Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.The Lifecycle of Data Leaks on the Deep and Dark Web
published on 2022-11-02 09:50:09 UTC by Hagar MargolinContent:
Data breaches have become one of the most prevalent and damaging cybersecurity threats for companies and organizations around the world. A recent survey has found that global data breach attacks increased by 28% in the third quarter of 2022 compared to the same period in 2021. The average weekly attacks per organization worldwide reached over 1,130.
Only in the past year, we have seen major breaches targeting all industries including attacks against Toyota, Panasonic, Moncler, and Flagstar Bank.
Data breach: Risks and consequences
There are different risks and consequences that a data breach can lead to, depending on the type of data and scale. Here are a few examples:
- Account takeover (ATO) – The leak provides hackers information that allows threat actors to abuse accounts for malicious activities.
- Repeated cyberattacks – When credentials or any sensitive information is leaked, threat actors can use it to hack into the system again from a different penetration point, leading to repeated cyberattacks and at times further mass leaks.
- Financial loss – The leaked credentials can be used to withdraw money from the accounts of the people whose credentials were exposed.
- Reputational damage – A massive breach can harm customer loyalty and deter potential customers. Major breaches can even cause companies to go out of business due to the reputational damage they may suffer.
Where are the different stages of leaked data on the deep and dark web?
Most of the stolen data is leaked and traded on the deep and dark web. These are the main platforms cybercriminals use for communication and trade with other cybercriminals. From a deep familiarity with these platforms, we have been noticing a similar cycle for many leaks:
Stage #1: Leaks for sale
The more valuable the stolen data is the more likely it is to first be sold on the deep and dark web. This means large-scale breaches, databases that contain highly sensitive information, or data that belongs to large or well-known organizations or government agencies are the main types of data leaks that are offered for sale. The more valuable the data is, the higher its pricing will go.
Where is leaked data traded on the deep and dark web?
