Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.XSS: The Top Russian Dark Web Forum
published on 2023-02-22 10:59:01 UTC by Sofia PrisiallniContent:
Brief Bio: XSS
- Launch date: 2013, relaunched in September 2018
- Main language: Russian
- Registered member count: 50K
- Total number of posts: 470K
- Main topics: Malware, exploits, vulnerabilities, carding, and credential databases
How did XSS start?
XSS forum, which stands for “Cross-Site Scripting” (a type of security vulnerability), was initially established as DaMaGeLaB back in 2013. After the arrest of one of its administrators in 2017, the website underwent a rebranding process and re-emerged as XSS in September 2018.
This hacking forum, which is Russian-based, is run by a Russian admin, and its primary user base is Russian-speakers. Like other hacking forums, XSS also hosts lively discussions about world events, only here we find more debates relating to the Russian cyber world. It includes conversations about Russian cybercriminals, cyberattacks against Russia, or steps Russia takes against Russian threat actors and Russian forums. The forum also mostly (but not always) supports Russia’s political positions, which became very evident at the beginning of the fighting between Russia and Ukraine.
Today, XSS is considered to be one of the most prominent and professional hacking forums within the Russian-speaking communities on the dark web.
The top illicit activities and content on XSS
XSS is well-established within the cybercriminal community and is known for hosting discussions on illicit topics.
Let’s cover the top types of content we can find on it:
APT and ransomware groups on XSS
XSS is used by APT groups, including ransomware groups, to stay informed about the latest tools, techniques, and vulnerabilities that are being discussed in the wider hacking community. In addition, these groups also do PR on XSS. Their members comment on threads that discuss their activities and publicize their activities to build their reputation.
Some of the APT groups that either used or are still using the XSS forum are Lockbit, REvil, Avoslocker, EternityTeam, Babuk, Darkside, etc.
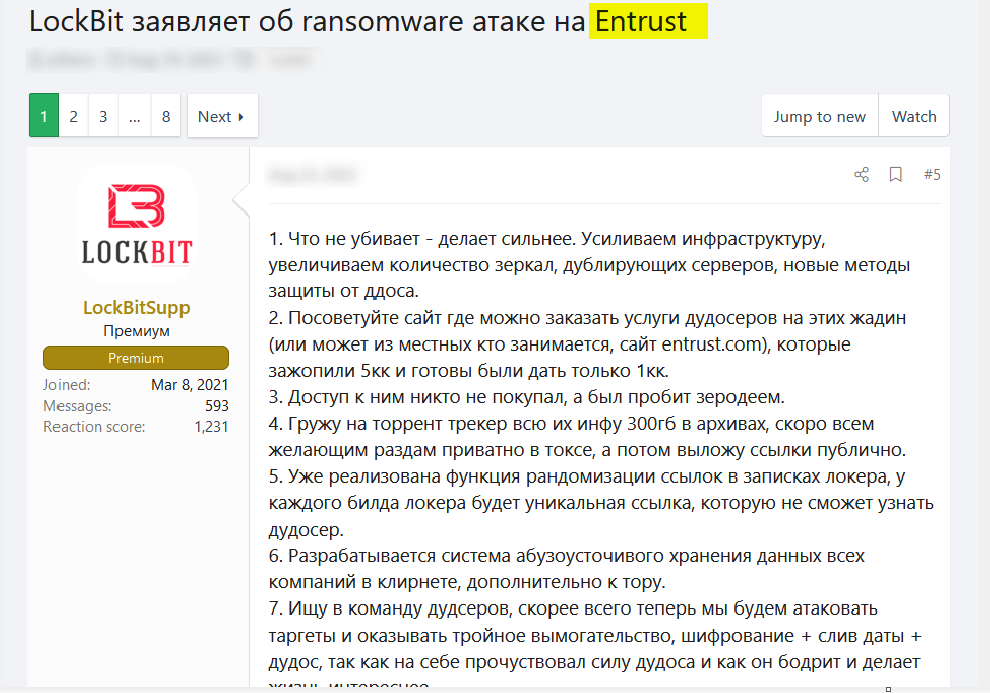
Take for example the image below, which shows a comment on a random post on XSS talking about a cyber attack Lockbit launched against Entrust. In this post, the group’s team implied that Entrust counter-attacked their website with a DDoS attack. In reaction, they also mentioned that they are taking all necessary measures to maintain normal operations and keep their website active.
