Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Two U.S. Men Charged in 2022 Hacking of DEA Portal
published on 2023-03-15 01:25:20 UTC by BrianKrebsContent:
Two U.S. men have been charged with hacking into a U.S. Drug Enforcement Agency (DEA) online portal that taps into 16 different federal law enforcement databases. Both are alleged to be part of a larger criminal organization that specializes in using fake emergency data requests from compromised police and government email accounts to publicly threaten and extort their victims.

Prosecutors for the Eastern District of New York today unsealed criminal complaints against Sagar Steven Singh — a.k.a “Weep” — a 19-year-old from Pawtucket, Rhode Island; and Nicholas Ceraolo, 25, of Queens, NY, who allegedly went by the handles “Convict” and “Ominus.”
The Justice Department says Singh and Ceraolo belong to a group of cybercriminals known to its members as “ViLE,” who specialize in obtaining personal information about third-party victims, which they then use to harass, threaten or extort the victims, a practice known as “doxing.”
“ViLE is collaborative, and the members routinely share tactics and illicitly obtained information with each other,” prosecutors charged.
The government alleges the defendants and other members of ViLE use various methods to obtain victims’ personal information, including:
-tricking customer service employees;
-submitting fraudulent legal process to social media companies to elicit users’ registration information;
-co-opting and corrupting corporate insiders;
-searching public and private online databases;
-accessing a nonpublic United States government database without authorization
-unlawfully using official email accounts belonging to other countries.
The complaint says once they obtained a victim’s information, Singh and Ceraolo would post the information in an online forum. The government refers to this community only as “Forum-1,” saying that it is administered by the leader of ViLE (referenced in the complaint as “CC-1”).
“Victims are extorted into paying CC-1 to have their information removed from Forum-1,” prosecutors allege. “Singh also uses the threat of revealing personal information to extort victims into giving him access to their social media accounts, which Singh then resells.”
Sources tell KrebsOnSecurity in addition to being members of ViLE, both Weep and Ominous are or were staff members for Doxbin, a highly toxic online community that provides a forum for digging up personal information on people and posting it publicly. This is supported by the Doxbin administrator’s claimed responsibility for a high-profile intrusion at the DEA’s law enforcement data sharing portal last year.
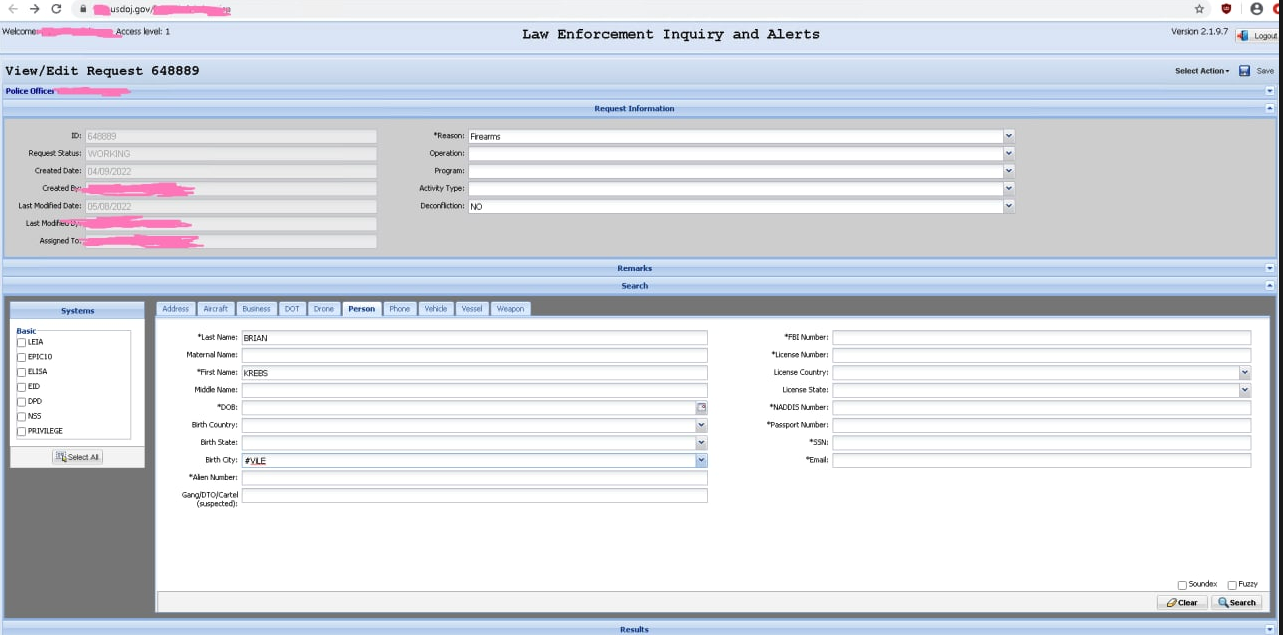
A screenshot of alleged access to the Drug Enforcement Agency’s intelligence sharing portal, shared by “KT,” the current administrator of the doxing and harassment community Doxbin.