Cybercriminals who seek to sell the data they stole will typically post the relevant details about the data they breached on a hacking forum or in a large, relevant chatroom. We found that high-value leaks are likely to be published for sale at least in one of the following hacking forums: Breached Forum, XSS, and Exploit.
What does a dark web post with leaked data look like?
Each post will include different details but the majority of them will include the following:
- The name/domain of the compromised organization
- The company’s description
- The number of records
- Date of breach
- The available compromised fields
- PoC (A sample of the leaked data or relevant screenshots which can prove the vendor is reliable)
- The demanded price for the leak
- Contact details of the seller such as email address or personal user details in chats (in order to have a personal conversation while keeping it safe and anonymous)
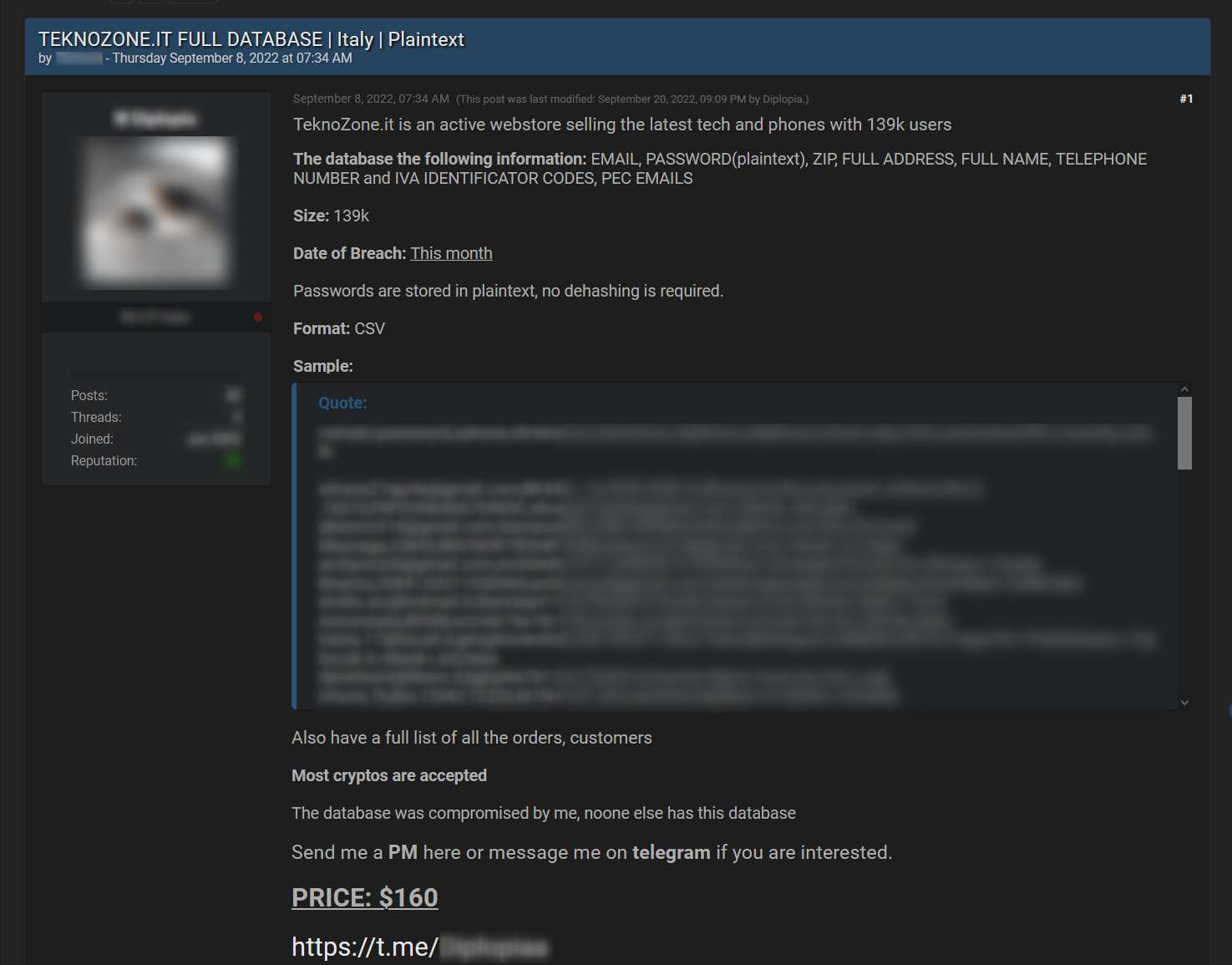
Example of a leak for sale
The next picture is of a post published by a threat actor who is offering a database for sale on a known dark web hacking forum Breached. In his post, the threat actor is providing all relevant details such as the domain that was breached, a description of the leak, the number of records, the breach date, the format of the document he is offering, a sample with a few compromised records as proof, the price, and his Telegram account to help interested parties get in touch with him.
Stage #2: Leaked data for free
When leaked data is sold, there is a high probability that it will end up being available for free download on the deep and dark web. The reason for this is that the leaked data loses some of its value over time, and starts circulating between different dark web users.
It is important to note that some leaked data is free to download from the beginning, or traded by using site credits, which are used for trading on the site. This usually happens in cases where a hacker or a group of hackers are trying to build their reputation or the reputation of the dark web site they maintain. In other cases, data is available for free when ransomware groups fail to negotiate a ransom payment and as a result, publish the data to everyone a few days or weeks later.
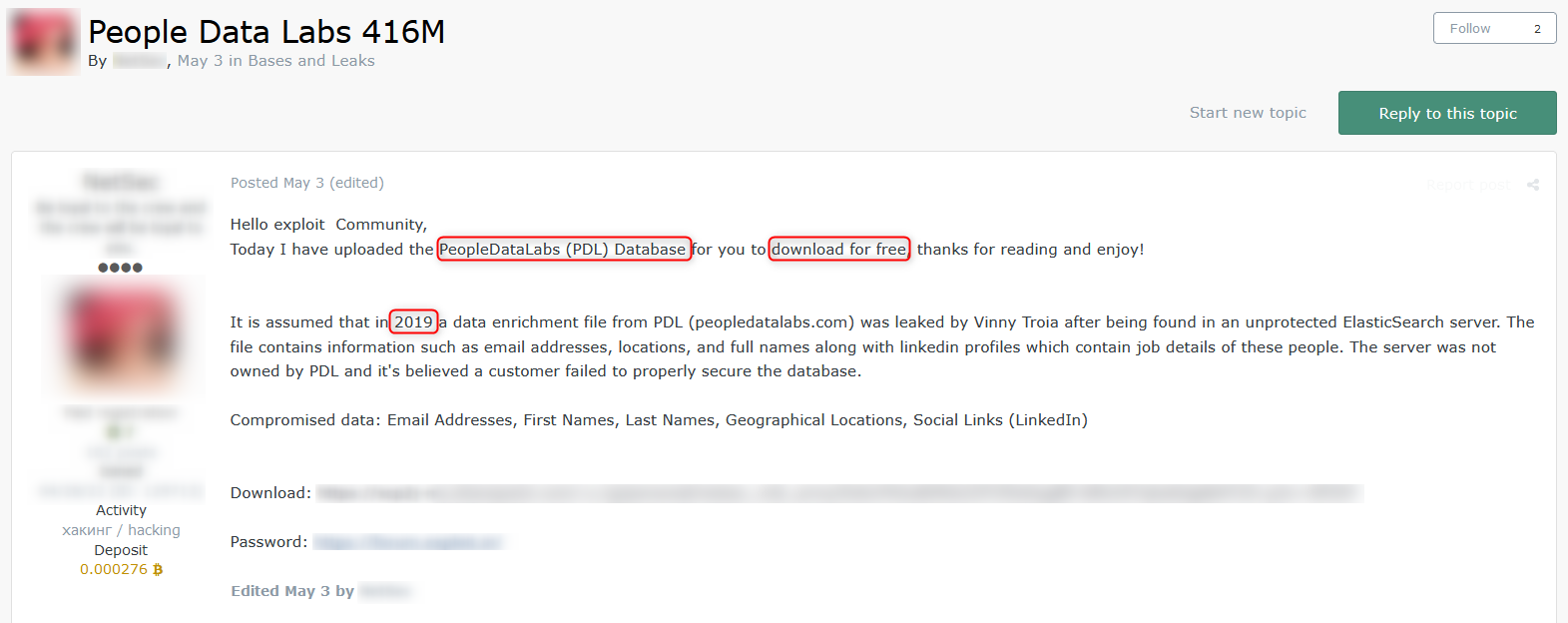
Example of free leaked data
In the following post, a threat actor is offering an old database for free download on Exploit.
