Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.From Dark Web Sites To Telegram Groups: Where Do Cybercriminals Operate?
published on 2022-08-10 11:51:24 UTC by Hagar MargolinContent:
After traditional dark web forums and markets, instant messaging platforms, like Telegram, are increasingly becoming a popular method of communication among cybercriminals. Over time, threat actors have found IM apps a convenient tool for communicating, exchanging information and sharing malicious files with other users.
Similarly to the dark web, a variety of crimes take place on these chatting apps due to the unique structure of instant communication and its enhanced capabilities. Cybercriminals, for example, use instant messaging apps to conduct illegal trade and money laundering. They also use them for hacking discussions and as a space to spread compromised data.
Another example of the audience that uses them for illicit activities are extremist groups who use the chatting application in order to spread their ideologies and propaganda, and urge others to take action.
Why do cybercriminals use instant messaging?
There are various reasons for cybercriminals to use these apps, but let’s take a look at the top five factors at play:
- End-to-end encryption – there are different instant messaging apps which offer end-to-end encryption services, which is a secure method that allows cybercriminals to remain anonymous (as they’re already used to communicating on private platforms on the dark web).
- Unindexed – standard search engines do not index IM group messages, making it fairly difficult for law enforcement authorities to locate cybercriminal groups. Hacking forums, however, are sometimes indexed.
- Ease of Use– instant messaging apps are easy to use on mobile devices, unlike the dark web. Over time, the illegal cyber economy is likely to be better supported by mobile-based platforms (which will give chatting platforms a further advantage).
- Different Chatting Options – in addition to the option of private-messaging (one-on-one communication), messaging app users can also open groups, channels, and servers to create closed/public communities with full ownership.
- Simple to Operate – building and maintaining your own website/domain on the dark web is more difficult and expensive than making your own community on IM apps.
It’s also worth mentioning that dark web users who migrate to IM don’t necessarily leave the dark web, but most of the time they use both services. We see this when threat actors publish their personal IM accounts on their profiles or in their signatures on the dark web forums they use.
For example, take a look at the following screenshot, taken from a hacking forum.
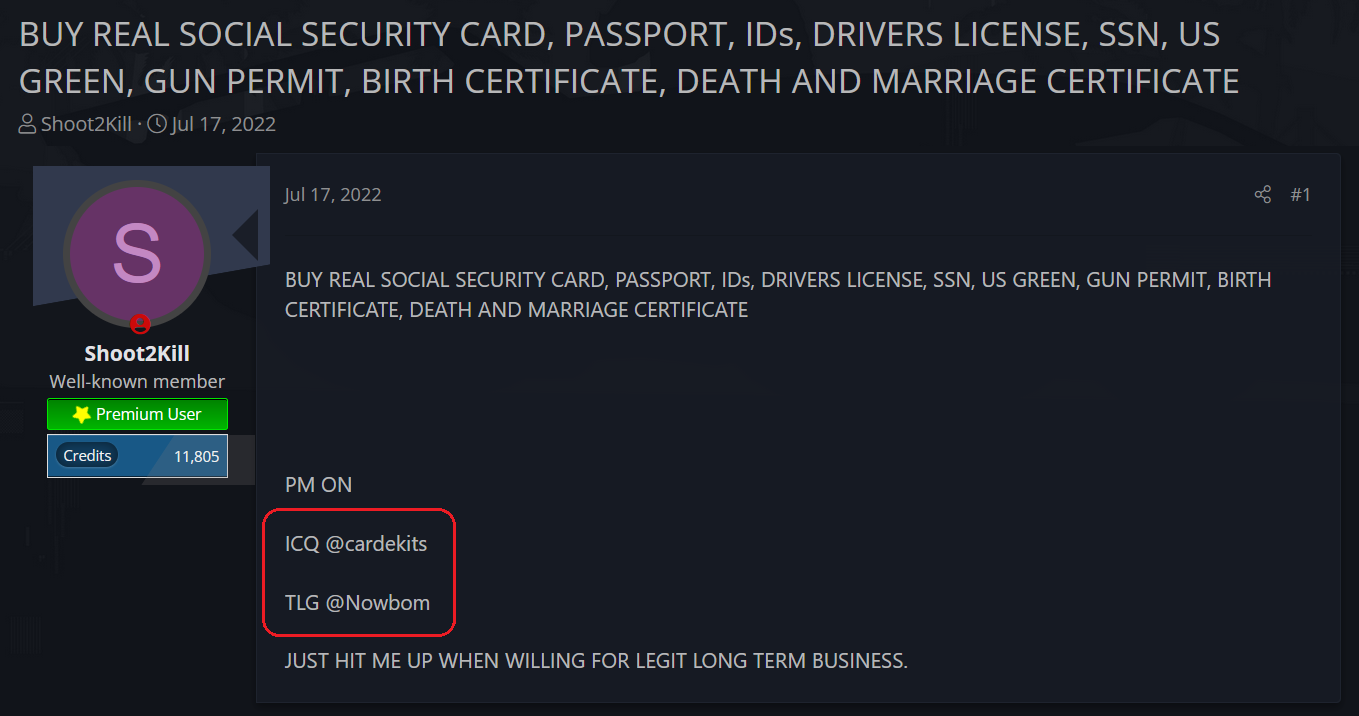
In the image above, the threat actor, named Shoot2Kill, is offering passports and other types of certificates for sale. To facilitate the negotiation, the threat actor posted his IM app details to help potential customers get in touch with him on his personal accounts.
