Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.The Top Industries Most at Risk for Data Leak in 2022
published on 2022-09-21 13:31:11 UTC by Liran SoraniContent:
Data loss has a lasting effect on the future of organizations. In the aftermath of an attack, organizations not only lose data that will need to be changed or retrieved but often they lose money and customers. Most organizations will need months and sometimes years to repair the reputational damage they suffered from such an attack.
In this post, we use our deep and dark web data to discover the top industries that were at risk of cyberattacks in 2022. We will also discuss the threat patterns, including the tools and methods the cybercriminals used, their main motives, and the different types of compromised data.
What are the top industries at the highest risk for data loss in 2022?
To discover the industries most at risk of data loss, we research the deep and dark web and trace the top 100 companies mentioned in the context of data breach activity. We then sorted them according to industry, as seen in the chart below:
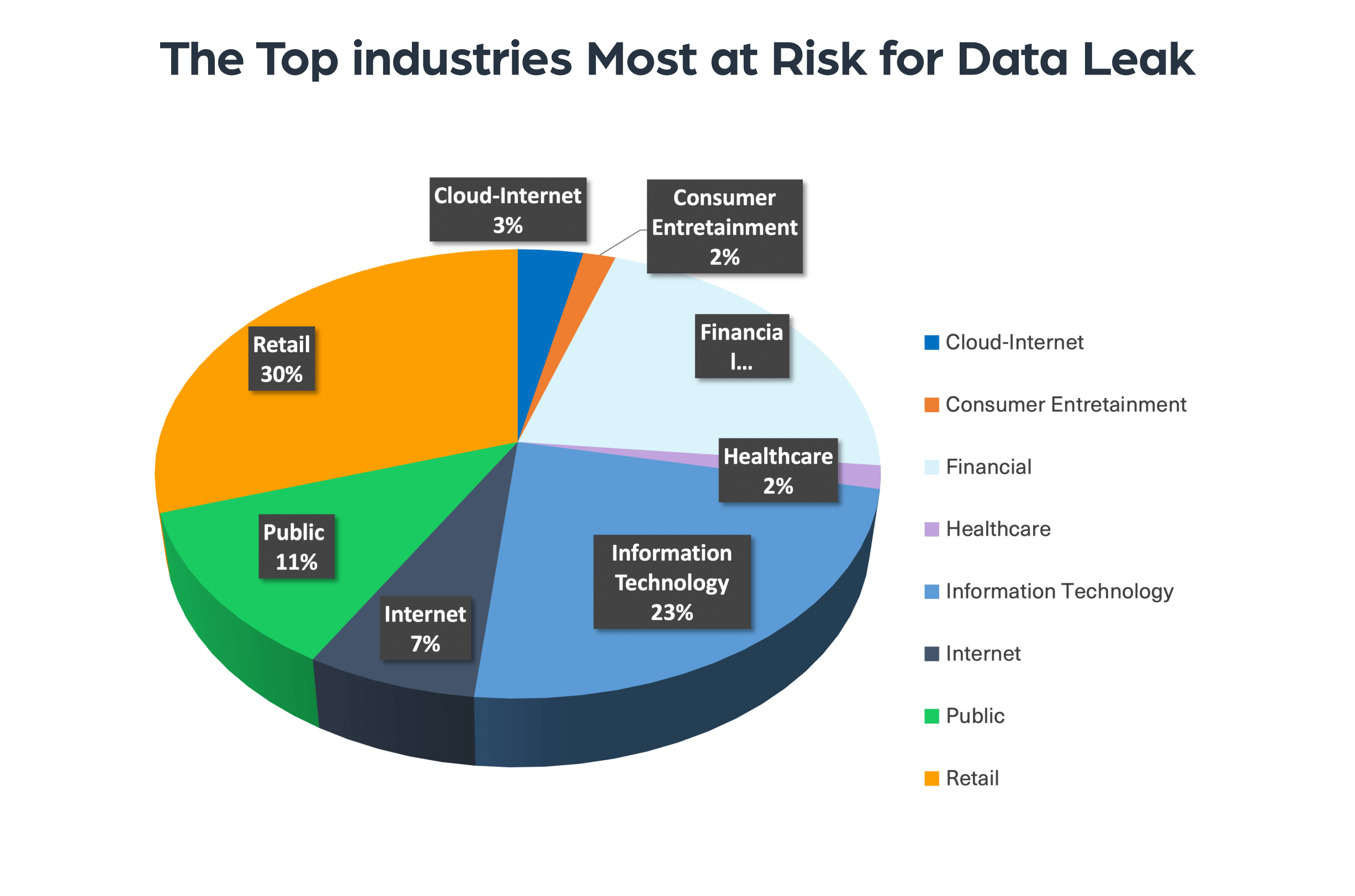
The industries that have been most commonly mentioned in the context of data breaches on the deep and dark web are:
- Retail
- Information Technology
- Financial
- Public organizations
- Telecommunications
Let’s take a closer look at two of the top industries.