Stage #3: Free combo lists
Once a leak is published for free, all credentials of the compromised accounts can be collected alongside many other leaked entities under a new list that is known as a combo list or combo. A combo list refers to a file containing a list of many usernames, email addresses, and passwords that were collected from many different leaks that had already been published. These types of leaks are considered less valuable than others and are also provided for free.
Combo lists are used by application programs and bots to conduct brute-force attacks, gaining unauthorized access to systems by trial and error. By using combo lists, threat actors have a greater chance of success in this type of attack as they provide a massive collection of compromised accounts and fact that many people use the same username or password across various sites.
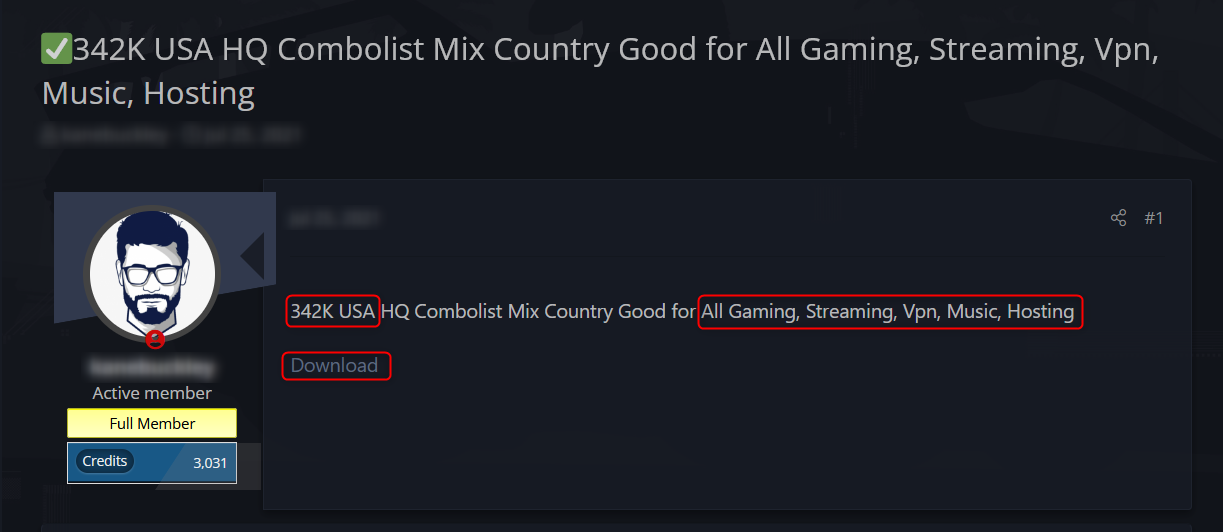
Example of a post offering a free combo list
In the following example, you can see a post where a threat actor is offering a free combo list ready for download. This combo list consists of compromised records from the U.S., collected from various breaches that were previously shared. The post also mentions the industries the compromised data was collected from, including the gaming and streaming industries.
How can monitoring the dark web help prevent data breaches?
With the number of data breaches continuing to increase, targeting enterprises and organizations across the globe, the need for timely and quality intelligence has become critical for the success of any business. Companies have to be alerted in real-time to any leaked and compromised data that appears on the deep and dark web, whether it’s compromised employee accounts, internal documents, or leaked databases. Monitoring these types of early indicators is key to mitigating and even preventing future potential risks, some of which are mentioned above. These alerts are essential to help companies take necessary actions in real time.
Webz.io’s Cyber API, which provides structured and enriched deep and dark web data, helps organizations to track any high-risk signal of a relevant data breach. Webz.io’s Data Breach Detection API helps complete the intelligence picture with a repository of compromised credentials that were leaked, such as emails, passwords, usernames, credit card numbers, phone numbers, passport numbers, and SSNs. Proactive monitoring is the best way to prevent the next data breach.
https://webz.io/dwp/the-lifecycle-of-data-leaks-on-the-deep-and-dark-web/
Published: 2022 11 02 09:50:09
Received: 2023 02 08 12:46:27
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 18