XSS as a trading platform for illicit digital goods
XSS is also used as a trading platform for illicit digital goods related to hacking and financial fraud. Many of its registered users engage in direct transactions of various items such as leaked databases, custom malware, hacking tools, vulnerabilities, and zero days that were discovered by hackers.
The following example includes a screenshot of a known author offering the malware he’d developed on a loan for different periods of time – such as a day, a week, or a month:
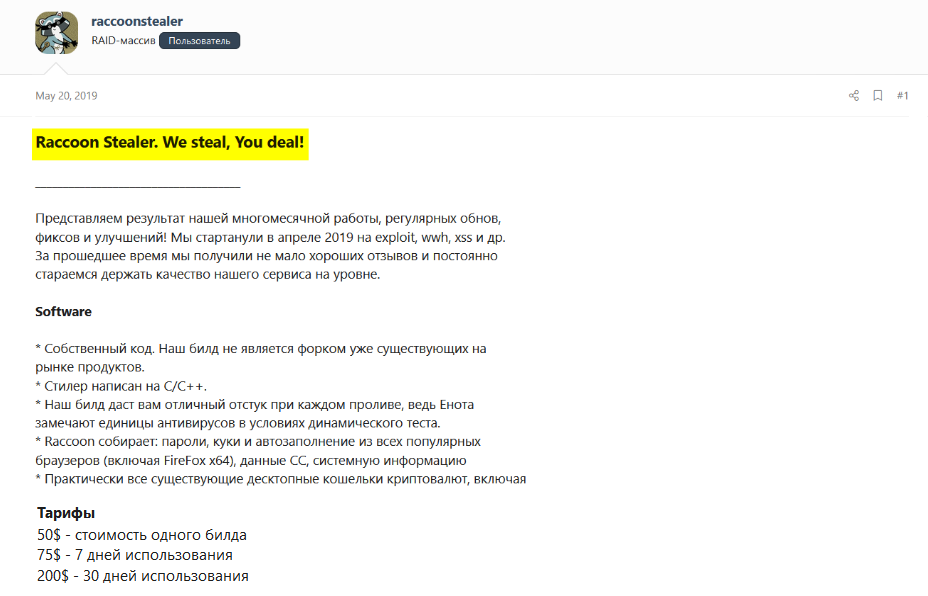
The malware he developed is called Raccoon Stealer, which is an information-stealing malware that cybercriminals typically use to unlawfully obtain sensitive data stored on the user’s browser.
XXS as an advertisement platform
a sense of trust and credibility.
