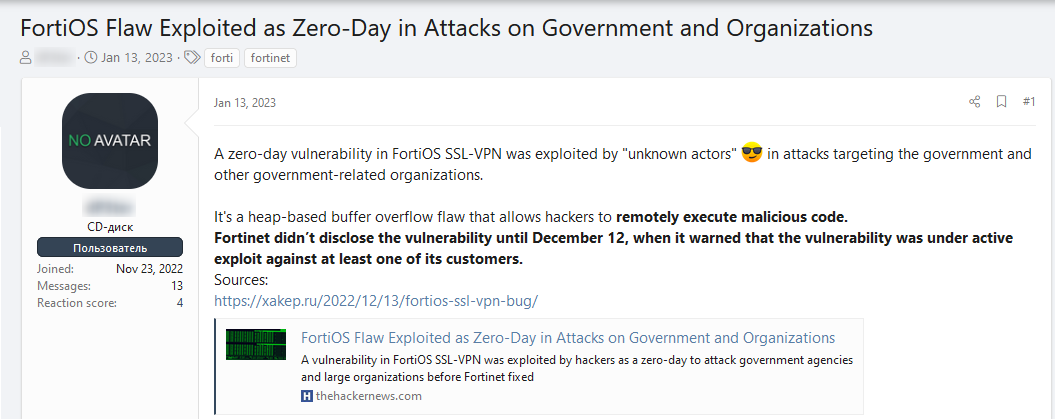
The CVE-2022-42474 is exploiting a buffer overflow vulnerability in Forti SSL-VPN, which belongs to FortiClient, a well-known VPN server-client solution, which is used by a wide range of organizations including banks, credit card companies, government organizations, and others.
This FortiOS exploit is a major exploit that requires an update in order to be protected.
Example #2: Hackers’ discussions about Cisco Systems VPN Client
CVE
We found another example on XSS forum where CVE 2022-20699, a critical vulnerability allowing privileged access to Cisco Systems VPN Client, was published:
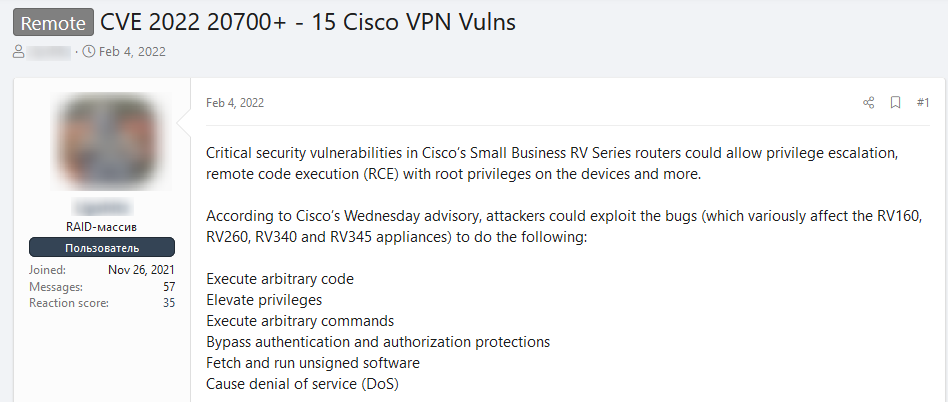
The CVE allows a hacker to perform RCE (Remote Code Execution) with elevated privileges, bypassing authentication due to insufficient memory checks in the SSL-VPN protocol.
The CVE affects popular Cisco routers that are used by many organizations.
Other XSS users expressed interest in the vulnerability and shared how to look for relevant devices that can be compromised.
Example #3: VPN leaks
Every day thousands of VPN accounts are being leaked on the deep and dark web. The leaks usually include login credentials.
There are two main implications to this:
- The compromised accounts are traded or shared for free – and others can freely use them until they are blocked
- Other hackers can use them to log in to the account’s web administration and exploit important information, such as browsing history or redirection to efficiently compromise sensitive information
In the next example you can see a post offering hundreds of IPVanish accounts for free:
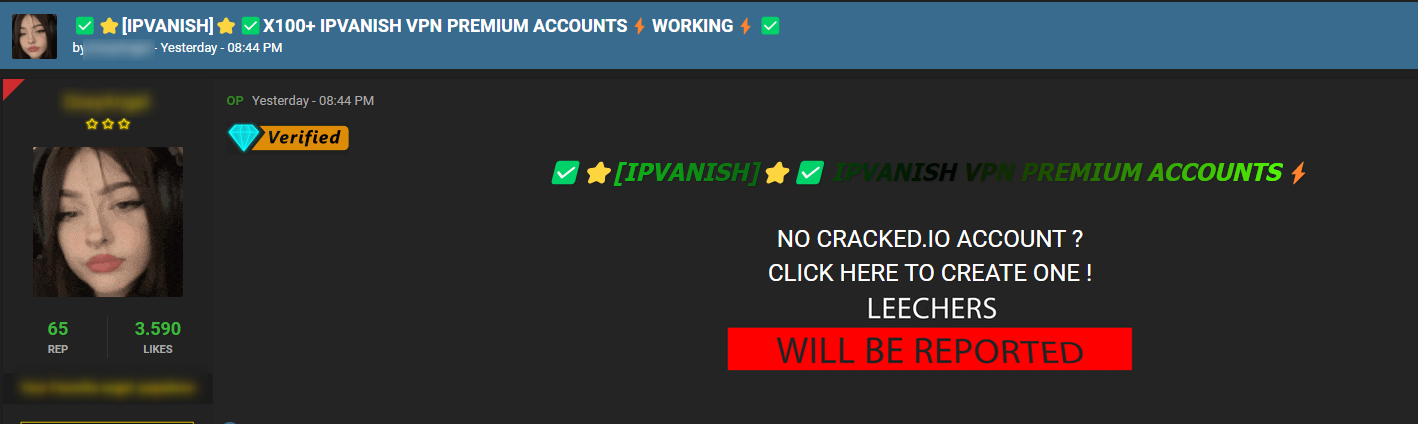
The post received quite a few reactions indicating that the leaked accounts were used.
How can monitoring the dark help identify risks to VPNs?
Monitoring the dark web can provide insight into current and emerging threats, allowing organizations and individuals to take proactive measures to protect themselves.
Using Webz.io’s Cyber API, we were able to find various discussions around cyber threats to VPNs in general and to specific VPN providers in particular.
The main content we found included:
- Stealing of credentials belonging to VPN users
- Vulnerabilities in encryption algorithms VPN providers are based on
- VPN scams such as Honeypots – free VPN services that can steal your data and also infect your device with malware
What’s next?
The use of VPNs is expected to rise in 2023, which means it is more critical now than ever to take proactive measures in monitoring and protecting against threats stemming from the use of VPNs.
With the increasing reliance on third-party services and remote devices, it can be challenging to keep track of all online activities. To mitigate these risks, organizations should implement a customized monitoring approach that meets their specific needs. This approach can help detect new risks relating to VPN providers as well as third-party devices and applications associated with the organization.
Tracking dark web data can prove to be a powerful tool to stay ahead and mitigate emerging risks associated with VPNs. Webz.io’s Cyber API can help individuals and organizations stay informed about potential threats by providing steady, consistent, and comprehensive coverage of the most important deep and dark web forums and marketplaces critical to tracking malicious activities
https://webz.io/dwp/revealed-the-dark-web-risk-score-for-top-vpn-providers/
Published: 2023 02 01 13:49:45
Received: 2023 02 08 12:46:27
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 16