Retail
Online retail has always suffered from cyberattacks. The main reasons for this are that retail is a leading sector of online transactions, they have many potential attack surfaces (cloud, backups, online services, and more), and they involve many admin-level entry points that can be abused to attack and extract sensitive information.
The biggest cause of data breaches in the retail industry is low-security standards. Retailers rely on third-party organizations to provide security services, and some have few if any security measures at all.
Among the most common attack methods, you can find phishing sites. There are also different types of DDoS attacks and some Ransomware attacks, which are used as part of more sophisticated attack that is customized per organization after a long process of intelligence-gathering by the threat actor.
In the following example you can see Disney accounts being sold after suffering a breach, which was carried out by using some of the techniques mentioned above:
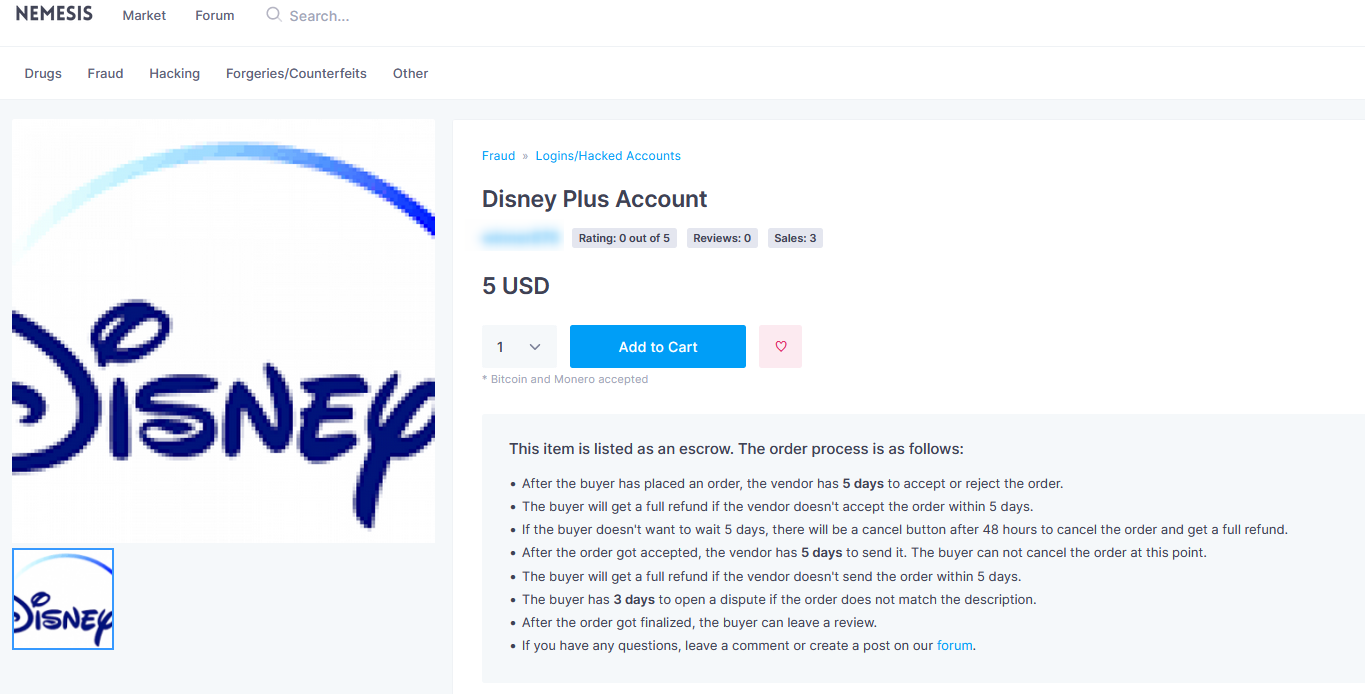
Such an account can be used to transfer money, in case it’s a gift card for example. This makes the problem even worse as additional personal details can leak and lead to further attacks. There are tens of thousands of such accounts traded on the dark web.
