Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.The Top Ransomware Trends on the Dark Web in 2022
published on 2022-12-07 08:43:56 UTC by Hagar MargolinContent:
Over the past years, ransomware attacks have been on the rise across the world. As we predicted in our 2021 report, this upward trend continued into most of 2022.
Because the deep and dark web is often used by ransomware gangs to plan, communicate, and leak stolen information, we used our Webz.io Cyber API, to track ransomware gangs and new ransomware trends. The findings, which you will soon see, can shed light on the activity of ransomware gangs on these dark corners of the web in 2022 – and give a glimpse into what we are expected to see in 2023.
How many ransomware groups operate a deep or dark web platform in 2022?
While the media attention to ransomware attacks has definitely increased in 2022, we wanted to examine the deep and dark web to see how many ransomware groups operate in this environment.
At the time of writing these lines, we have seen that 30 new ransomware groups opened a channel on the deep or dark web, out of an estimated total of 98 new ransomware groups that have been created this year. This means that 30% of the new ransomware groups that started operating this year run their own site on deep and dark web platforms.
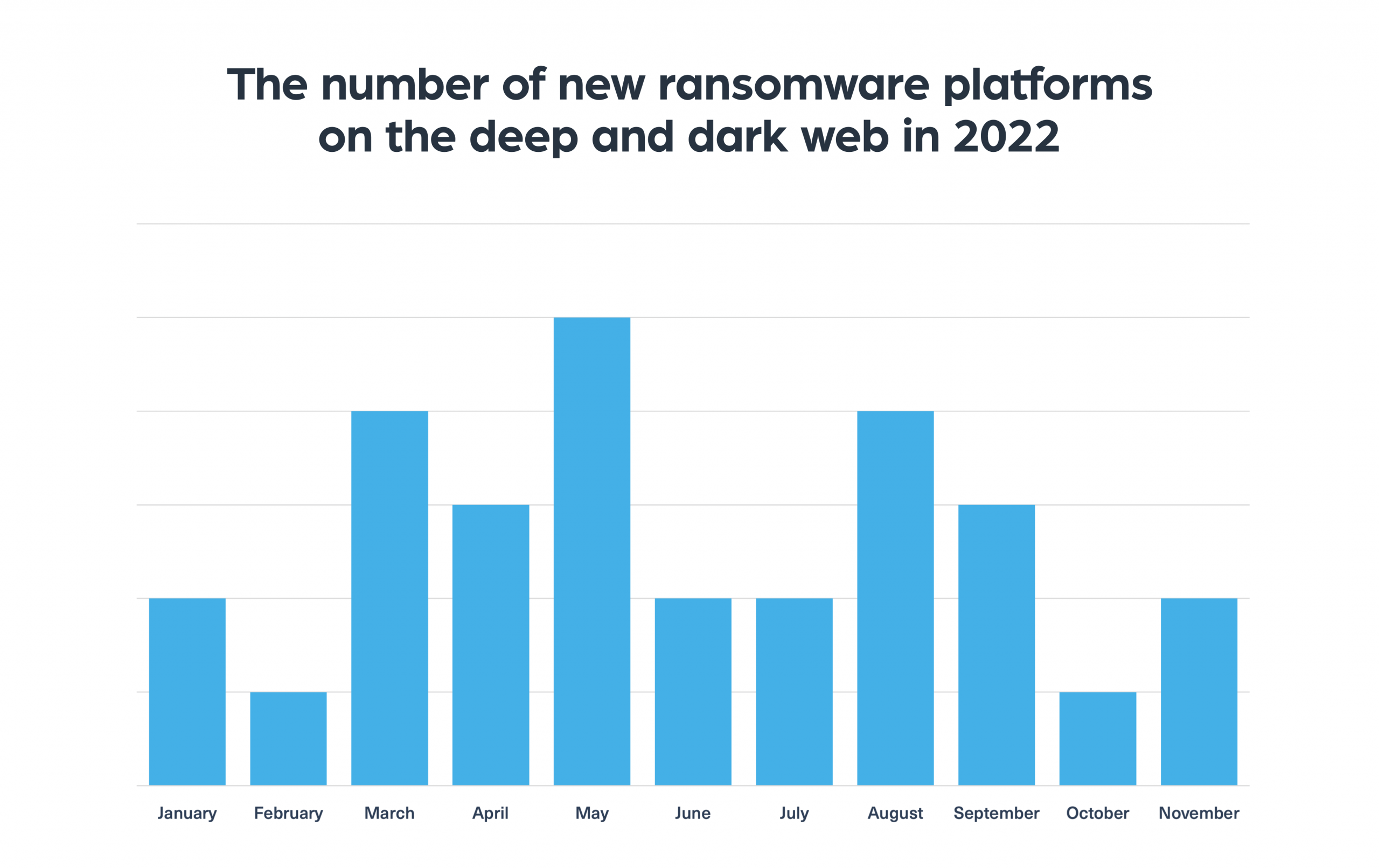
Out of the 30 new dark web channels, 11 are already down, which means that 36% of the new ransomware groups were unable to maintain their dark web platform for long.
