Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Inside the Underground World of Cybercriminal Groups
published on 2022-03-23 11:16:10 UTC by Hagar MargolinContent:
Working with dark web feeds on a daily basis means our cyber team has become very familiar with the day to day operations of organized cybercriminal groups and ransomware gangs in the deep and dark web. We have been studying their methods of work, witnessed new groups emerging, and recognized the rise of new groups, sites and threats.
With the growing number of cyber attacks, and in particular ransomware attacks, we have decided to shed light on the methods of work of the cybercriminal groups behind them.
Cybercriminal groups have developed their modus operandi over the years to achieve their goals. Let’s take a closer look at what those goals are and the deep and dark web platforms these groups are using to attain them:
How do cybercriminal groups communicate with their victims in the deep and dark web?
In the past, the majority of cyber attacks targeted individuals, with little to no significant economic damage to enterprises. In recent years we have witnessed a huge increase in the number of cyber attacks aimed at enterprises, organizations and governments.
Cybercriminals have ganged up to target as many organizations as possible to maximize profits. The groups they formed can be divided in two:
- Ransomware gangs – cybercriminals who demand money from companies they managed to breach and encrypt their files. They will ask ransom in return for unlocking the encryption and at times – in return for not leaking or selling of the data to the public.
- Other hacking groups who are either primarily concerned with stealing the victims’ data (while still allowing them access to those files) or with launching massive and disruptive attacks on the victim’s site. If they are successful in stealing the data, they will demand payment for keeping from leaking the sensitive data they stole to the public or highest bidder.
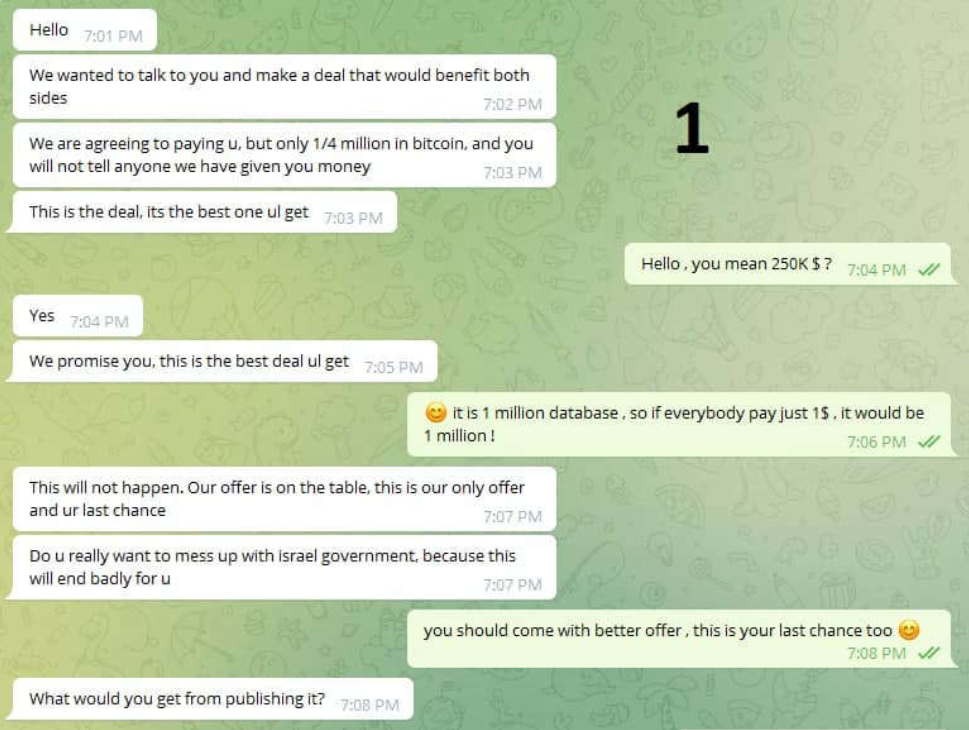
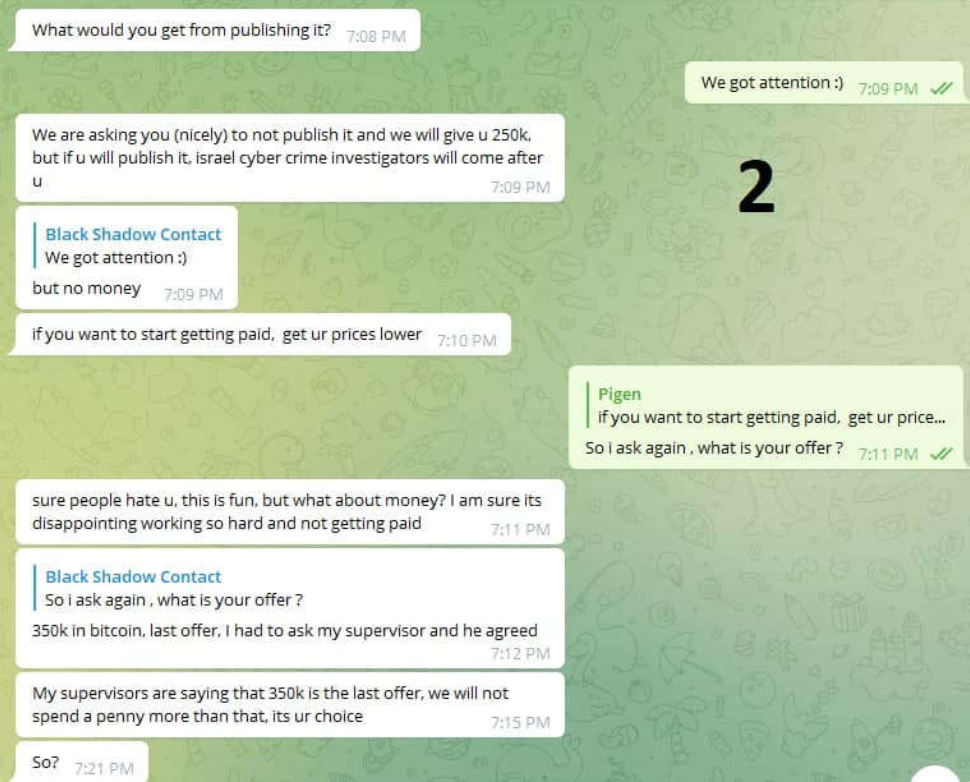
Both in the case of ransomware gangs and other hacking groups, they would leave contact information for negotiation and payment – whether on an encrypted file or on the victim’s site.
Communication between the two will be usually conducted via encrypted emails and encrypted chat platforms like Telegram. The payment method will be conducted through crypto addresses as a measure to protect the hackers’ anonymity.
In the image below you can see an example of an interaction of this nature in a Telegram post leaked by Iranian hackers group Black Shadow who conducted negotiations with a body representing the Israeli government in order to prevent the publication of stolen data they retrieved from the Israeli LGBT dating app Atraf.
Where do cybercriminal groups publish the leaked data in the deep and dark web?
The cybercriminal group will usually publish a list of its victims on a site they create on a public platform (if it owns one) on the deep and dark web, such as a Tor and open web website or Telegram group.
The reason cybercriminals will use a public platform at this stage is to pressure companies and government agencies into paying ransom out of a fear that their stolen information would be leaked on the same platform.
If negotiations fail, the cybercriminal groups will release the information they stole – either for free or for sale to any bidder as a last ditch effort to profit.
