Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Revealed: The Top 10 Paste Sites Used by Cybercriminals in 2023
published on 2023-02-22 10:36:20 UTC by Yuval ShibiContent:
What is a paste site?
A paste site is a website that allows users to store and share text-based information, such as code snippets, scripts, configuration files, or any other form of plain text. Paste sites typically provide users with a simple interface to paste their content, which is then saved as a unique URL that can be shared with others. There are thousands of paste sites online, most of which cater to specific groups of interests.
Although paste sites are commonly used by developers, system administrators, and other technical professionals for various work tasks, because they enable users to quickly and easily share information anonymously, they are also widely used by cybercriminals.
Why are paste sites so popular among cybercriminals?
There are several reasons behind the popularity of paste sites among threat actors and hackers.
They include:
- These platforms are a convenient and anonymous way to share critical information such as code, configurations, and password files that were stolen
- They do not require registration or authentication
- Admins don’t typically monitor or remove content
Are paste sites found on the open or dark web?
The majority of the paste sites are found on the open web but some can also be found on encrypted networks. Since these sites offer their users a level of anonymity when sharing pastes, users are likely to be less concerned about whether the paste site operates over an encrypted or open web platform and are more likely to decide which paste site to use according to the main topics found on it.
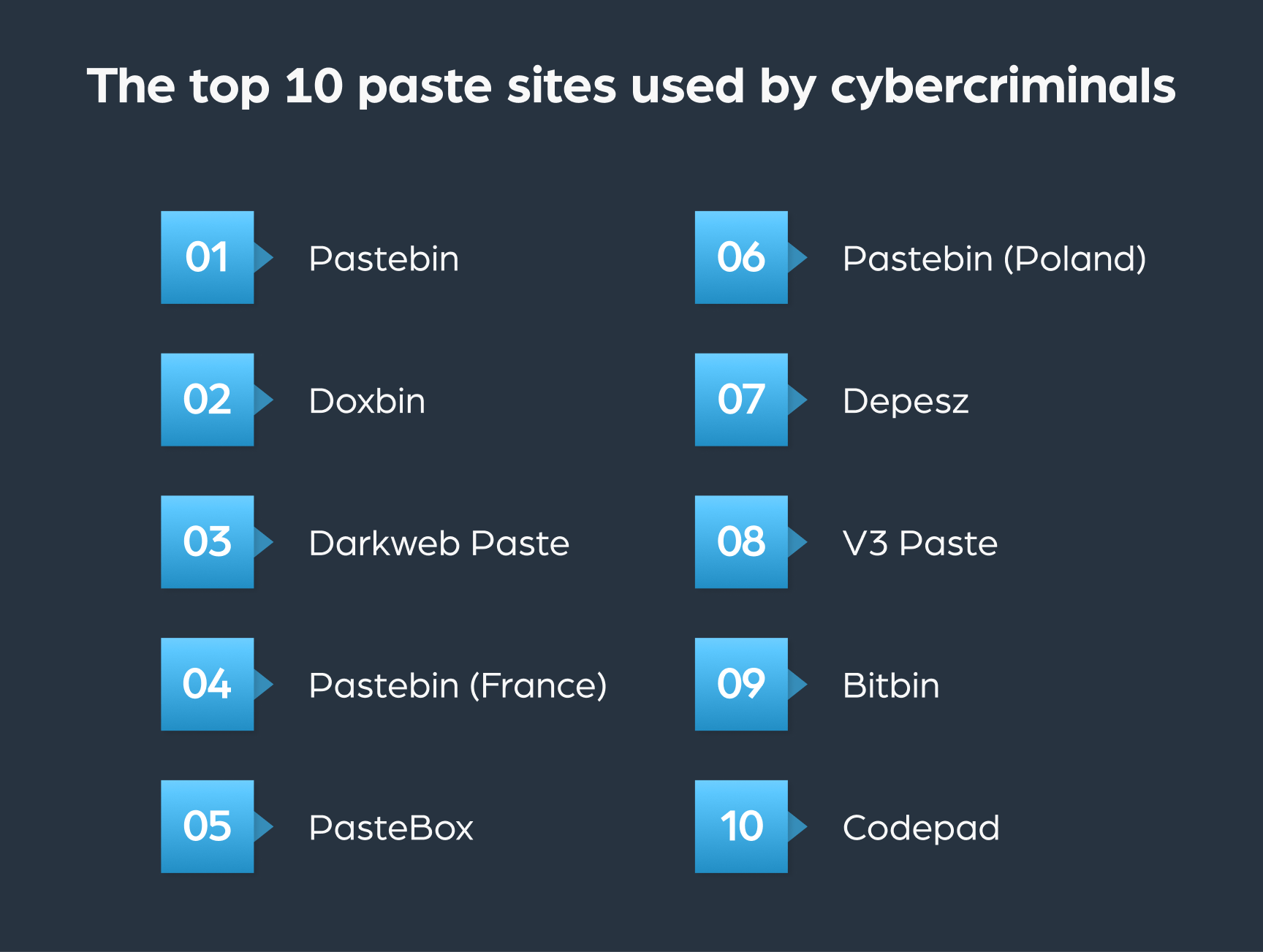
What are the top 10 paste sites used by cybercriminals?
We used our Dark Web API to find the leading paste sites used by cybercriminals. We have listed them from the site most used to the least used:
What illegal content is found on paste sites?
Paste sites host a variety of illicit content, some are more common among cybercriminals and others are considered less popular on other deep and dark web platforms, which makes them more unique to paste sites.