Since Telegram is one of the most popular chat applications among cybercriminals, we’ll take a closer look at examples we found by using our Cyber API that show how threat actors use both dark web sites and Telegram for their illegal operations.
Example #1: Drug trafficking
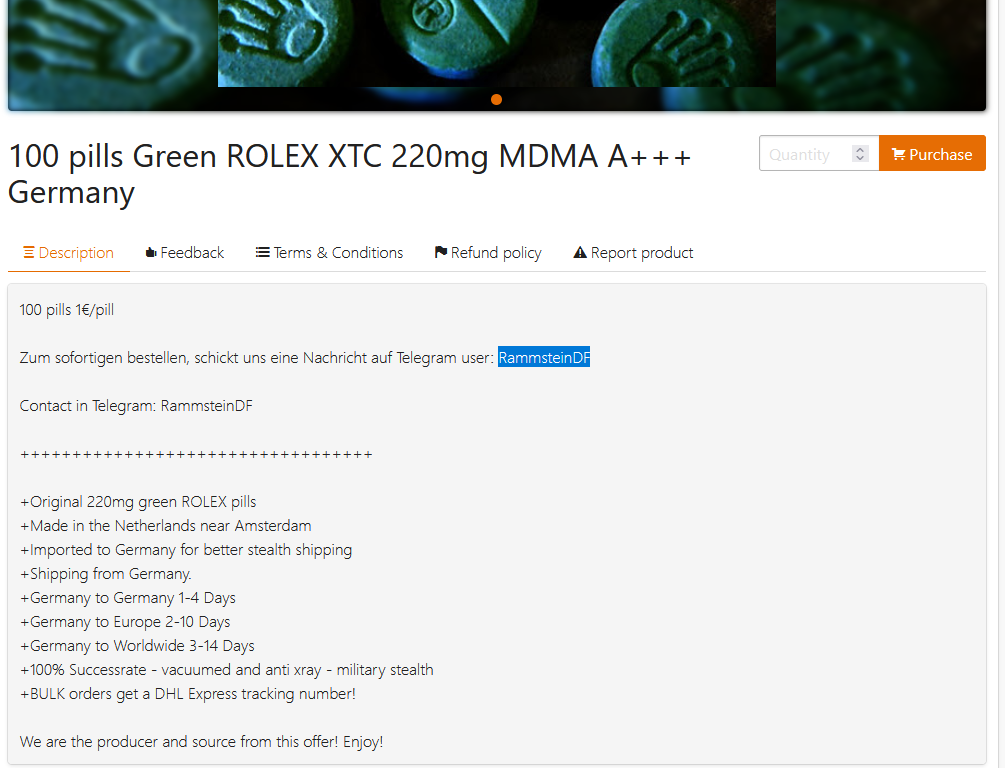
In the following example, a vendor named Rammstein listed the illegal drugs he is offering for sale on one of the top illicit dark web marketplaces on Tor. The cybercriminal lists his drug offering, along with his Telegram account, for negotiation purposes.