The government alleges that on May 7, 2022, Singh used stolen credentials to log into a U.S. federal government portal without authorization. The complaint doesn’t specify which agency portal was hacked, but it does state that the portal included access to law enforcement databases that track narcotics seizures in the United States.
On May 12, 2022, KrebsOnSecurity broke the news that hackers had gained access to a DEA portal that taps into 16 different federal law enforcement databases. As reported at the time, the inside scoop on how that hack went down came from KT, the current administrator of the Doxbin and the individual referenced in the government’s complaint as “CC-1.”
Indeed, a screenshot of the ViLE group website includes the group’s official roster, which lists KT at the top, followed by Weep and Ominus.

A screenshot of the website for the cybercriminal group “ViLE.” Image: USDOJ.
In March 2022, KrebsOnSecurity warned that multiple cybercrime groups were finding success with fraudulent Emergency Data Requests (EDRs), wherein the hackers use compromised police and government email accounts to file warrantless data requests with social media firms and mobile telephony providers, attesting that the information being requested can’t wait for a warrant because it relates to an urgent matter of life and death.
That story showed that the previous owner of the Doxbin also was part of a teenage hacking group that specialized in offering fake EDRs as a service on the dark web.
Prosecutors say they tied Singh to the government portal hack because he connected to it from an Internet address that he’d previously used to access a social media account registered in his name. When they raided Singh’s residence on Sept. 8, 2022 and seized his devices, investigators with Homeland Security found a cellular phone and laptop that allegedly “contained extensive evidence of access to the Portal.”
The complaint alleges that between February 2022 and May 2022, Ceraolo used an official email account belonging to a Bangladeshi police official to pose as a police officer in communication with U.S.-based social media platforms.
“In these communications, Ceraolo requested personal information about users of these platforms, under the false pretense that the users were committing crimes or in life-threatening danger,” the complaint states.
For example, on or about March 13, 2022, Ceraolo allegedly used the Bangladeshi police email account to falsely claim that the target of the EDR had sent bomb threats, distributed child pornography and threatened officials of the Bangladeshi government.
On or about May 9, 2022, the government says, Singh sent a friend screenshots of text messages between himself and someone he had doxed on the Doxbin and was trying to extort for their Instagram handle. The data included the victim’s Social Security number, driver’s license number, cellphone number, and home address.
“Look familiar?” Singh allegedly wrote to the victim. “You’re gonna comply to me if you don’t want anything negative to happen to your parents. . . I have every detail involving your parents . . . allowing me to do whatever I desire to them in malicious ways.”
Neither of the defendants could be immediately reached for comment. KT, the current administrator of Doxbin, declined a request for comment on the charges.
Ceraolo is a self-described security researcher who has been credited in many news stories over the years with discovering security vulnerabilities at AT&T, T-Mobile, Comcast and Cox Communications.
Ceraolo’s stated partner in most of these discoveries — a 30-year-old Connecticut man named Ryan “Phobia” Stevenson — was charged in 2019 with being part of a group that stole millions of dollars worth of cryptocurrencies via SIM-swapping, a crime that involves tricking a mobile provider into routing a target’s calls and text messages to another device.
In 2018, KrebsOnSecurity detailed how Stevenson earned bug bounty rewards and public recognition from top telecom companies for finding and reporting security holes in their websites, all the while secretly peddling those same vulnerabilities to cybercriminals.
According to the Justice Department, if convicted Ceraolo faces up to 20 years’ imprisonment for conspiracy to commit wire fraud; both Ceraolo and Singh face five years’ imprisonment for conspiracy to commit computer intrusions.
A copy of the complaint against Ceraolo and Singh is here (PDF).
https://krebsonsecurity.com/2023/03/two-us-men-charged-in-2022-hacking-of-dea-portal/
Published: 2023 03 15 01:25:20
Received: 2023 03 15 15:22:12
Feed: Krebs on Security
Source: Krebs on Security
Category: Cyber Security
Topic: Cyber Security
Views: 3