When examining the number of new ransomware groups on the dark web in 2022 in comparison to 2021, we see a decrease of 44%, going down from 173 groups in 2021 to only 98 groups in 2022. This is likely to be the result of a wave of crackdowns on ransomware groups launched by law enforcement forces around the world. However, alongside the increase in the number of arrests, we continue to see new ransomware groups opening and stepping into the gaps left behind. This makes monitoring the deep and dark web as if not more important to keep up with the evolving ransomware landscape.
The ransomware landscape on the deep and dark web in 2022
What have we learned about ransomware groups and activities in 2022? Here are some key insights.
Who are the top 5 most active ransomware groups in 2022?
- Lockbit (like in 2021)
- Revil (although it has shut down and its members were arrested this year, some suspect the remaining members may relaunch under a new group called “BlogXX”)
- SAlphv (BlackCat)
- Conti (the group has ceased to operate after several crises, such as the leak of their source code and a DDoS attack after they supported Russia in the war against Ukraine)
- Vice Society
The top deep and dark web platforms used by ransomware groups in 2022
- Tor Network – Most ransomware groups active on the dark web maintain a Tor site where they publicize their targets, including their internal information.
- Telegram – Maintaining Telegram channels or closed groups has become popular already in 2021 and has continued into this year. It is used by ransomware gangs to distribute news and messages, as well as to share information about their negotiation with victims.
- Hacking forums – Ransomware gangs often have representatives in hacking forums to remain active within the hacking community. There, they usually monitor different cyber events, exchange information, and alert to anything that could relate to them.
You can read more about the underworld of cybercriminal groups here.
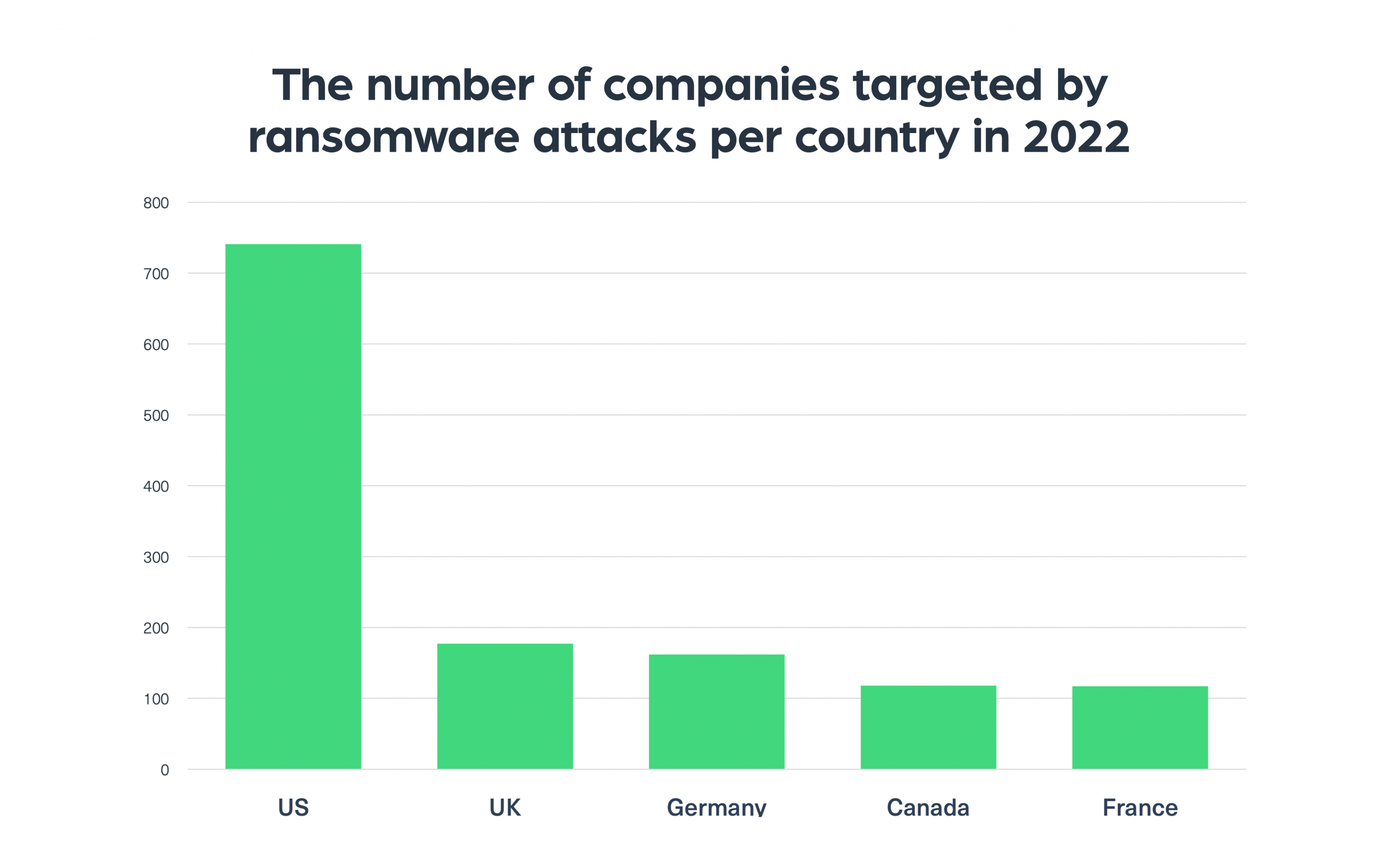
What are the most targeted countries by ransomware groups?
Similarly to 2021, the United States remains the leading target of ransomware attacks. The second most targeted country, although with a huge gap from the first place, is the UK, followed by Germany, Canada, and then France.
In the chart below you can see the trend over the past year, which we created by using our data to determine the number of companies targeted by ransomware attacks – per country:
The most targeted industries by ransomware groups
One of the most alarming statistics of the year we discovered when monitoring the dark web was the rise in the number of attacks against some industries.
The energy and healthcare industries are the most targeted industries this year by ransomware gangs. This indicates a real shift of ransomware groups that are now gearing their attacks against the public sector and not just private companies.