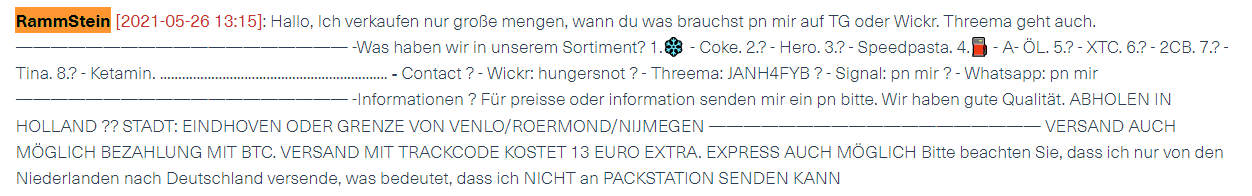
We used his Telegram username to search for other posts written by him on different Telegram groups and channels we monitor. Below, you can see a screenshot of one of the results on our Cyber API. In it, you can see a message by Rammstein sent in a Telegram group dedicated to drug trafficking, where he is listing drugs for sale.
Example #2: Cybercriminal groups activities
There are many cybercriminal groups who are responsible for conducting cyberattacks (such as DDoS attacks, ransomware attacks, etc.) and leak data they steal. Since this practice has become commonplace over the past few years, the use of chat applications by those cybercriminal groups has also increased.
These groups use chatting apps to privately communicate with the victims and carry out negotiations. They use chat rooms to mostly announce upcoming attacks, recruit other cybercriminals and publish or sell compromised databases they’ve already stolen.
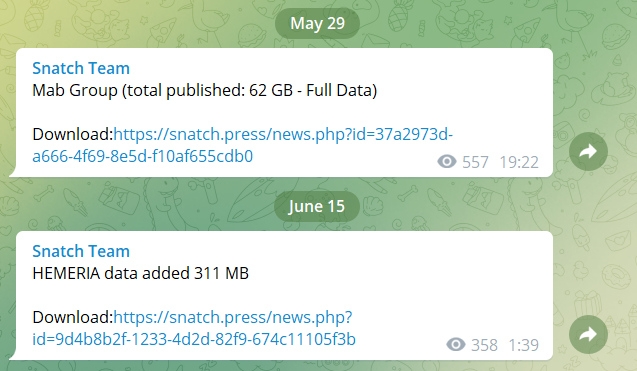
In the following example, you can see a screenshot we took from a dark web Tor site operated by Snatch group.
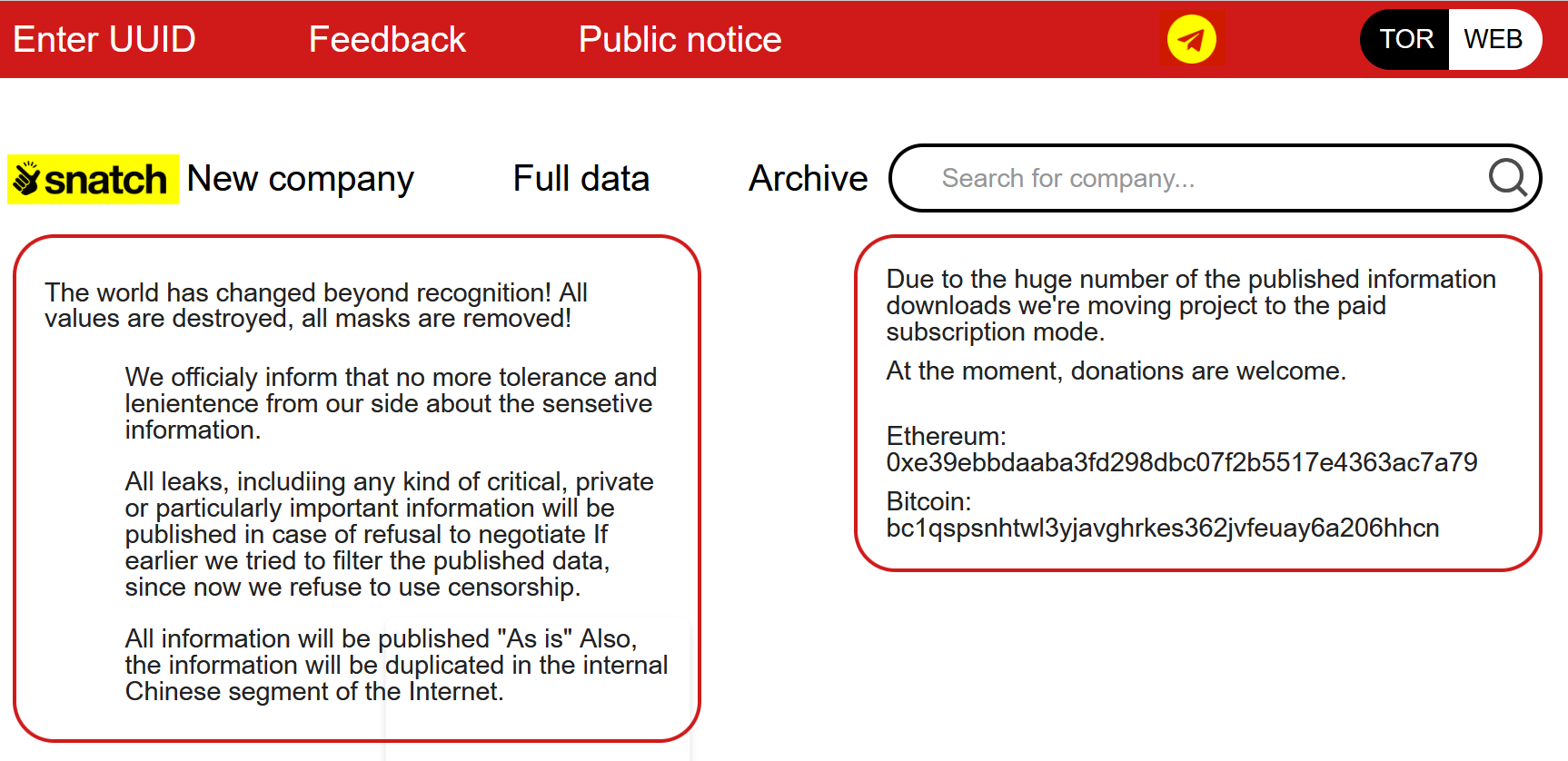
As you can see on the top right (highlighted in yellow), the group has also left an invite link to the Telegram channel they operate. They use this channel to publish compromised databases belonging to companies they had targeted.
Like we wrote in previous Dark Web Pulse posts, there are many other cyber criminal groups who use Telegram, such as RansomHouse, Arvin Club, Lapsus , BlackShoadow, GhostSec, Moses Staff and more.
