Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.IoT: The Next Top Cyber Threat in 2023
published on 2023-01-11 12:59:56 UTC by Hagar MargolinContent:
What is IoT?
The Internet of Things (IoT) is a system of smart web-enabled connected devices that can communicate and exchange data with each other and with humans – and act accordingly. These devices can be smart appliances, sensors, and vehicles.
IoT devices can be split into two categories:
- The first category is tailored to the end user, focused on daily consumption, and is designed to be supported by simpler applications; for example – smart AC systems or security cameras which can be remotely controlled. These devices, however, can also be used by organizations.
- The second category includes devices used by the business sector – also known as Industrial IoT (IIoT) – specifically designed to achieve better business efficiency. IIoT devices can be found in different industries and include sensors, software, or robots, which support processes such as manufacturing, controlling, resources management, transportation, and more.
What IoT security threats are organizations facing today?
Since IoT devices have network connectivity, cybercriminals can take advantage of their inherent vulnerability in order to gain unauthorized access to the device but also to the entire network, which can pose a threat to many organizations. This malicious access enables threat actors to steal sensitive organizational data, control the attacked devices, harm them or even infect other devices in its network.
What IoT security threats can be found on the deep and dark web?
The growing popularity of IoT devices has also been accompanied by increased interest and mentions of IoT on the deep and dark web.
We used our dark web data to monitor the number of IoT mentions on the deep and dark web over the past six months. As you can see in the chart below, there has been an increase in the number of IoT mentions overall:
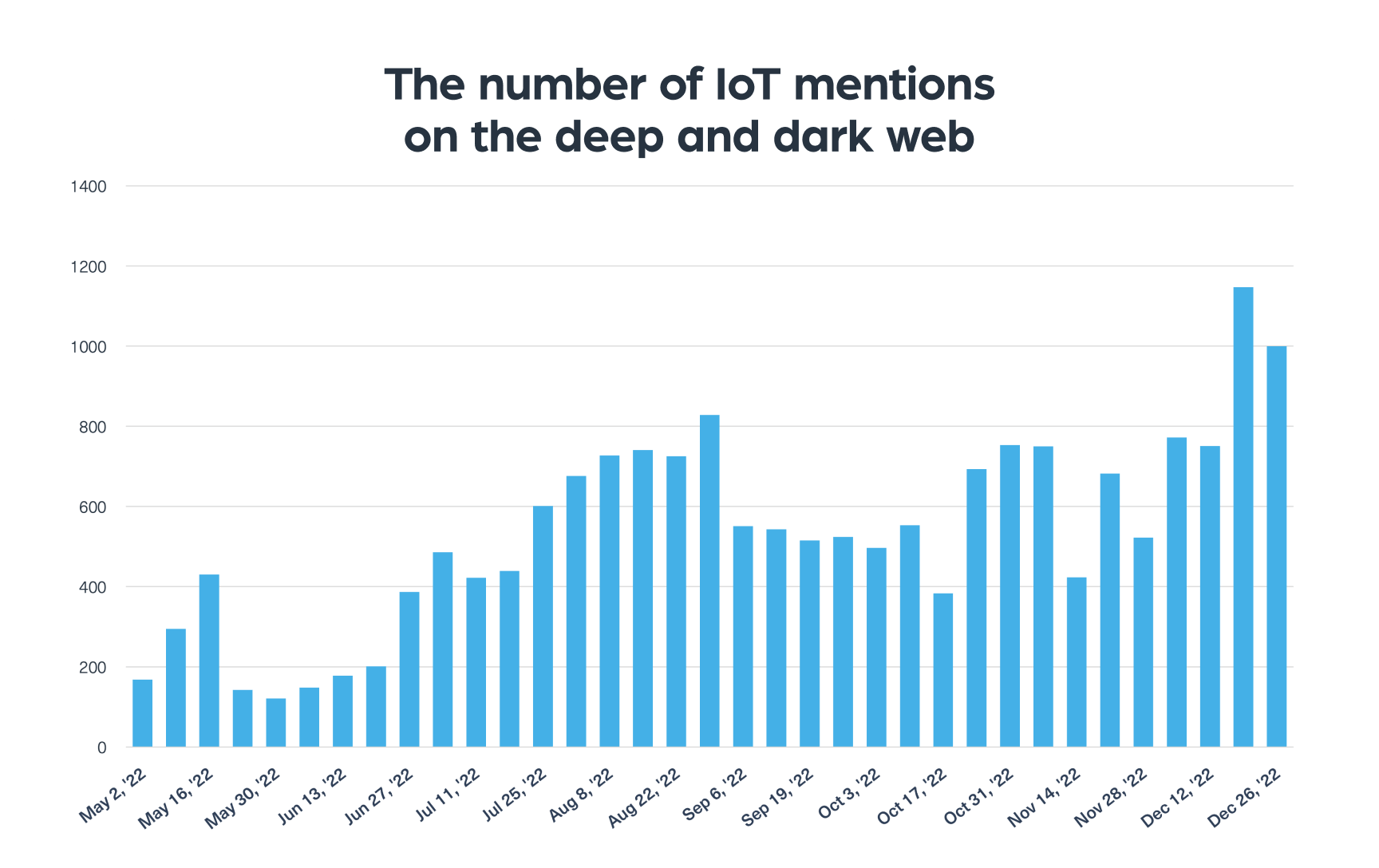
According to our data, discussions related to IoT can be mainly found in dark web forums, marketplaces, and chats. We can find on these platforms many cybercriminals who share exploits they could find on IoT devices and offer them for sale.
