Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.The Trick Cybercriminals Use to Avoid Detection and How to Overcome It
published on 2023-02-22 10:55:59 UTC by Sofia PrisiallniContent:
The dark web has emerged as a notorious underground space on the internet, where cybercriminals engage in illicit activities and trade illegal tools and content such as exploits, zero days, and compromised databases.
Cybercriminals continually adapt and refine their methods and activities on the darknets, making it increasingly challenging for threat intelligence bodies and law enforcement to track them. Research has highlighted this need, predicting that the global threat intelligence market size is expected to grow from $8.9 billion in 2021 to $16.1 billion by 2026.
We have been tracking cybercriminals on the dark web to understand the tactics they use to evade detection. One tactic we have seen threat actors increasingly using is posting illicit content while concealing the identifiers of their victims, such as the company’s name or domain. Instead, they only mention the victim’s industry. This allows them to sell sensitive data and exploits on dark web platforms for maximum profit and minimum interruption. Some threat actors have even indicated that this practice enables them to sustain their criminal operations for extended periods, as you can see in one of the examples below.
Let’s take a look at a few examples from the dark web.
Example #1: Zero Day exploit to hack IT management system
The first example includes a post a cybercriminal published on the hacking forum BreachForums in February 2023, where he offered a zero day exploit targeting an IT management system for sale.
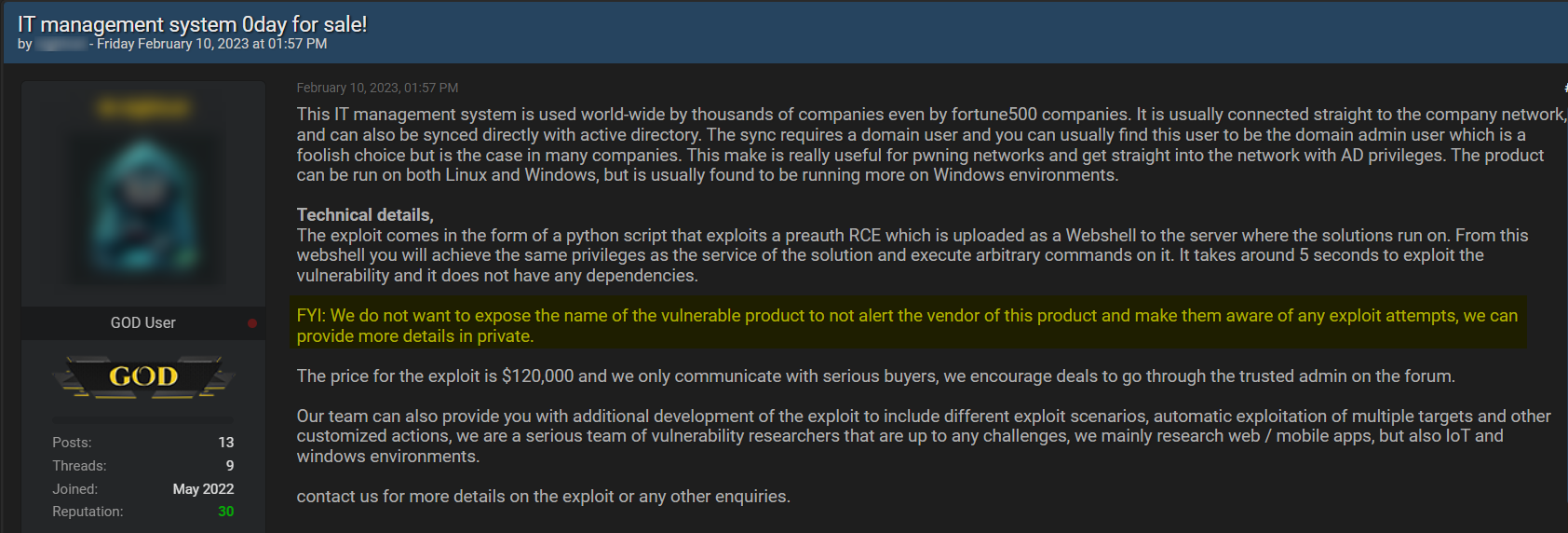
The threat actor seems to go through a lot of effort to deliberately hide the identity of the targeted organization. Not only do they avoid any direct reference to the victim’s name but they literally explain in the post that they take this protective measure “to not alert the vendor”.
This practice of refraining from using the victim’s name is intended to prevent drawing attention to their vulnerability, which allows the threat actor to continue selling it for longer periods.