Some data breaches that affect department store chains result in leaking personal online accounts, credit card numbers (with expiration dates), and passwords.
In summary
- Top threat actor motive: Financial, in some cases industrial espionage.
- Data compromised: Payment details, personal details.
- Top threat methods: Phishing, social engineering, ransomware.
Information technology
The COVID-19 pandemic led to the rise of hybrid work and online work life. As a result, online social accounts have become a critical tool for many organizations and individuals.
Information technology covers different social networks and social media platforms including solutions that help businesses to store, manipulate, and analyze data.
In recent years there has been an increase in the number of attacks against this industry, especially in the form of supply chain attacks, allowing access to data that belongs to end customers.
The next example shows a threat actor who is looking to buy existing Microsoft Azure or Office 365 accounts.
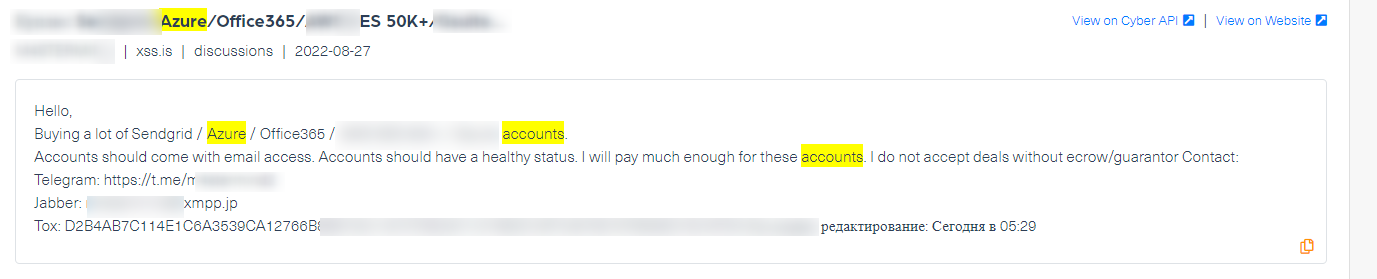
This threat actor is willing to pay a high price for existing accounts that will help him build either a botnet or a phishing scam, including exploiting sensitive information stored in the accounts.