The main contents on paste sites include:
- Hacking guides and tutorials
- Malicious software codes such as viruses, malware, worms, trojan horse, backdoor, and attack scripts
- Sensitive security information, such as source codes, vulnerabilities, and configuration information
- Stolen data and leaked data
- Criminal services such as hitman services
- Illegal trade of drugs, weapons, and even human trafficking
Are all paste sites publicly accessible?
Most paste sites keep a database of all their historical ‘paste files’ accessible to the public. Those which are published on open web sites in particular can be even more easily accessible, due to the fact that they can be indexed by standard web search engines, such as Google or Bing.
However, some paste files are more restricted to the public. Because several paste sites allow their users to hide their files so only people with the unique URL can get full access to them. The reason for this is to allow anonymity to users who wish to remain anonymous or keep their files more protected.
Examples of illicit content on paste sites
As mentioned before, some of the content on paste sites is illicit. We’ve used our Cyber API to reveal 3 examples of deep and dark pastes that feature leaked stolen data, hacking tools, and a cybercriminal service listing.
Example #1: Leaked PII
The following post, which was published on the known paste site DoxBin, features private data of several executives.
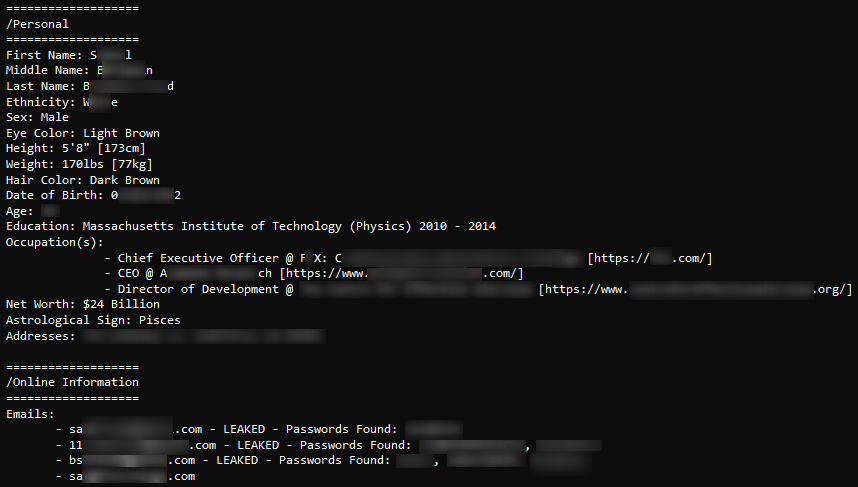
The data includes email addresses, phone numbers, social media profiles, education, occupation, physical addresses, birth dates, etc. DoxBin paste site is known as an important source of information belonging to and targeting executives and VIPs.
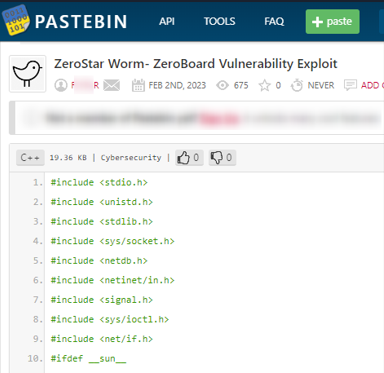
Example #2: Hacking tools
In the next example (below) taken from PasteBin, a threat actor pasted a script of a security vulnerability found on the platform of IT firm ZeroBoard along with its exploit.
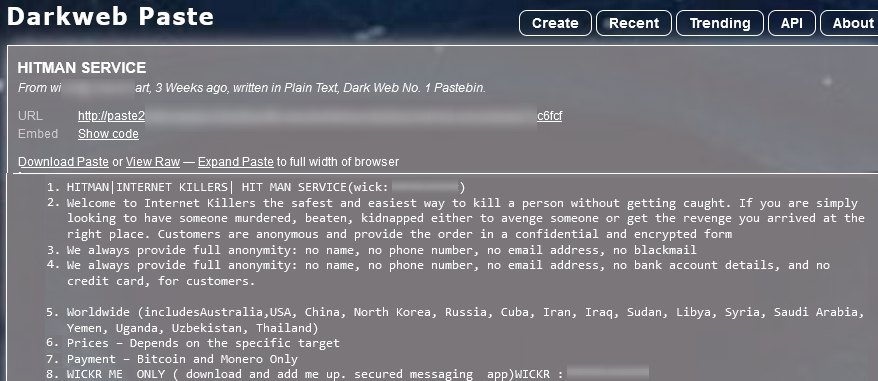
Example #3: Criminal services
Below is an example of a post from Darkweb Paste, a Tor-based hidden platform, offering hitman services, which are typical to paste sites:
Why is it important to monitor paste sites?
In today’s digital landscape, monitoring paste sites has become a critical part of protecting companies and brands from potential cyber and digital threats. While many paste sites are publicly accessible, some allow authors to make their posts hidden or can only be accessed via the dark web. By using specialized dark web content providers, such as Webz.io, companies can gain access to valuable information that may not be available through a simple web search. This can include details on hacking services, stolen data, vulnerabilities, and exploits, allowing companies to stay ahead of potential threats and protect their sensitive data.
https://webz.io/dwp/revealed-the-top-10-paste-sites-used-by-cybercriminals-in-2023/
Published: 2023 02 22 10:36:20
Received: 2023 02 22 10:45:29
Feed: Webz.io Dark Web Posts Data Breach Threats
Source: Webz.io Dark Web Posts
Category: News
Topic: Data Breach Threats
Views: 15