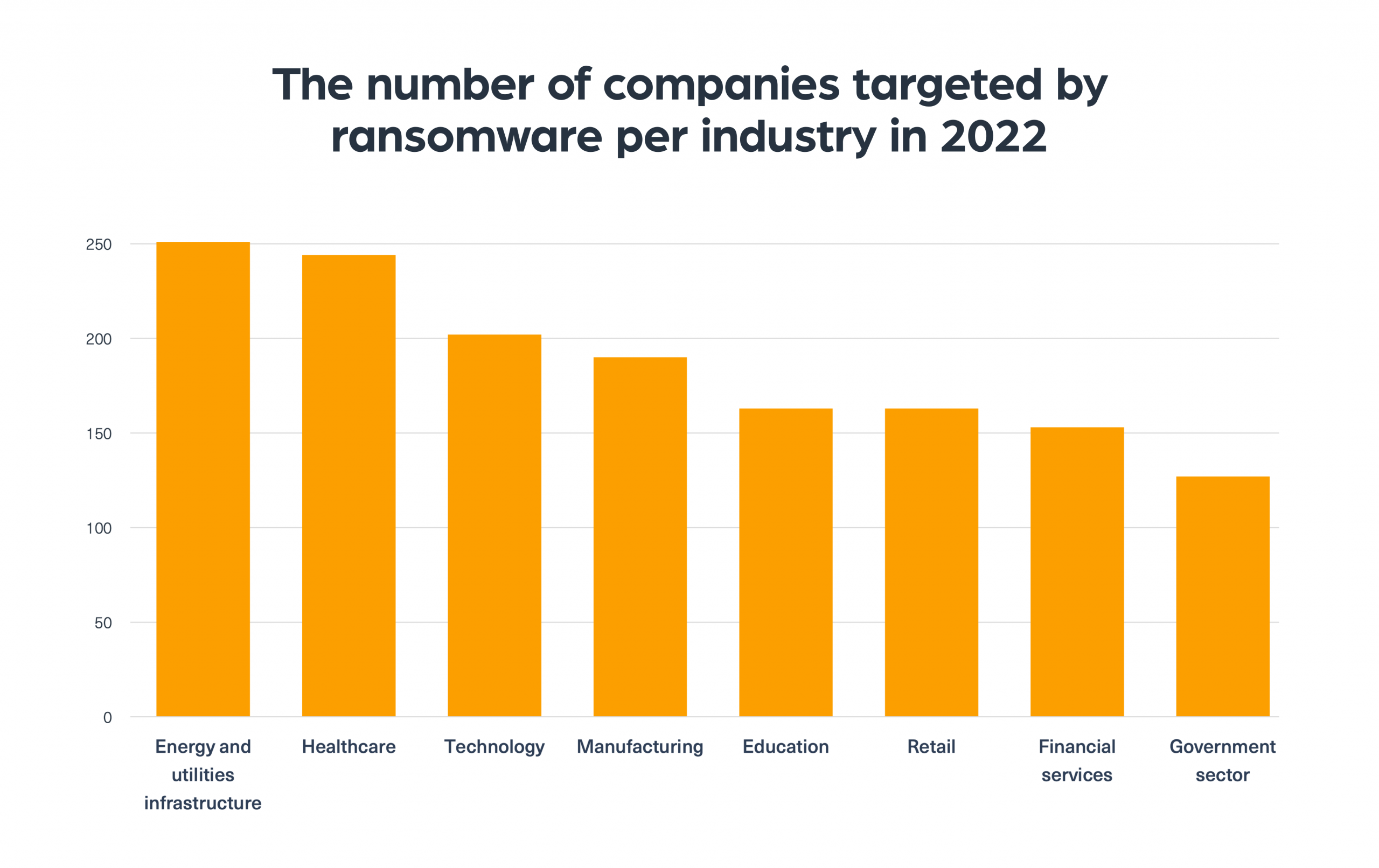
One explanation for this shift, which we discussed in a previous Dark Web Pulse item, was that ransomware groups are keener to target these industries because they pose a higher risk, as such attacks can affect large populations and daily life, which puts more public pressure to give in to their high demands.
Ransomware as an industry
Over the past years, ransomware has developed into a new, professional industry, with a market, stakeholders, and processes similar to other legitimate industries. This evolution is something we have witnessed on the deep and dark web.
It starts from the group’s need to maintain a public channel, like any self-respecting brand, in order to gain recognition and reputation. Similarly to other brands, reputation plays an important role as it increases the chances the group will receive the ransom it demands from its victims. Because the more reliable the group is, the more likely it is that the victim will be convinced the ransom payment will actually allow them to regain access to their encrypted files.
For ransomware groups that also operate out of a political agenda or activism, which we have seen happening this past year since the war between Russia and Ukraine broke, the reputation helps them to promote their agenda more widely.