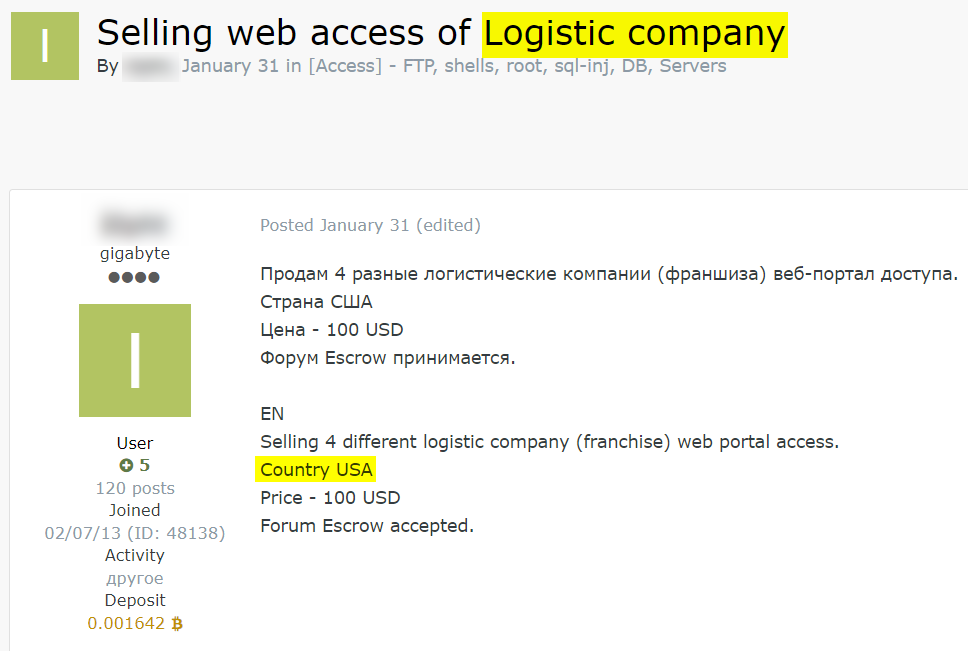
Example #2: Web portal access to US logistics company
In January 2023, a Russian threat actor advertised the illicit sale of four web portal access belonging to a US-based Logistic company located on the hacking forum Exploit. In a bid to conceal the identity of the targeted organization, the threat actor chose to mention only the broader industry and geographic location in which the firm operates.
Example #3: Admin credentials of Argentinian eCommerce stores
In this last example, a cybercriminal is offering for sale admin credentials of one of the largest electronics and home goods eCommerce stores in Argentina on the hacking forum BreachForums.
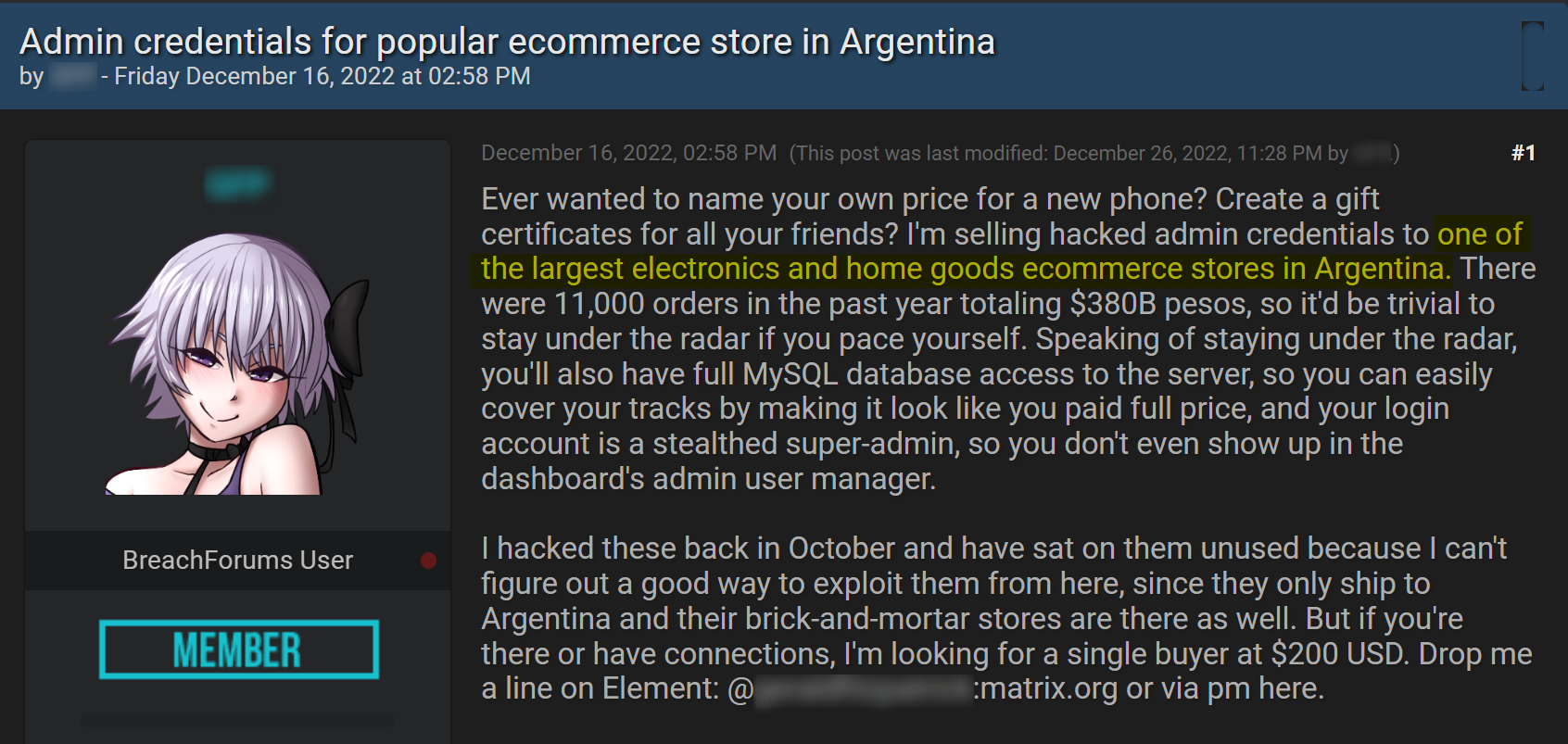
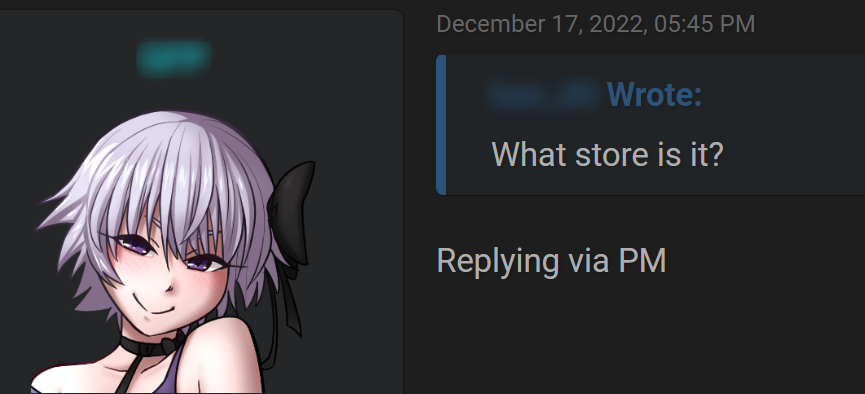
The threat actor just mentioned the industry and the location, keeping any other specific information out of their post. In the next image, you can see that even when a different user is attempting to get more information, like the name of the store, the threat actor wouldn’t share more information unless it was in a private message.
How can monitoring the dark web help?
Given the wide range of tactics that cybercriminals use to evade detection and carry out illegal activities on the dark web, it is imperative to monitor this underground space.
Monitoring the dark web can help threat intelligence teams, cybersecurity professionals, and law enforcement agencies to:
- Stay up-to-date on emerging threats and identify potential attacks before they occur
- Detect compromised credentials, stolen data, and other illicit activity associated with organizations
- Find significant indicators linked to threat actors operating in dark web space for profile investigations
By monitoring these spaces, organizations can respond promptly and proactively to protect their digital assets and prevent financial losses or reputational damage.
Webz.io’s dark web data powers some of the world’s largest monitoring systems and enables them to easily spot vital information in near real-time, to mitigate potential breaches and minimize downtime and business disruption.
https://webz.io/dwp/the-trick-cybercriminals-use-to-avoid-detection-and-how-to-overcome-it/
Published: 2023 02 22 10:55:59
Received: 2023 02 22 11:05:47
Feed: Webz.io Dark Web Posts All
Source: Webz.io Dark Web Posts
Category: News
Topic: Cyber Security
Views: 11
