Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Yandex Mega Leak: An Insider Attack or Data Breach Attack?
published on 2023-02-01 12:27:59 UTC by Hagar MargolinContent:
Recently a new user on Breached forum created a thread named “yandex git sources”. The thread, which has quickly drawn a lot of attention, included 44.7 GB of compromised Git source code belonging to Russian tech giant Yandex. According to the post, the leaked code contains all of Yandex’s source code except for anti-spam rules.
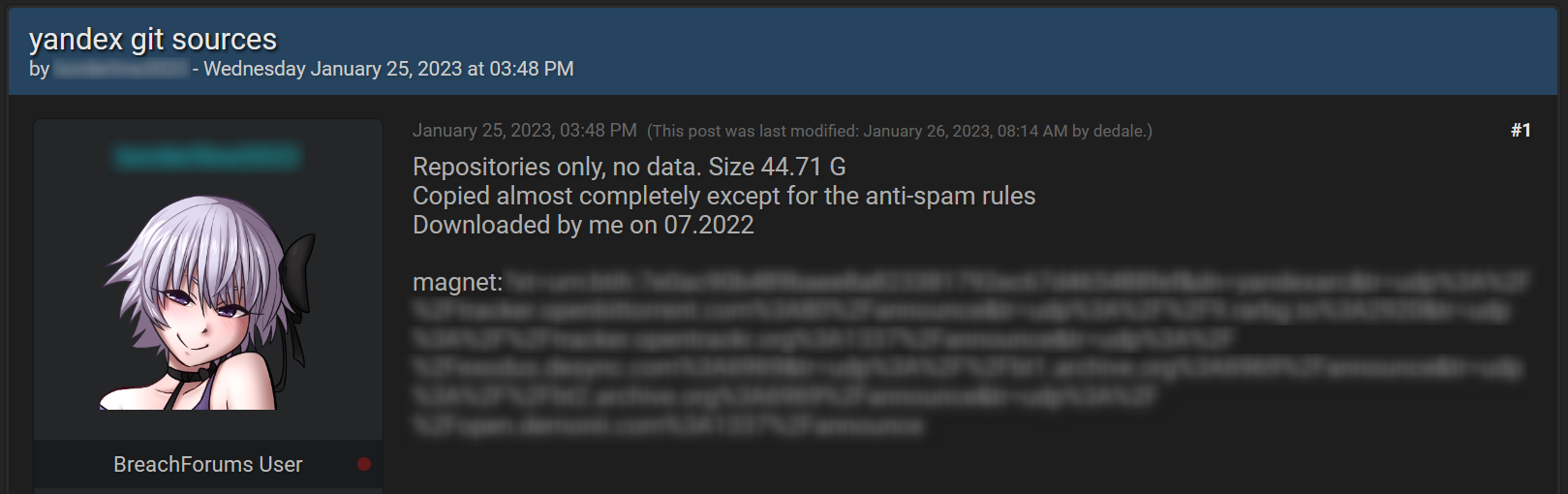
Following the release of their source code, Yandex made an announcement, claiming that a former employee was responsible for stealing and leaking the sensitive data, and denying it was the result of a breach of their systems.
The fact the information was leaked for free may support their claim but we decided to take a closer look into this case.
What is an insider threat?
Before we answer this question, let’s first discuss Insider threat. This term refers to people with lawful access to internal tools, information, or systems within an organization who intentionally abuse this access (by using legitimate credentials) for financial or personal gain. Malicious insiders are often current or former employees, contractors or business associates.
Just like other cybercriminals, malicious insiders also turn to the deep and dark web to discuss and share their activities. Like other cybercriminals, some insiders are motivated by financial gain, yet others seek revenge on their current or former employer, corporate espionage for a competitor, or nation-state espionage.
As mentioned before, since the compromised Yandex data was offered for free, the latter motivations sound more relevant. But we’ve decided to use our dark web data to see if we could find any indication to confirm or deny Yanedx’s claim.