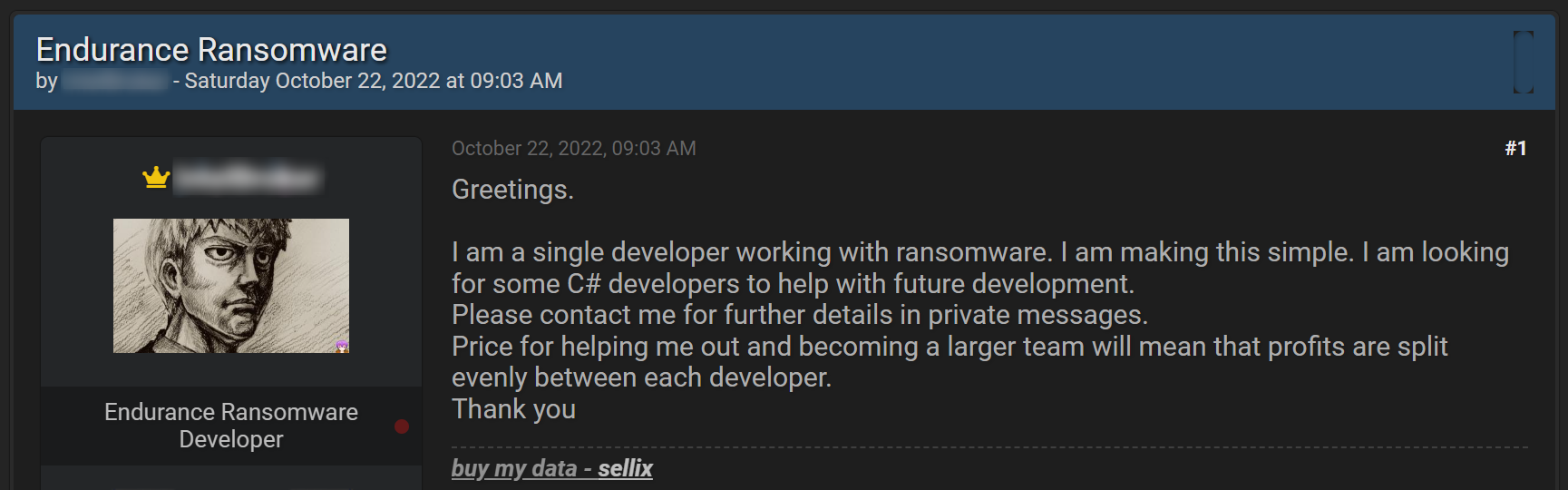
Like other organizations, ransomware groups now have different roles filled by different people; one is responsible for the development of the ransomware and for executing the attack. A different one is responsible for negotiations with the victims, while someone else acts as a representative in the various dark web forums, etc. With the need for these different roles, ransomware groups are constantly recruiting new people, using campaigns that would not embarrass a respectful HR team.
In the next example, taken from Breached, a popular dark web hacking forum, you can see a developer working for a ransomware group, looking to recruit someone to his team:
Another sign of the level of professionalism that is developed by ransomware groups is their malware innovation. Ransomware groups are continuously developing their own tool kit, just like legitimate software companies, in order to develop cross-platform malware so they can be more adaptive, effective, and easy to use.
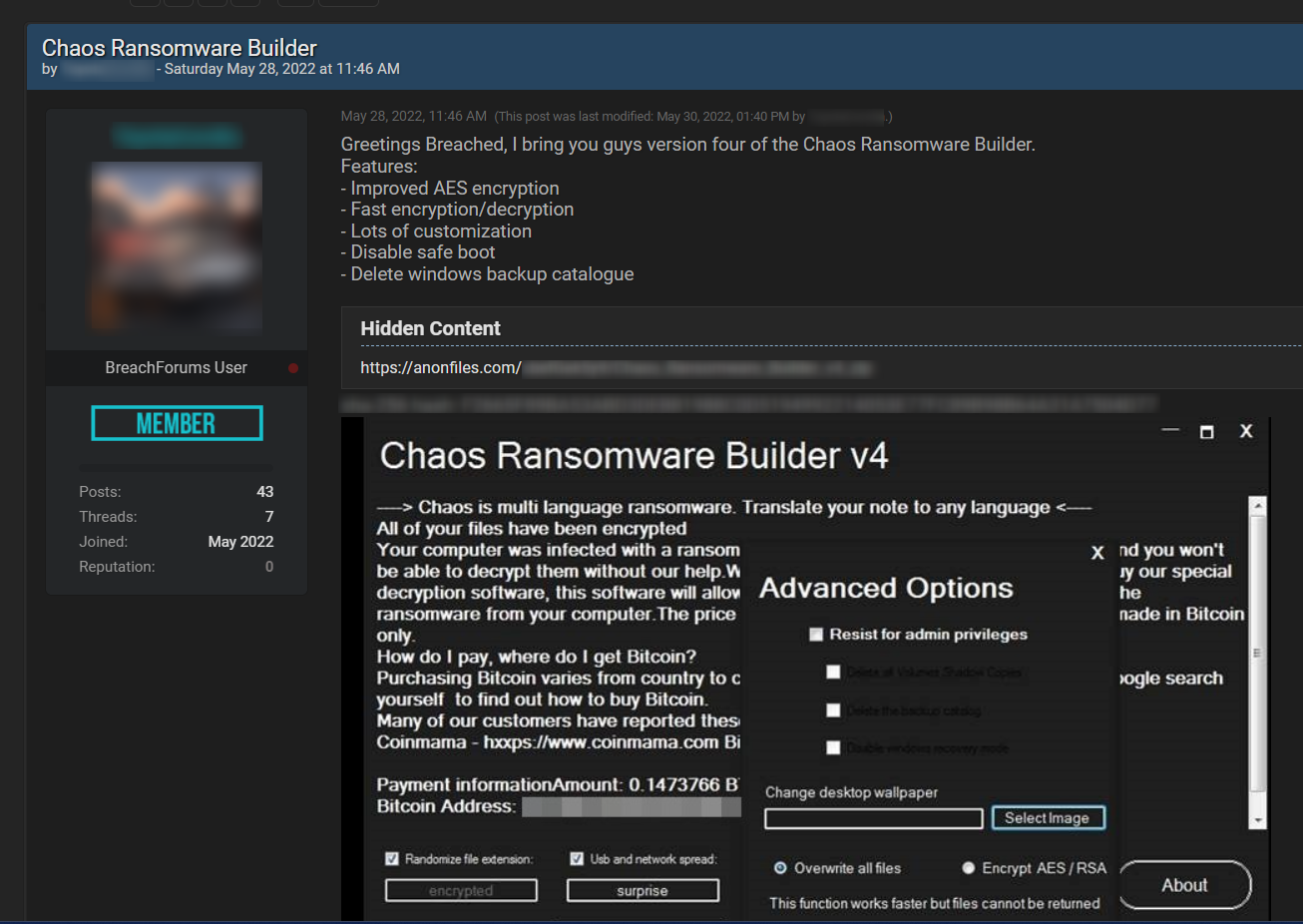
A new, small, market has developed where people trade custom ransomware, on-demand ransomware services, as part of the RaaS (Ransomware as a service) model, or offer ransomware builders for home-made developed trojans that are very similar to the functionality and capabilities of today’s ransomware. In the next image you can find an example of that, where a threat actor is offering a customizable ransomware builder, named Chaos, on Breached, a dark web hacking forum:
Where will ransomware be in 2023?