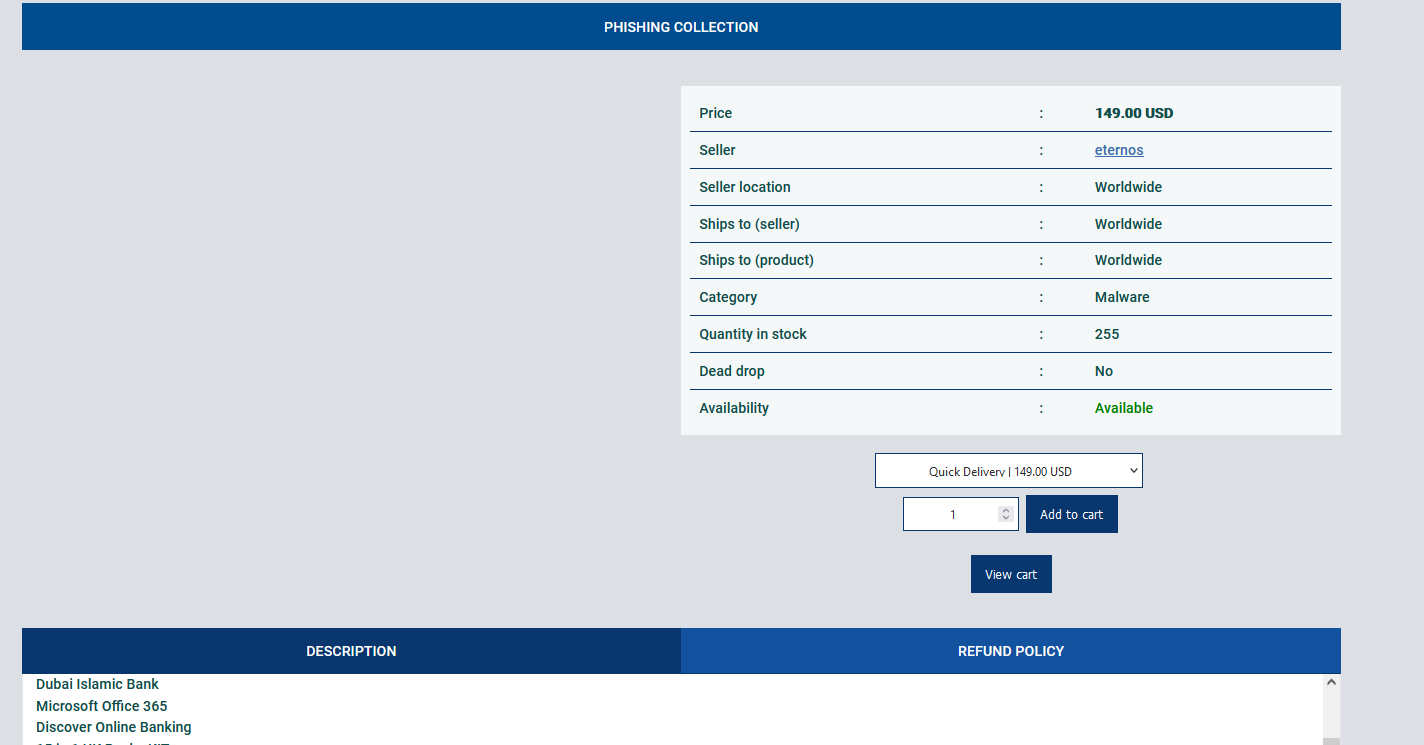
Below you can see another example of a phishing site designed to steal Microsoft 365 accounts and then use the accounts for fraudulent activities, or for stealing sensitive information.
In summary
- Top threat actor motive: Financial, in some cases – industrial espionage.
- Data Compromised: Payment, anti-government (disinformation, and inciting trends)
- Top threat methods: Phishing, ransomware, targeting breached accounts
As data breaches continue to target enterprises and organizations around the world, the need for timely and quality intelligence has become critical for the success of any business.
Webz.io works with some of the world’s leading cyber intelligence and event monitoring companies and provides them with structured and enriched deep and dark web data to help track IOCs and high-risk signals to protect organizations and individuals.
https://webz.io/dwp/the-top-industries-most-at-risk-for-data-leak-in-2022/
Published: 2022 09 21 13:31:11
Received: 2023 02 08 12:46:27
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 13