What are the most targeted industries by IoT threats?
We used our Cyber API to track the most targeted industries by IoT threats. To do that, we looked for the most mentioned industries on the dark web in the context of IoT attacks and security threats, which you can see in the chart below.
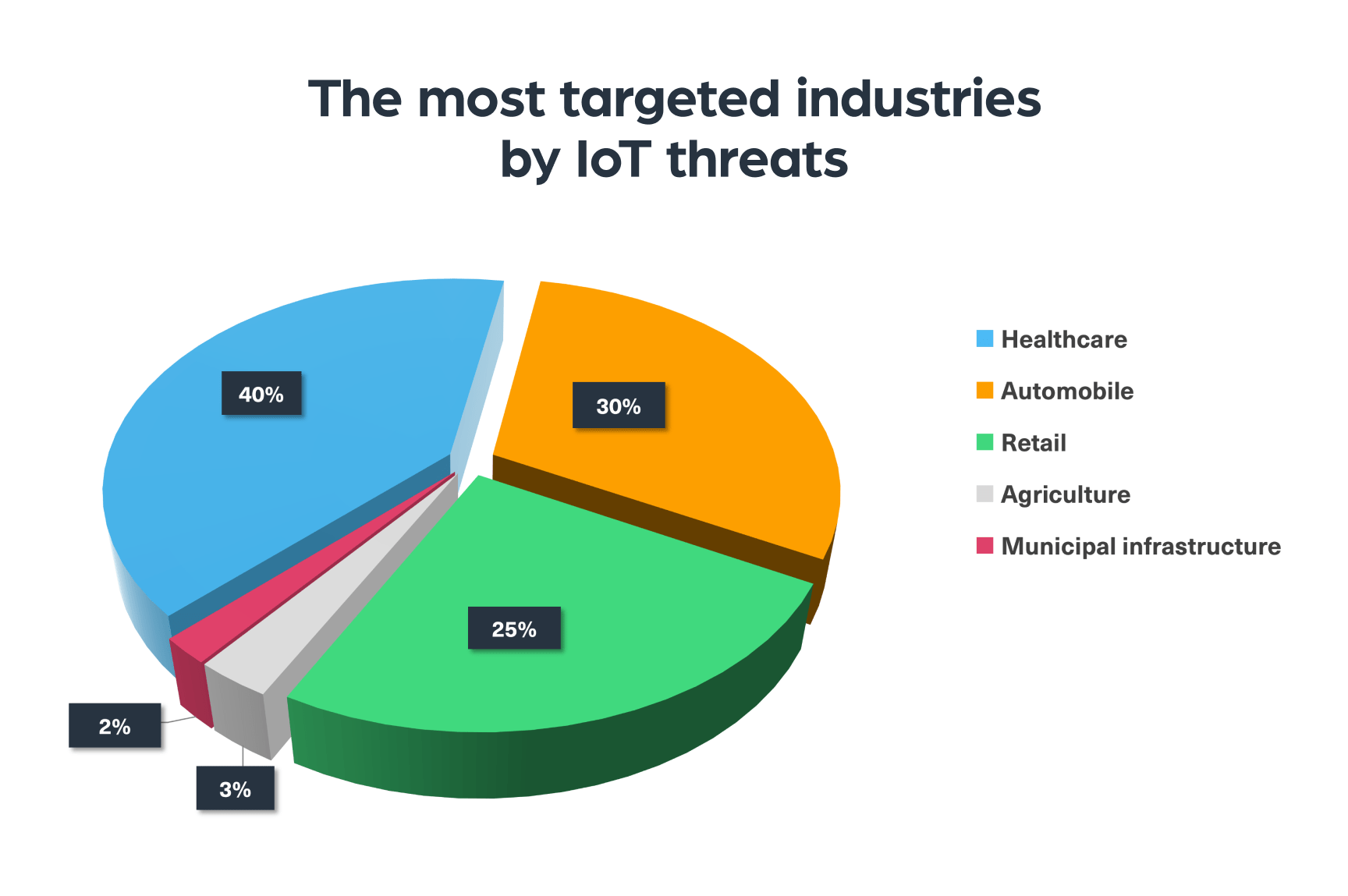
As you can see, the healthcare industry is leading with 40% of the total mentions being in the context of medical devices. They were followed by the automobile industry, whose popularity may increase as more consumers are buying electric cars. The third most mentioned industry in that context is retail, which is very susceptible to data breaches and financial theft, followed by the agricultural sector and municipal infrastructure (which was mentioned in the context of smart cities).