Looking ahead, 2023 is not likely to see a significant decrease in the number of ransomware attacks. Another trend that could take off is individuals, without previous experience in ransomware attacks, who will build their own destructive trojans (which are very similar to the traditional ransomware) in order to carry out cyberattacks. They’re more likely to be able to do so because many tools are available today, some of them even for free, on the dark web. Many businesses today, regardless of their size, do not have the awareness and capability to monitor these attacks.
Another important trend that is likely to continue and even increase in 2023 is the activity of ransomware groups that are not only financially motivated but also motivated by activism and political and extremist agenda.
As the ransomware industry continues to evolve, ransomware attacks are becoming more sophisticated, frequent, and damaging. 2022 has seen more companies from different industries affected by ransomware attacks, a trend we are very likely to see continue into 2023. For these reasons, many companies are investing more time and budgets into gathering intelligence, which helps detect threats ahead of time.
With the deep and dark web serving as the main space for ransomware groups to operate, any proactive intelligence gathering in 2023 will include timely data from these parts of the web. Already today, leading cyber threat intelligence companies use Webz.io’s Cyber API to detect this critical data. We expect this to expand in 2023, with more companies needing these powerful tools to monitor ransomware discussions, sites belonging to ransomware groups, and emerging new tools and trends, which provide the in-depth intelligence every company needs today.
https://webz.io/dwp/the-top-ransomware-trends-on-the-dark-web-in-2022/
Published: 2022 12 07 08:43:56
Received: 2023 02 08 12:46:28
Feed: Webz.io Dark Web Posts Ransomware
Source: Webz.io Dark Web Posts
Category: News
Topic: Ransomware
Views: 22