Example #3: Hacking forum activities on IM
Interestingly, hacking forums admins also run chatting groups and channels. Take Breached for example, a widely known hacker forum, who operates its own Telegram channel. On this channel, the admins publish updates related to the forum and other new and interesting topics that are being discussed, published or items that are sold on the forum.
This screenshot below was taken from that channel, where a Breached admin published a URL directing to a thread on the forum, where he offers to leverage his “middle man services” for transactions with other members of the forum.
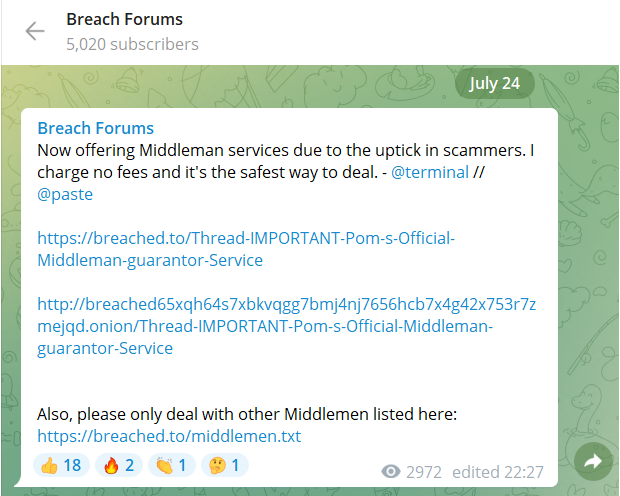
What’s next?
Over time, more and more new features are being added to chatting apps, which makes their use easier and the platforms even more accessible. With chatting applications becoming a key platform for cybercriminals, monitoring them alongside dark web sites is critical.
We work with leading MSSPs (Managed security service providers), MDRs (Managed detection and response), DRP (Dark Risk Protection), WEBINT, Crypto protection, CTI (Cyber Threat Intelligence) and IT (Identity Thief monitoring) teams to provide them with the most relevant data from deep, dark web sites and chatting applications in near-real time.
https://webz.io/dwp/from-dark-web-sites-to-telegram-groups-where-do-cybercriminals-operate/
Published: 2022 08 10 11:51:24
Received: 2023 02 08 12:46:29
Feed: Webz.io Dark Web Posts Web Intelligence
Source: Webz.io Dark Web Posts
Category: News
Topic: Web Intelligence
Views: 19