Now let’s take a look at real-life IoT threats from the dark web.
Example #1: IoT Zero-day exploit for sale
We found a recent, interesting example on BreachForums, a known hacking forum, in which a threat actor is offering for sale a zero-day exploit for Mercury-based PAC (programmable automation controller – IoT) devices.
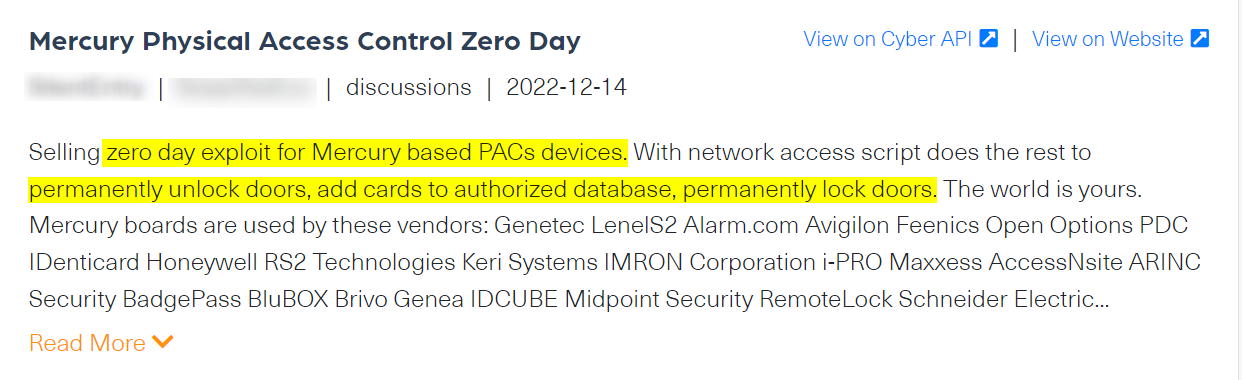
Mercury, a producer of OEM access control hardware, provides field-proven card readers and keypad interfaces, some of which are used for door configuration systems. Using that exploit, as mentioned in the post, an attacker is able to control doors that use these devices – and can open them remotely, permanently lock them and even add external people to the door’s authorization system.
This exploit, which may be risky for other Mercury’s IoT devices (such as controllers, additional readers, and other accessories they produce), can pose a threat to any organization using them. The risk is even more critical for organizations with sensitive information such as government agencies, security organizations, law enforcement agencies, infrastructure companies, etc.
Example #2: Hacktivists publish Israeli CCTV footage
The second example covers a different type of IoT threat – posed by hacktivists. The main purpose of the posts published by hacktivists is to promote their agenda, damage their victim, and spread fear.
In the following example, you can see a post published by a hacking group, named Moses staff, showing live footage from CCTV cameras from different cities in Israel.