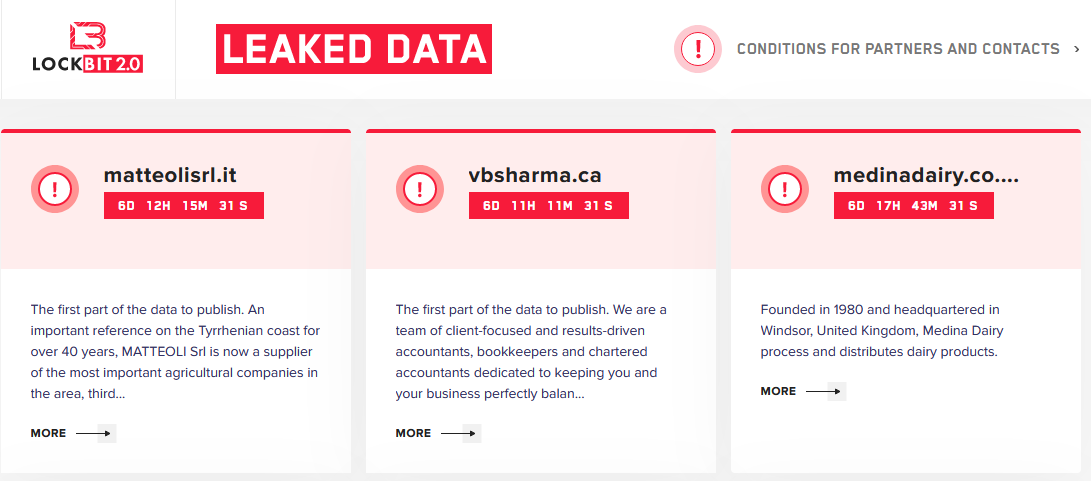
In the following example, we can see databases that the LockBit ransomware group breached and encrypted – but was yet to be leaked. Next to each victim, there is a countdown on display, showing the time until the data is due to be leaked to the public, unless the ransom is paid. This is a common tactic they use to pressure their victims into paying their ransom.
How do cybercriminal groups communicate their messaging to the public?
While the main drive behind most hacking groups is profit, there are some hackers who are driven by ideology. The main term used for these hacking groups is “hacktivists” and they refer to hackers who collaborate to launch cyber attacks in support of political, environmental and religious causes.
These groups use social networks and image boards as well as paste sites and other websites to communicate their messages or propaganda to the general public.
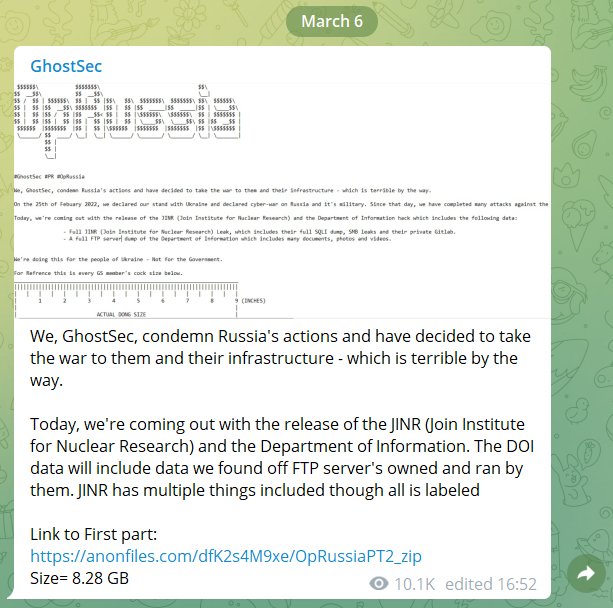
In the next example (see image below), you can read a message that was sent by the hacktivist group GhostSec, an offshoot of the Anonymous hacking group. In it, they announce they support Ukraine and declare a cyber war on Russia and its military. In the same message, they also leaked sensitive data that belongs to Russia’s JINR, the Joint Institute for Nuclear Research, and to the Russian Department of Information.
We have seen many similar announcements on the deep and dark web over the past weeks, since the hybrid war between Russia and Ukraine broke out.
As this war developed, we have surprisingly seen ransomware groups joining the ranks of one of the two countries.
For example, in the image below you can find a post by ransomware group Conti. They used the website they operate in the dark web as a platform to publicly announce their support of Russia and its citizens.