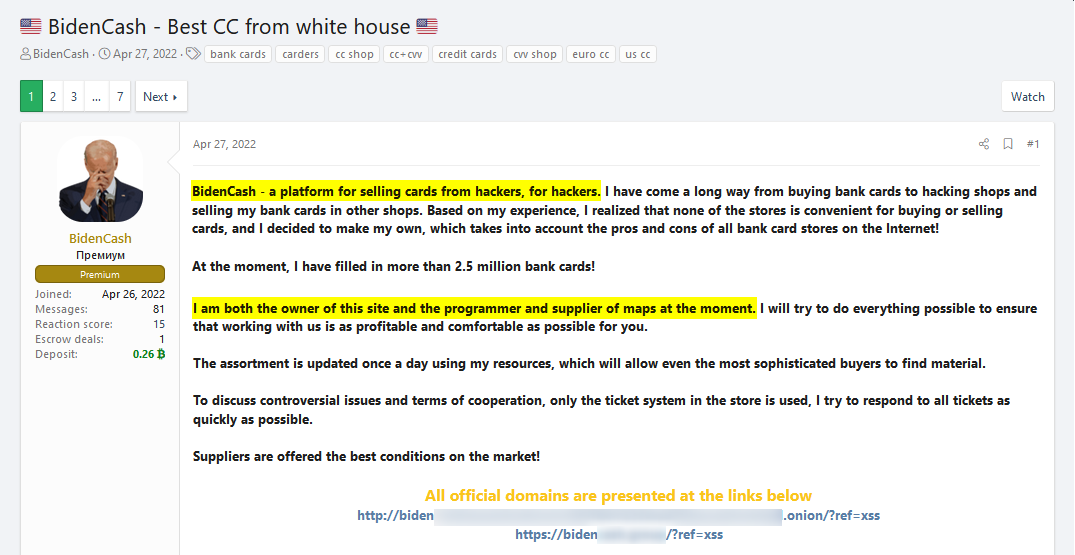
The example below includes an ad posted by BidenCash’s admin, a marketplace for stolen credit cards:
How to access XSS?
XSS can be accessed in encrypted and mainstream browsers. However, an account must be created and approved by an XSS admin in order to view and post content. The forum has restricted sections and threads that can only be accessed through paid membership for a premium account. Each user receives a user rank with a reaction score based on their contribution to the forum.
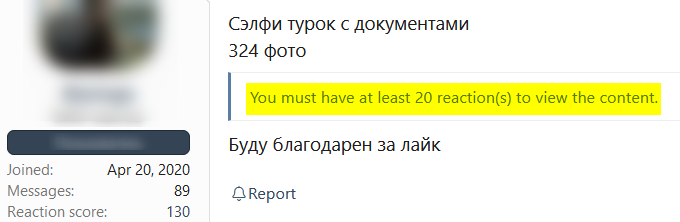
Depending on the user’s plan, they will be required to attain a specific level of activity or spend a minimum amount of time in the forum in order to view the complete content of a post. The following image includes a post that can only be accessed by users with a minimum of 20 reactions.
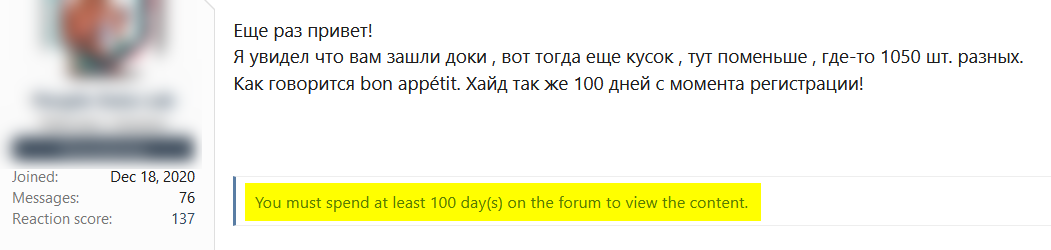
The next example includes a post that is restricted to users who have been members of the forum for at least 100 days:
What’s next?
The increasing relevance of these forums in recent years is a direct result of the growing number of cyber incidents. XSS, like many other hacker forums, has become a critical source of information for monitoring and investigating a variety of cyber threats, including data breaches, ransomware attacks, DDoS attacks, phishing, and other emerging digital risks.
For this reason, many threat intelligence companies track these dark web sources, with the use of dark web data providers like Webz.io, to detect potential threats and identify malware and vulnerabilities that can be exploited by malicious actors against organizations and enterprises.
https://webz.io/dwp/xss-the-top-russian-dark-web-forum/
Published: 2023 02 22 10:59:01
Received: 2023 02 22 11:05:47
Feed: Webz.io Dark Web Posts All
Source: Webz.io Dark Web Posts
Category: News
Topic: Cyber Security
Views: 4