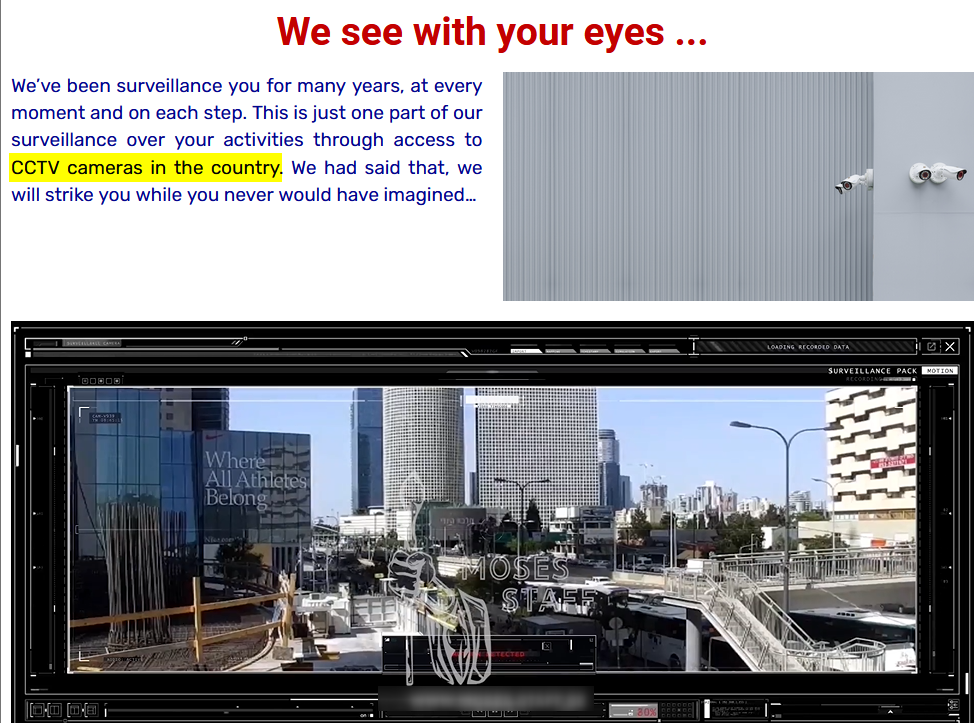
In one part of the video they even showed real-time footage from a street camera that captured a terrorist attack at that time. Such an act has a big impact on the deterrence and fear hacktivist groups, like the one above, try to create.
What are the challenges faced by industries using IoT?
When it comes to cybersecurity, many companies tend to first protect the internet-connected systems they are more familiar with. For example, they usually implement security solutions for networks, cloud-based systems, and applications. But that means that a lot of IoT devices, like sensors and software that are used by many organizations from different industries, are being neglected. The lack of awareness around those devices also means that the security measures IoT devices manufacturers use are not always enough to mitigate or protect against these threats.
This is why, alongside security solutions that may not always be sufficient, there is a growing need for timely monitoring of the networks used by cybercriminals to identify any IoT security threat.
Cyber intelligence organizations are increasingly using deep and dark web data, such as Webz.io’s Cyber API, in order to:
- Help organizations identify threats and attacks directed against them through IoT devices they own.
- Provide supply chain risk protection for cases where an IoT security threat may trigger an attack on any organization using the relevant IoT device.
- Generate ongoing threat intelligence to manufacturers of IoT devices to discover any vulnerabilities related to their IoT products.
IoT threats in 2023: What to expect?
As IoT technology helps organizations and enterprises to optimize their ongoing operations, the use of IoT devices isn’t going to decrease in the foreseeable future.
It also won’t be long until every organization, down to the individual user, understands the potential of IoT devices. This is why we expect the number of IoT attacks and their level of sophistication to only grow over the coming year – and beyond.
Take for example the following hacktivist post about an attack against an AC system in Israel:
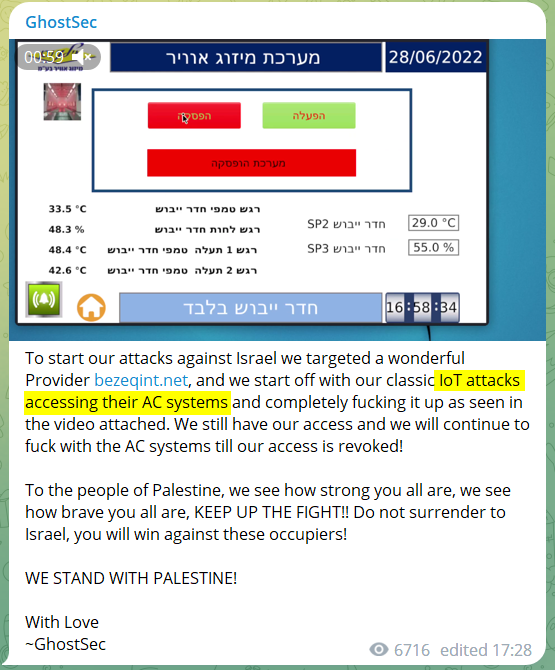
These sort of attacks prove that IoT attacks can target anyone – companies and individuals alike.
https://webz.io/dwp/iot-the-next-top-cyber-threat-in-2023/
Published: 2023 01 11 12:59:56
Received: 2023 02 08 12:46:27
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 20