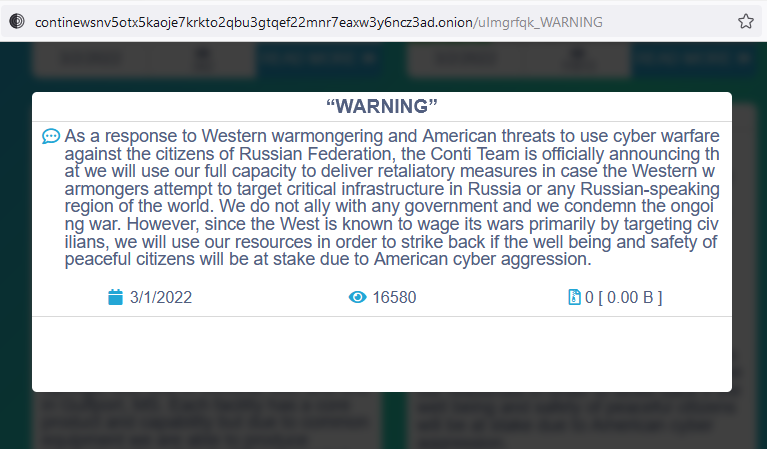
In this message, Conti threatens any western organizations, and particularly American bodies, who will attempt to attack Russian entities.
How do cybercriminals communicate with other cybercriminals?
Another use of the dark web by cybercriminal groups is correspondence with other cybercriminals. We usually find these communications in closed hacking forums where threat actors discuss general cyber issues. These discussions can go from technical matters to the latest cyber news, like the arrest of other fellow cybercriminals.
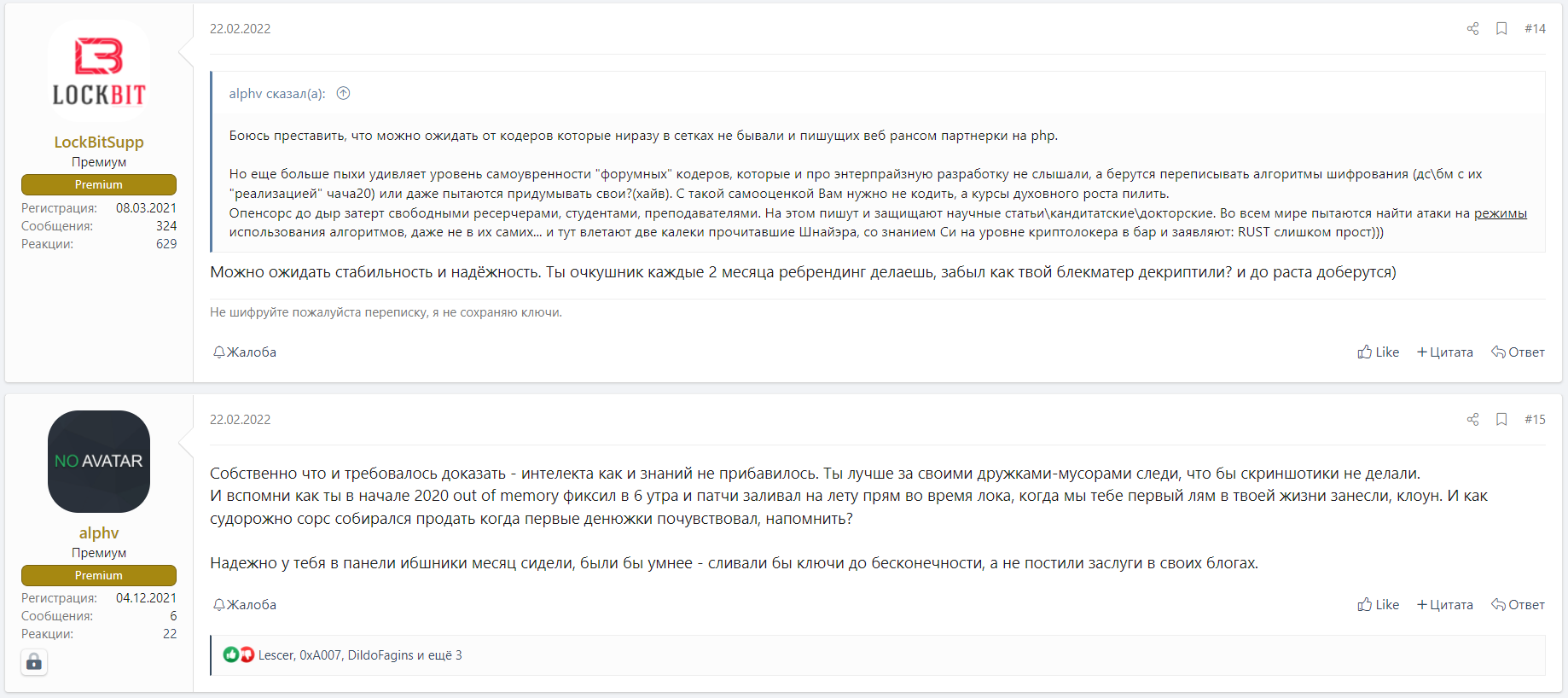
At times, we see some unusual correspondence between ransomware group members. You can find the perfect example of that in the post below where members from two known ransomware groups, one from Lockbit and one from Alphv (aka BlackCat). The two teased one another over the stability and quality of their ransomware source codes. The Alphv group member even went as far as claiming that one of the biggest security companies was able to gain access to Lockbit’s panels and decryption keys for a whole month.