Was the Yandex leak the result of an insider threat?
Since there isn’t clear-cut proof that Yandex’s leaked data was compromised by a former employee, we decided to check whether we could find potential cyber threats to Yandex on the dark web. Ones that could provide another alternative that their systems could have been breached.
We used Webz.io’s Cyber API to run a search and found hundreds of thousands of Yandex mentions in malicious discussions on these platforms, some of which can also lead to a data breach.
The mentions included:
- Hacking web services per request
- Leaked credentials (such as accounts, cookies, internal databases, combolists)
- Stolen digital fingerprints
- Financial fraud
- Browser hijacking
- Vulnerabilities
- Phishing as a service
Let’s take a look at a few examples of such posts we found on the dark web.
Example #1: Stolen digital fingerprint on Russian Market
An internal (employee) Yandex domain (“yandex-team.ru”) was traded on the dark web market “Russian Market”, as part of stolen digital fingerprints. The stolen information, which was obtained with Racoon malware, includes IP addresses, and browsing history, and can potentially include user browser data such as cookies, login info from visited websites, and other OS details.
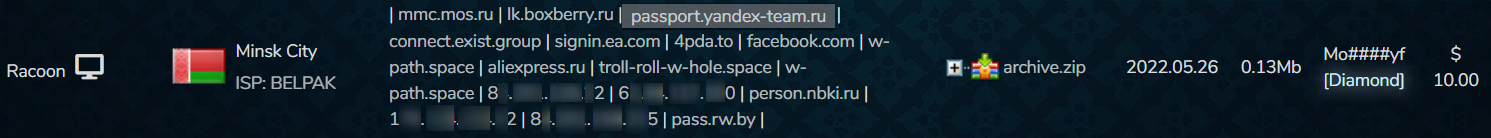
This kind of data, which we suspect belongs to a Yandex employee in Belarus in this specific case, could give threat actors malicious access to the company’s network if obtained.
Example #2: Leaked employee data
We used our DBD (Data Breach Detection) endpoint, to also check whether we could find any identified personal information (PII) belonging to Yandex employees and other executives that were leaked following previous data breaches.
We ran a search for the “yandex-team.ru” domain, which retrieved hundreds of different emails with that domain that were leaked in various breaches, along with other compromised fields such as usernames and passwords.
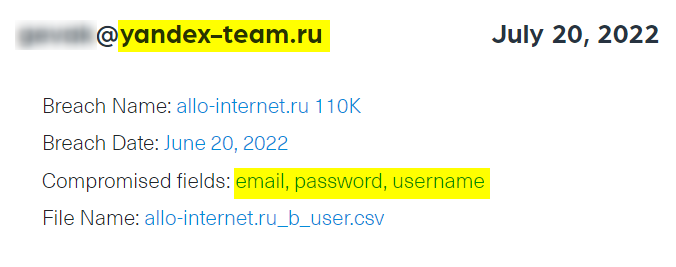
Using compromised credentials such as the ones we found can help threat actors to gain access to internal platforms on Yandex, based on the assumption that many people use the same password for multiple online accounts.
The next example shows an email address of a Yandex employee that was leaked along with the username and password. This was found in a breach of Allo Internet, a Russian e-commerce company, that was published a few months ago on BreachForums.
An insider threat or a breach?
It is hard to determine whether Yandex’s leak was the result of an insider threat or a breach given there is no definitive proof to back either of these causes. What we do know is that all organizations, including Yandex, need to monitor malicious discussions on the dark web to prevent future data leaks. The deep and dark web are crucial spaces to keep track of in order to protect sensitive organizational data and the organization’s reputation.
https://webz.io/dwp/yandex-mega-leak-an-insider-attack-or-data-breach-attack/
Published: 2023 02 01 12:27:59
Received: 2023 02 08 12:46:27
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 13