How do cybercriminal groups recruit and form partnerships with other cybercriminals?
Cybercriminal groups also use various platforms on the deep and dark web to reach out and enlist new “talents” into their ranks.
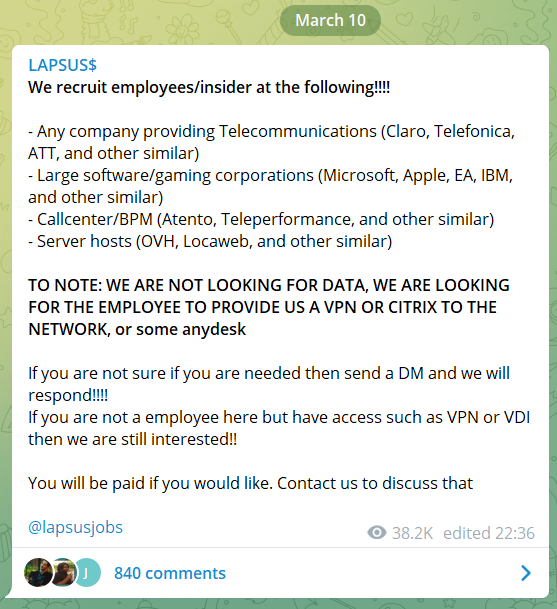
One of the most talked-about recruitments in recent days was from ransomware group Lapsus$ on their Telegram channel (see image below). The ransomware gang published their “job ad” in look for insiders who are willing to sell remote access to major technological corporations and ISPs (Internet Service Providers).
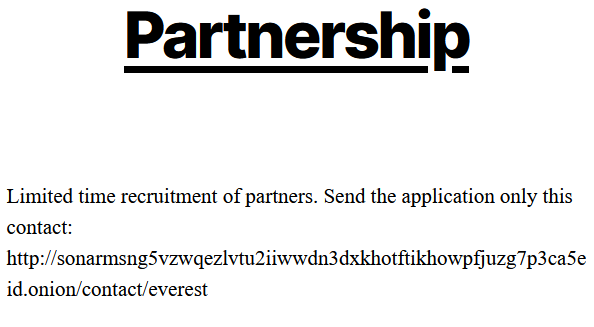
In another example we found (see next image), the Everest ransomware group looked to recruit new hackers to help launch cyber attacks in an ad they published on a site maintained on the dark web. The link attached to the post leads to a contact page on the Tor network, where candidates can anonymously send a cover letter in which they introduce themselves and persuade them they have relevant hacking capabilities.
Alongside organized hacking groups who engage in new recruitments, we also see the early days of new hacking groups as they are formed and new malwares.
In the example below, taken from the popular dark web forum Dread, a threat actor announces he developed a new version of the Chaos ransomware and asks other forum members for feedback.
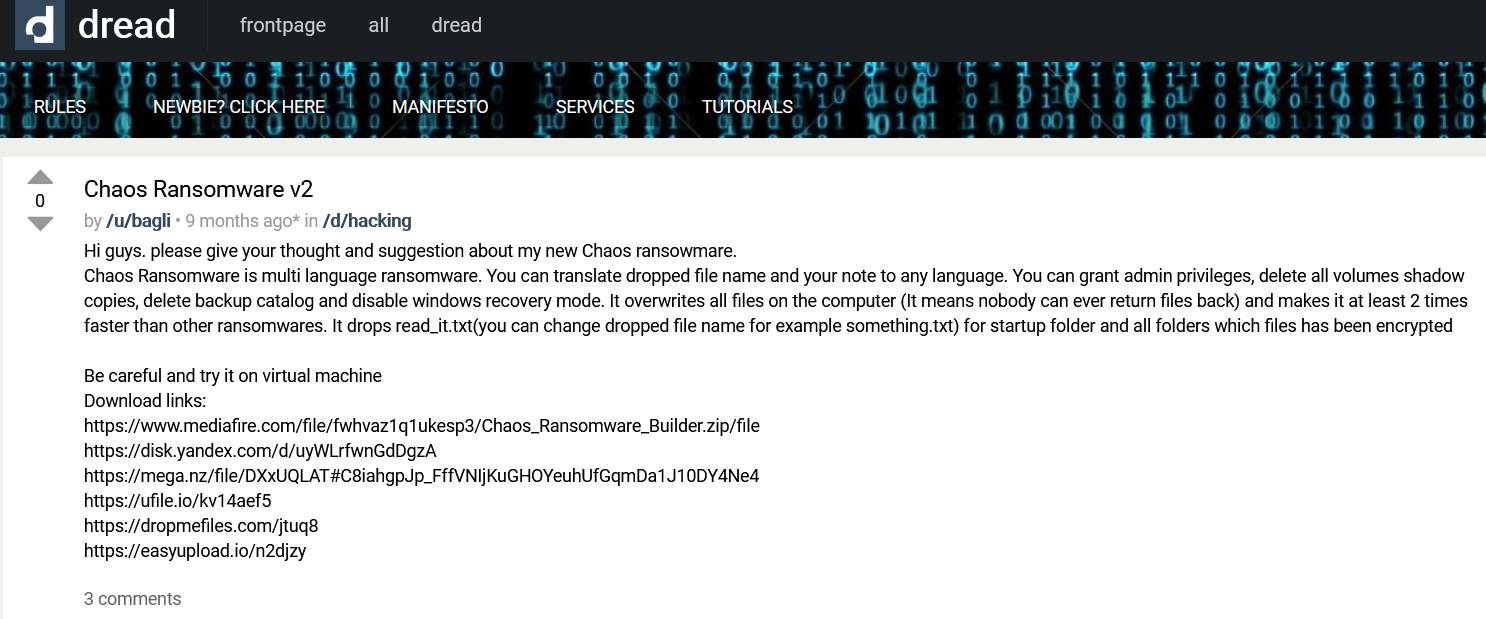
The deep and dark web serve as a comfortable and relatively safe environment for cybercriminal groups to grow their activities and prosper away from the public eye. Cybercriminals discuss, plan, organize, communicate and even recruit their talents in the deep and dark web. The only way to track new and emerging cyber threats is by monitoring these hidden spaces of the web in real time.
Webz.io works with the world’s largest companies to provide relevant darknet web data to always stay one step ahead of cybercriminal groups.
https://webz.io/dwp/inside-the-underground-world-of-cybercriminal-groups/
Published: 2022 03 23 11:16:10
Received: 2023 02 08 12:46:29
Feed: Webz.io Dark Web Posts Web Intelligence
Source: Webz.io Dark Web Posts
Category: News
Topic: Web Intelligence
Views: 15